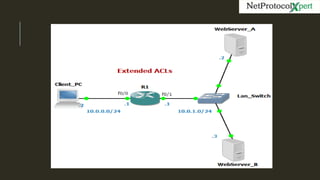
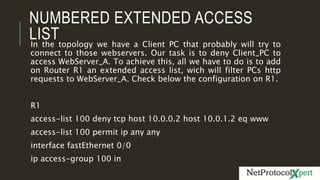
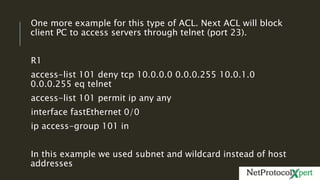
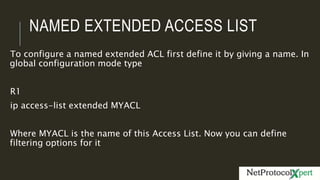
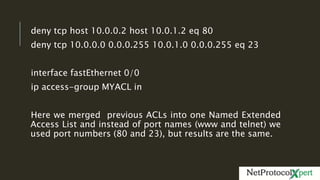
Extended access lists allow filtering of traffic based on source and destination IP addresses and port numbers. The document provides an example of an extended access list configured on Router R1 to deny HTTP requests from client PC 10.0.0.2 to web server 10.0.1.2. It also shows another example using subnets to deny telnet access. Finally, it demonstrates how to configure a named extended access list to filter both HTTP and telnet traffic from the client PC.