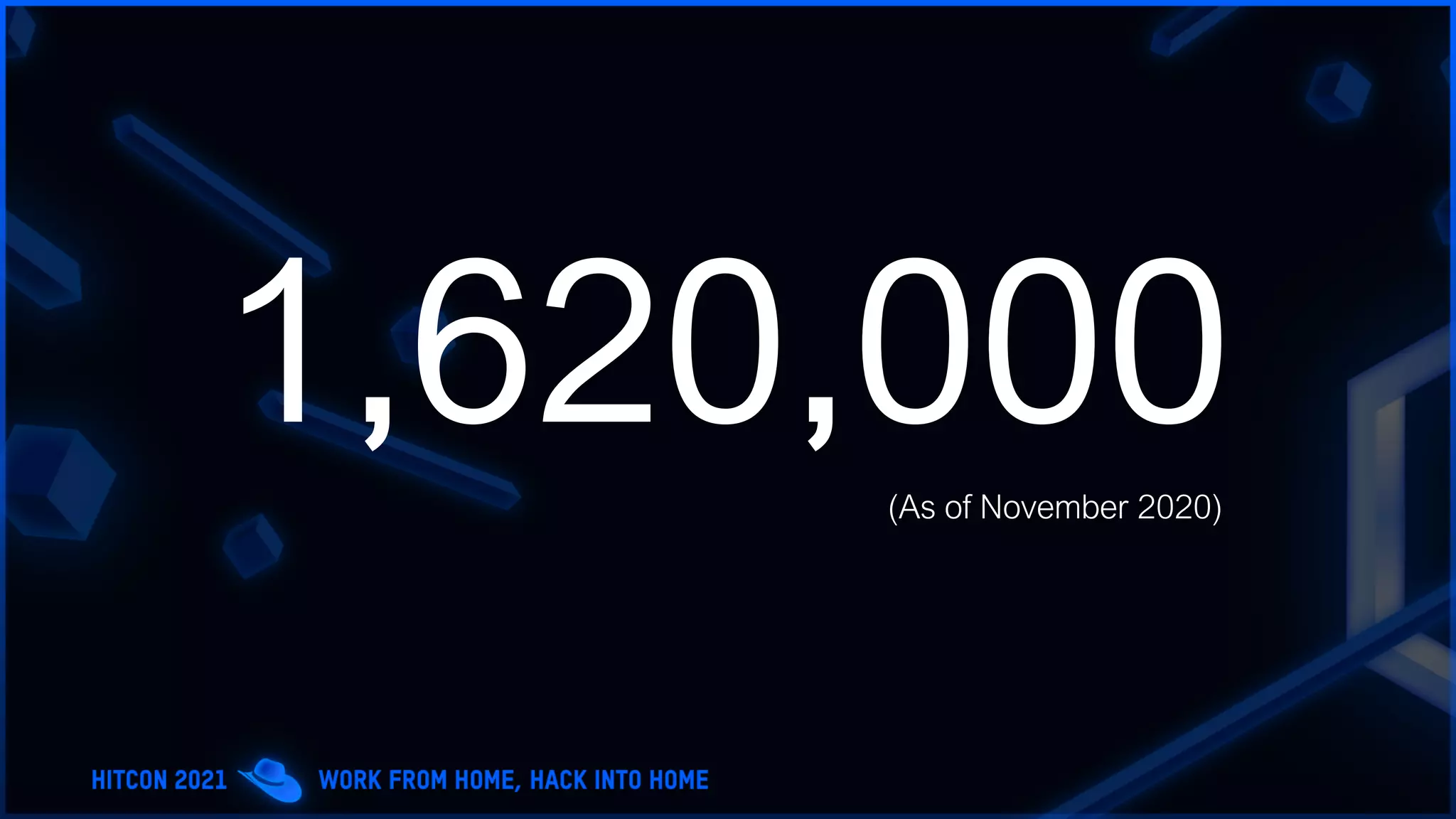
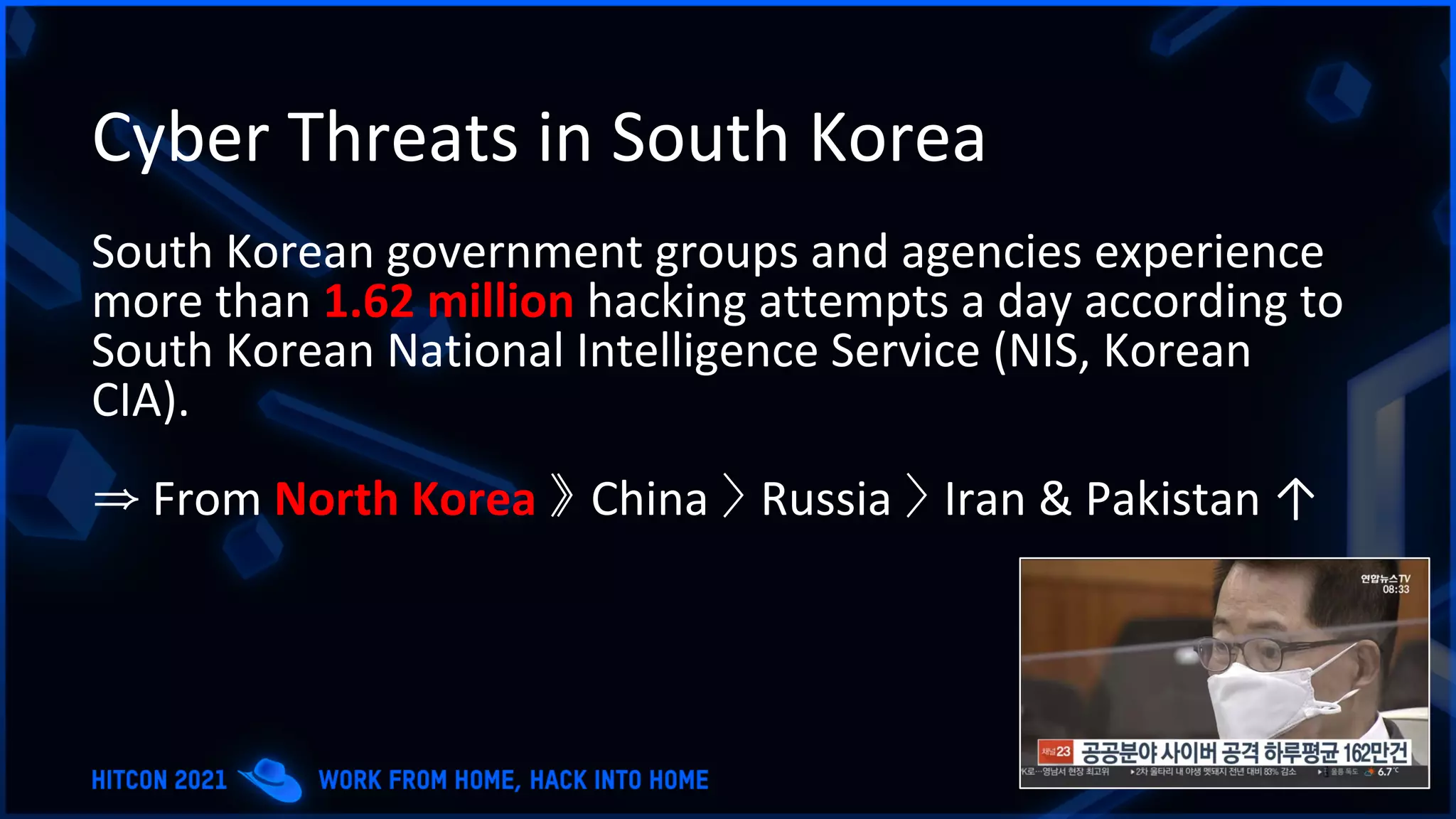
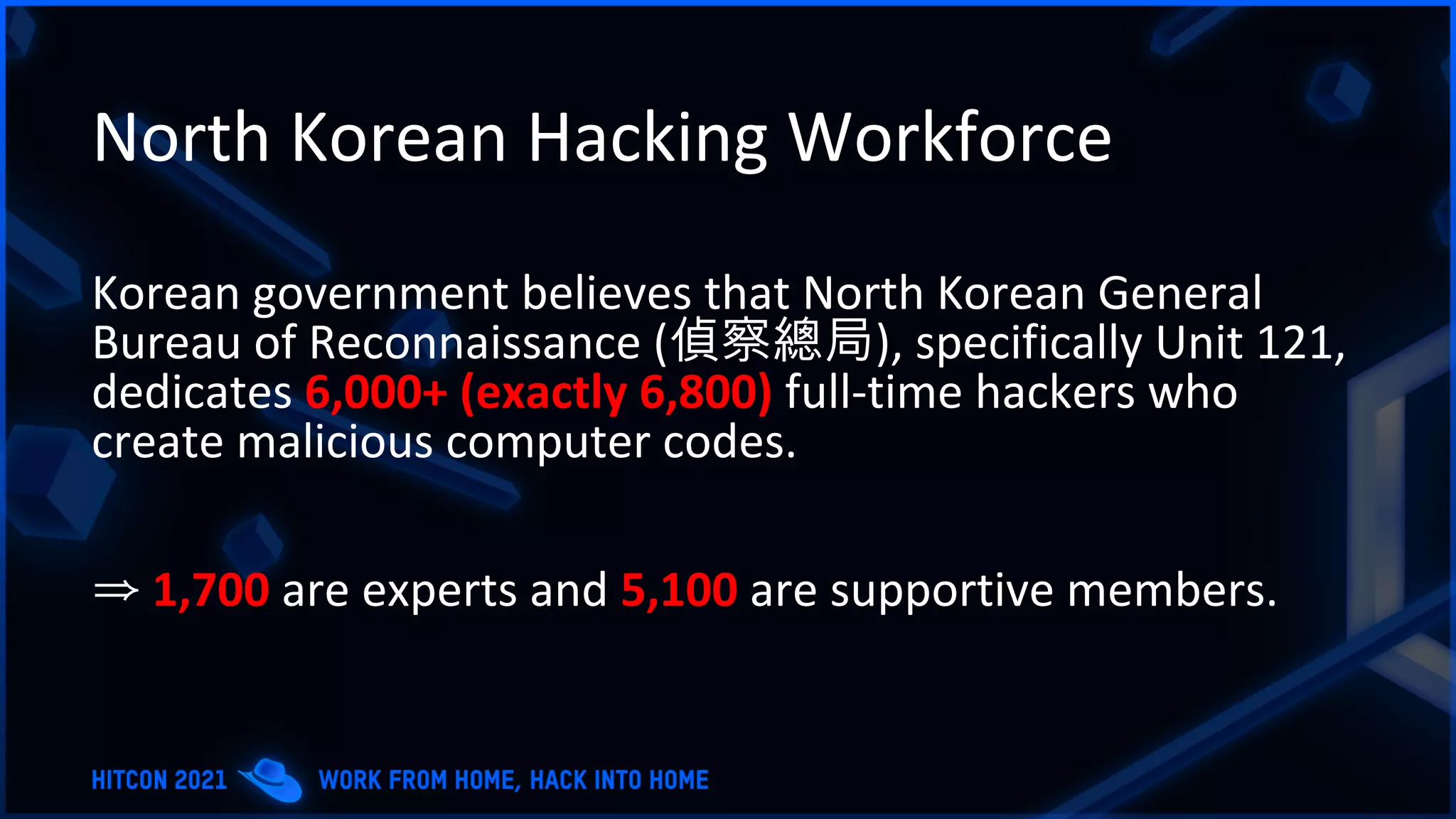
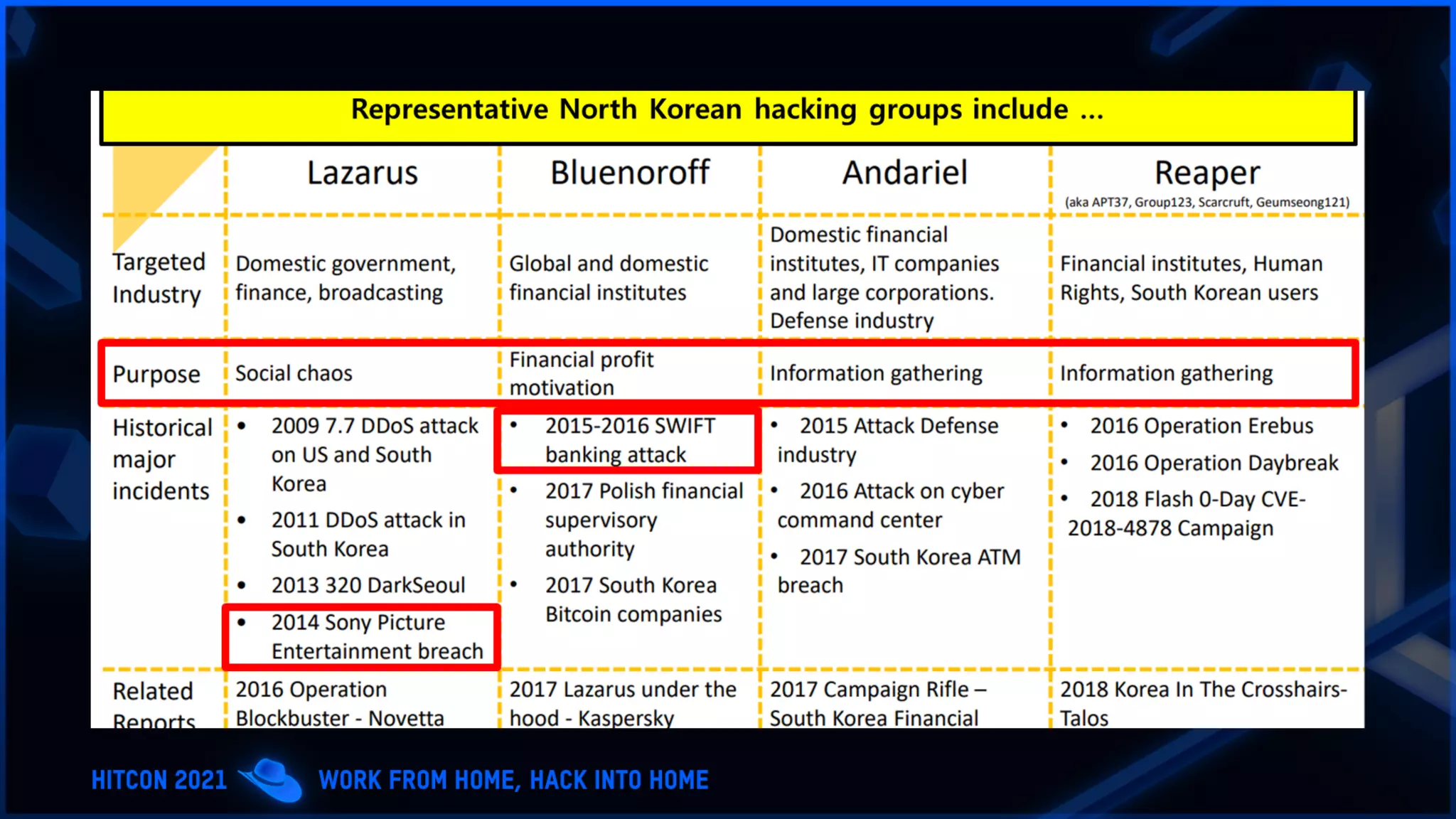
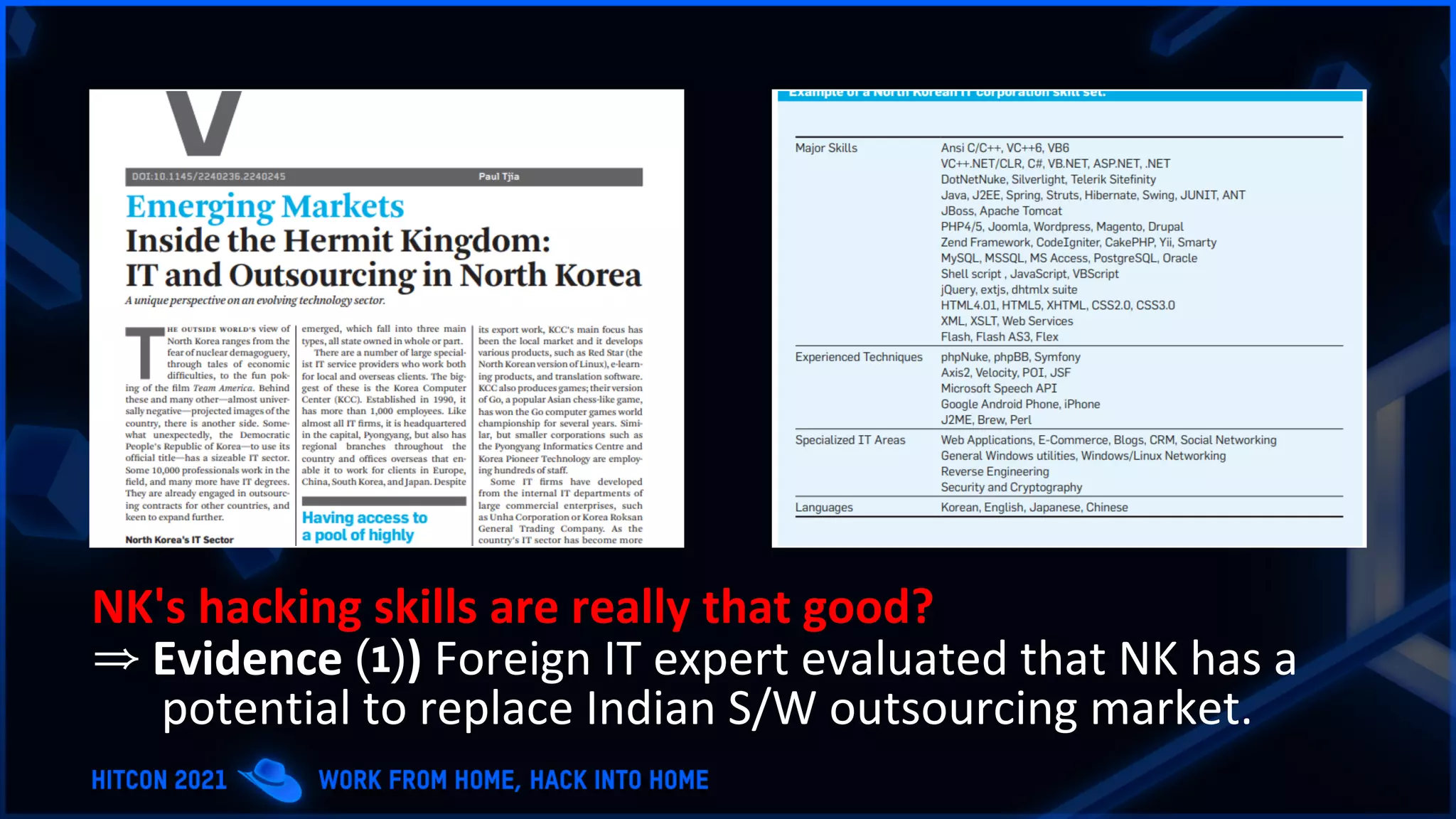
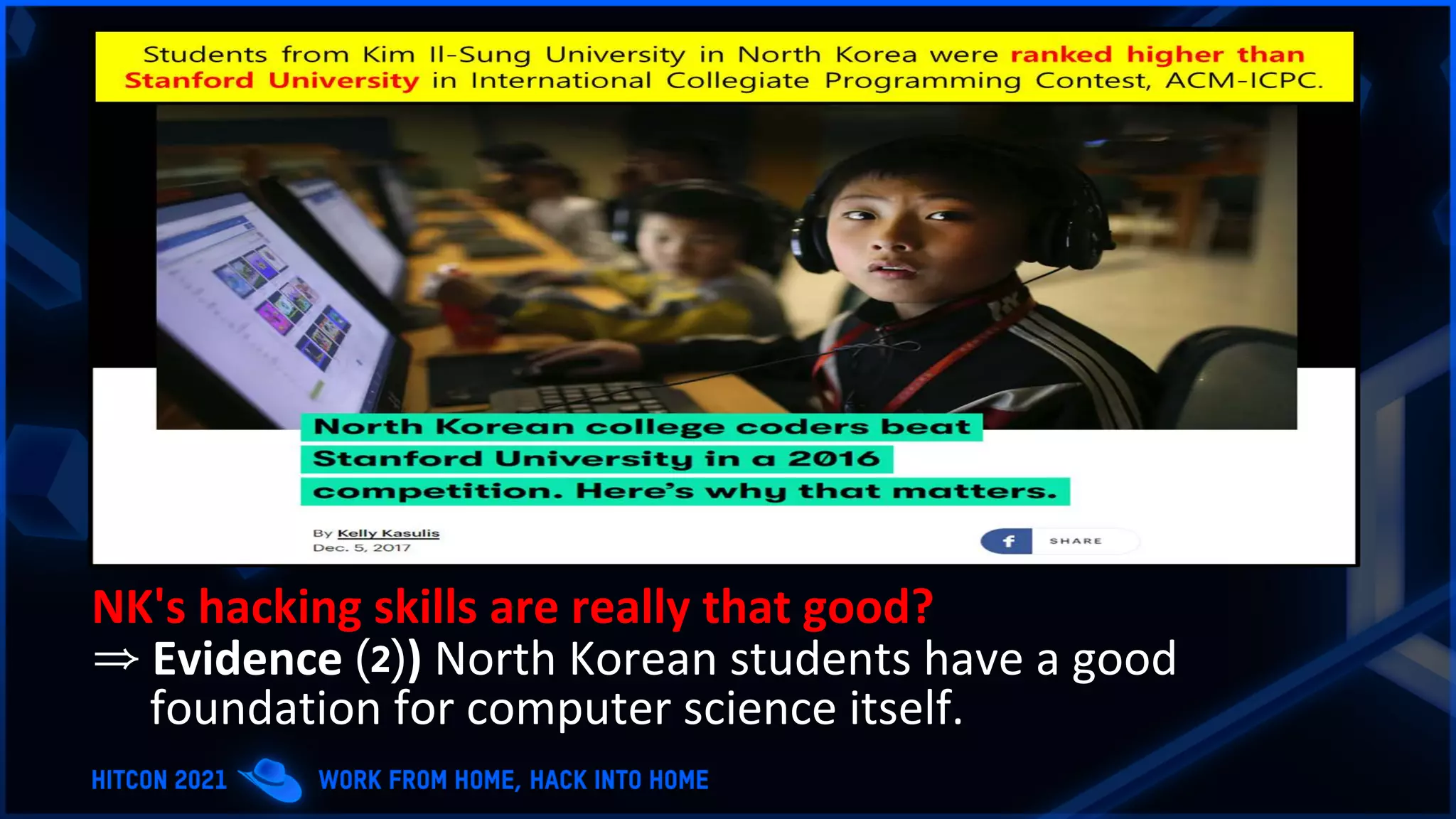
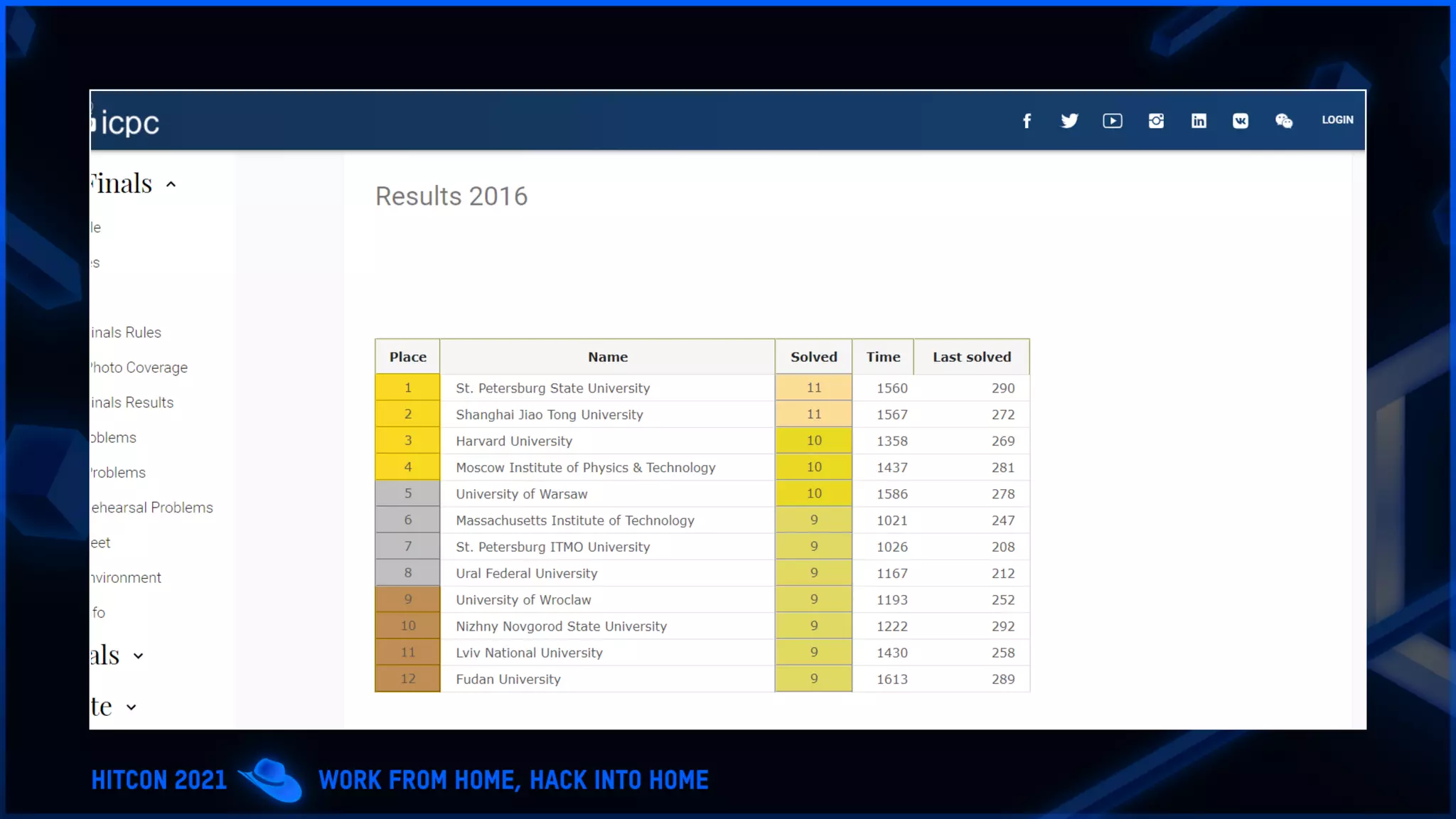
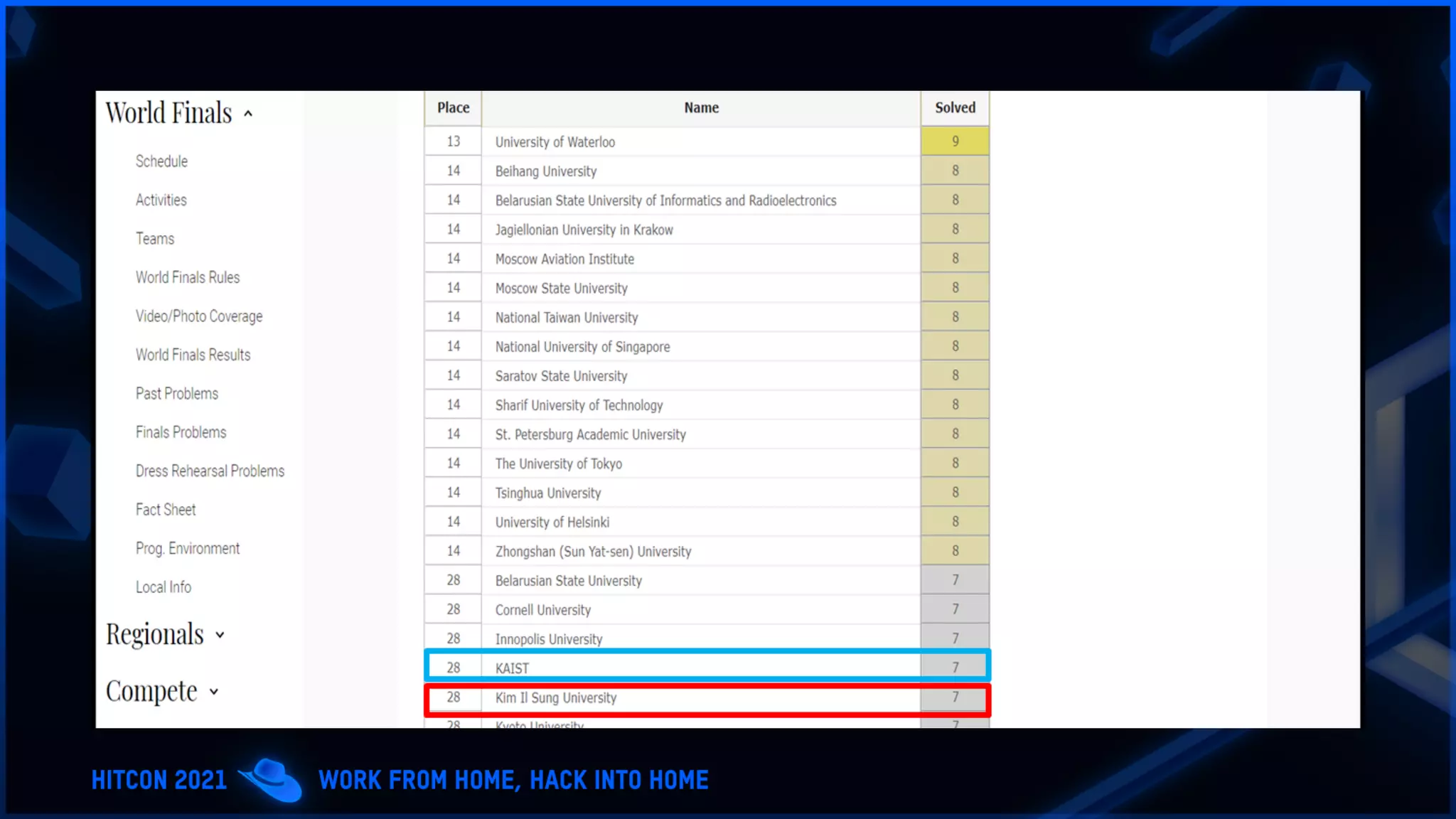
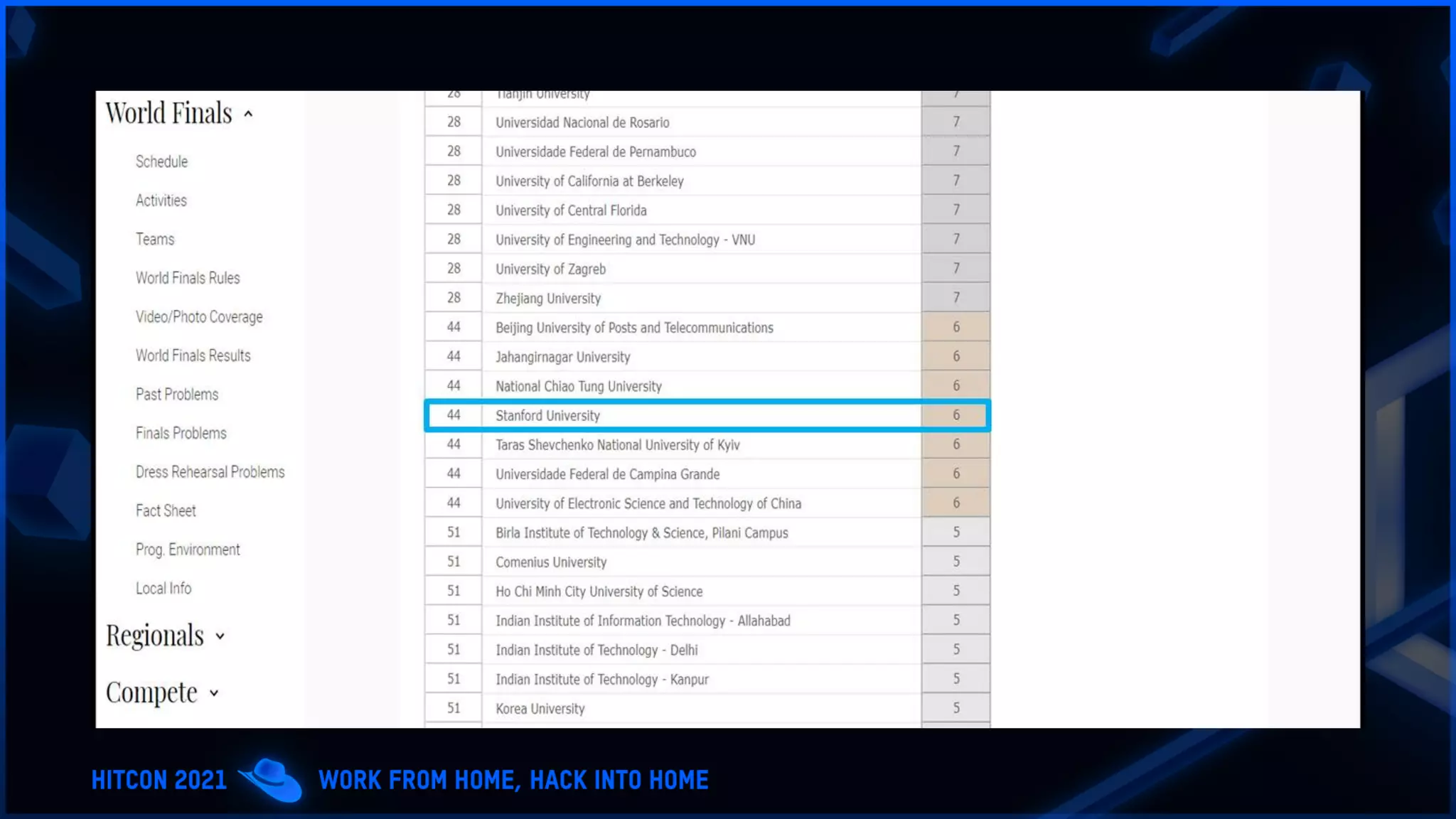
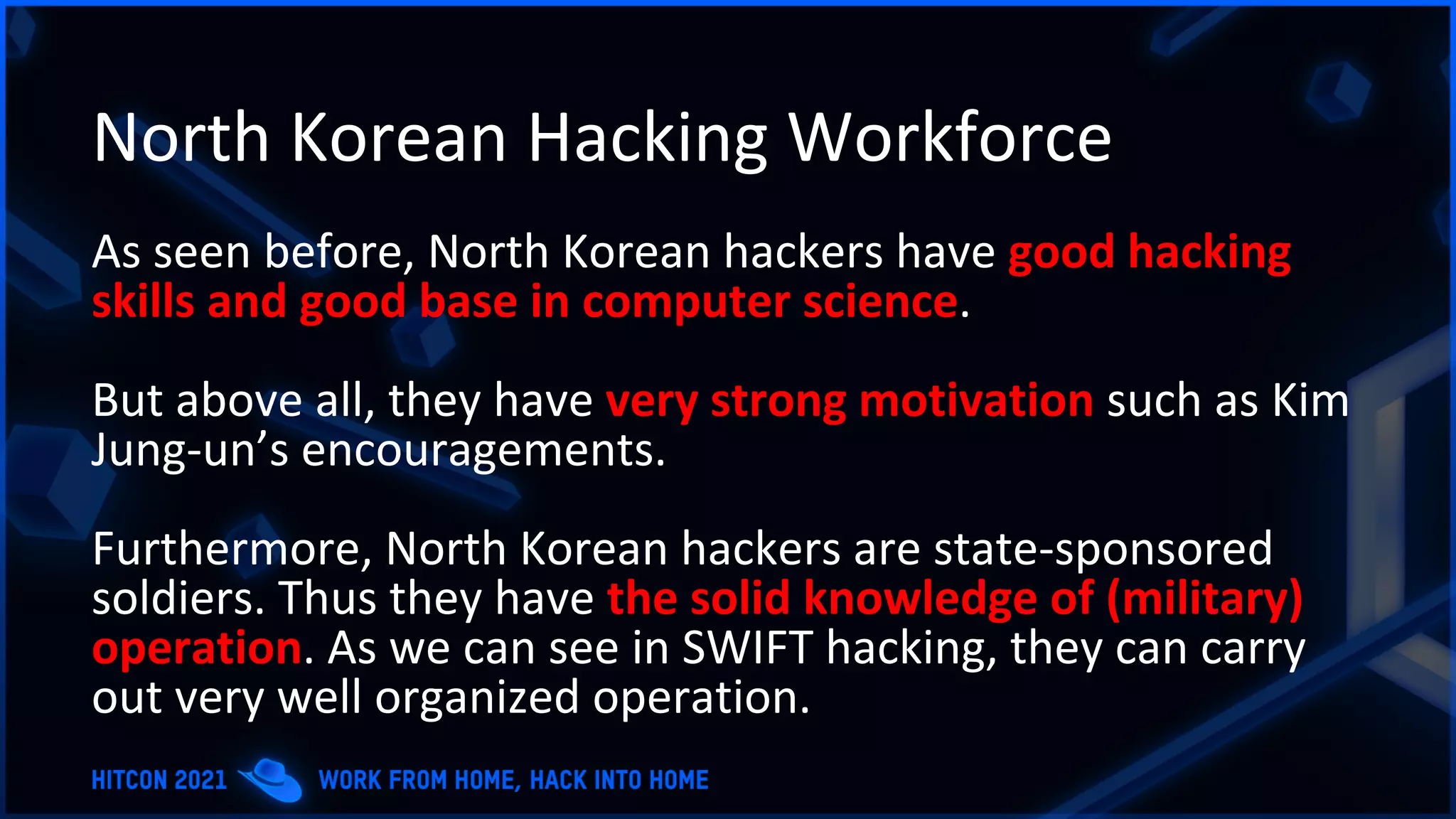
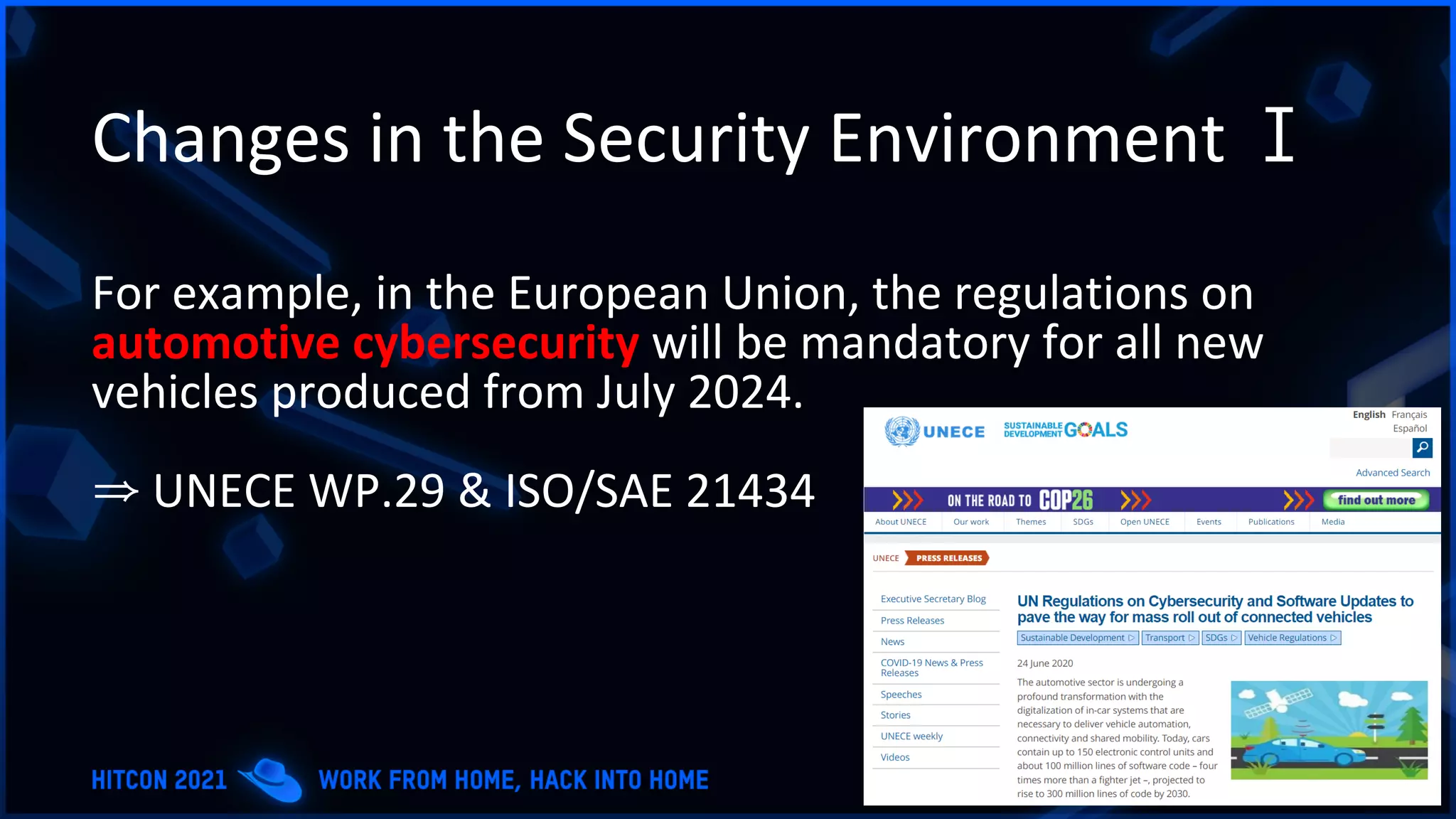
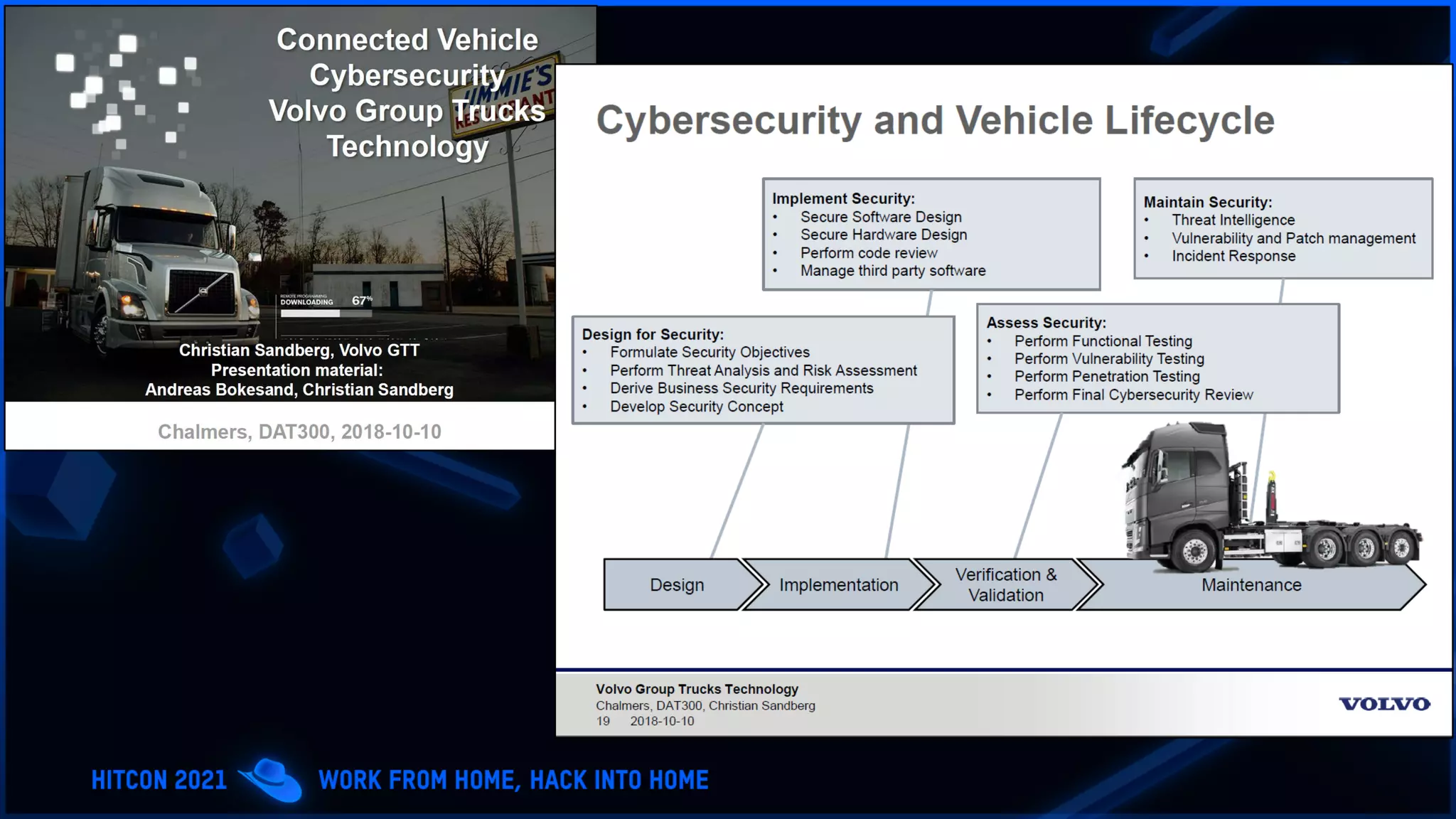
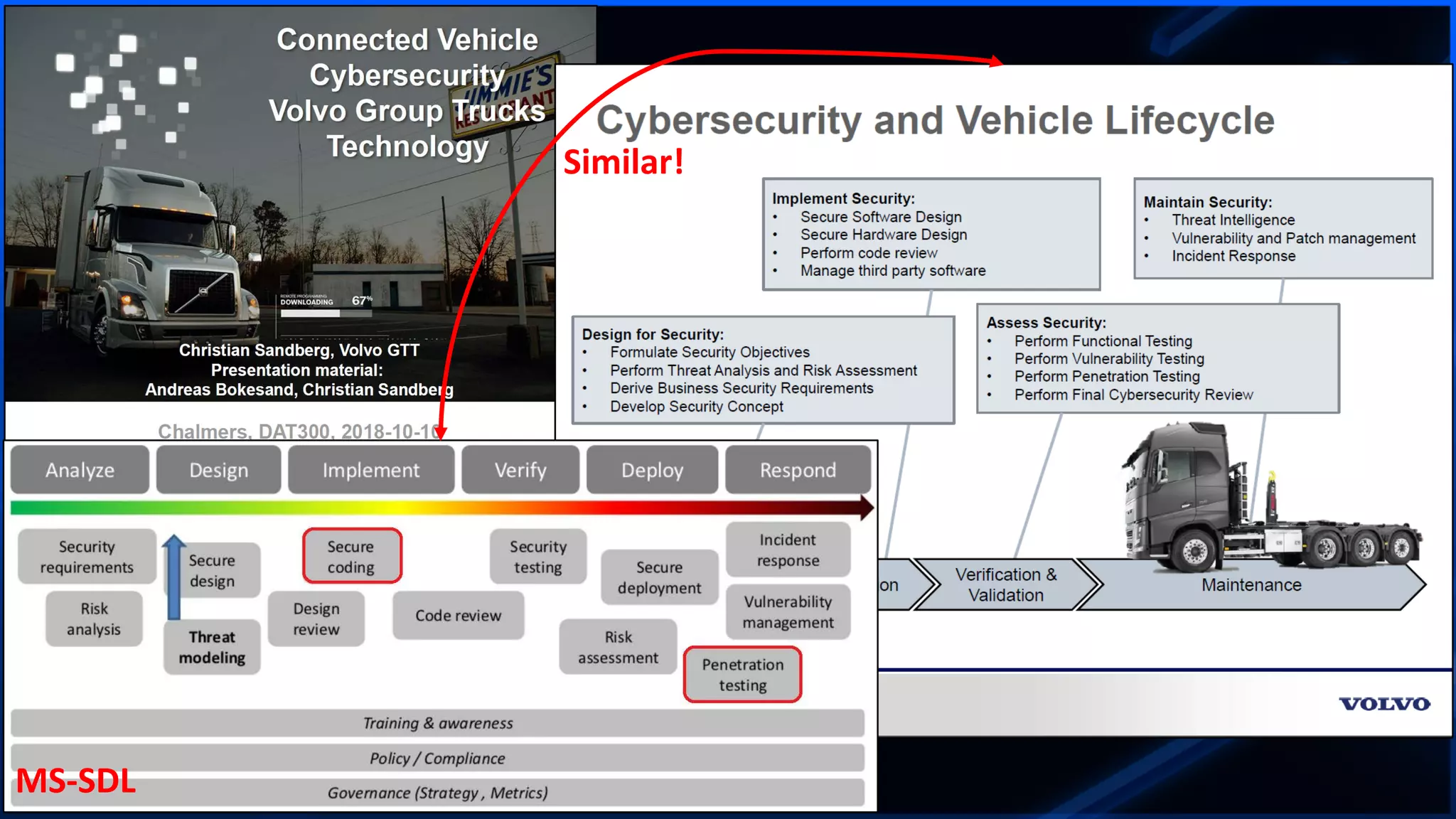
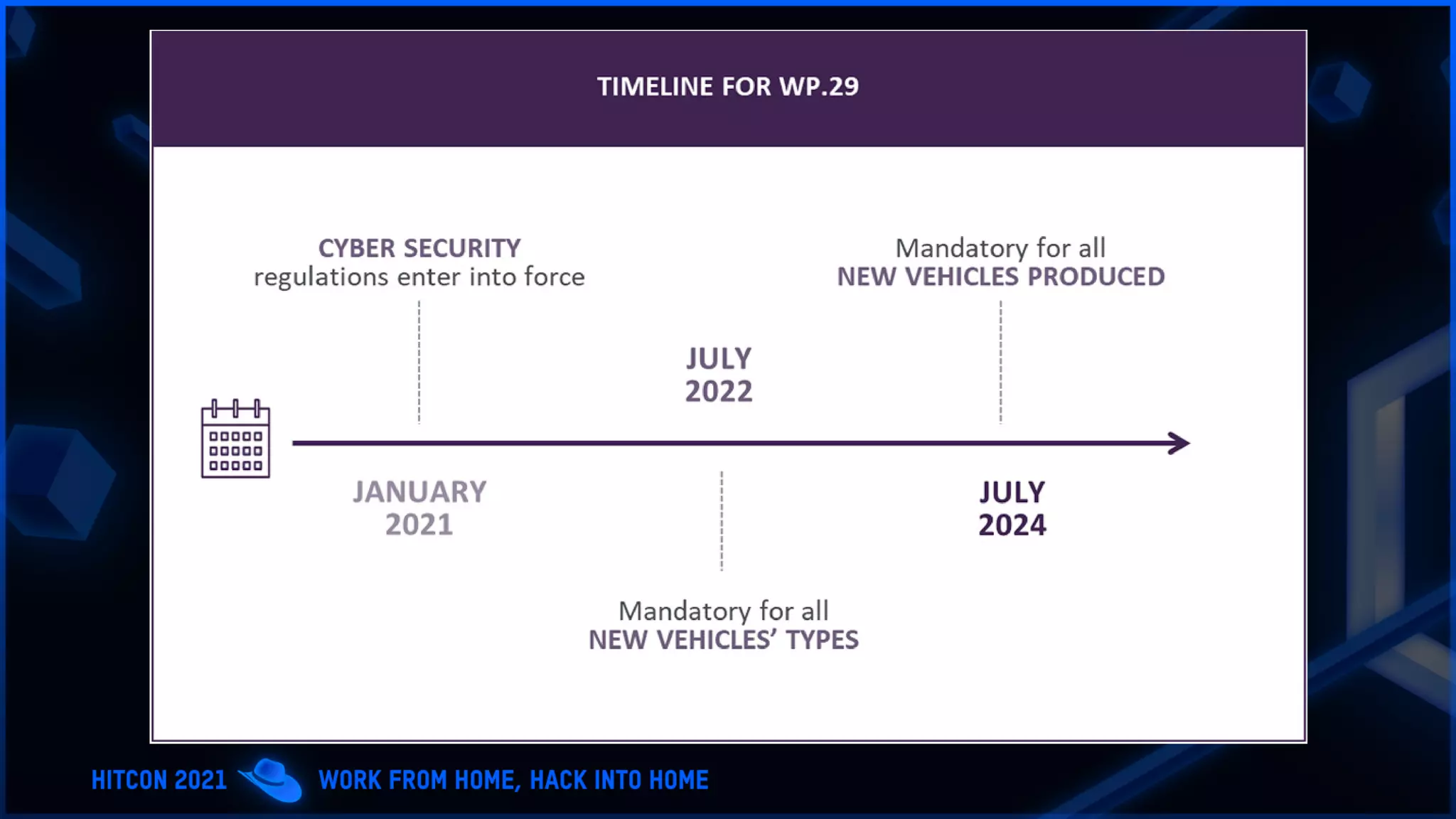
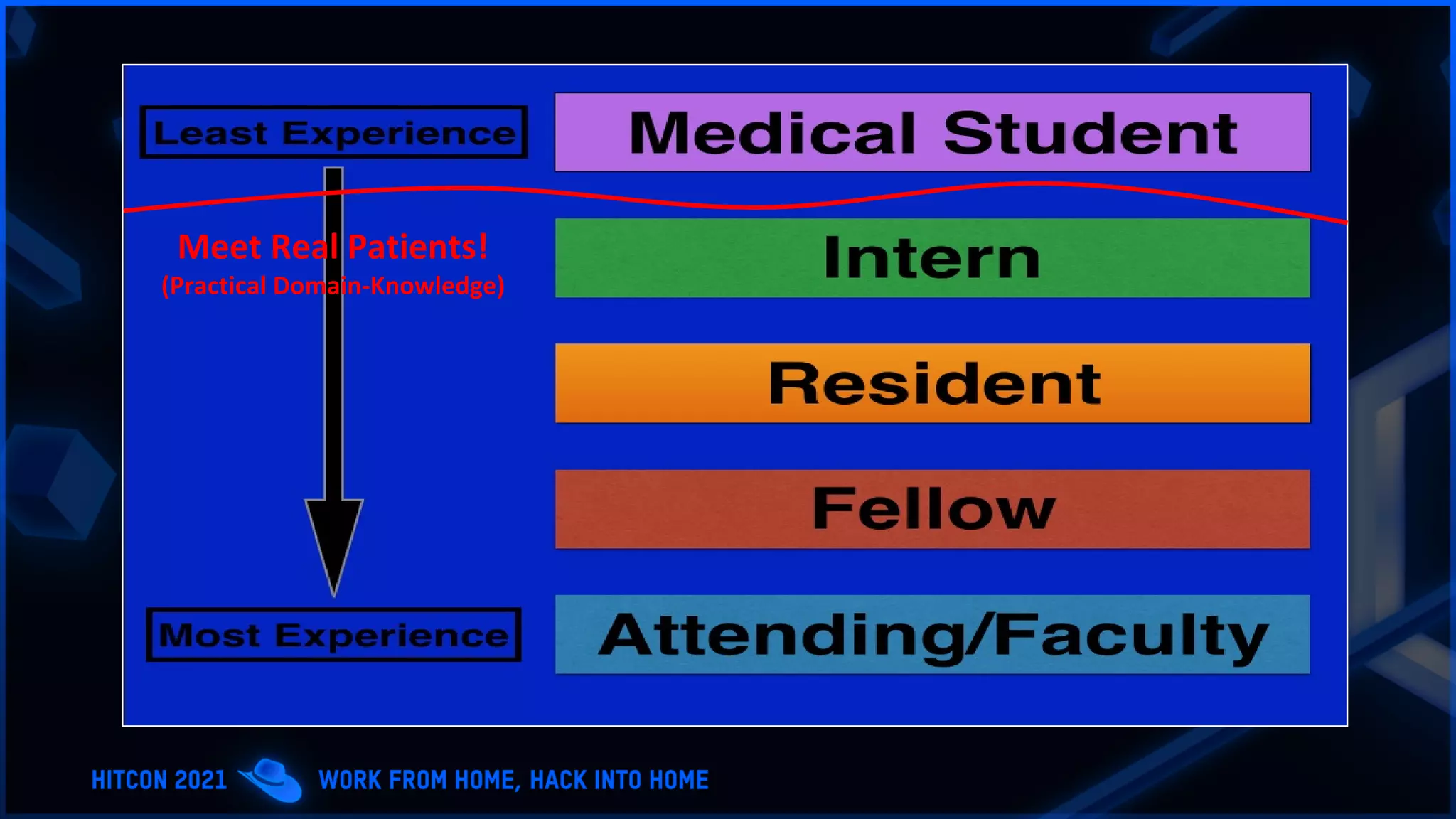
The document addresses the increasing difficulty of training the cybersecurity workforce in South Korea amid daily hacking attempts, primarily from North Korea and other countries. It highlights the importance of strong foundational education in cybersecurity, as well as the need for public-private partnerships to provide practical domain knowledge and experiences for students. The evolving security environment due to the 4th industrial revolution demands more specialized expertise in cybersecurity across various industries and presents challenges for smaller enterprises in recruiting talent.