Embed presentation
Downloaded 21 times












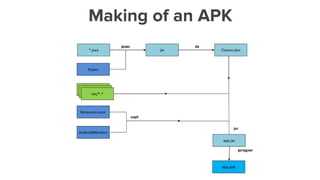




![assets - all the unmodified app contents
AndroidManifest.xml - Generic; The app-map
classes.dex - Java files’ package. The Dalvik executable [ yeah! the source ]
res - All the resources ( drawables, icons, values )
lib - External/custom native libraries
Resources.asrc - Compiled resources / binaries
META-INF - Certificates](https://image.slidesharecdn.com/dissectingandroidapk-160918120101/85/Dissecting-Android-APK-19-320.jpg)









This document provides an overview of reversing Android applications. It discusses the Android security model including permissions and ARM TrustZone. It describes real world Android malware like ransomware and data stealing malware. The structure of an Android APK file is explained including the dex, resources, libraries and manifest. Tools for analyzing APKs are introduced, like APKTool for decompiling and Dex2Jar for extracting dex files. The document demonstrates decompiling an APK and analyzing the smali code. It provides a glossary of related terms and references for further reading.


















![assets - all the unmodified app contents
AndroidManifest.xml - Generic; The app-map
classes.dex - Java files’ package. The Dalvik executable [ yeah! the source ]
res - All the resources ( drawables, icons, values )
lib - External/custom native libraries
Resources.asrc - Compiled resources / binaries
META-INF - Certificates](https://image.slidesharecdn.com/dissectingandroidapk-160918120101/85/Dissecting-Android-APK-19-320.jpg)









