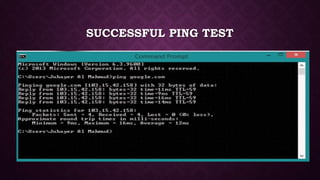
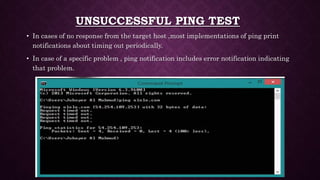
Ping is a network utility that checks the reachability of an IP address and measures round trip time for messages. It operates by sending ICMP echo requests and can indicate errors, packet loss, and latency issues. The 'ping of death' is a historical denial of service attack involving oversized ICMP packets that could cause system crashes, prompting vendors to issue patches.