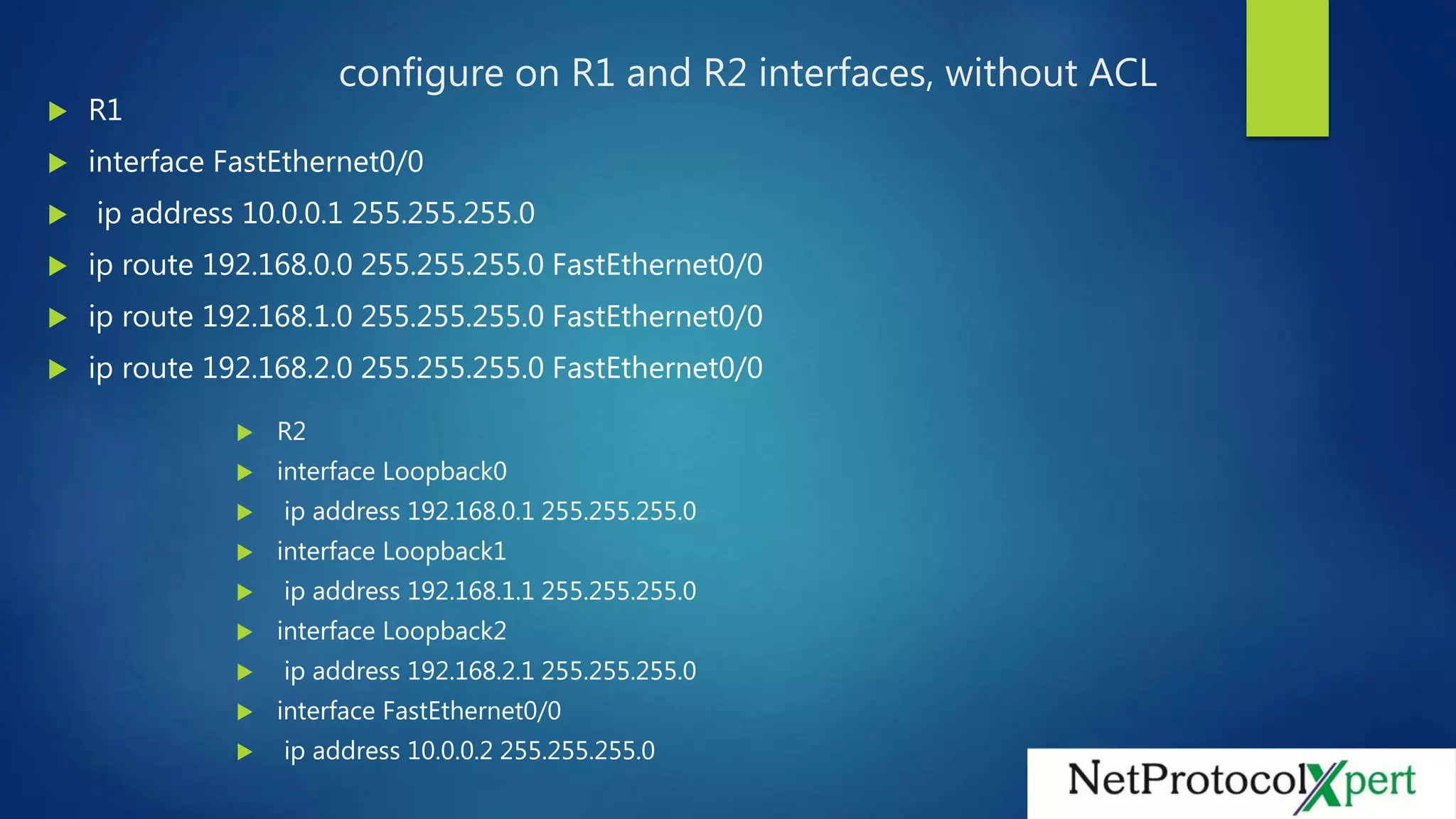
The document discusses configuring a standard access control list (ACL) on router R1 to filter traffic from router R2's loopback interfaces. The ACL denies traffic from R2's 192.168.0.0 network and permits traffic from 192.168.1.0. Applying the ACL to R1's interface confirms that pings are dropped from 192.168.0.1 but allowed from 192.168.1.1.