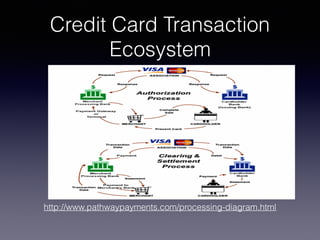
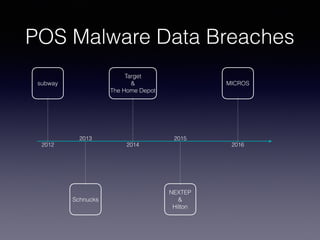
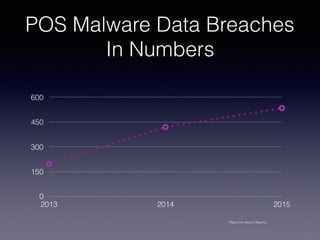
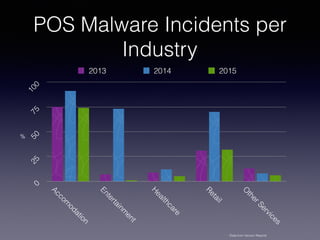
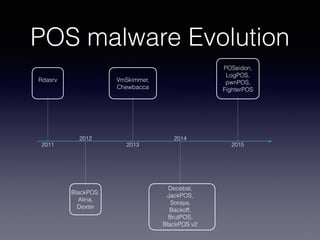
This document discusses point-of-sale (POS) malware and credit card transaction security. It begins by explaining how POS terminals and the credit card transaction ecosystem work. It then introduces POS malware, noting how early breaches captured card data during transmission but modern malware extracts it from RAM. The document outlines the evolution of POS malware from 2011-2015 and common infection methods. It provides a case study on the BlackPOS malware and discusses new technologies like EMV chips, NFC payments, and their impacts on security.