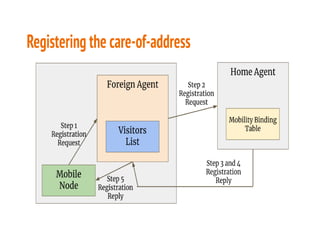
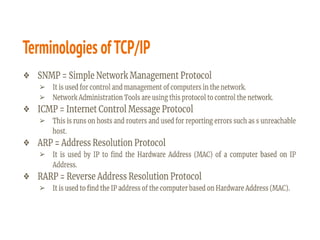
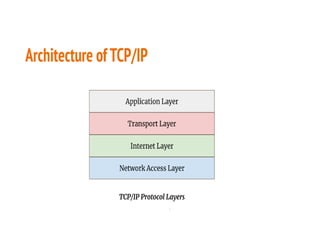
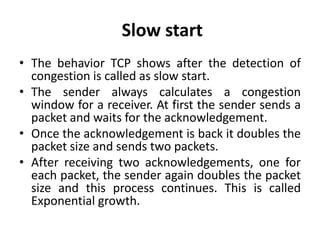
This document discusses the key topics covered in Unit II of a course on Mobile Computing. It covers Mobile Internet Protocol (Mobile IP) which allows users to move between networks while keeping the same IP address. The key components of Mobile IP are described including the mobile node, home agent, foreign agent, and care-of address. It also discusses how packet delivery works when the mobile node moves to a foreign network using tunneling. Improving TCP performance over wireless networks is also covered, including congestion control, slow start, fast retransmission, and indirect TCP which uses the access point as a proxy.