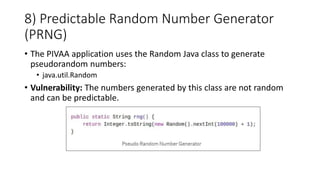
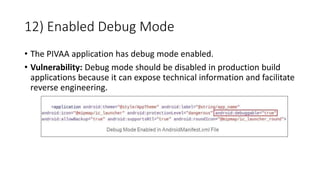
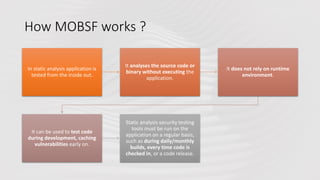
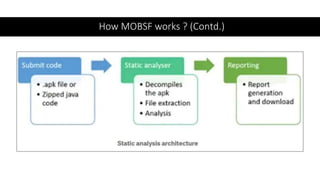
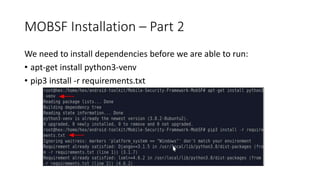
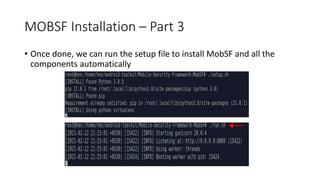
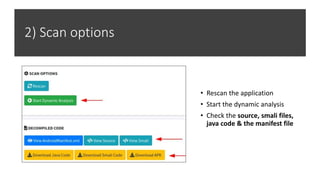
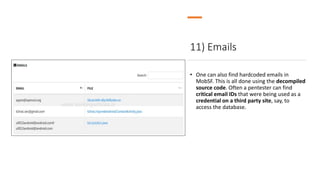
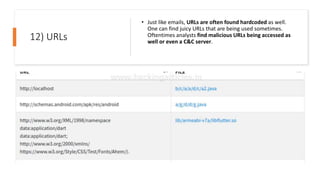
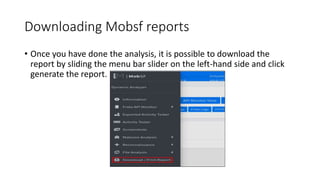
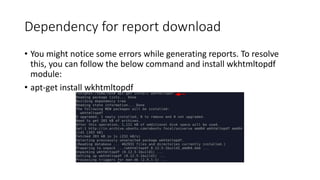
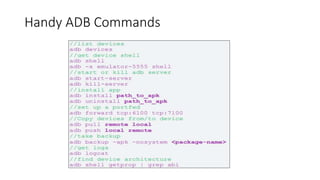
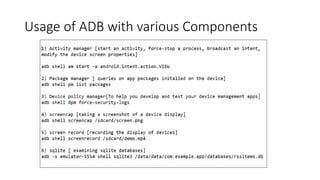
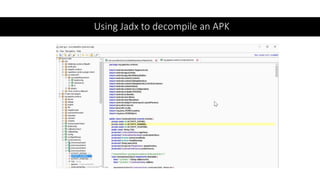
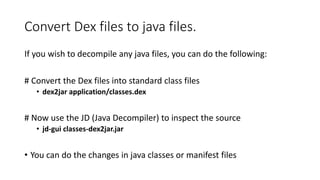
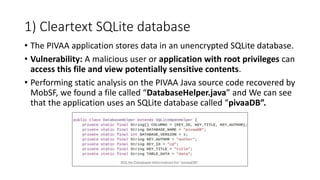
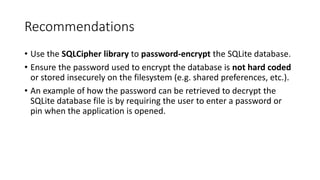
The document provides a detailed agenda for a day 2 Android hacking session focusing on automated static analysis with the MobSF framework. It includes installation instructions, components, and methodology for analyzing Android applications, alongside a manual static analysis and secure code review with an example application called Pivaa. Various vulnerabilities are discussed with recommendations for each to ensure secure application development and maintenance.
























![Recommendations:
• Use SQL Prepared statements, which implement a pre-compiled SQL
query and parameters that act as placeholders for user input which
are required before the SQL query can be executed. This treats user
input as data and not as commands, e.g.:
# SQL Prepared Statement Example
• db.rawQuery("select * from " + DATABASE_TABLE + " where " + "username=?
and password=?", new String [] {loginUsername, loginpass})
• Try to sanitize input from users where possible and appropriate,
• e.g. if you are expecting an integer as input, then you can validate for integers
only.](https://image.slidesharecdn.com/day2androidhacking-230119014405-01a4a296/85/Android-Penetration-testing-Day-2-45-320.jpg)