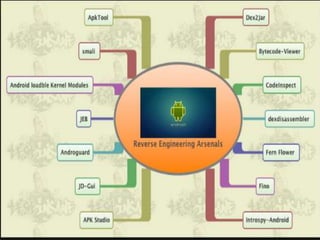
Minali Arora is a cyber security professional with 6 years of experience in application and network pentesting, bash scripting, and red teaming. She also works as a part-time bug bounty hunter and blogger. The document discusses Android security architecture, which uses UID separation and sandboxing to isolate apps from each other. It describes tools used for static and dynamic Android application testing such as apktool, dex2jar, and Drozer. Common vulnerabilities found include OTP bypass, authentication bypass, and privilege escalation. The document provides tips for developers to store data safely, enforce secure communication, and implement least privilege permissions.