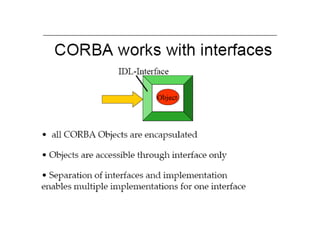
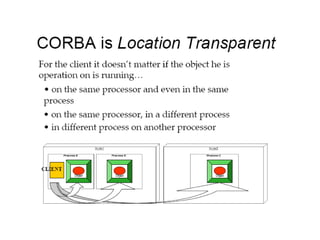
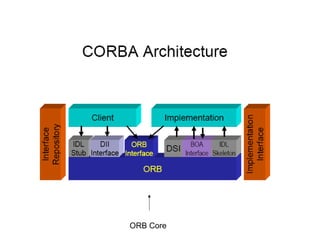
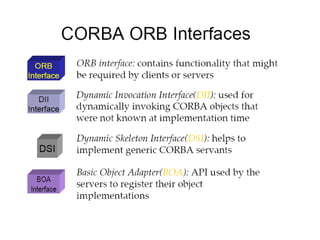
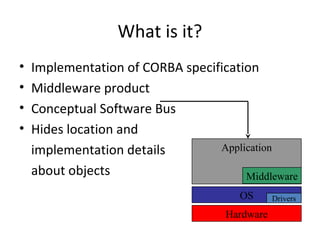
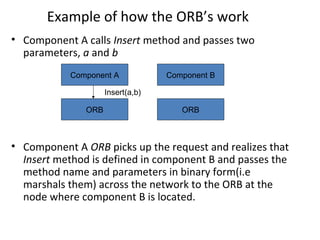
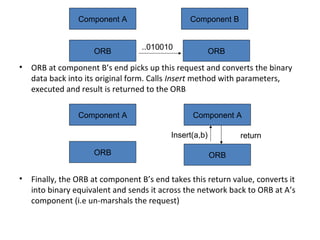
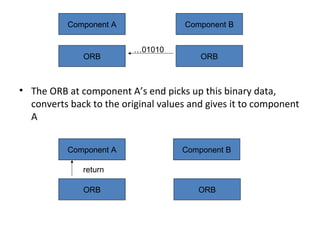
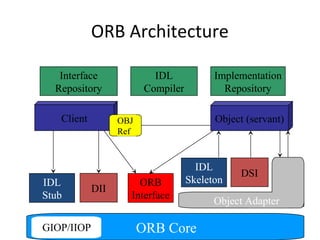
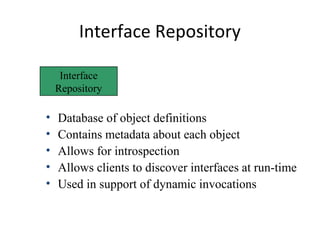
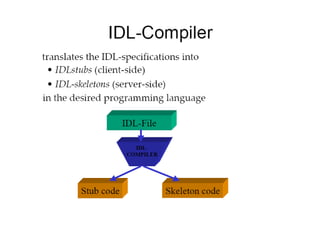
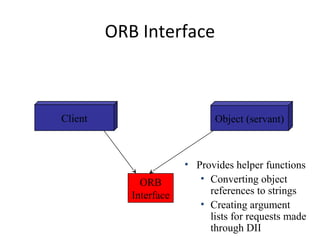
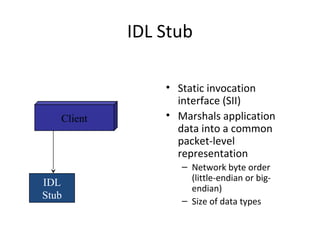
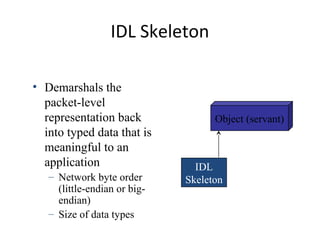
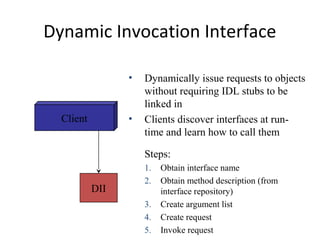
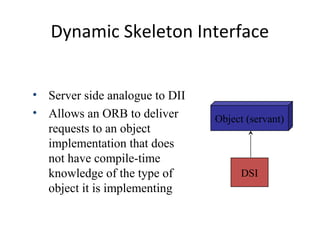
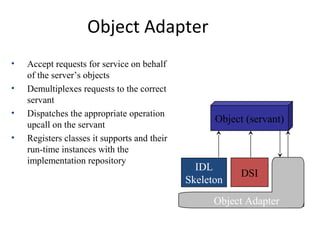
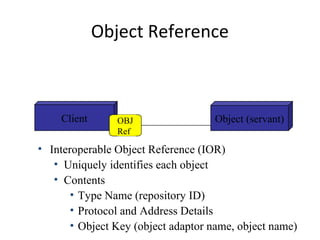
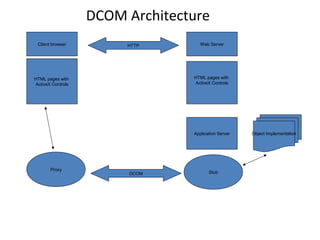
CORBA and DCOM are specifications for distributed computing that allow objects to communicate across a network. CORBA uses an Object Request Broker (ORB) as middleware to locate and invoke remote objects transparently. It defines an Interface Definition Language (IDL) and supports location transparency. DCOM is Microsoft's version that extends COM to allow components to interact remotely. It uses proxies on the client side and stubs on the server side to marshal requests and responses.