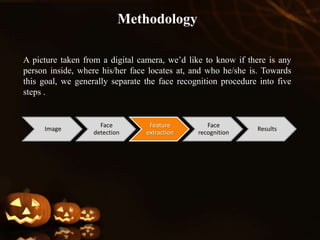
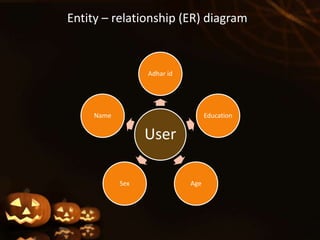
Face recognition is a biometric technique that uses unique facial measurements to identify or verify individuals in images. It analyzes the shape, pattern, and positioning of facial features. Face recognition systems first detect faces in images, then extract distinguishing nodal points like eye depth, nose width, and distance between eyes. They compare these measurements to templates stored in a database to identify matches. While convenient and non-invasive, face recognition has limitations like inability to distinguish identical twins and decreased accuracy with changes in appearance. It finds applications in security, law enforcement, and commercial uses like building access control and ATMs.