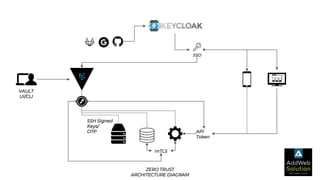
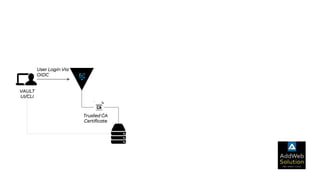
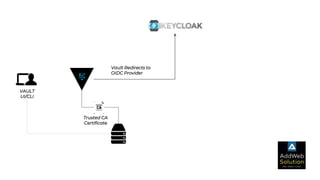
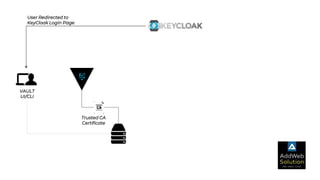
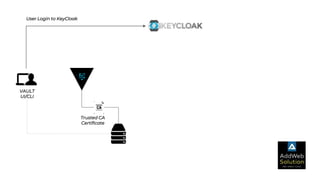
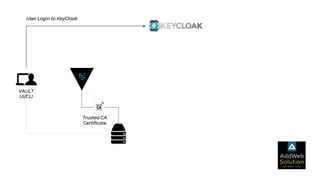
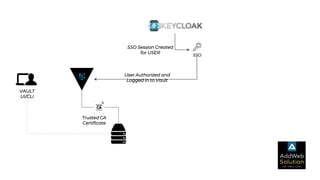
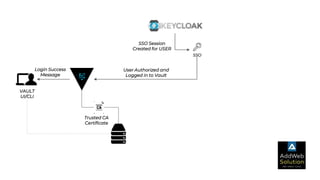
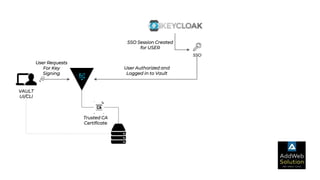
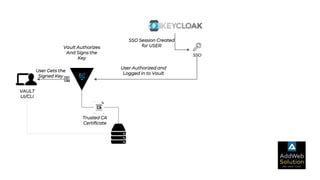
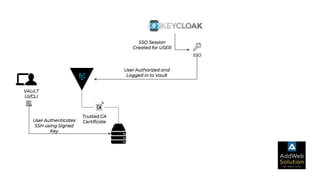
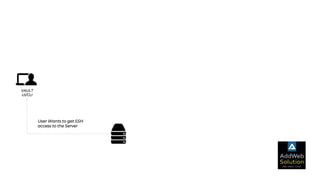
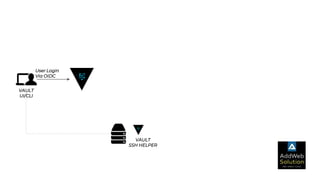
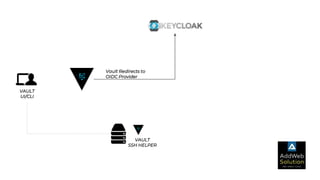
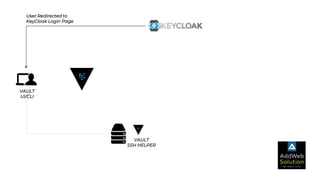
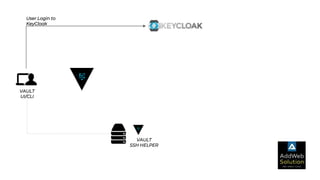
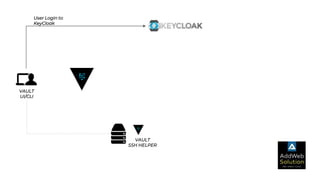
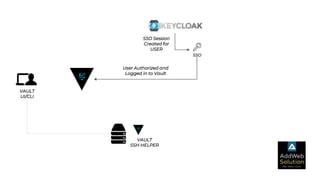
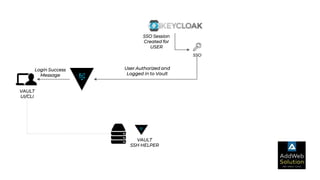
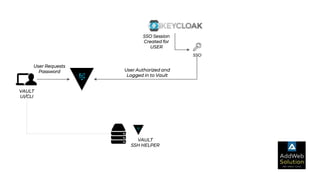
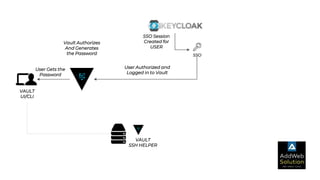
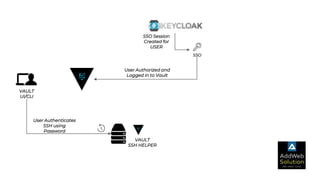
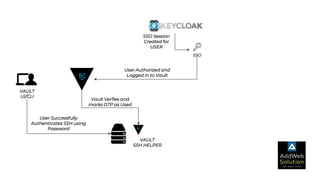
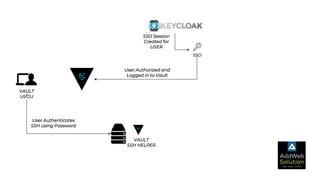
The document explains zero trust architecture, which emphasizes the need for verification of all actors, systems, and services before granting access, moving away from the assumption of inherent trust. It details the key components required to achieve zero trust, including a centralized authentication system using Keycloak for identity management and HashiCorp Vault for secure secrets management, along with their key features for enhancing security. The document also outlines the integration process for these systems to enable secure access to servers and services.