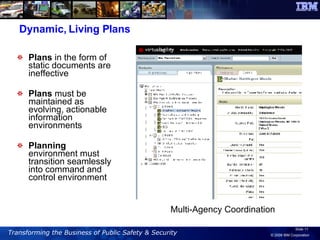
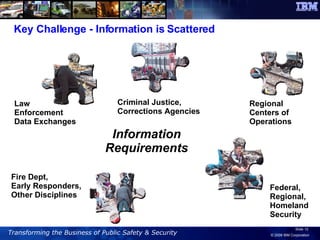
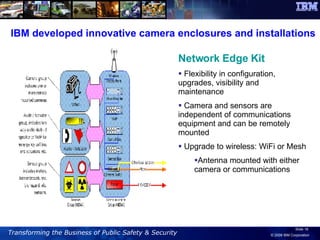
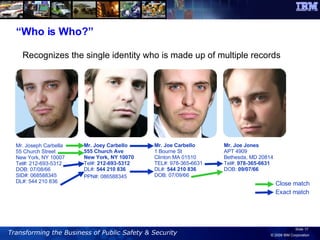
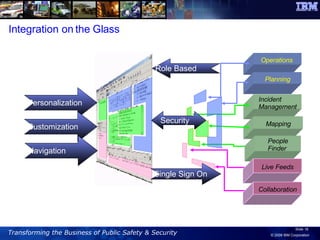
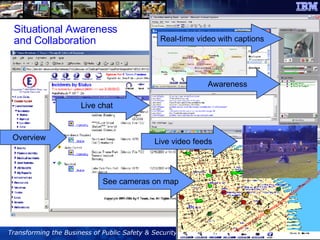
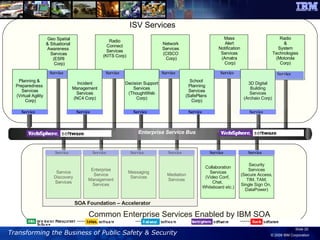
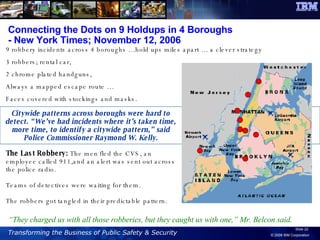
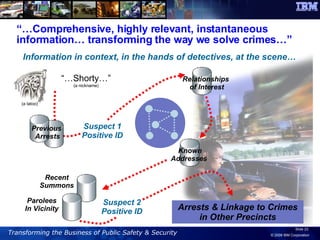
The document discusses the integration of information and communication technology (ICT) in disaster risk management, highlighting the importance of collaboration and data sharing among emergency response organizations. Case studies illustrate IBM's deployment of disaster management systems and the challenges faced by responders during incidents, emphasizing the need for real-time communication and effective incident management. Solutions are proposed for improved coordination and operational efficiency through innovative technologies and frameworks, aimed at enhancing public safety and disaster preparedness initiatives.
![Disaster Risk Management in the Information Age ICT, Disaster Risk Assessment, Mitigation, and Reduction Transforming the Business of Public Safety & Security Andrew S. Levy IBM Corporate Service Corps Fellow [email_address]](https://image.slidesharecdn.com/6ibm-1225117882895128-8/75/Disaster-Risk-Management-in-the-Information-Age-1-2048.jpg)

















![Additional Information citizencorps.blogspot.com www-03.ibm.com/industries/government/doc/jsp/indseg/all/f/index.jsp?re=gihome67gov Andrew S. Levy IBM Corporate Service Corps Fellow [email_address] Reaching over 13,000 people in over 1,400 cities in over 75 countries in 12 months.](https://image.slidesharecdn.com/6ibm-1225117882895128-8/85/Disaster-Risk-Management-in-the-Information-Age-28-320.jpg)