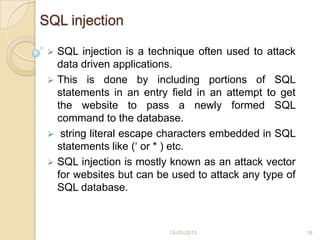
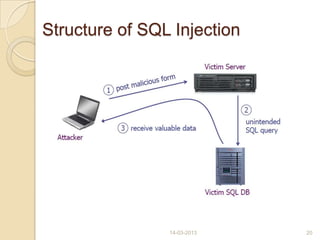
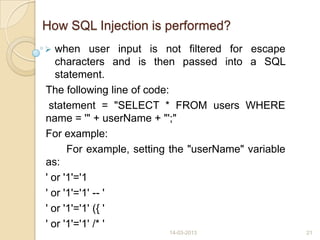
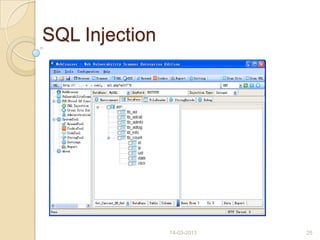
This document discusses black hat hackers and hacking. It begins with an introduction that defines hacking and black hat hackers. It then covers the history of hacking from the 1980s to 2007. It discusses famous black hat hackers and the different types of hackers including white hat, black hat, and grey hat hackers. It describes the pre-hacking stages a black hat hacker goes through when targeting a system. It also outlines the domains affected by hacking, types of attacks like denial of service and SQL injection, detection and prevention methods, and the pros and cons of hiring black hat hackers to test security systems.