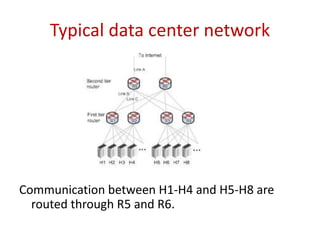
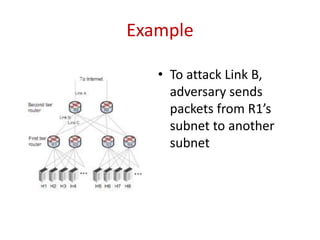
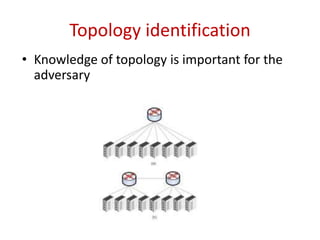
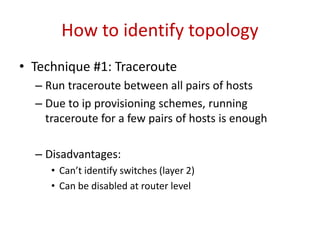
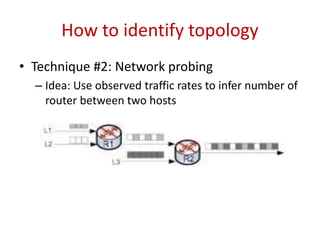
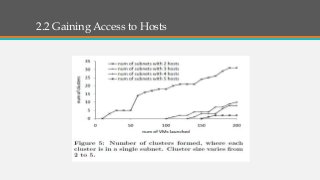
The document describes a new type of denial-of-service (DoS) attack that can occur in cloud data centers due to their underprovisioned nature. It identifies that by saturating the network bandwidth between hosts in different subnets, an attacker can target specific applications by congesting the uplink connecting the targeted subnet. It then proposes two approaches for an attacker to identify the network topology and determine a suitable bottleneck link to attack. Finally, it shows that through rapidly launching many virtual machines, an attacker can quickly gain access to a sufficient number of hosts connected to the targeted router subnet to launch an effective bandwidth saturation attack.