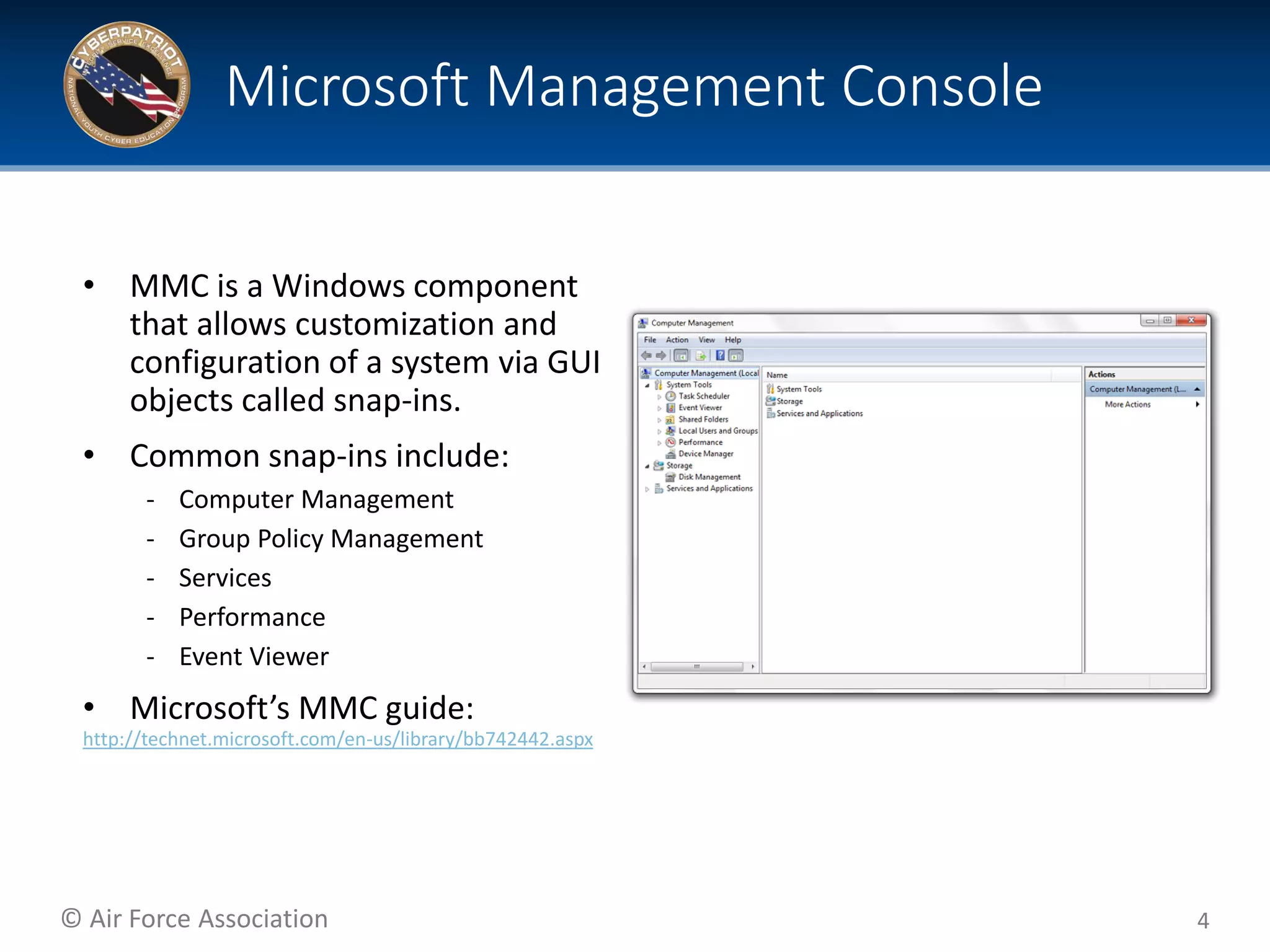
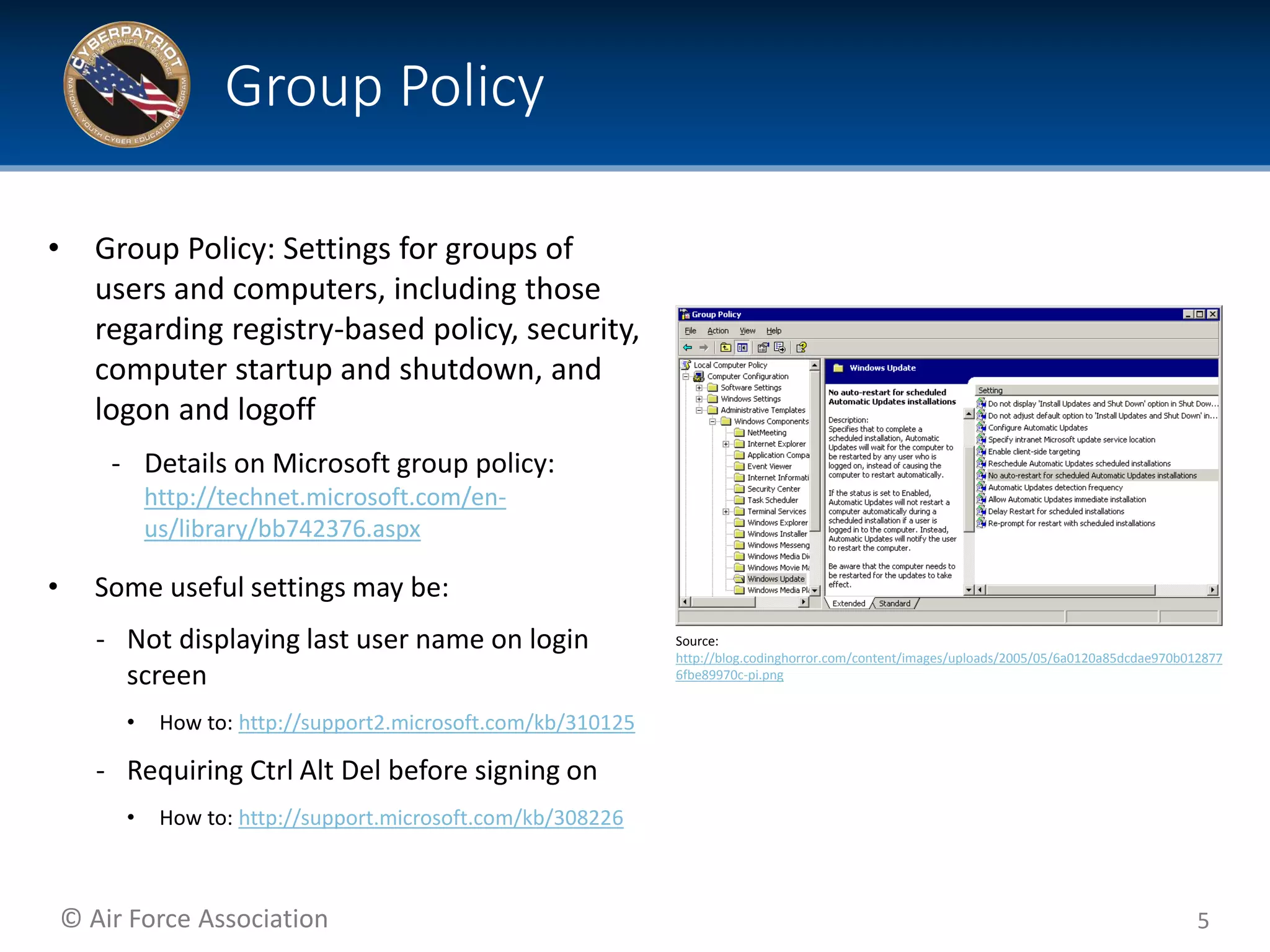
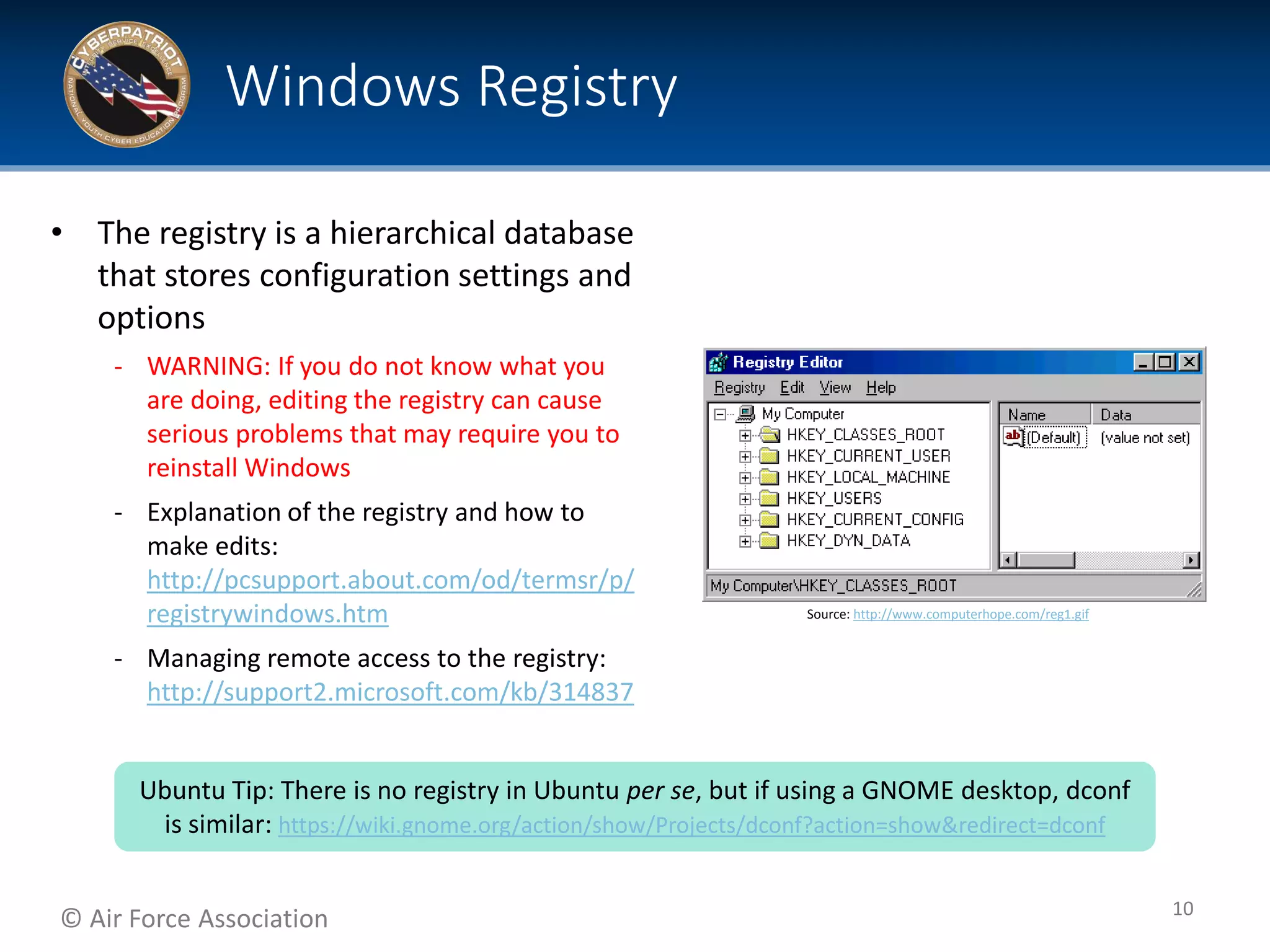
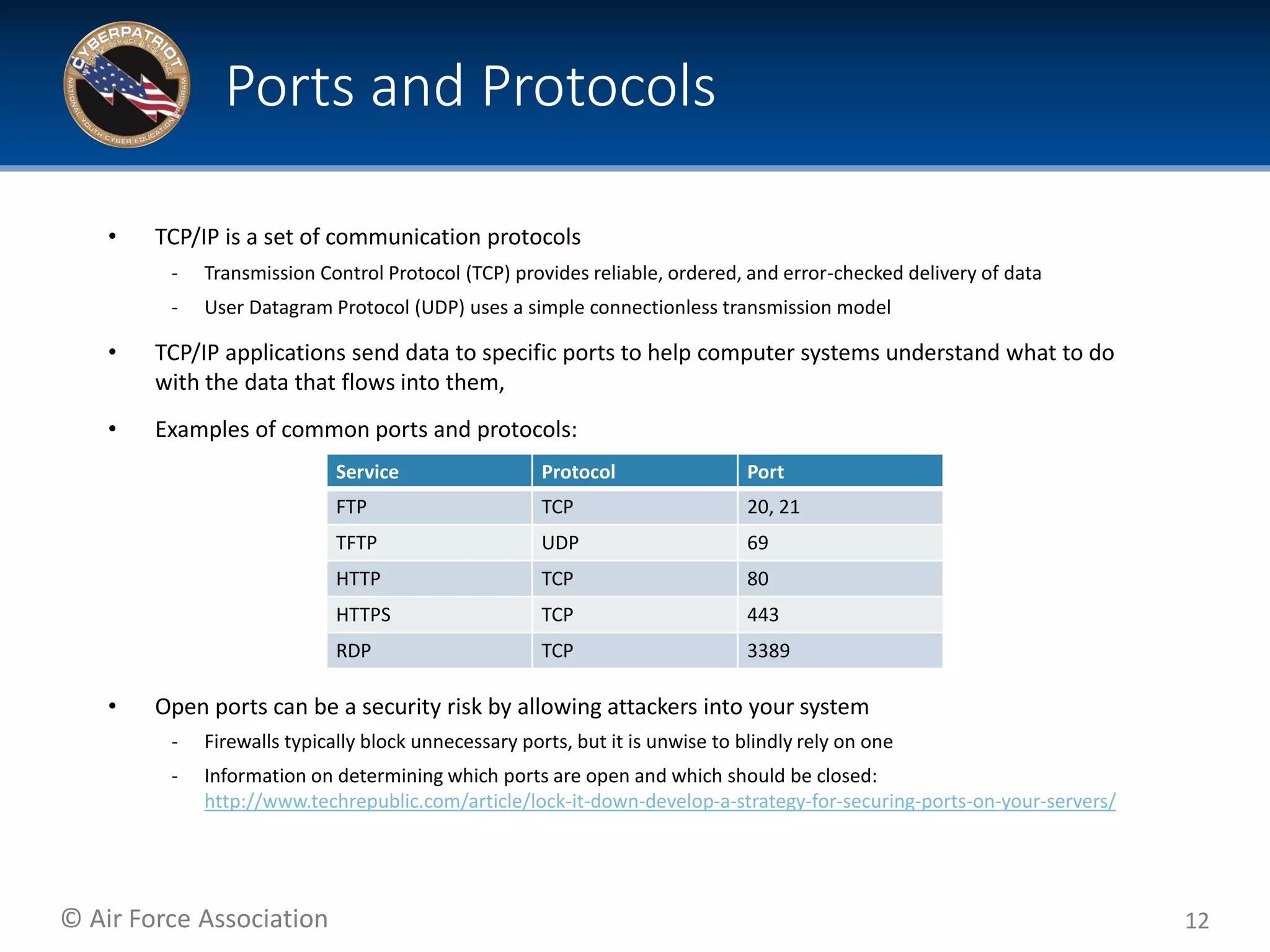
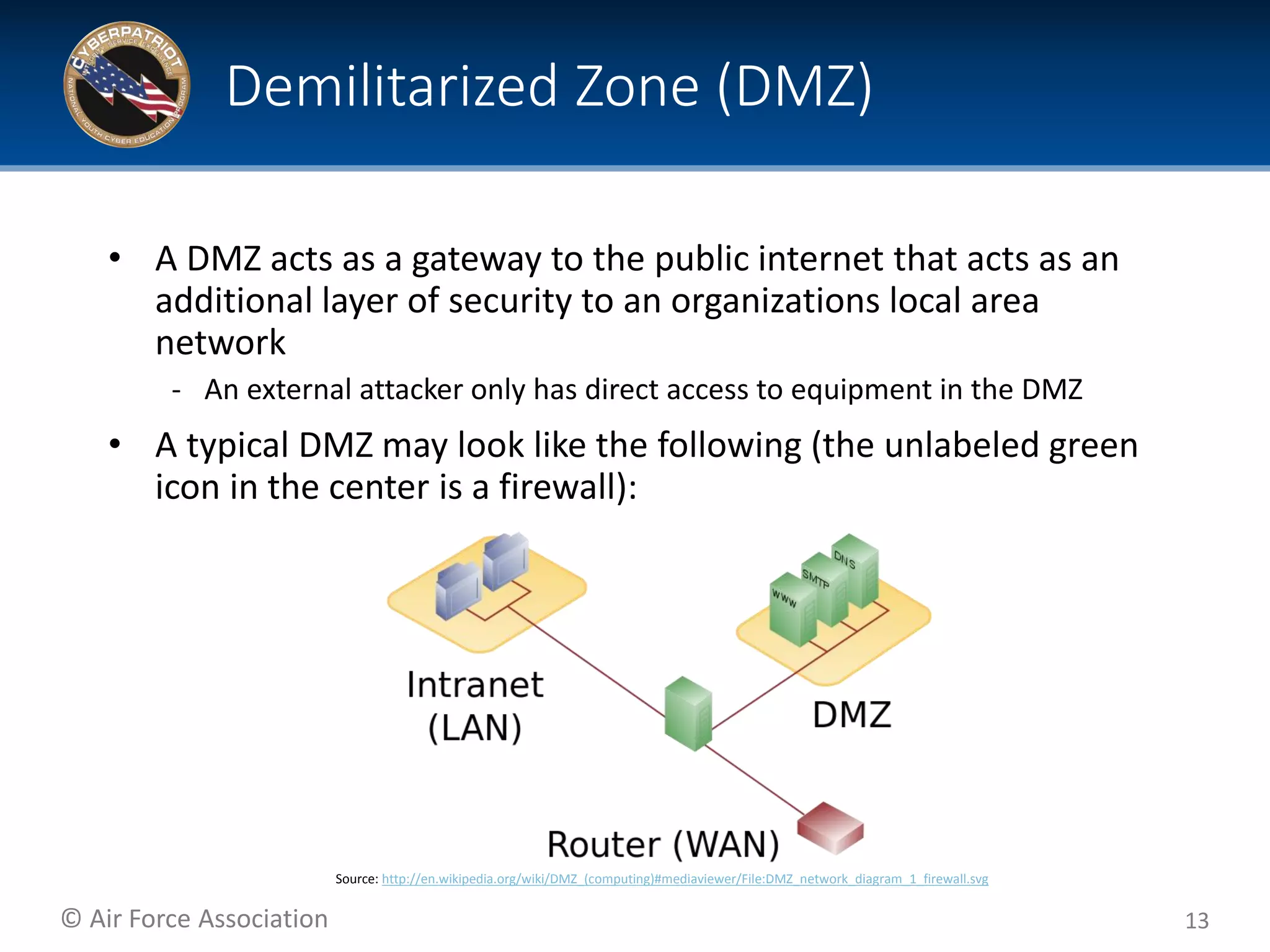
This document provides tips and additional topics for students to study to improve their skills in the CyberPatriot competition. It discusses various topics like web servers, file systems, the Microsoft Management Console, group policy, password hashing, and more. For each topic, it provides definitions and links to online resources for further reading. The document also shares tips from past CyberPatriot mentors, such as familiarizing yourself with Windows and Linux tools, documenting your work, getting hands-on practice, and having students who are not actively working take notes to help the other students.