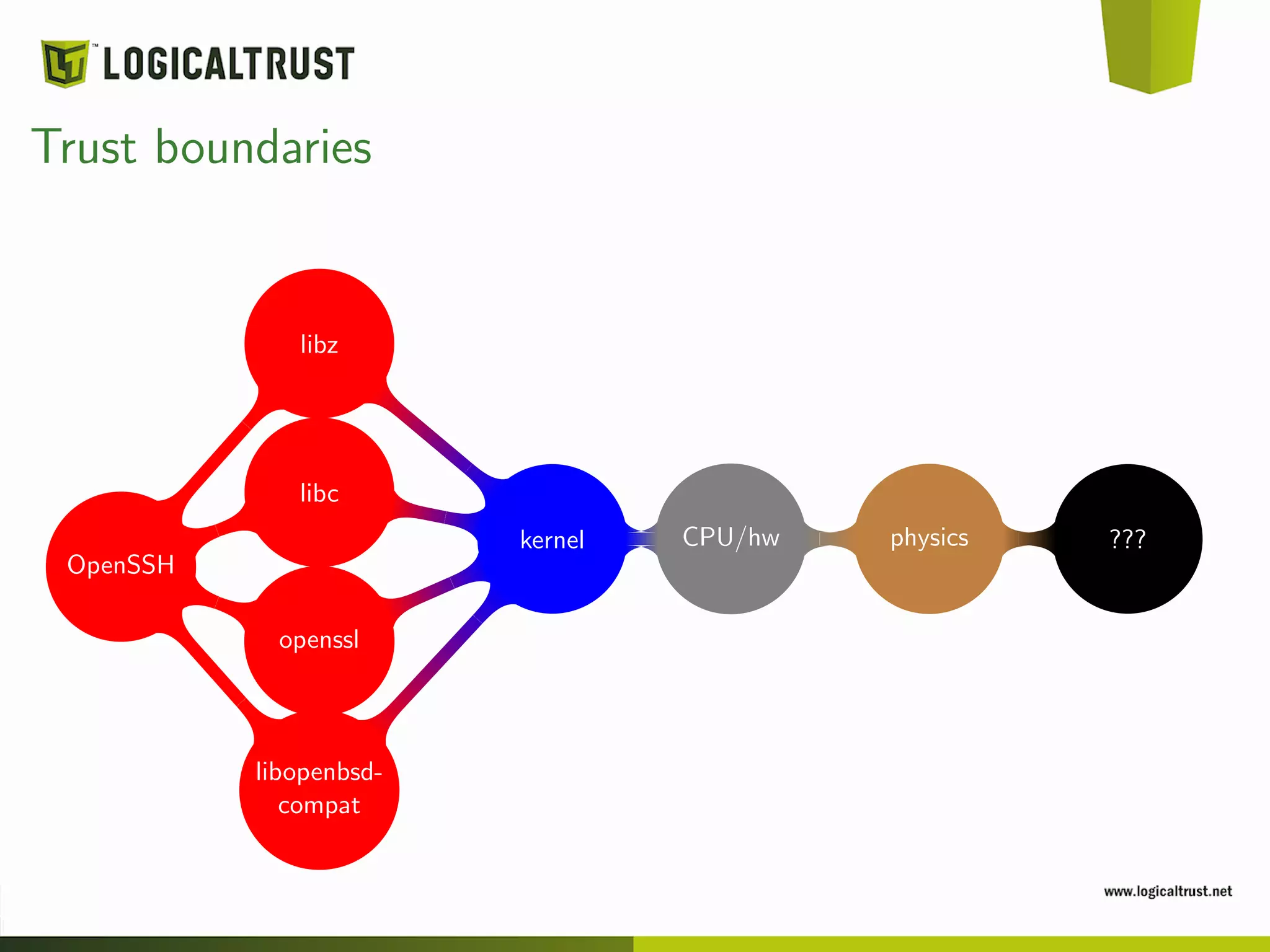
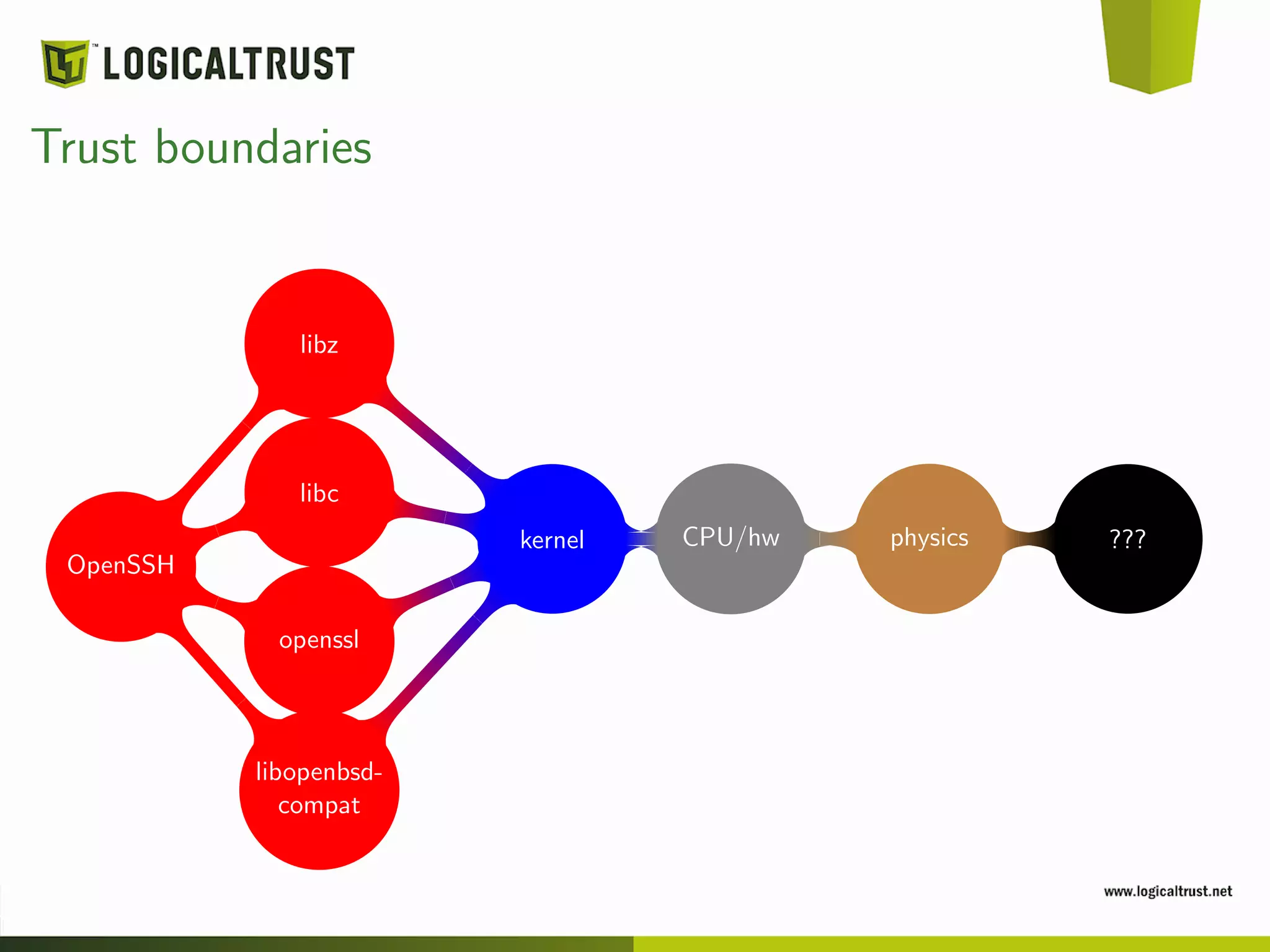
The document discusses the concept of trust boundaries in software security, emphasizing the inherent assumptions made when trusting certain applications. It critiques popular software like OpenSSH and OpenSSL, highlighting potential vulnerabilities and flaws in their code. Ultimately, the presentation promotes a cautious and critical approach towards trusting software, advocating for open-source transparency and reproducibility in builds.

















![OpenSSH - potential stack overflow
key.c:
static int
cert_parse(Buffer *b, Key *key, const u_char *blob, u_int blen)
{
u_char *principals, *critical, *exts, *sig_key, *sig;
u_int signed_len, plen, clen, sklen, slen, kidlen, elen;
Buffer tmp;
char *principal;
int ret = -1;
int v00 = key->type == KEY_DSA_CERT_V00 ||
key->type == KEY_RSA_CERT_V00;
[...]
if ((key->cert->signature_key = key_from_blob(sig_key,
sklen)) == NULL) {
[...]
Key *
key_from_blob(const u_char *blob, u_int blen)
{
[...]
if (key_is_cert(key) && cert_parse(&b, key, blob, blen) == -1) {
error("key_from_blob: can’t parse cert data");
goto badkey;
}
[...]
Fixed a year or two ago, left here for historical reasons... key from blob can
be called remotely using pubkey authentication. If you’re interested then take
a look to previous versions of auth2-pubkey.c.](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-19-2048.jpg)
![OpenSSH - potential stack overflow
(Un)fortunately certificate is handled by the Buffer structure, which
maximum length is bounded:
buffer.c:
#define BUFFER_MAX_CHUNK 0x100000
[...]
void *
buffer_append_space(Buffer *buffer, u_int len)
{
u_int newlen;
void *p;
if (len > BUFFER_MAX_CHUNK)
fatal("buffer_append_space: len %u not supported", len);
No cookies this time, but maybe somewhere in space there are systems (or
configurations) which are exploitable. (Bounded stack + something
important near to it).](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-20-2048.jpg)








![Libraries - LibreSSL - off-by-one #1
Let’s take BIGNUM −0 and apply it to the BN bn2hex
crypto/bn/bn print.c:
char *BN_bn2hex(const BIGNUM *a)
{
char *buf;
char *p;
buf=(char *)OPENSSL_malloc(a->top*BN_BYTES*2+2);
[...]
p=buf;
if (a->neg) *(p++)=’-’;
if (BN_is_zero(a)) *(p++)=’0’;
for (i=a->top-1; i >=0; i--)
[...]
*p=’0’;
How to get −0 in LibreSSL? It is a task for the listener](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-30-2048.jpg)
![Libraries - LibreSSL - off-by-one #2
Let’s call BN rand(BN, 1, 1, 0)- bnrand crypto/bn/bn rand.c:
static int
bnrand(int pseudorand, BIGNUM *rnd, int bits, int top, int bottom)
{
unsigned char *buf = NULL;
[...]
bytes = (bits + 7) / 8;
bit = (bits - 1) % 8;
buf = OPENSSL_malloc(bytes);
if (top != -1) {
if (top) {
if (bit == 0) {
buf[0] = 1;
buf[1] |= 0x80;
[...]](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-31-2048.jpg)
![Libraries - libz
zlib - easy, small library for data compression/decompression
inflate.c:
int ZEXPORT inflateInit_(strm, version, stream_size)
z_streamp strm;
const char *version;
int stream_size;
{
return inflateInit2_(strm, DEF_WBITS, version, stream_size);
}
[...]
int ZEXPORT inflateInit2_(strm, windowBits, version, stream_size)
z_streamp strm;
int windowBits;
const char *version;
int stream_size;
{
[...]
struct inflate_state FAR *state;
[...]
if (strm->zalloc == (alloc_func)0) {
[...]
}
state = (struct inflate_state FAR *)
ZALLOC(strm, 1, sizeof(struct inflate_state));
[...]
strm->state = (struct internal_state FAR *)state;
state->window = Z_NULL;
ret = inflateReset2(strm, windowBits);
[...]
}](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-32-2048.jpg)
![Libraries - libz cont.
inflate.c:
int ZEXPORT inflateReset2(strm, windowBits)
z_streamp strm;
int windowBits;
{
int wrap;
struct inflate_state FAR *state;
if (strm == Z_NULL || strm->state == Z_NULL) return Z_STREAM_ERROR;
state = (struct inflate_state FAR *)strm->state;
if (windowBits < 0) {
wrap = 0;
windowBits = -windowBits;
} else {
wrap = (windowBits >> 4) + 1;
}
/* set number of window bits, free window if different */
if (windowBits && (windowBits < 8 || windowBits > 15))
return Z_STREAM_ERROR;
if (state->window != Z_NULL && state->wbits != (unsigned)windowBits) {
ZFREE(strm, state->window);
state->window = Z_NULL;
}
[...]
OpenSSH is not affected, but how about other popular software? YES IT IS!](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-33-2048.jpg)
![Libraries - libc - dobule free - getaddrinfo IDN
$ traceroute $(printf "302a")
*** glibc detected *** traceroute: munmap_chunk(): invalid pointer: 0x00007fff1b43a547 ***
======= Backtrace: =========
/lib64/libc.so.6(cfree+0x166)[0x32244758c6]
/lib64/libc.so.6[0x32244bc116]
/lib64/libc.so.6(getaddrinfo+0x21a)[0x32244be94a]
traceroute[0x402926]
traceroute[0x4029f1]
traceroute[0x406281]
traceroute[0x403546]
/lib64/libc.so.6(__libc_start_main+0xf4)[0x322441d9f4]
traceroute[0x401619]
======= Memory map: ========
00400000-00409000 r-xp 00000000 68:06 7103807 /bin/traceroute
00608000-00609000 rw-p 00008000 68:06 7103807 /bin/traceroute
00609000-0060a000 rw-p 00609000 00:00 0
00808000-00809000 rw-p 00008000 68:06 7103807 /bin/traceroute
00ff7000-01018000 rw-p 00ff7000 00:00 0 [heap]
3224000000-322401c000 r-xp 00000000 68:06 7332914 /lib64/ld-2.5.so
http://www.openwall.com/lists/oss-security/2015/01/27/11](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-34-2048.jpg)


![Kernel - FreeBSD - IGMP - CVE-2015-1414
netinet/igmp.c:
case IGMP_VERSION_3: {
struct igmpv3 *igmpv3;
uint16_t igmpv3len;
uint16_t srclen;
int nsrc;
[...]
igmpv3 = (struct igmpv3 *)igmp;
/* Validate length based on source count. */
nsrc = ntohs(igmpv3->igmp_numsrc);
srclen = sizeof(struct in_addr) * nsrc;
if (nsrc * sizeof(in_addr_t) > srclen) {
IGMPSTAT_INC(igps_rcv_tooshort);
return;
}
[...]
igmpv3len = iphlen + IGMP_V3_QUERY_MINLEN +
srclen;
if ((m->m_flags & M_EXT ||
m->m_len < igmpv3len) &&
(m = m_pullup(m, igmpv3len)) == NULL) {
IGMPSTAT_INC(igps_rcv_tooshort);
return;
}
igmpv3 = (struct igmpv3 *)(mtod(m, uint8_t *)
+ iphlen);
if (igmp_input_v3_query(ifp, ip, igmpv3) != 0) {
[...]](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-37-2048.jpg)
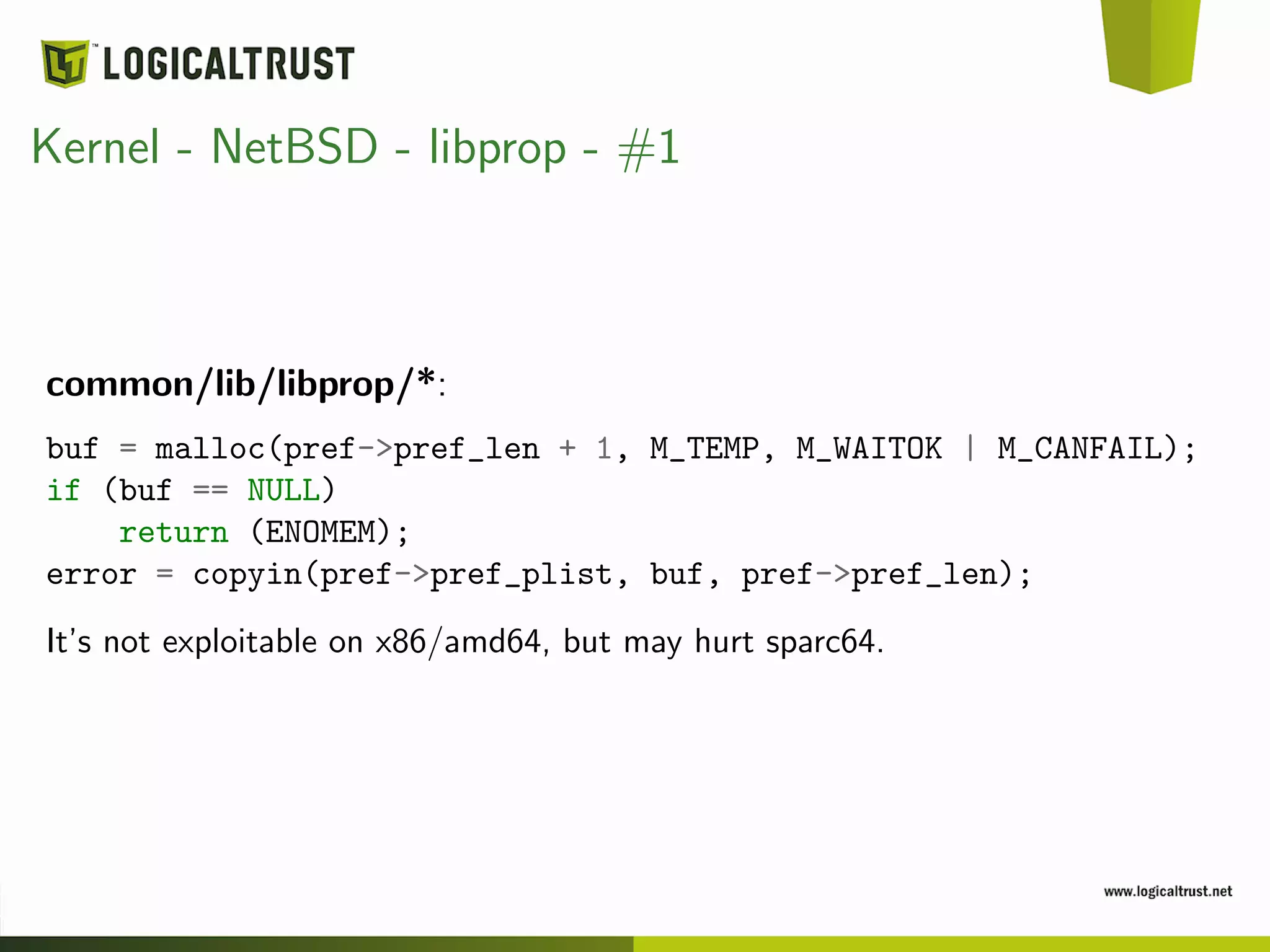
![Kernel - NetBSD - libprop - #2
common/lib/libprop/*:
#define _PROP_EOF(c) ((c) == ’0’)
#define _PROP_ISSPACE(c)
((c) == ’ ’ || (c) == ’t’ || (c) == ’n’ || (c) == ’r’ ||
_PROP_EOF(c))
struct _prop_object_internalize_context *
_prop_object_internalize_context_alloc(const char *xml)
{
[...]
/*
* Skip any whitespace and XML preamble stuff that we don’t
* know about / care about.
*/
for (;;) {
while (_PROP_ISSPACE(*xml))
xml++;](https://image.slidesharecdn.com/granice-150619131645-lva1-app6891/75/Trust-boundaries-Confidence-2015-39-2048.jpg)