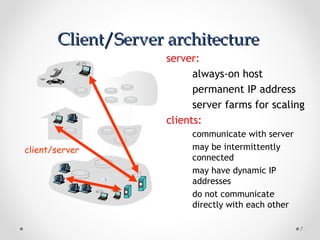
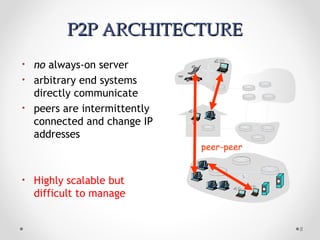
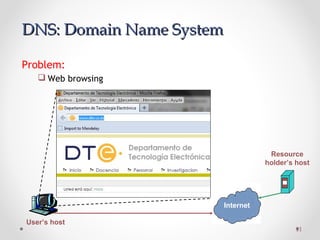
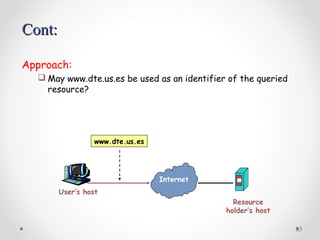
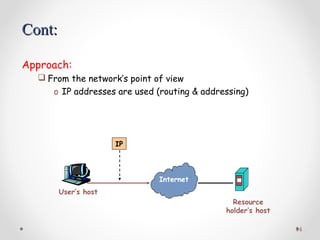
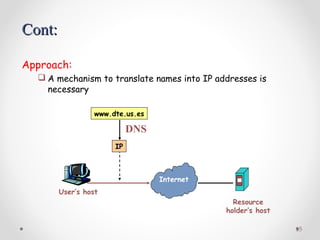
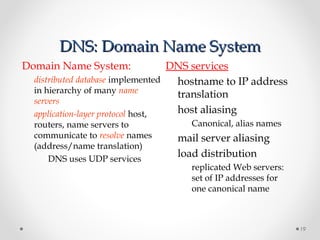
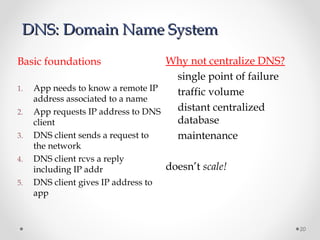
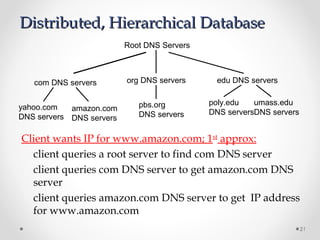
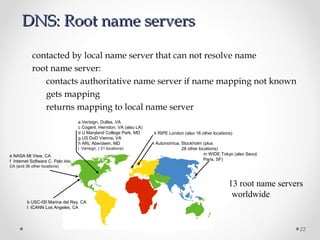
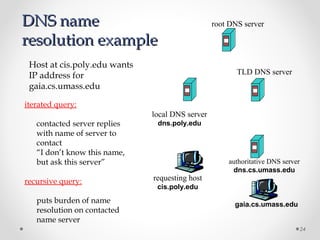
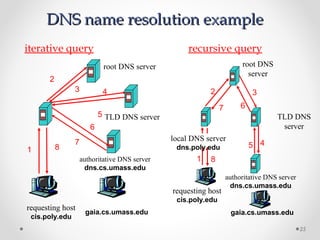
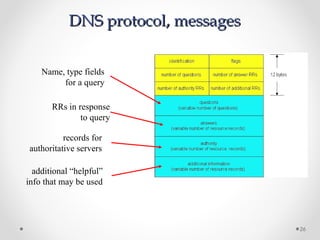
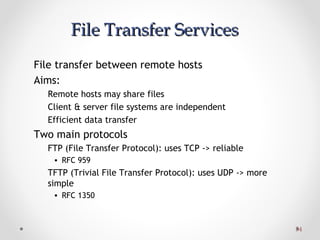
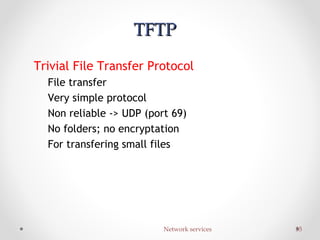
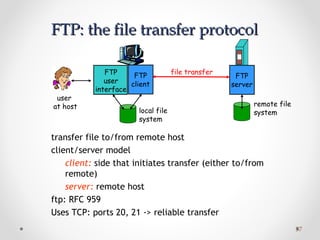
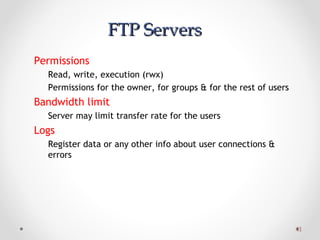
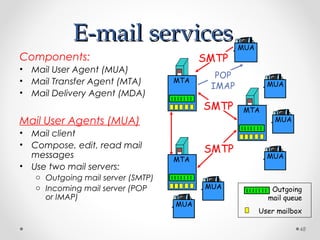
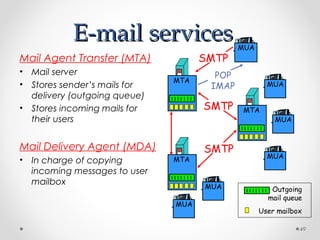
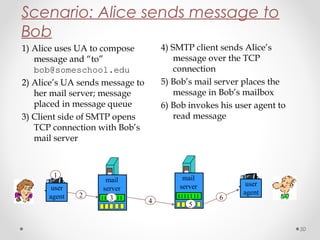
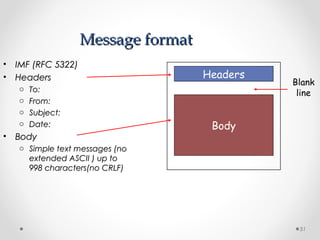
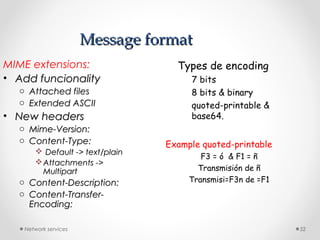
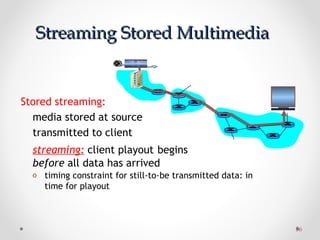
The document discusses various common network services including domain name servers (DNS), remote access services like SSH and Telnet, file transfer services like FTP and TFTP, email services using SMTP, POP and IMAP, and streaming services. It describes the client-server and peer-to-peer architectures used by these services and provides details on protocols, components, and how many of the services work at a high level.