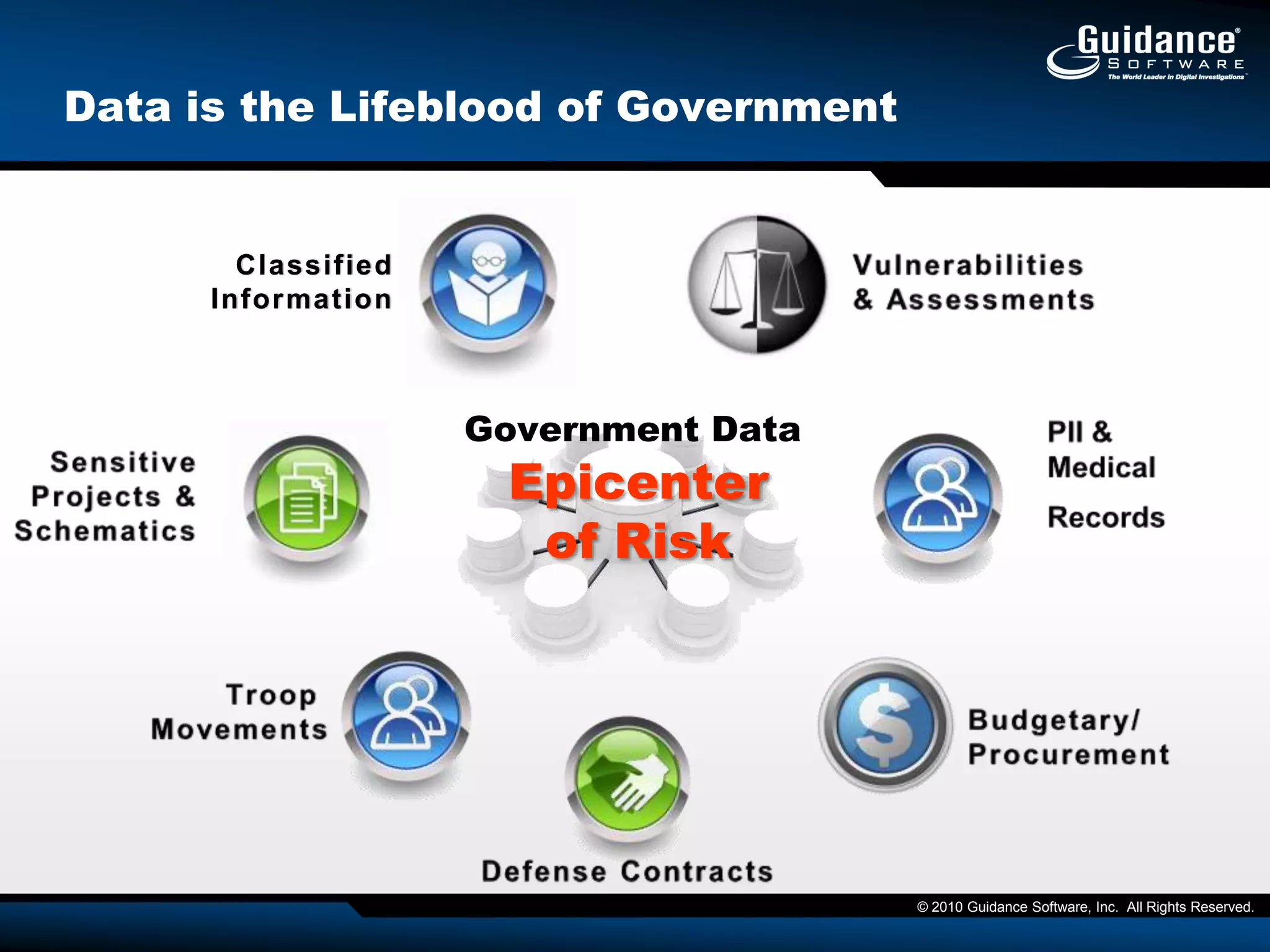
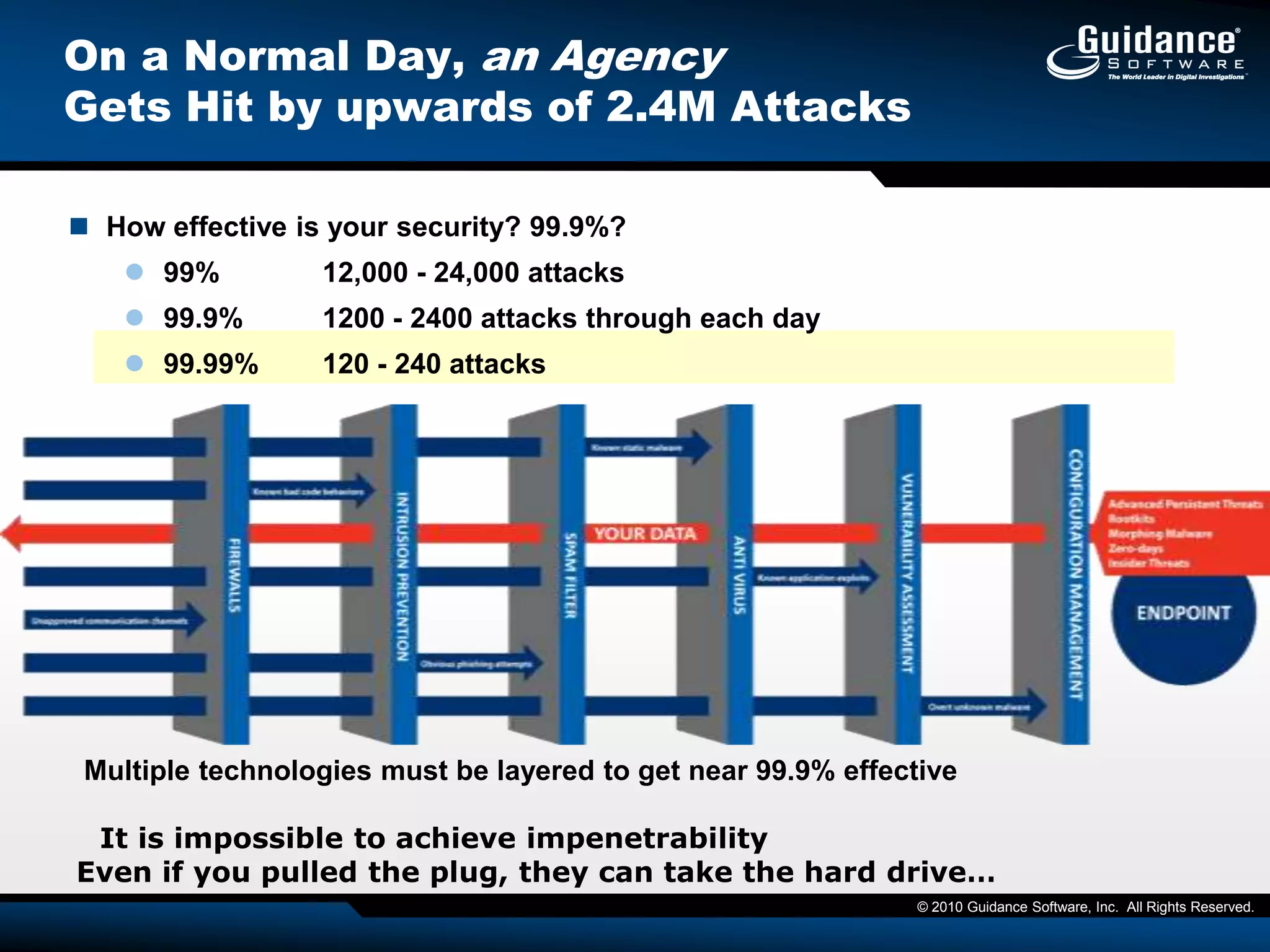
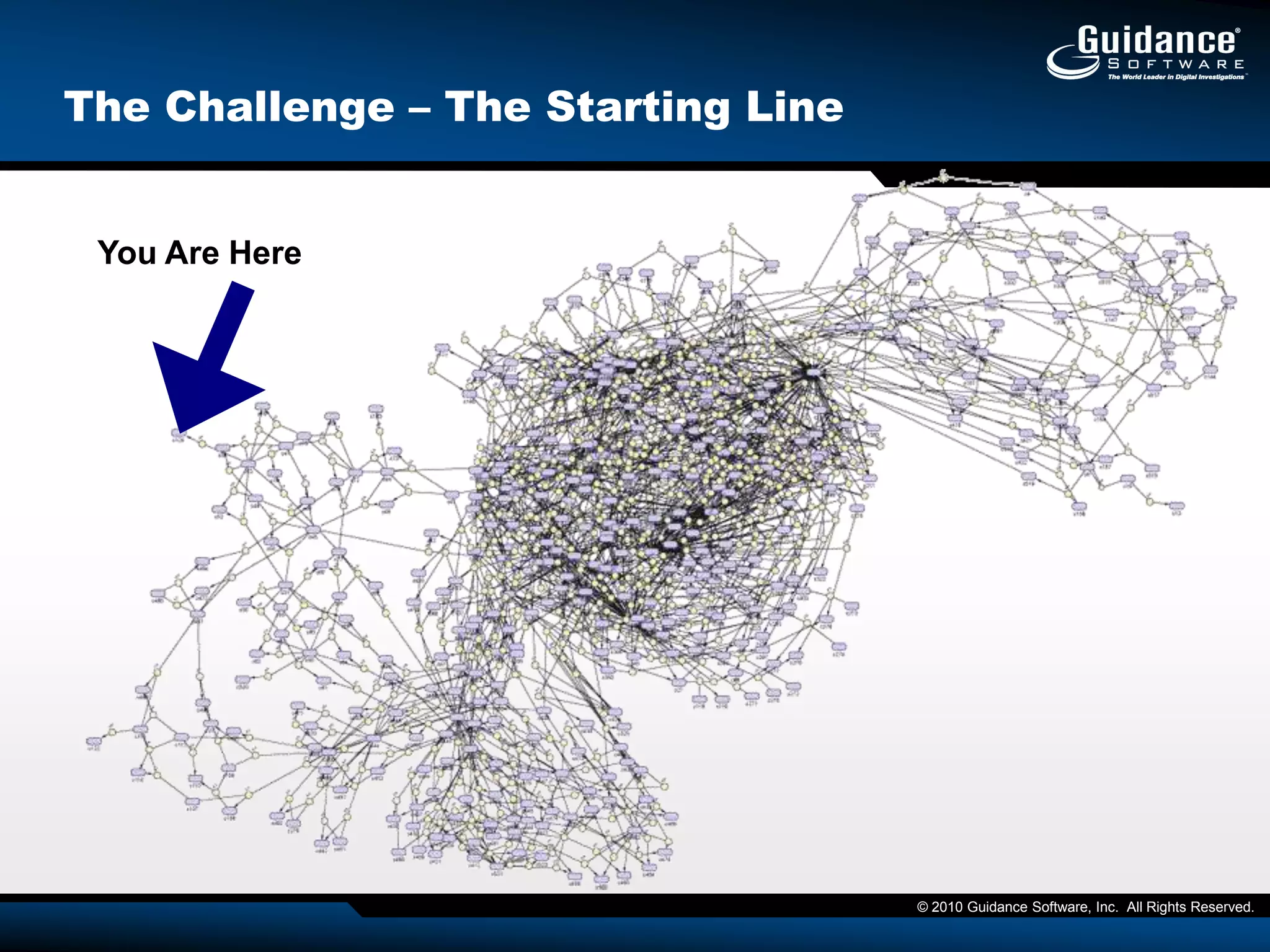
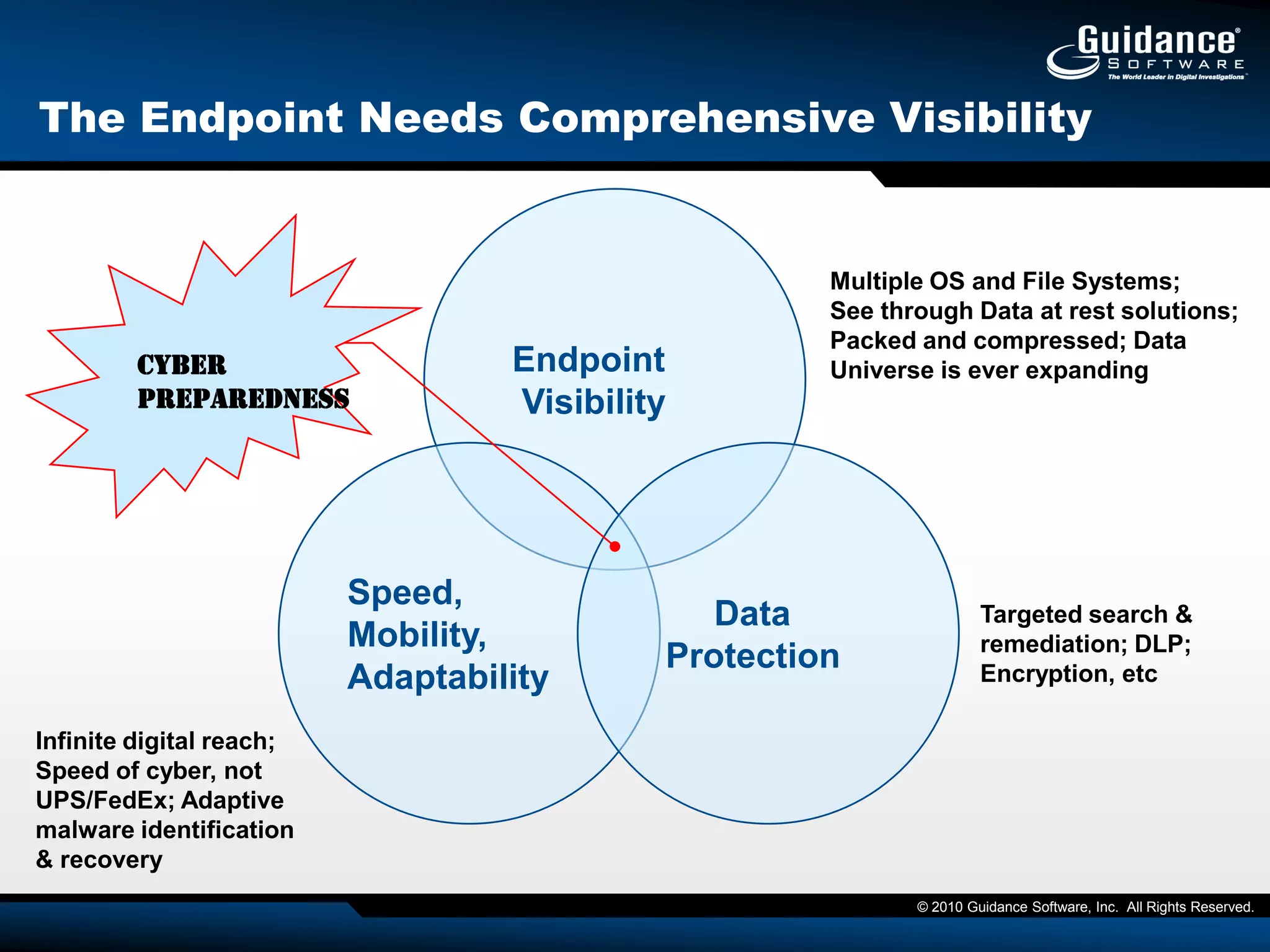
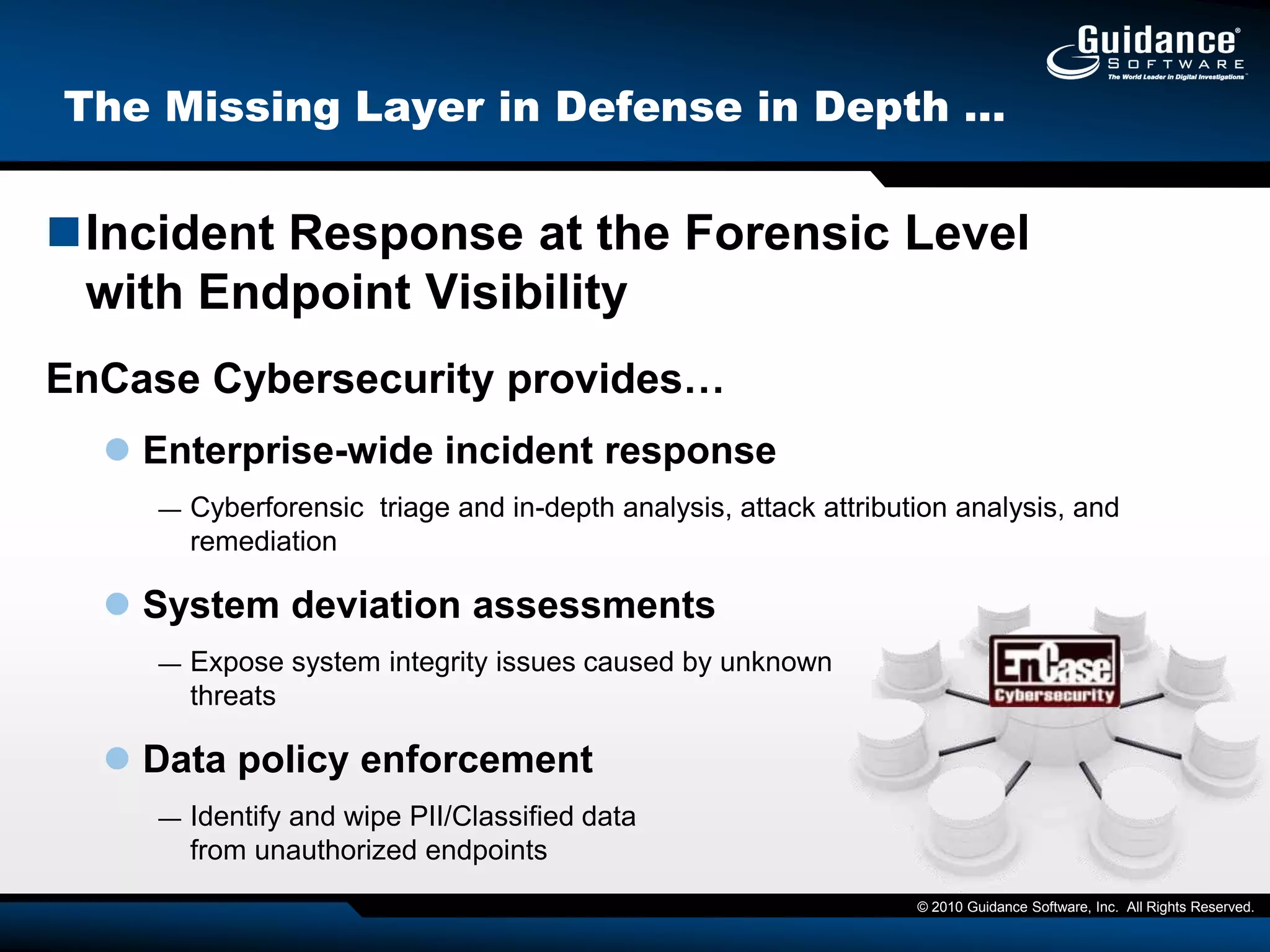
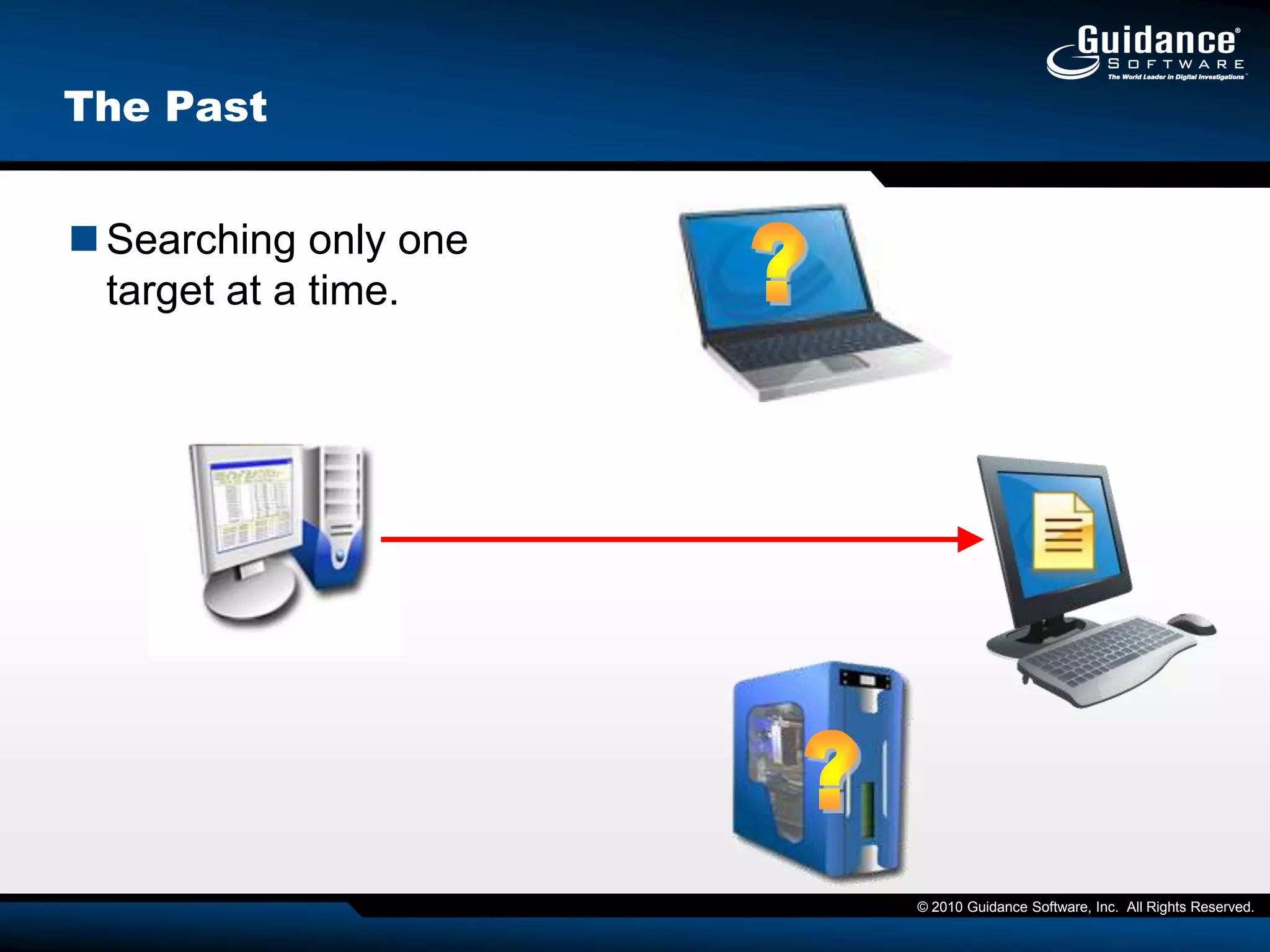
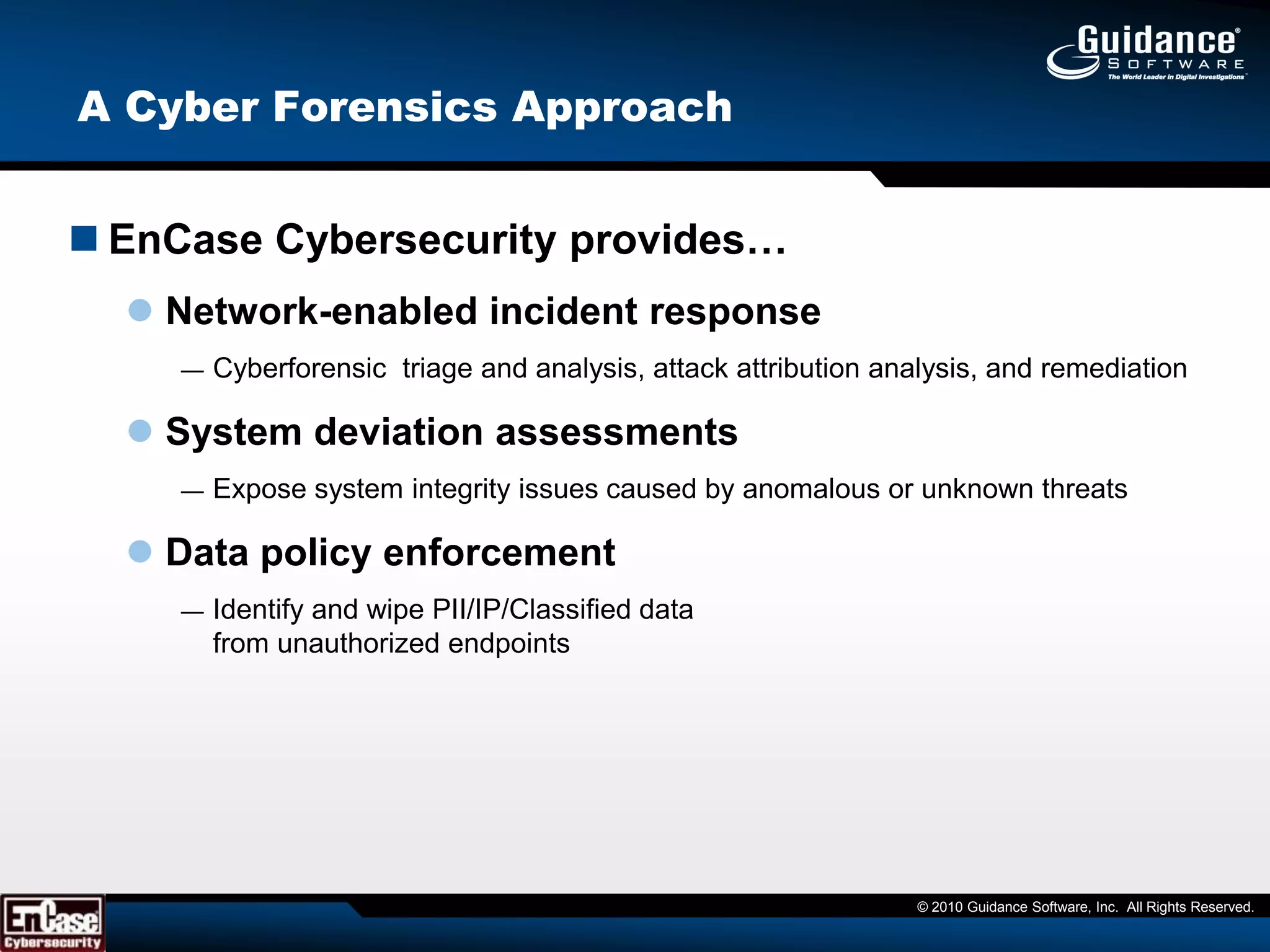
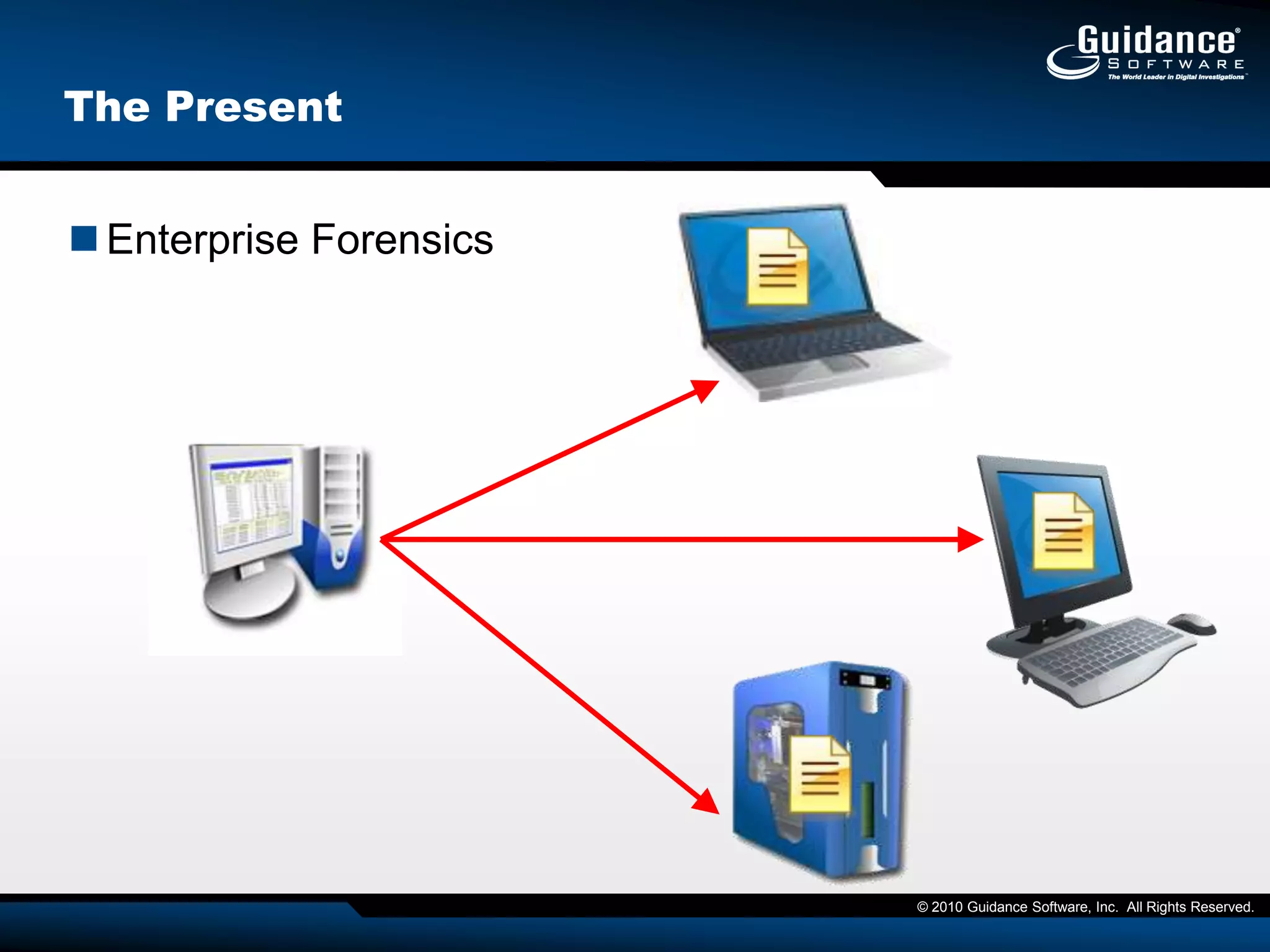
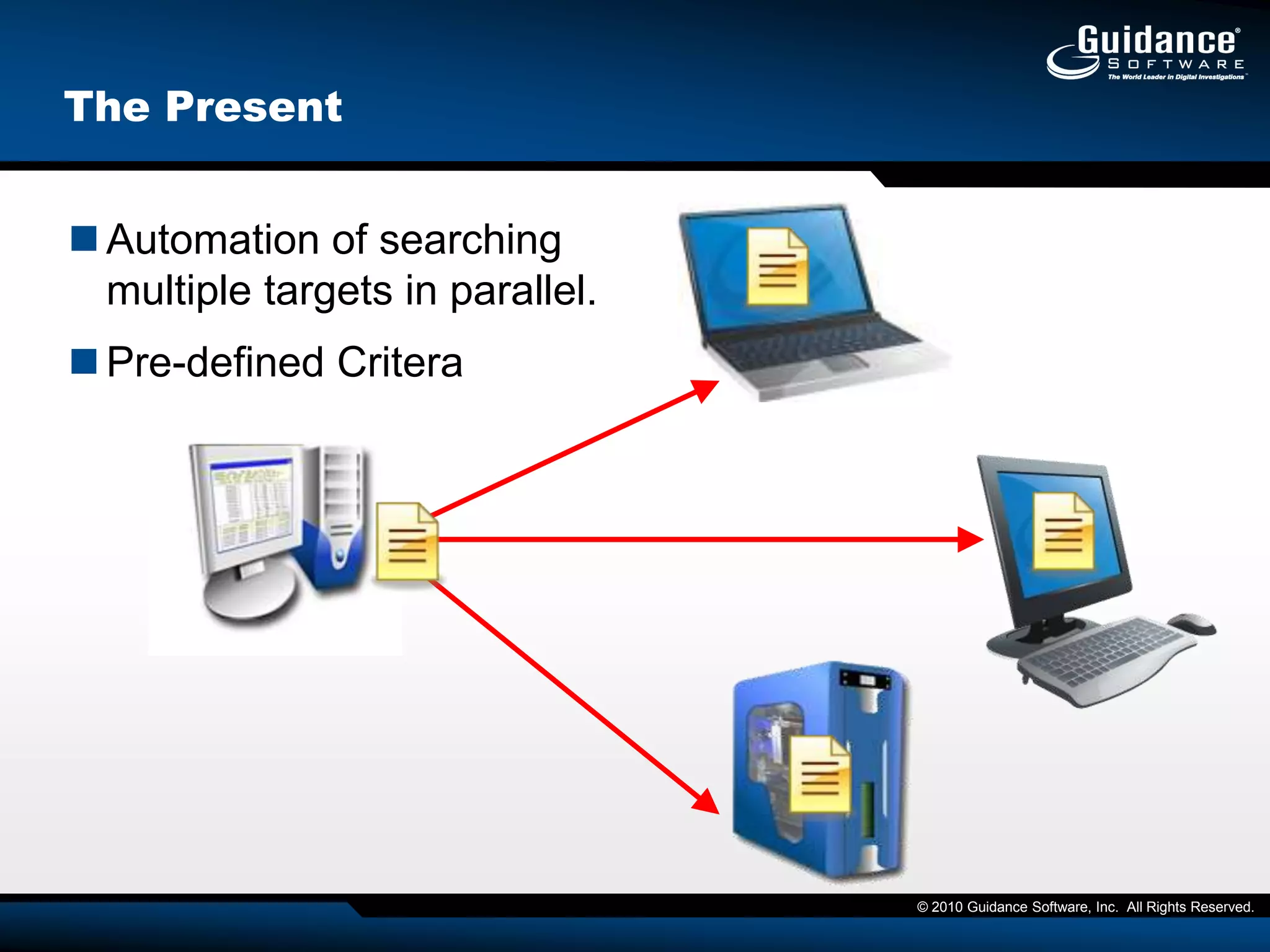
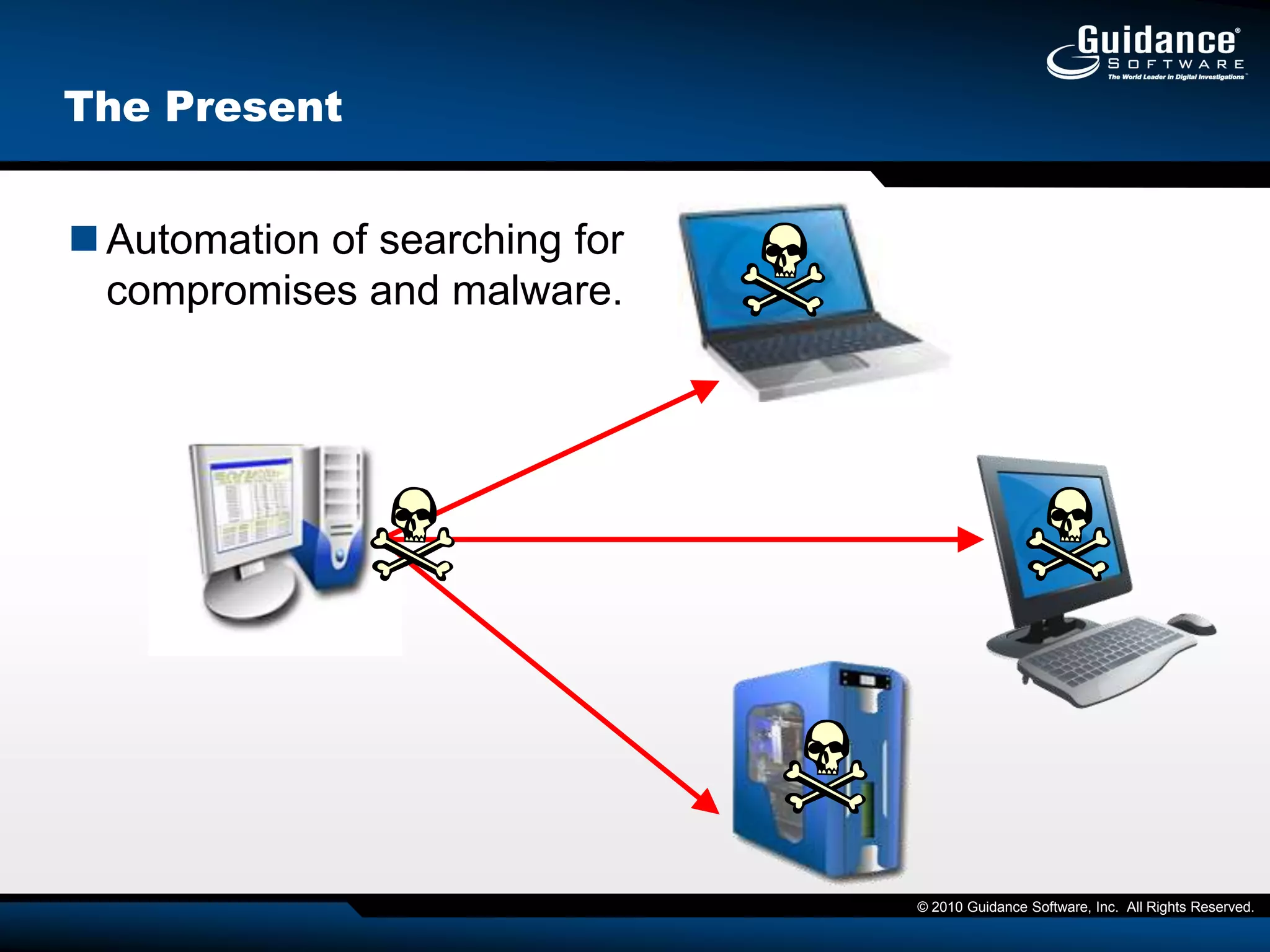
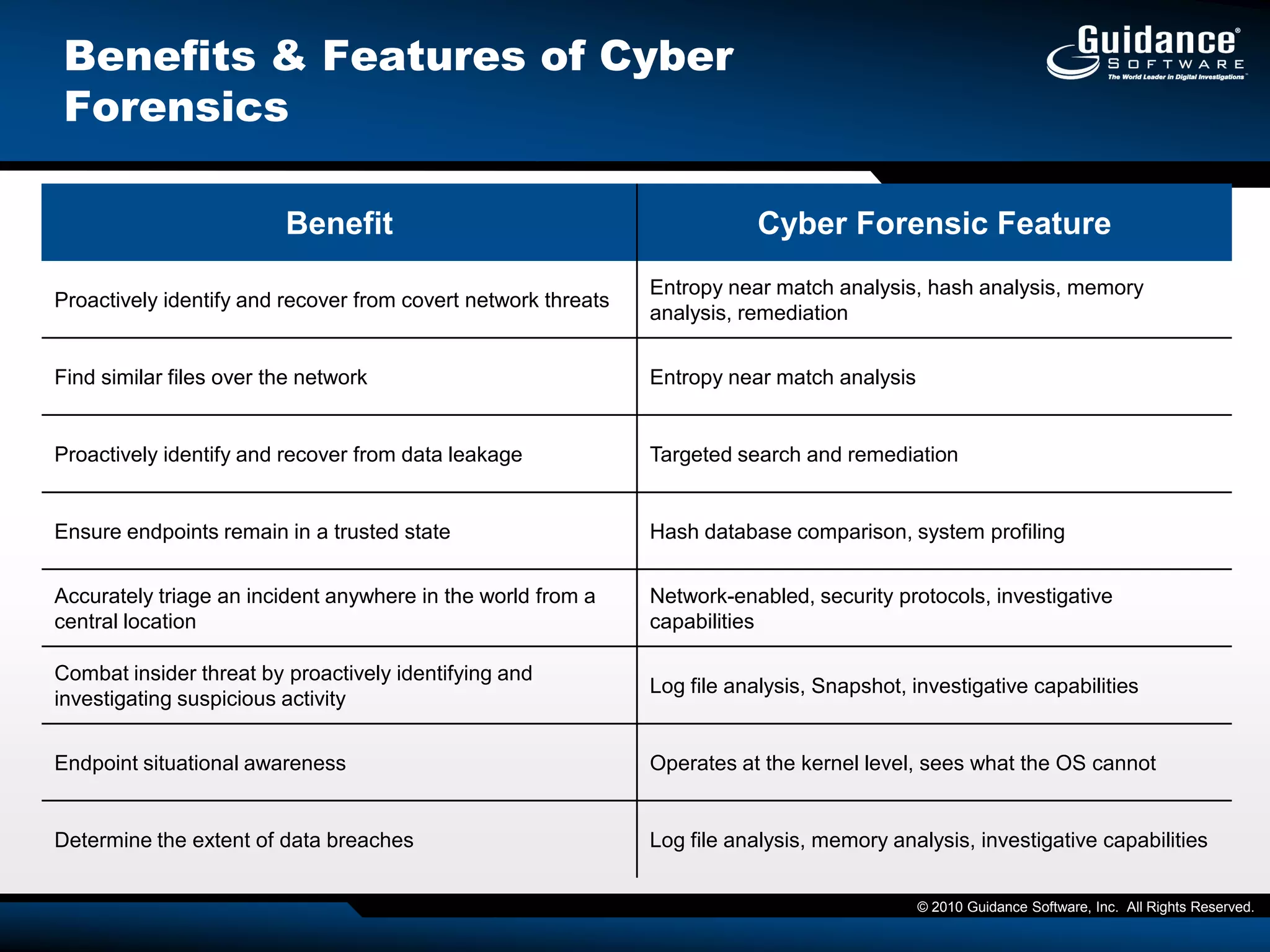
This document discusses the need for cyber forensics capabilities to effectively respond to modern cybersecurity threats and incidents. It notes that traditional perimeter-based defenses are no longer sufficient, and that comprehensive endpoint visibility is needed to identify covert threats, attribute attacks, and limit data breaches. The document promotes the Guidance Software EnCase Cybersecurity solution as providing critical network-enabled incident response and forensic investigation capabilities for enterprises.