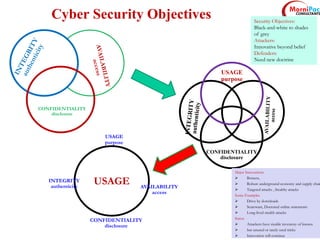
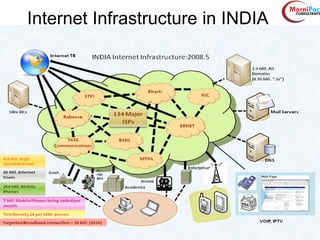
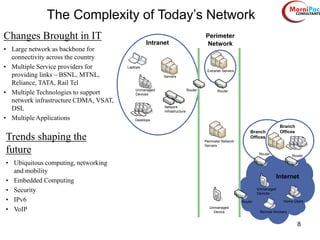
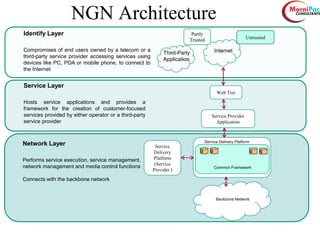
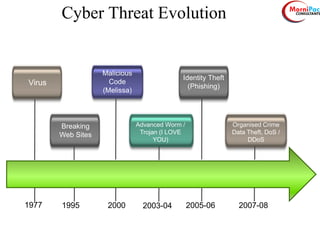
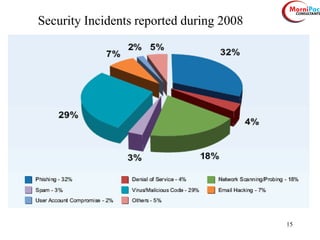
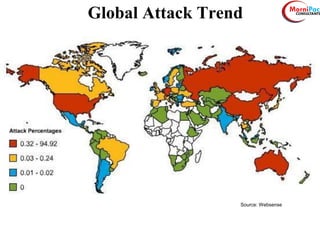
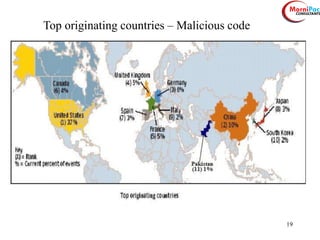
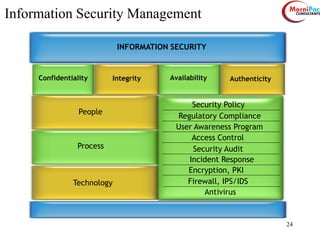
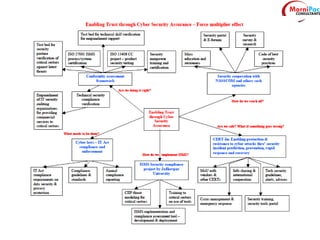
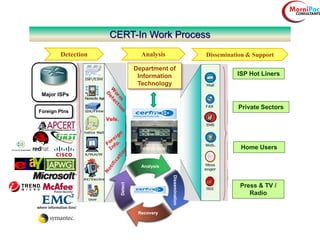
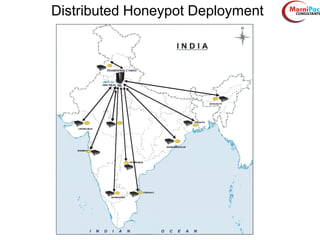
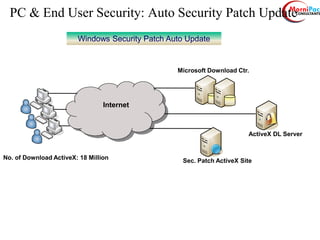
This document discusses cyber security from past, present, and future perspectives. It notes that cyber security has evolved from an immature field to one that will become more scientific and technology-centric over time. The document outlines key cyber threats such as botnets, targeted attacks, and the underground economy that supports them. It also summarizes India's cyber security strategy, noting the importance of legal frameworks, incident response, capacity building, research and development, and international collaboration to enhance cyber security.