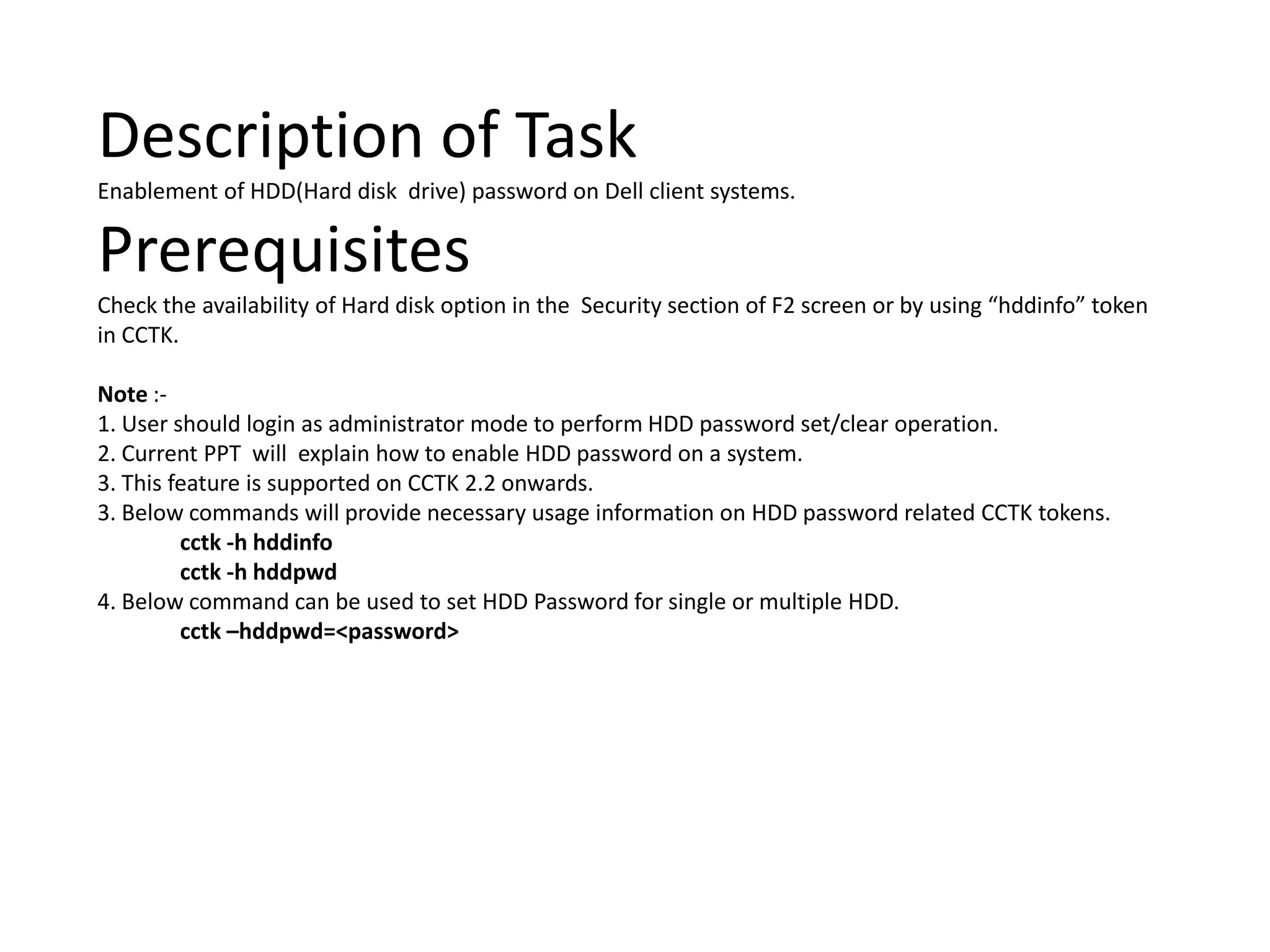
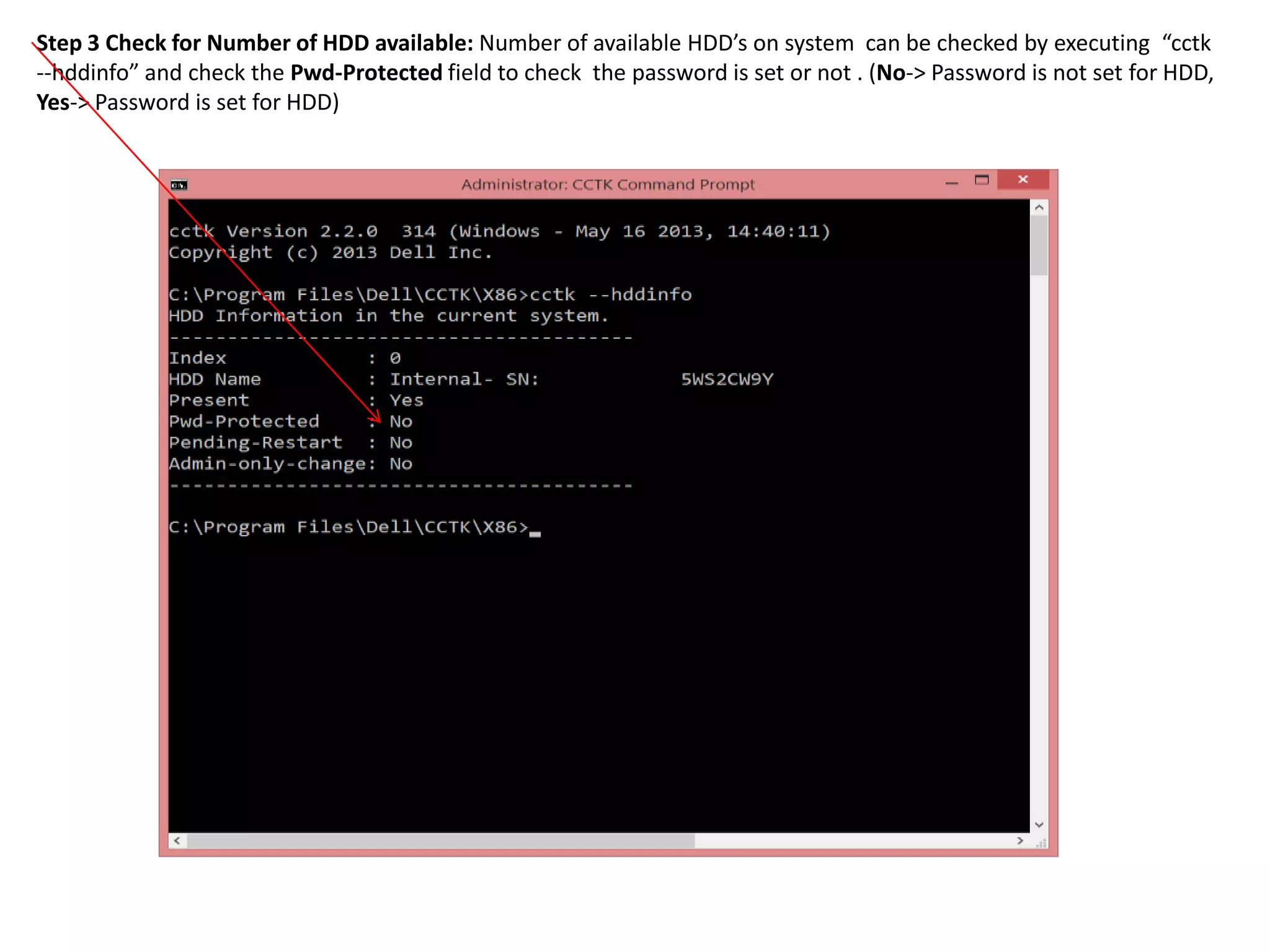
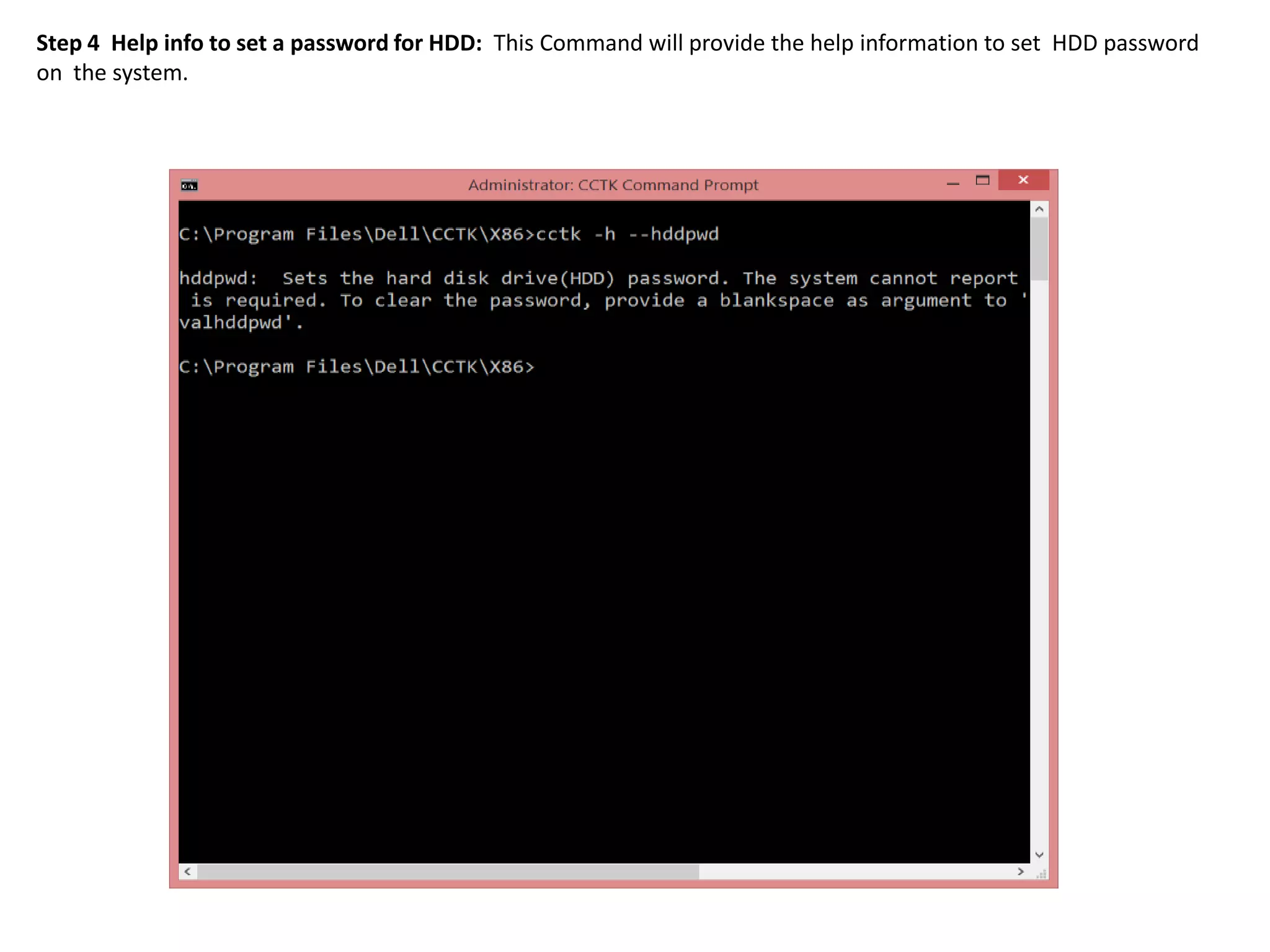
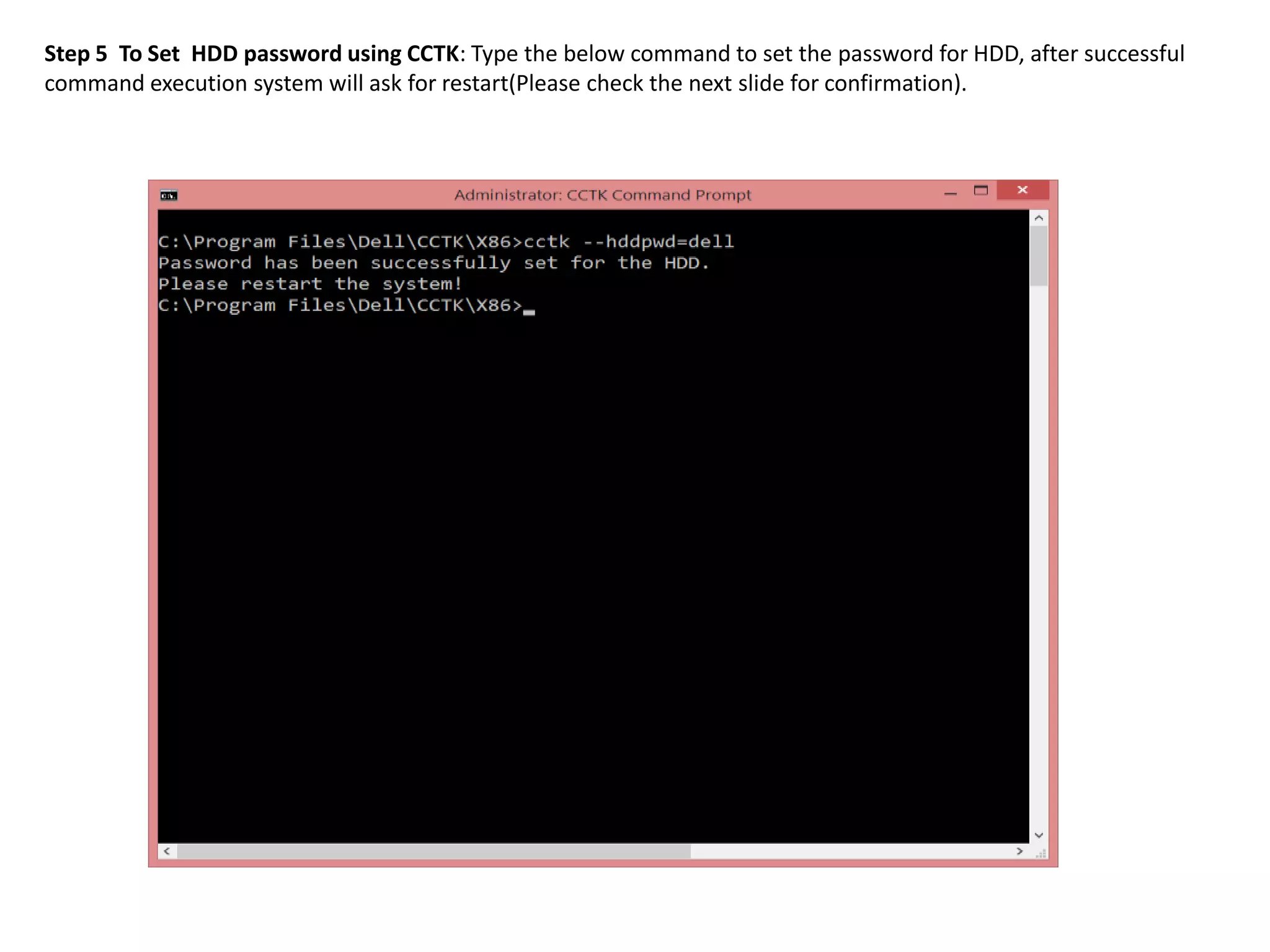
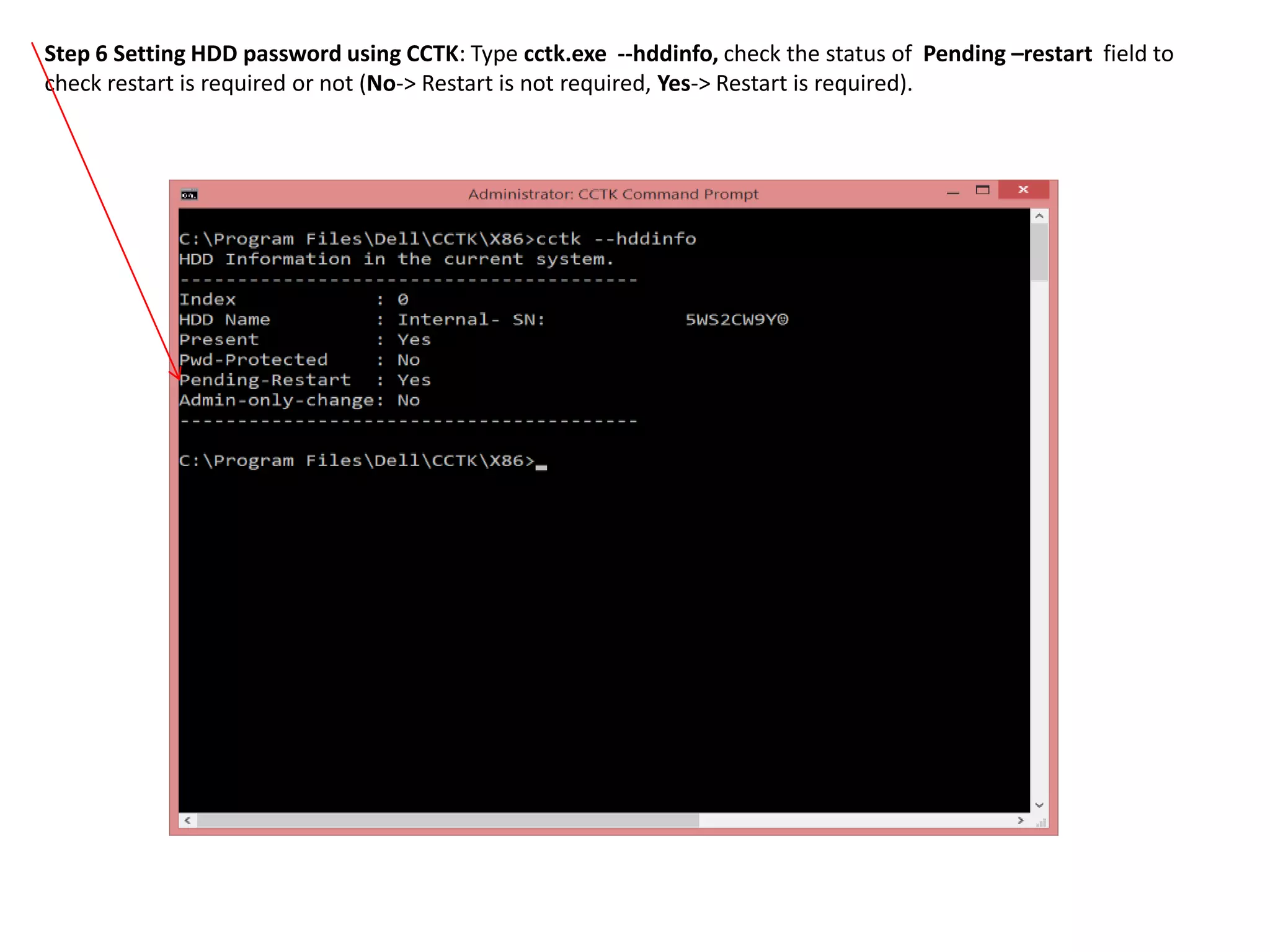
1. This document describes how to enable and disable hard disk drive (HDD) passwords on Dell client systems using the Client Configuration Toolkit (CCTK).
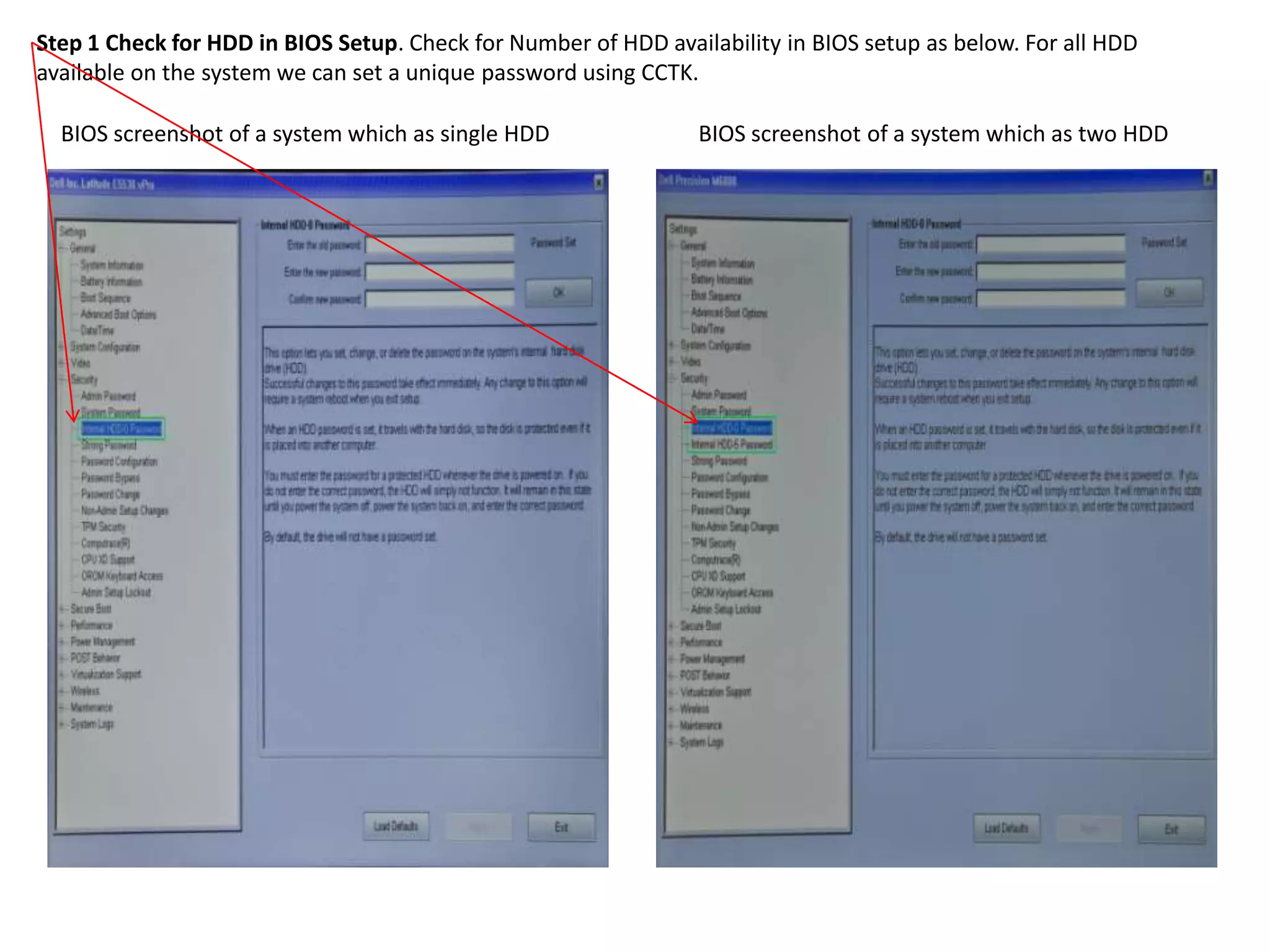
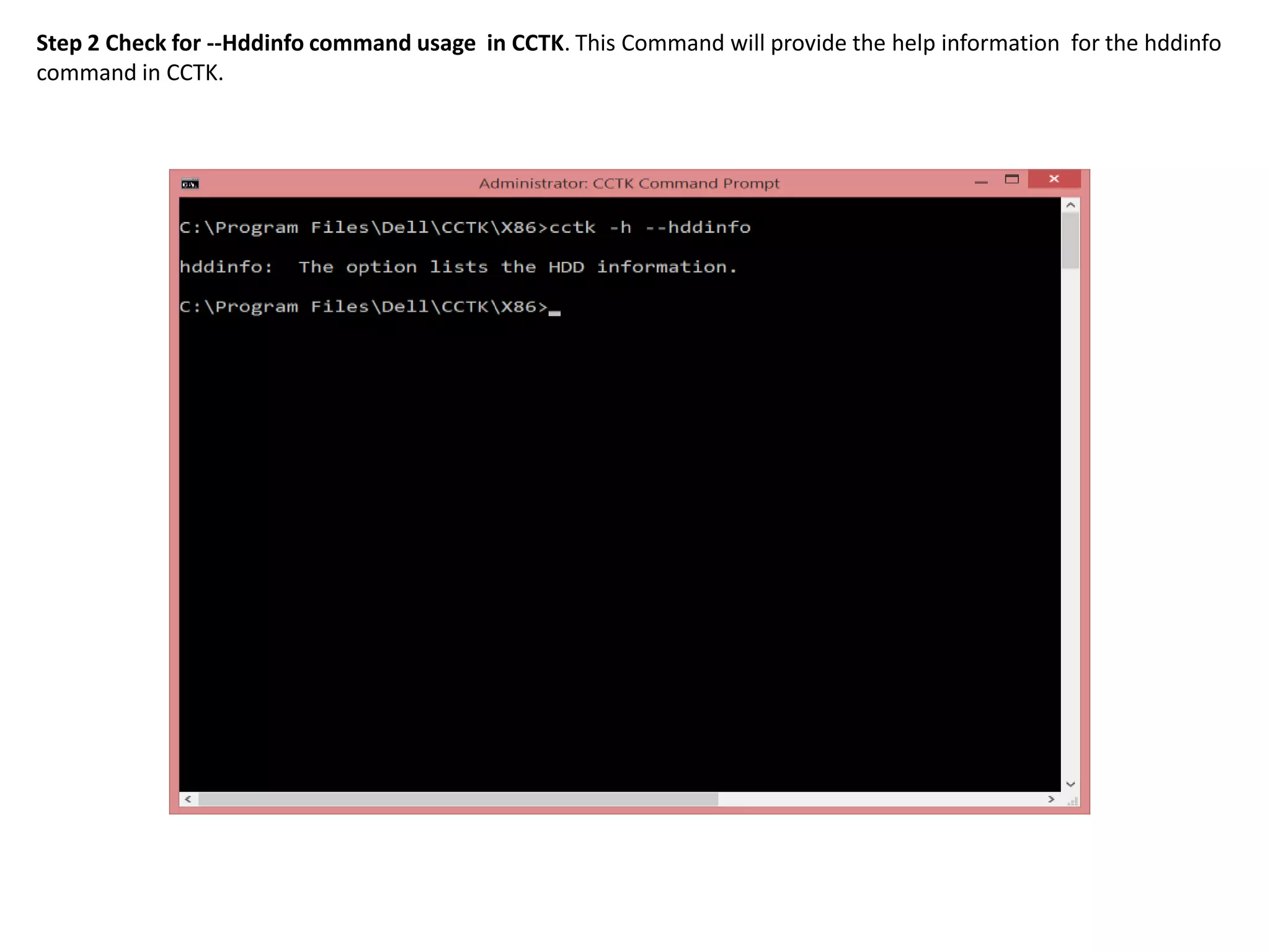
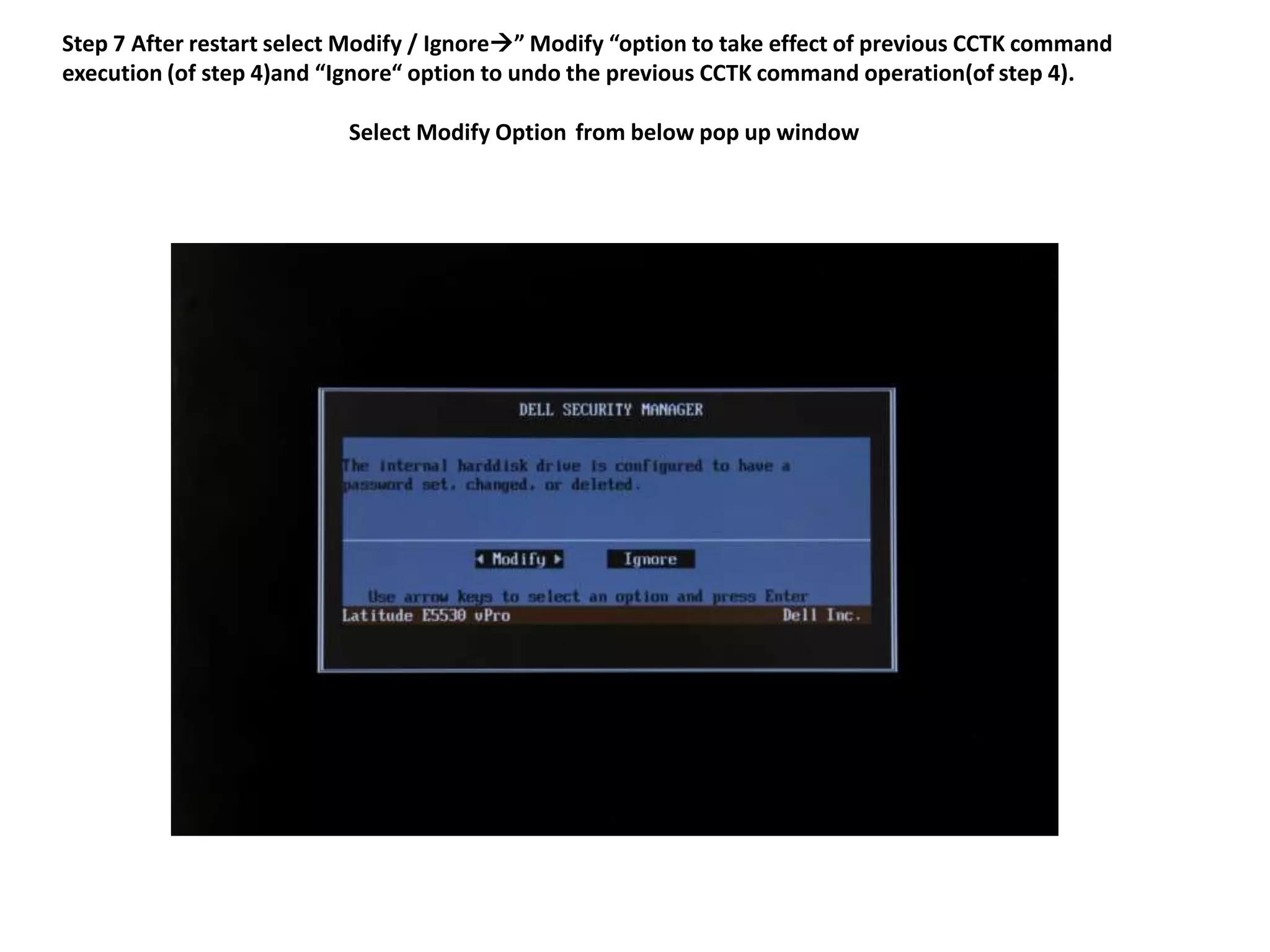
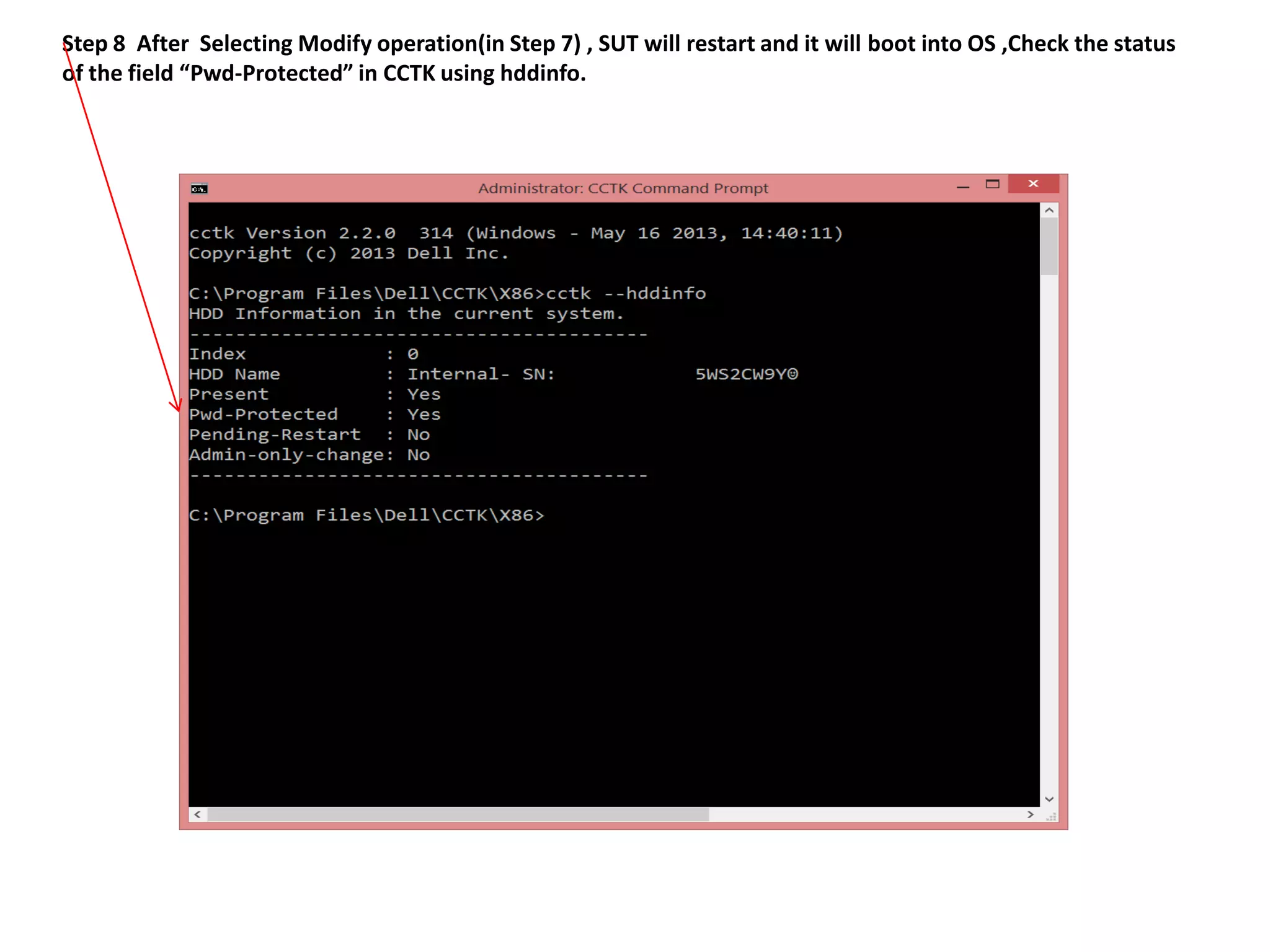
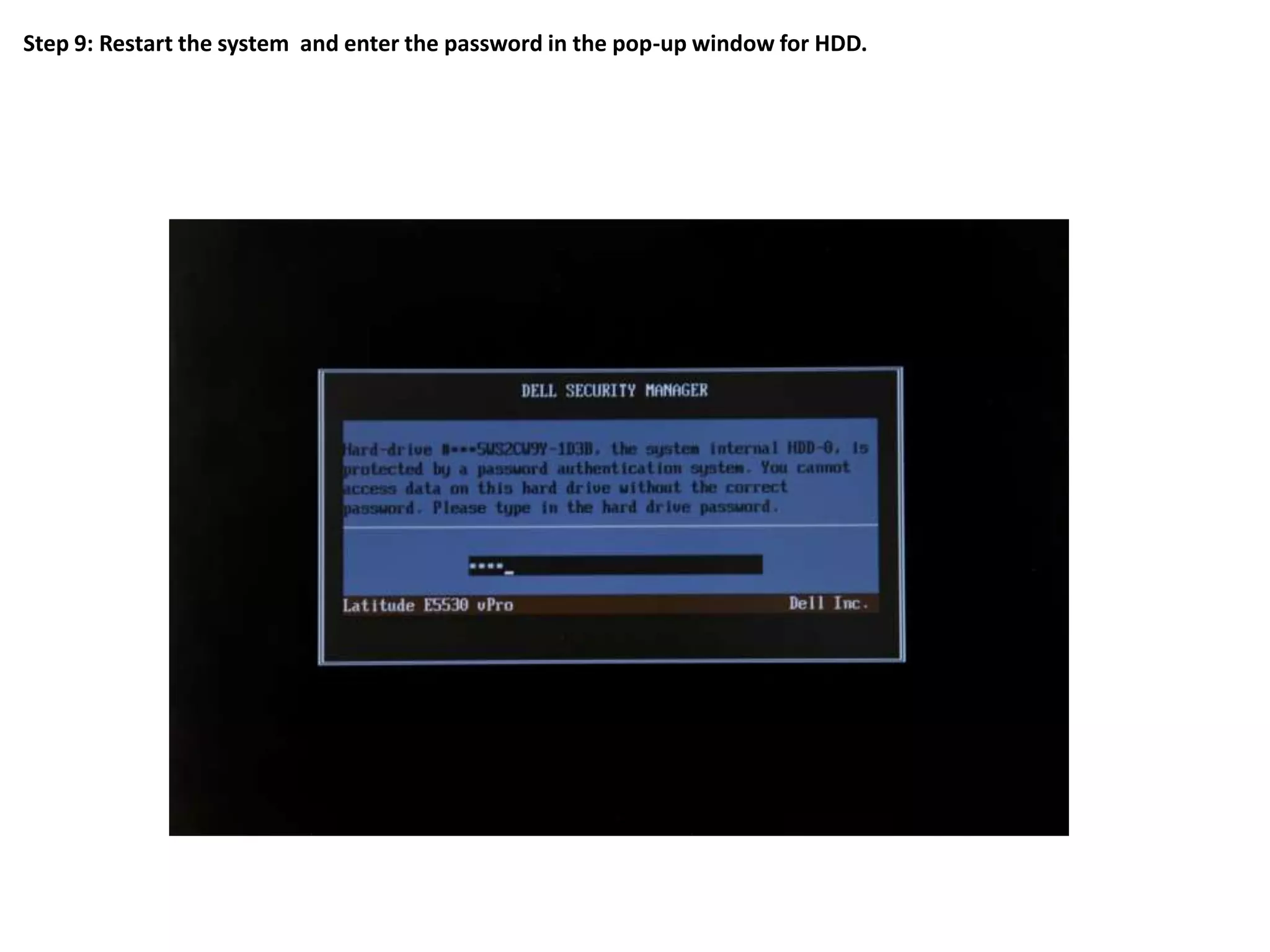
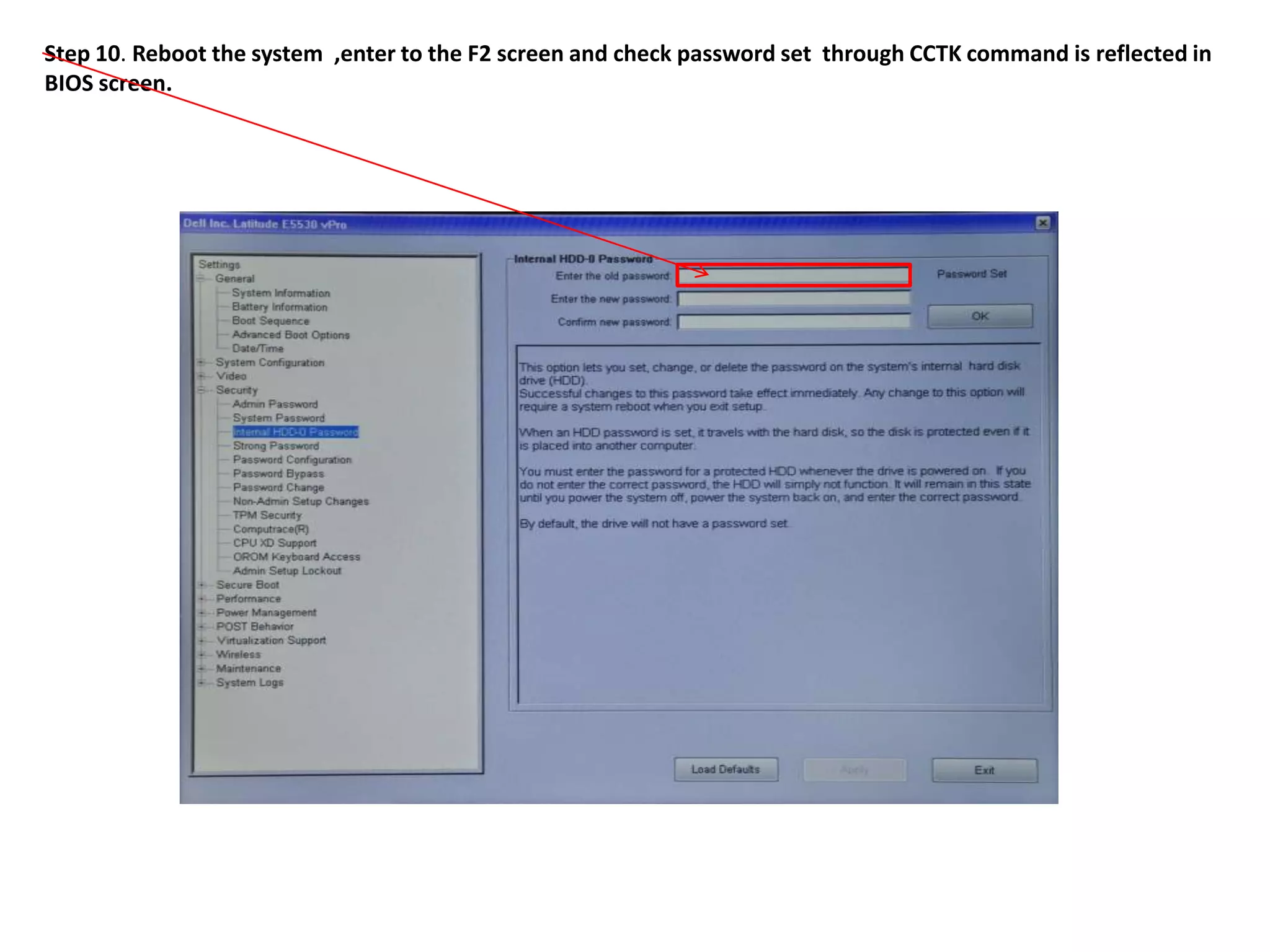
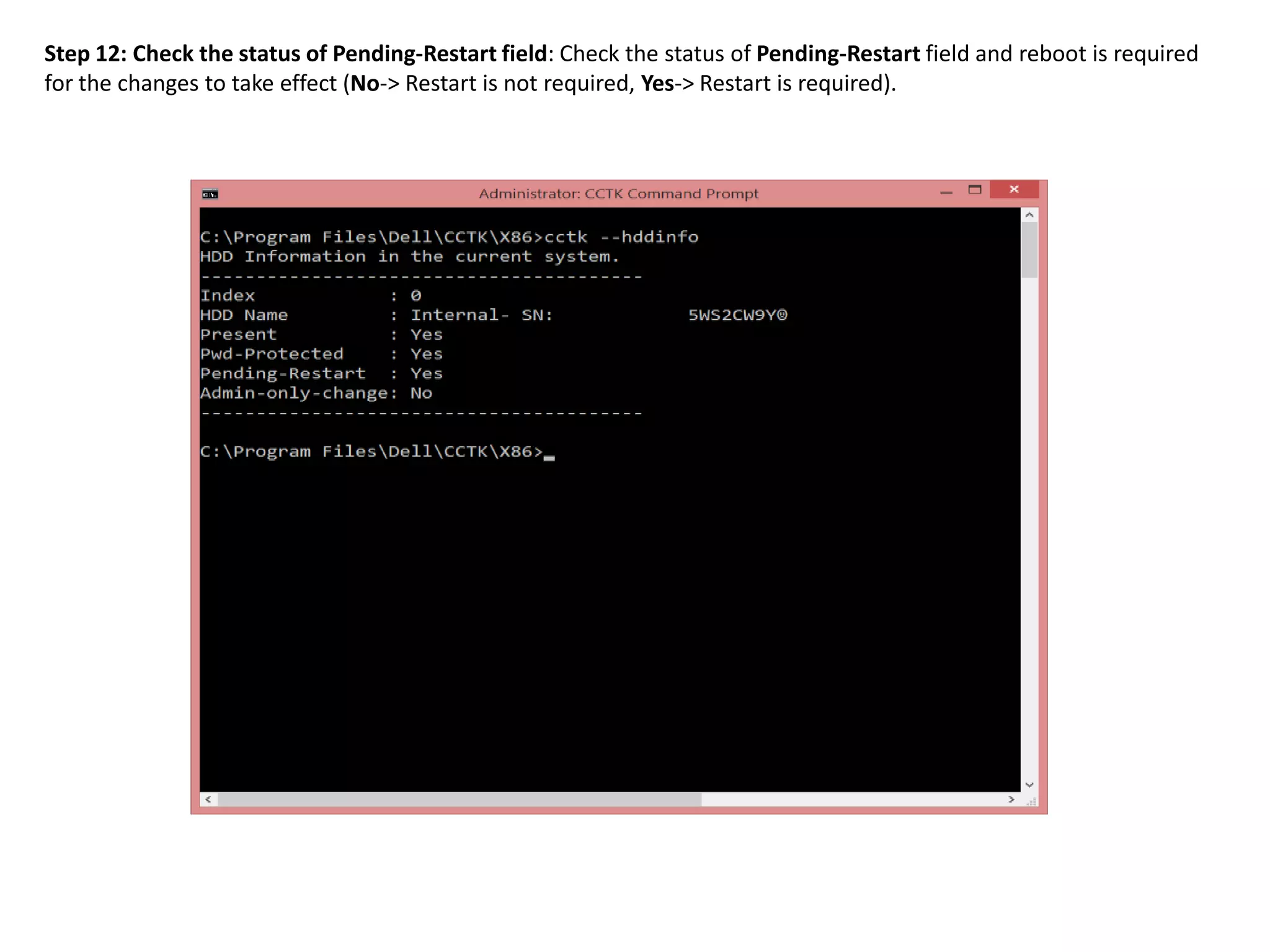
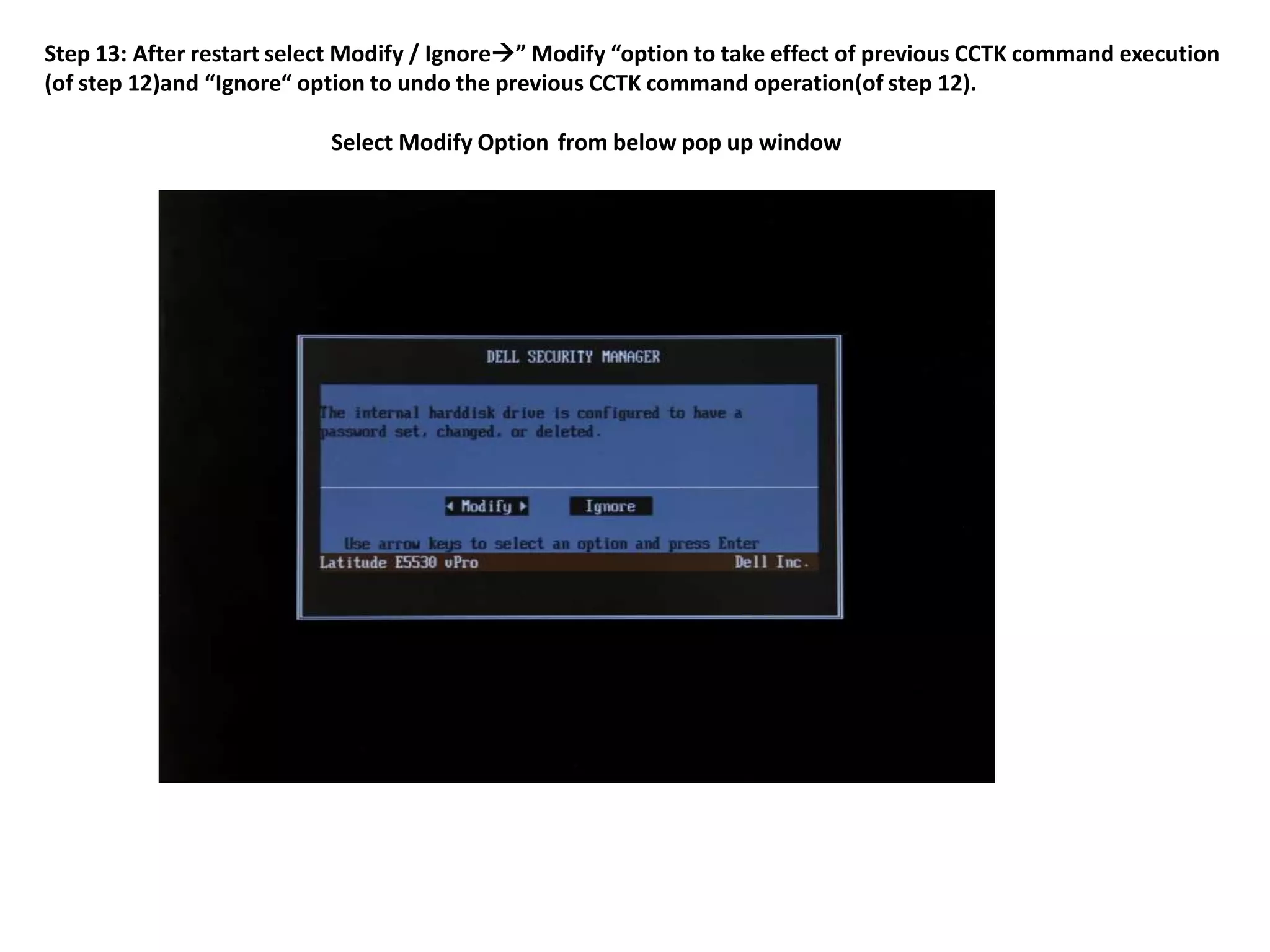
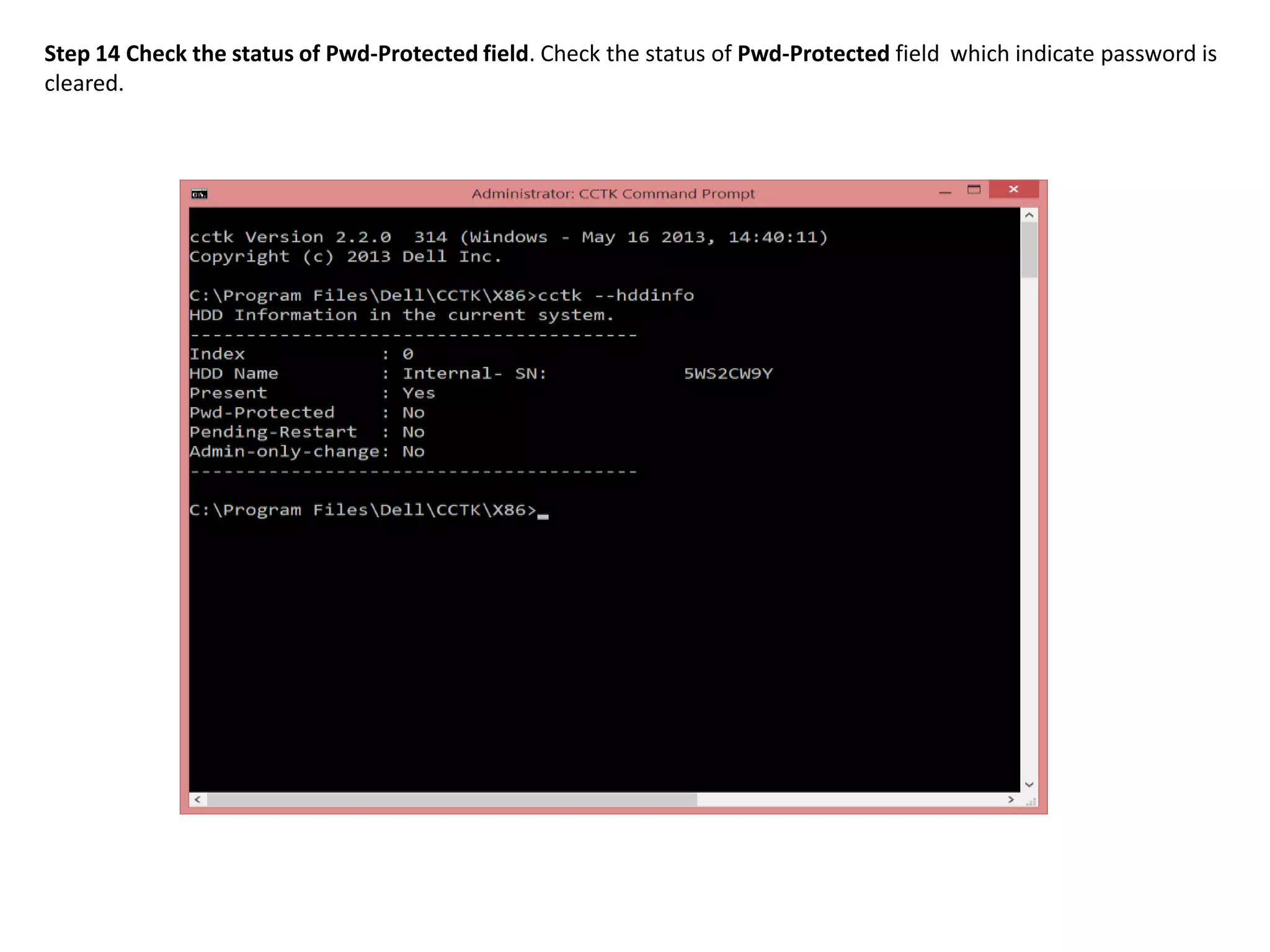
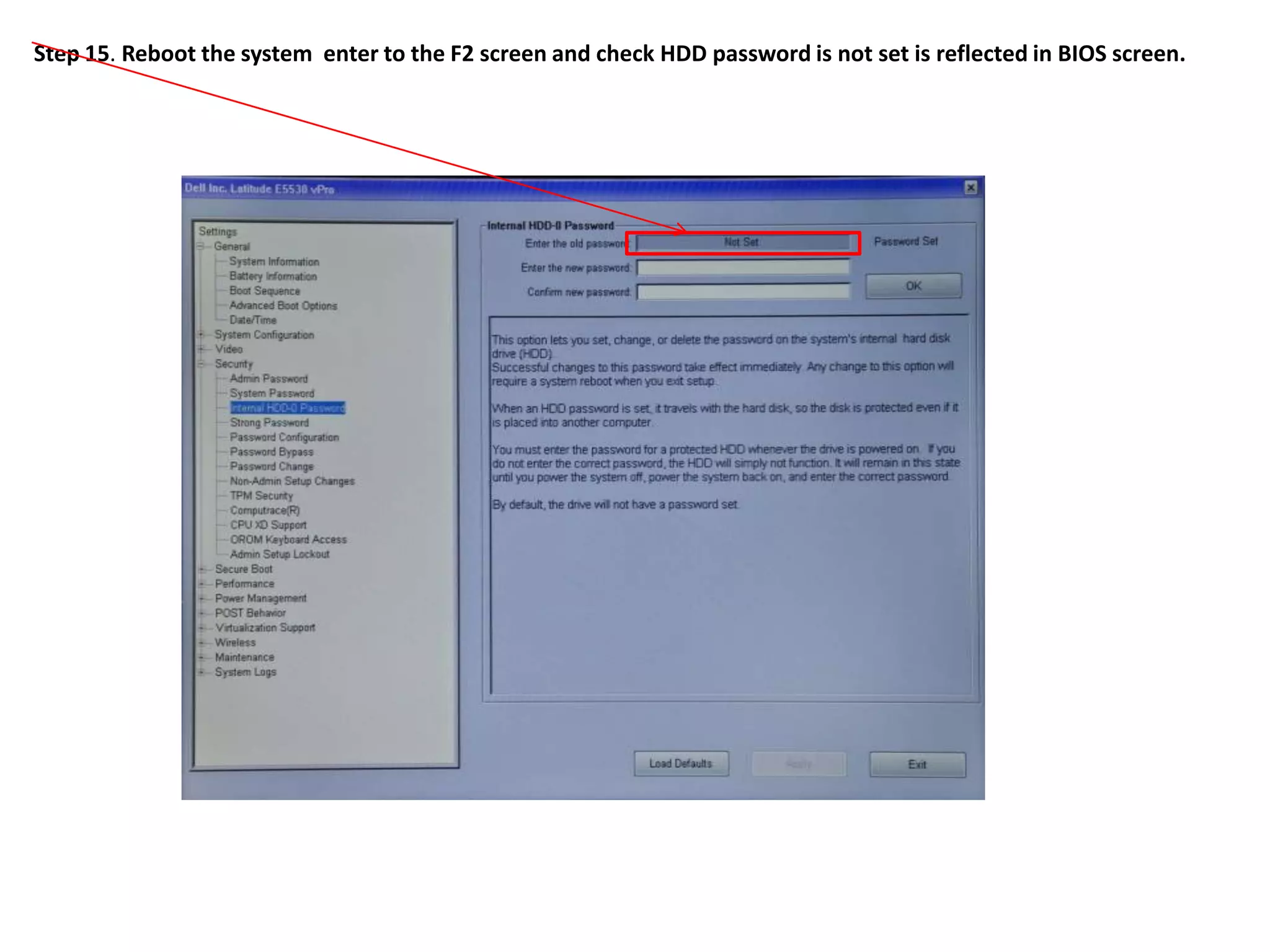
2. The steps include checking for HDD availability in the BIOS, using the "hddinfo" and "hddpwd" CCTK commands to view HDD details and set passwords, rebooting the system for changes to take effect, and verifying passwords are set properly in the BIOS and through additional CCTK commands.
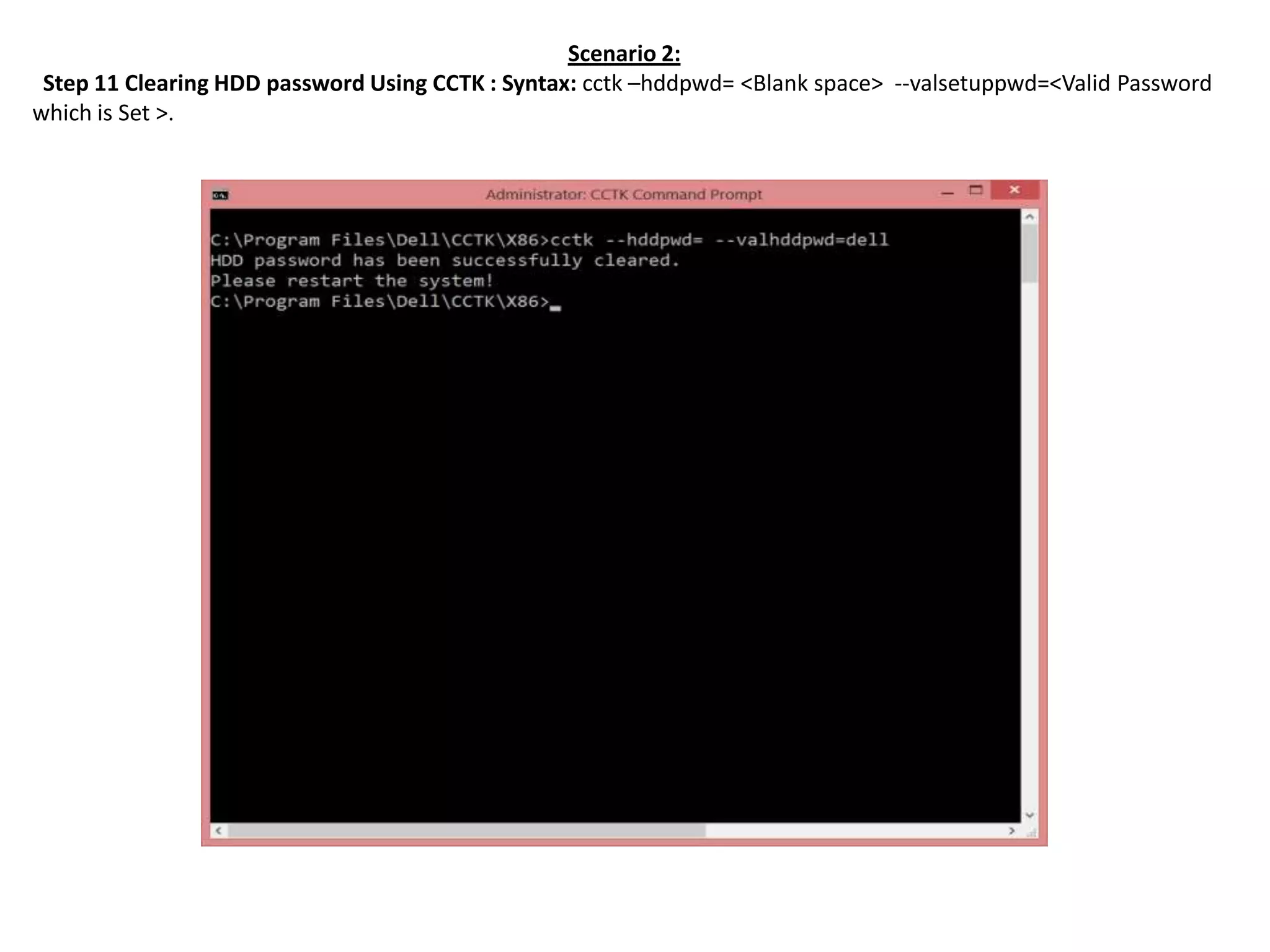
3. The process to clear an HDD password uses the "hddpwd=" CCTK command along with the valid password that was previously set.