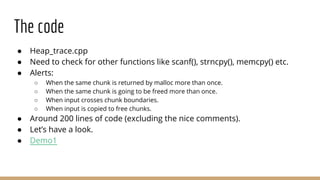
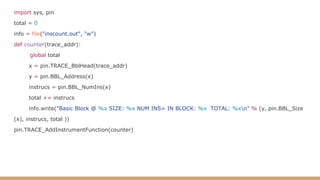
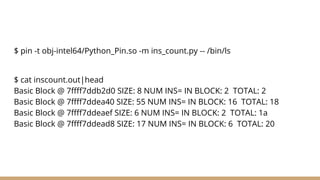
This document discusses dynamic binary instrumentation using Intel's PIN tool. It provides an overview of instrumentation, why dynamic binary instrumentation (DBI) is useful, and examples of using PIN for instrumentation and analysis. Key points include that instrumentation inserts extra code into a process's memory, PIN is useful for reverse engineering and malware analysis, and examples demonstrate using PIN to count instructions and detect heap bugs.

![Why DBI
…...
if (size < sizeof(min_buf)) {
iov_to_buf(iov, iovcnt, 0, min_buf, size);
memset(&min_buf[size], 0, sizeof(min_buf) - size);
}
else if (iov->iov_len < MAXIMUM_ETHERNET_HDR_LEN) {
/* This is very unlikely, but may happen. */
iov_to_buf(iov, iovcnt, 0, min_buf, MAXIMUM_ETHERNET_HDR_LEN);
filter_buf = min_buf;
}
…...](https://image.slidesharecdn.com/dbi-161121122724/85/Dynamic-Binary-Instrumentation-3-320.jpg)
![….
if (size < sizeof(min_buf)) {
printf(“Good size branchn”);
iov_to_buf(iov, iovcnt, 0, min_buf, size);
memset(&min_buf[size], 0, sizeof(min_buf) - size);
}
else if (iov->iov_len < MAXIMUM_ETHERNET_HDR_LEN) {
/* This is very unlikely, but may happen. */
printf(“Got a rare casen”);
iov_to_buf(iov, iovcnt, 0, min_buf, MAXIMUM_ETHERNET_HDR_LEN);
filter_buf = min_buf;
}
….](https://image.slidesharecdn.com/dbi-161121122724/85/Dynamic-Binary-Instrumentation-4-320.jpg)


![#include <iostream>
#include "pin.H"
UINT64 icount = 0;
VOID IncCounter() {
icount++;}
VOID Instruction(INS ins, VOID *v) {
INS_InsertCall(ins, IPOINT_BEFORE, (AFUNPTR)IncCounter, IARG_END);}
VOID Fini(INT32 code, VOID *v) {
std::cerr << "Count " << icount << endl;}
int main(int argc, char * argv[]) {
PIN_Init(argc, argv);
INS_AddInstrumentFunction(Instruction, 0);
PIN_AddFiniFunction(Fini, 0);
PIN_StartProgram();
return 0;}
Analysis
Instrumentation](https://image.slidesharecdn.com/dbi-161121122724/85/Dynamic-Binary-Instrumentation-7-320.jpg)