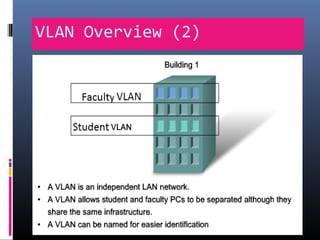
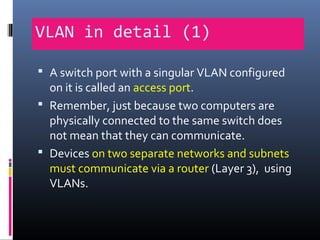
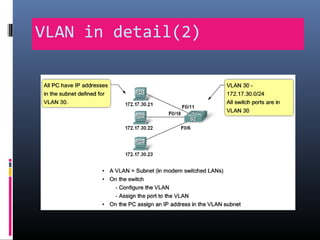
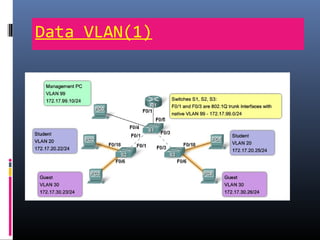
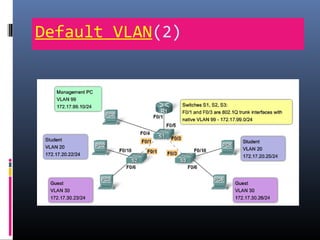
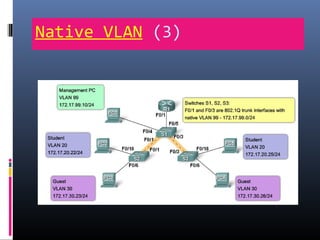
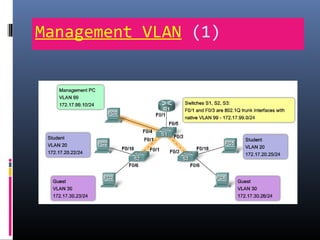
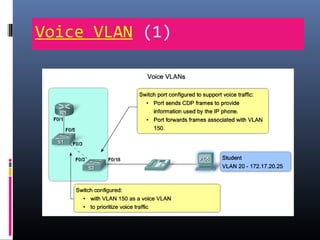
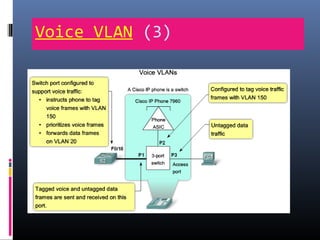
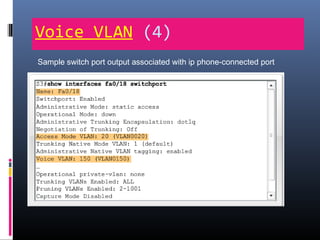
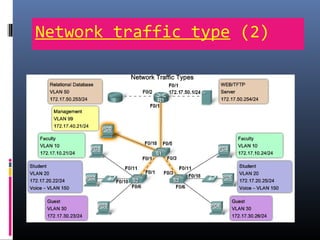
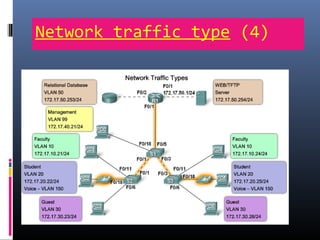
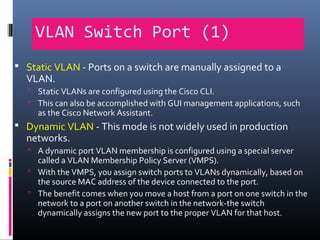
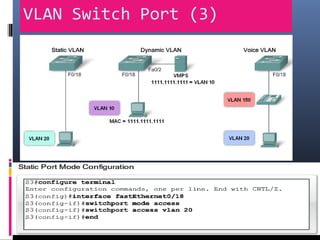
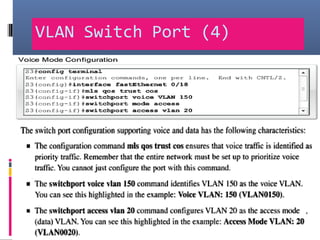
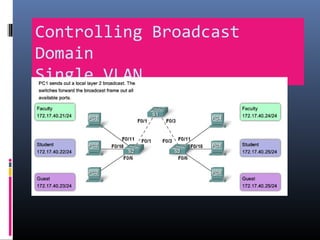
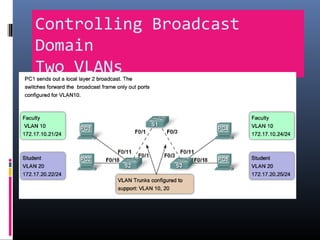
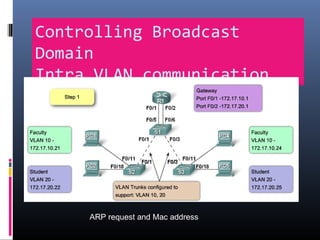
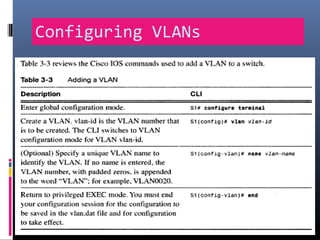
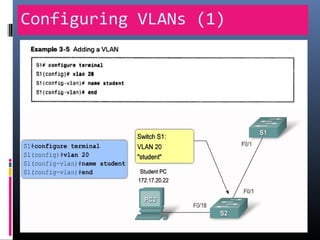
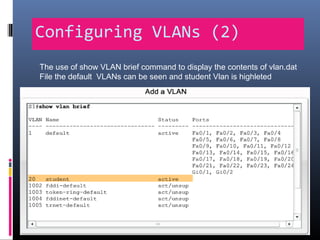
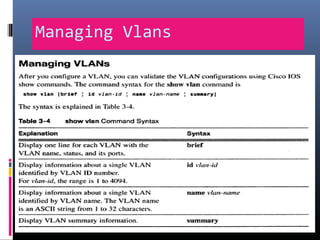
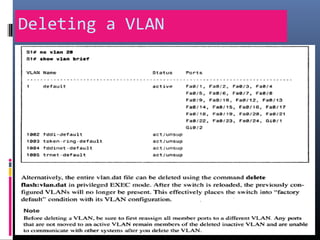
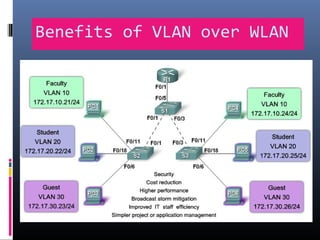
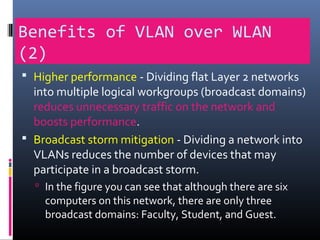
This document provides an overview of virtual local area networks (VLANs). It begins with an introduction to VLANs, explaining that they allow devices to communicate as if on the same physical LAN even if they are on different physical LANs. The document then covers VLAN types including data, default, native and voice VLANs. It also discusses VLAN switch ports, managing VLANs, and the benefits of VLANs over wireless local area networks. In conclusion, it states that VLANs segment broadcast domains to improve LAN performance and manageability while reducing costs.