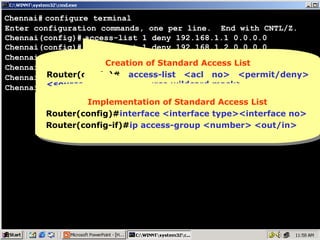
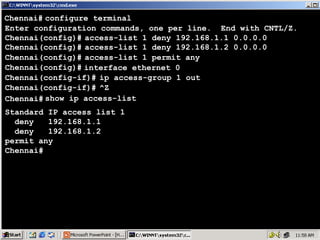
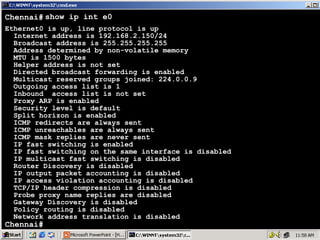
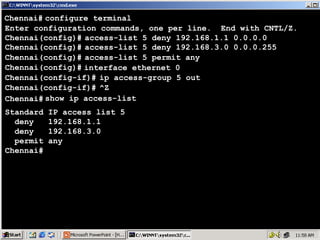
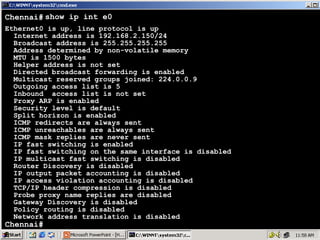
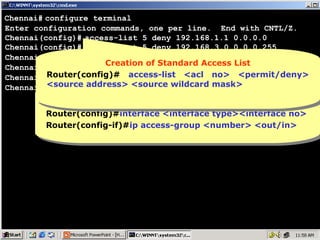
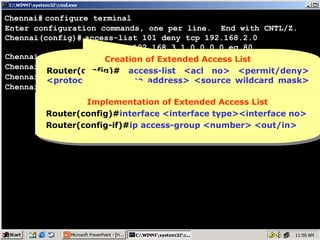
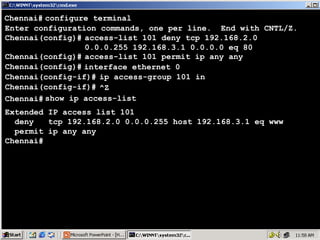
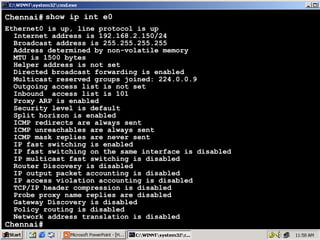
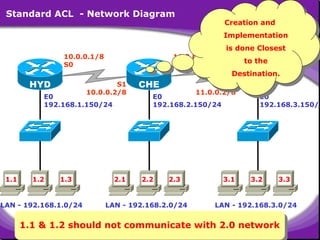
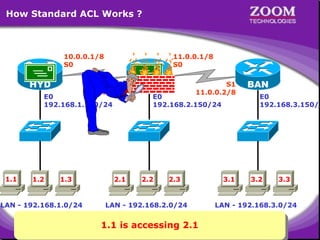
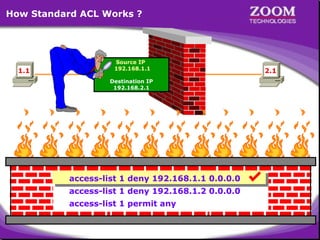
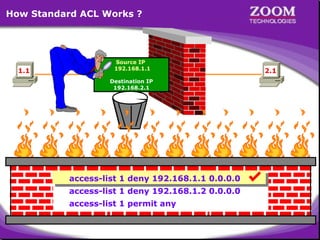
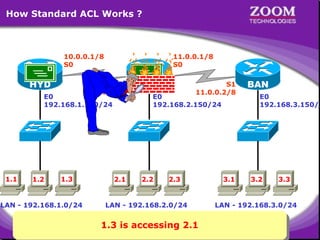
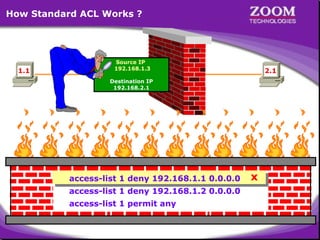
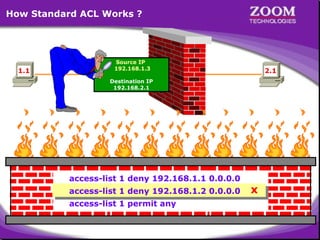
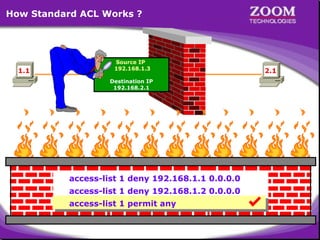
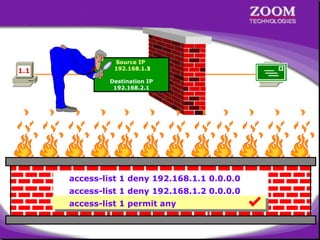
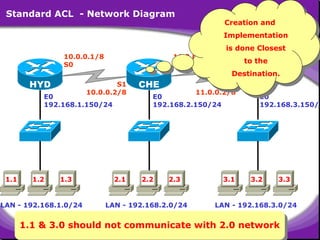
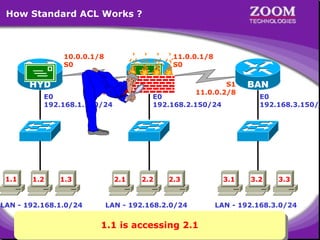
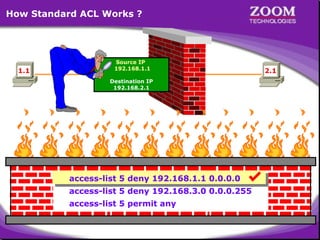
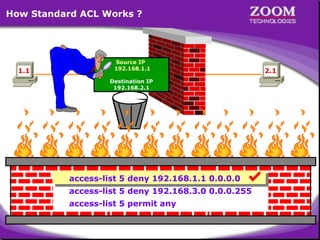
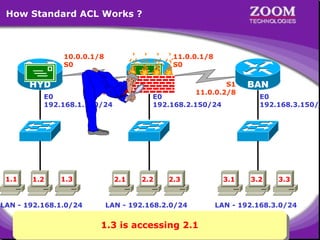
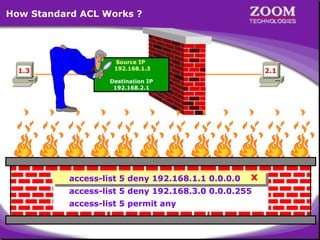
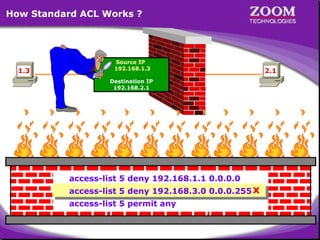
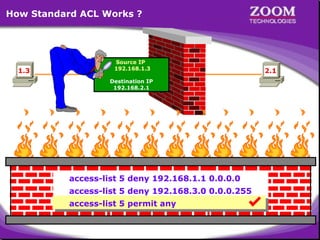
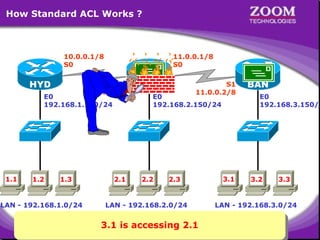
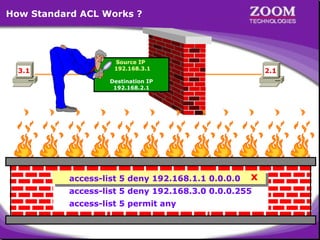
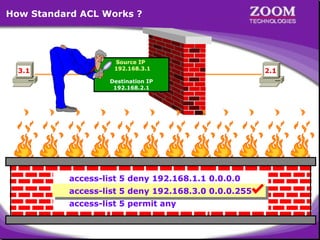
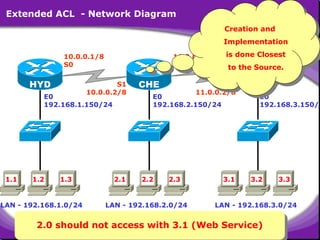
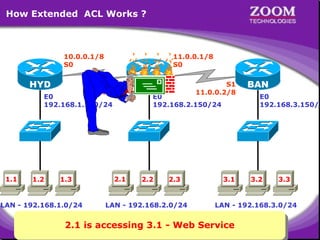
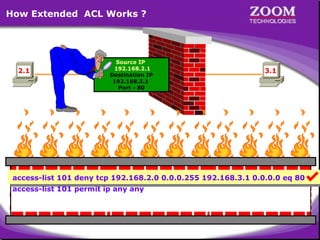
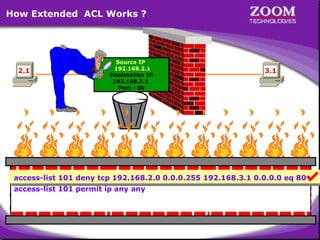
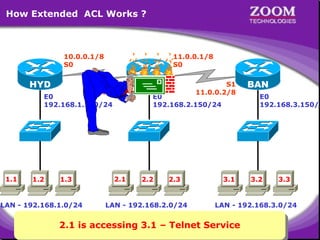
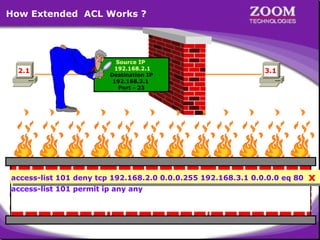
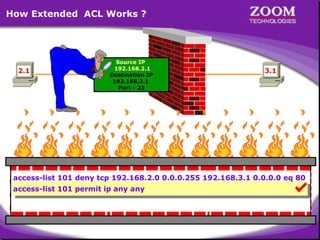
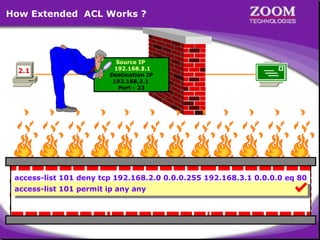
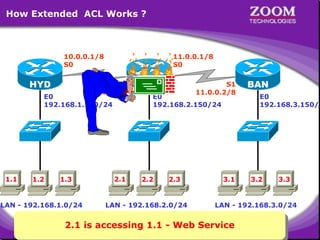
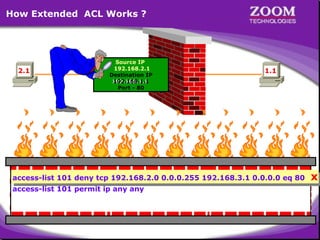
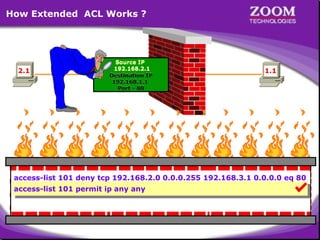
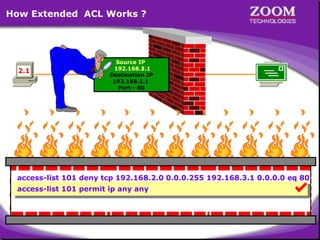
The document outlines rules for access control lists (ACLs) in networking, stating that all deny statements must precede permit statements and that each interface can have one ACL per direction. It describes standard ACLs and their function in controlling traffic between different IP networks while emphasizing that they operate in a sequential manner without the ability to edit individual statements once created. Additionally, the document details examples of ACL configurations for specific source and destination IP pairs, illustrating how access restrictions are implemented.






![Microsoft Windows 2000 [Version 5.00.2195]
(C) Copyright 1985-2000 Microsoft Corp.
C:> telnet 192.168.1.150
Connecting .....
================================
Welcome to Hyderabad Router
================================
User Access Verification
password : ****
Hyderabad> enable
password : ****
Hyderabad# show ip route
Gateway of last resort is not set
C
10.0.0.0/8 is directly connected, Serial0
R
11.0.0.0/8 [120/1] via 10.0.0.2, 00:00:25, Serial0
C
192.168.1.0/24 is directly connected, Ethernet0
R
192.168.2.0/24 [120/1] via 10.0.0.2, 00:00:25, Serial0
R
192.168.3.0/24 [120/2] via 10.0.0.2, 00:00:25, Serial0
Hyderabad#
41](https://image.slidesharecdn.com/accesscontrollist1-140102214611-phpapp01/85/Access-Control-List-1-41-320.jpg)
![Microsoft Windows 2000 [Version 5.00.2195]
(C) Copyright 1985-2000 Microsoft Corp.
C:> telnet 192.168.2.150
Connecting .....
================================
Welcome to Chennai Router
================================
User Access Verification
password : ****
Chennai> enable
password : ****
Chennai# show ip route
Gateway of last resort is not set
C
10.0.0.0/8 is directly connected, Serial1
C
11.0.0.0/8 is directly connected, Serial0
R
192.168.1.0/24 [120/1] via 10.0.0.1, 00:00:01, Serial1
C
192.168.2.0/24 is directly connected, Ethernet0
R
192.168.3.0/24 [120/1] via 11.0.0.2, 00:00:12, Serial0
Chennai#
42](https://image.slidesharecdn.com/accesscontrollist1-140102214611-phpapp01/85/Access-Control-List-1-42-320.jpg)
![Microsoft Windows 2000 [Version 5.00.2195]
(C) Copyright 1985-2000 Microsoft Corp.
C:> telnet 192.168.3.150
Connecting .....
================================
Welcome to Banglore Router
================================
User Access Verification
password : ****
Banglore> enable
password : ****
Banglore# show ip route
Gateway of last resort is not set
R
10.0.0.0/8 [120/1] via 11.0.0.1, 00:00:04, Serial1
C
11.0.0.0/8 is directly connected, Serial1
R
192.168.1.0/24 [120/2] via 11.0.0.1, 00:00:04, Serial1
R
192.168.2.0/24 [120/1] via 11.0.0.1, 00:00:04, Serial1
C
192.168.3.0/24 is directly connected, Ethernet0
Banglore#
43](https://image.slidesharecdn.com/accesscontrollist1-140102214611-phpapp01/85/Access-Control-List-1-43-320.jpg)
![Microsoft Windows 2000 [Version 5.00.2195]
(C) Copyright 1985-2000 Microsoft Corp.
C:> telnet 192.168.2.150
Connecting .....
================================
Welcome to Chennai Router
================================
User Access Verification
password : ****
Chennai> enable
password : ****
Chennai# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Chennai(config)# interface serial 1
Chennai(config-if)# ip address 10.0.0.2 255.0.0.0
Chennai(config-if)# no shut
Chennai(config-if)# encapsulation hdlc
Chennai(config-if)# interface serial 0
Chennai(config-if)# ip address 11.0.0.1 255.0.0.0
Chennai(config-if)# no shut
Chennai(config-if)# encapsulation hdlc
44](https://image.slidesharecdn.com/accesscontrollist1-140102214611-phpapp01/85/Access-Control-List-1-44-320.jpg)