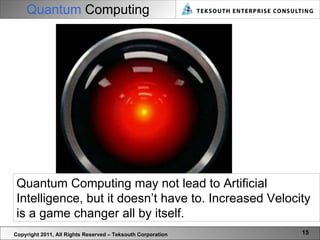
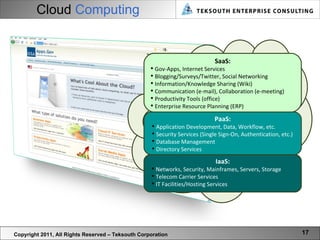
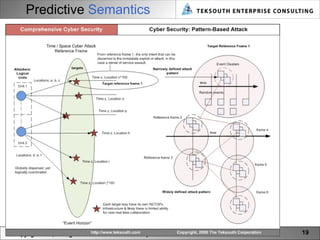
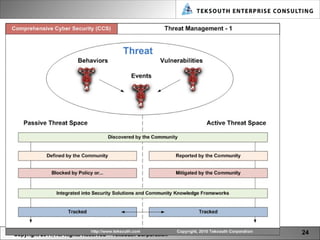
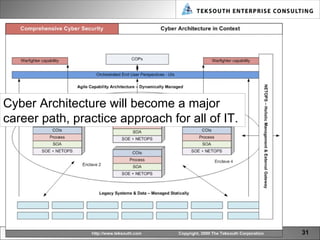
The document provides a vision for cyber security in 2021, including emerging technologies, threats, and practices. It predicts that technologies like mobile computing, quantum computing, cloud computing, predictive semantics, and dynamic networks will impact cyber security. Threats will become more sophisticated through cyber warfare, crime, and activism. Cyber security practice will evolve to be more multi-dimensional and holistic through practices like cyber architecture and lifecycle management. A new lexicon for cyber security terms is also envisioned.




























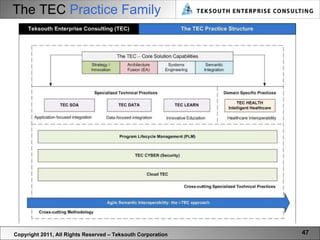

![TEC CYBER Copyright 2011, All Rights Reserved – Teksouth Corporation TEC CYBER offers comprehensive solutions and capabilities in seven primary categories, each representing a crucial stage in our solution approach: Foundation [Strategy & Semantics] Architect [Design] Assure [Operations] Aware [Analytics] Validate [Compliance] Collaborate [Real-time Integration] Intelligence [Inference, Pattern Recognition] The true power of our offerings is their ability to support integration and Cyber Security management within a single, holistic Lifecycle.](https://image.slidesharecdn.com/futureofcybersecurity-110725180846-phpapp01/85/The-Future-of-Cyber-Security-49-320.jpg)