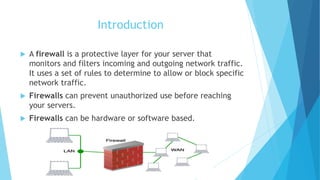
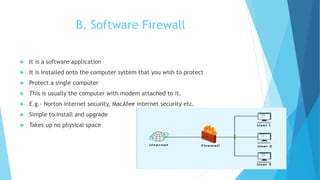
A firewall serves as a protective layer for servers by monitoring and filtering network traffic based on predefined rules to prevent unauthorized access. Firewalls come in hardware and software forms, and they help safeguard confidential information and network resources from malicious threats. Additional concepts discussed include access control lists (ACLs), packet filtering techniques, and the use of a demilitarized zone (DMZ) to enhance security while allowing access to external networks.