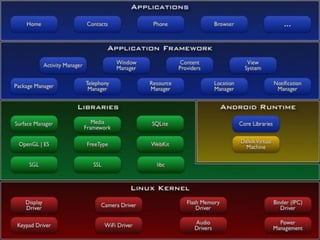
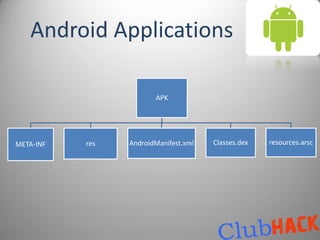
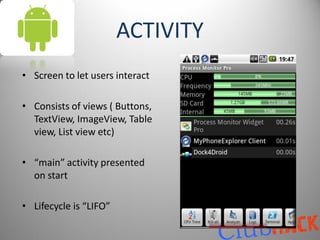
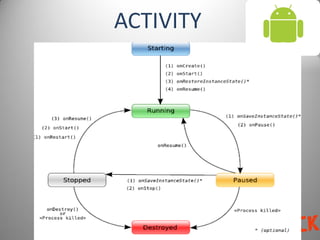
This document provides an overview of malware on Android systems. It discusses the Android architecture and security model, how to analyze Android application packages (APKs), and techniques for reverse engineering and creating Android malware. Specific malware examples like Trojan-SMS.FakePlayer.a and Geinimi are described. The document also covers tools for mobile application penetration testing and discusses both legal and illegal ways that Android malware can generate money.















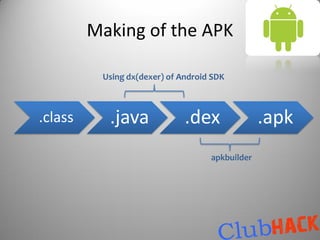
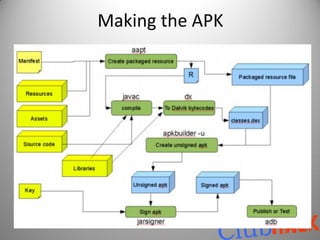
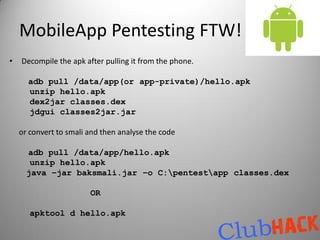
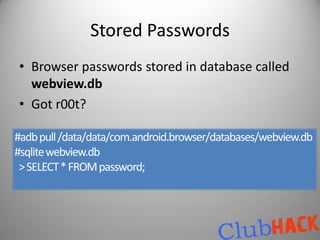
![Making the APK
aapt package -f -M ${manifest.file} -F ${packaged.resource.file} -I ${path.to.android-
jar.library} -S
${android-resource-directory} [-m -J ${folder.to.output.the.R.java}]
use javac
dx.bat –dex –output=${output.dex.file} ${compiled.classes.directory} ${jar files..}
apkbuilder ${output.apk.file} -u -z ${packagedresource.file} -f ${dex.file} -
rf ${source.dir} -rj ${libraries.dir}
use keytool
jarsigner -keystore ${keystore} -storepass ${keystore.password} -keypass ${keypass} -
signedjar ${signed.apkfile} ${unsigned.apkfile} ${keyalias}
adb -d install -r ${signed.apk}](https://image.slidesharecdn.com/hackingyourdroidclubhack2011-111210015853-phpapp01/85/Hacking-your-Droid-Aditya-Gupta-27-320.jpg)











![[$]Where is the money?[$]
[$$$]100% Illegal Ways to get rich! [$$$]
•Mobile App moolah by Jimmy Shah
Your phone has been hacked!
•Premium Rates SMSes Transfer $1000 to my account
Or else…….
•Make malwares for sale Acc No : xxxxxxxxxxxxxxxxxxxx
•Click Fraud, BlackHat SEO, Traffic generation, PPC Ads
•Steal Accounts/CCs and sell them
•Get personal information and blackmail the owner
•Sign up to many services with your referral id
•Make a bank phishing app](https://image.slidesharecdn.com/hackingyourdroidclubhack2011-111210015853-phpapp01/85/Hacking-your-Droid-Aditya-Gupta-52-320.jpg)
![[$$]Spread Yourself![$$]
• Forums
• P2P
• Send SMS’es/chat with your download link from the infected user’s phone
• Make a blog of cracked full version of famous android apps!
• Social Network viral scripts
• Android Market
• Amazon App Store](https://image.slidesharecdn.com/hackingyourdroidclubhack2011-111210015853-phpapp01/85/Hacking-your-Droid-Aditya-Gupta-53-320.jpg)