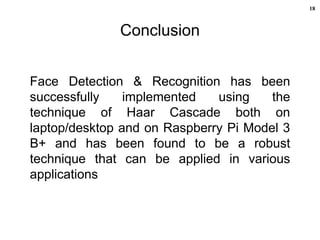
The document discusses face detection and recognition, emphasizing its significance in social interactions and various applications such as security, identification, and entertainment. It outlines the technology behind face detection using Haar cascades, its advantages and challenges, and presents a successful implementation using Python and OpenCV. Additionally, it includes details on hardware like the Raspberry Pi 3 Model B+, suitable for running these applications.


![4
Applications [8], [12], [13], [14]
Area Applications
Information Security Access Security (OS, Database)
Data Privacy (e.g. medical records)
User authentications (trading, on-line banking)
Access Management Secure Access Authentications (restricted facilities)
Permission based system
Access log or Audit Trails
Biometrics Personal identification (national IDs, passport, voter
registration, driver licenses)
Automated identity verification (boarder control)
Law Enforcement Video Surveillance,
Suspect identification
Suspect tracking ( investigation )
Simulated aging
Forensic Reconstruction of faces from remains,
Tracing missing children.
Personal Security Home video surveillance system
Expression interpretation (driver monitoring system)
Entertainment Home video game systems
Photo camera applications](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-4-320.jpg)
![5
Introduction
Face
Detection & Recognition
by
Humans
• Human brain is trained for
face detection and recognition.
Face detection and recognition
is an easy task for humans [1].
•Experimentally it has been
found that even one to three
day old babies are able to
distinguish between known
faces [2].
So how hard could it be for a computer ?](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-5-320.jpg)

![8
Face Recognition
“Face Recognition is the task
of identifying an already
detected face as a KNOWN
or UNKNOWN face, and in
more advanced cases,
TELLING EXACTLY
WHO’S IT IS ! “ [8]
Face recognition problem statement:
Given still or video images of a scene, identify or verify one or more persons in the scene
using a stored database of faces.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-8-320.jpg)
![9
Features [9]
1. Distance between the eyes
2. Width of the nose
3. Depth of the eye socket
4. Cheekbones
5. Jaw line
6. Chin
Face
Detection
Features
Extraction
Face
Recognition
How it works?
Figure: [8]](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-9-320.jpg)
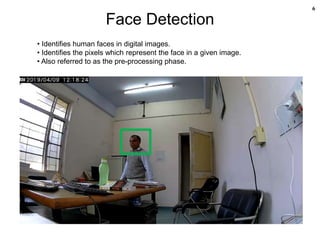
![10
Face Detection using Haar Cascades [3], [10]
• Devised by Paul Viola and Michael Jones in 2001.
• Robust and very quick.
• 15 times quicker than any technique at the time of release.
• Could be operated in real-time.
• (95% accuracy at around 17 fps.)
• Feature extraction and feature evaluation.
(Rectangular features are used)
• With a new image representation their calculation is very fast.
• Classifier training and feature selection using a method called
AdaBoost. (A long and exhaustive training process)
• A degenerate decision tree of classifiers is formed.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-10-320.jpg)
![Features [3], [10]
11
Edge Feature
Line Feature
Four basic types:
• They are easy to calculate.
• The white areas are subtracted from the black ones.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-11-320.jpg)
![12
Features Extraction [3], [10]](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-12-320.jpg)
![13
Challenges in Haar Cascades [10]
• Variations in pose Head positions, frontal view, profile
view and head tilt, facial expressions.
• Illumination Changes Light direction and intensity changes,
cluttered background, low quality
images.
• Camera Parameters Resolution, color balance etc.
• Occlusion Glasses, facial hair and makeup.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-13-320.jpg)
![14
Advantages & Disadvantages [11]
Advantages:
• High detection accuracy.
• Low false positive rate.
Disadvantages:
• Computationally complex and slow.
• Longer training time.
• Less accurate on black faces.
• Limitation in difficult lightening conditions.
• Less robust to occlusion/obstacle.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-14-320.jpg)
![15
OpenCV
Open Source Computer Vision [1]
Features:
• a library of programming functions mainly aimed at
real-time computer vision.
• Originally developed by Intel.
• The library is cross-platform free for use under the
open- source BSD license.
• OpenCV supports the deep learning frameworks
TensorFlow, Torch/PyTorch and Caffe.
• Applications are object, face and gesture recognition,
lip reading, Human- Computer Interaction (HCI),
Motion Tracking, Motion understanding, and Mobile
Robotics.](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-15-320.jpg)
![16
Raspberry Pi 3 Model B+
Features:[4]
•Broadcom BCM2837B0, Cortex-A53
(ARMv8) 64-bit SoC @ 1.4GHz
•1GB LPDDR2 SDRAM
• 2.4GHz and 5GHz IEEE 802.11.b/g/n/ac
wireless LAN, Bluetooth 4.2, BLE
• Gigabit Ethernet over USB 2.0
(maximum throughput 300 Mbps)
• Extended 40-pin GPIO header
• Full-size HDMI
• 4 USB 2.0 ports
• CSI camera port for connecting a
Raspberry Pi camera
• DSI display port for connecting a
Raspberry Pi touchscreen display
• 4-pole stereo output and composite
video port
• Micro SD port for loading your operating
system and storing data
• 5V/2.5A DC power input
• Power-over-Ethernet (PoE) support
(requires separate PoE HAT)](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-16-320.jpg)
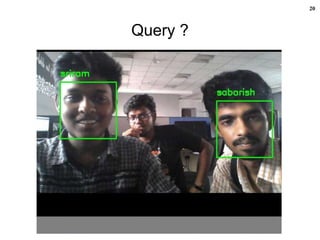
![17
Live Demo
on
Face Detection & Recognition
using
Python + OpenCV [5], [6], [7]
(Laptop/Desktop/Raspberry Pi Model 3 B+)](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-17-320.jpg)
![19
References[1] https://docs.opencv.org/2.4/modules/contrib/doc/facerec/facerec_tutorial.html#tu06
[Accessed: 22-June-2019]
[2] Chiara Turati, Viola Macchi Cassia, F. S., and Leo, I. Newborns face recognition:
Role of inner and outer facial features. Child Development 77, 2 (2006), 297– 311.
[3] https://docs.opencv.org/3.3.0/d7/d8b/tutorial_py_face_detection.html
[Accessed: 22-June-2019]
[4] https://www.raspberrypi.org/products/raspberry-pi-3-model-b-plus/
[Accessed: 22-June-2019]
[5] https://www.hackster.io/sriram17ei/facial-recognition-opencv-python-9bc724
[Accessed: 22-June-2019]
[6] https://github.com/sriram251/-face_recognition
[Accessed: 22-June-2019]
[7] https://github.com/opencv/opencv
[Accessed: 22-June-2019]
[8] https://www.slideshare.net/vaishalibansalbhati/face-recognition-
vaishali?qid=3a4a0ba2-493d-470c-8156-ad157f2bec94&v=&b=&from_search=8
[Accessed: 22-June-2019]
[9] https://www.slideshare.net/awesomearjun10/face-detection-attendance-system-by-
arjun-sharma?qid=b252b129-b4e7-458a-ab74-7d8ab1e0dc3f&v=&b=&from_search=1
[Accessed: 22-June-2019]
[10] https://www.slideshare.net/AbhiroopGhatak/automated-face-detection-
system?qid=8803eb10-e5a6-4e27-afc0-9eab148ec171&v=&b=&from_search=1
[Accessed: 22-June-2019]](https://image.slidesharecdn.com/facedetectionandrecognition-190701012850/85/Face-detection-and-recognition-19-320.jpg)