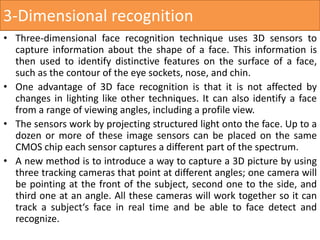
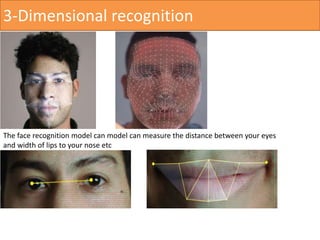
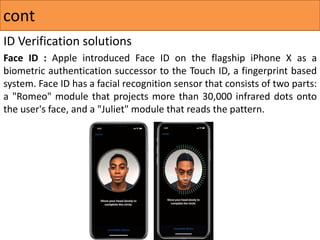
The document discusses face recognition technology, detailing its methods, history, and applications in various fields including security and marketing. It highlights advances in algorithms and biometric systems, particularly the development of 3D face recognition techniques that improve accuracy under varying conditions. Additionally, it raises concerns about privacy violations and the potential misuse of face recognition technology in law enforcement and public surveillance.