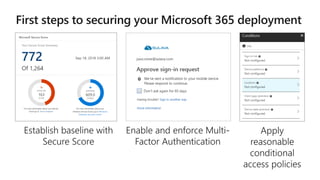
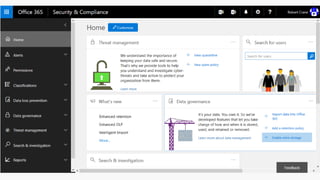
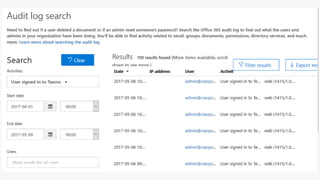
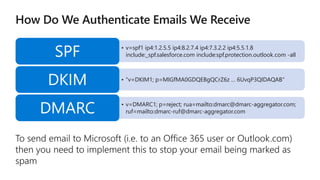
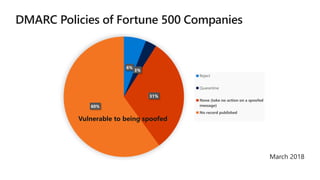
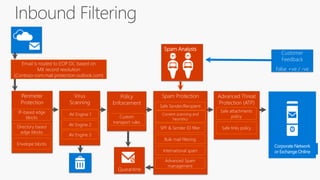
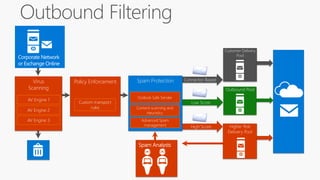
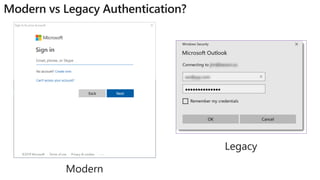
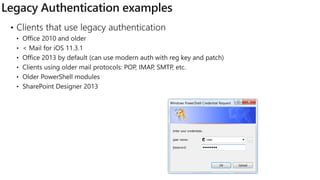
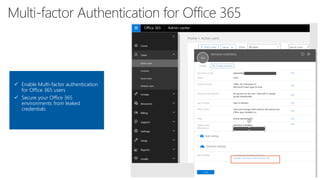
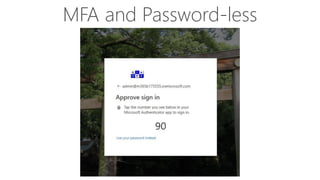
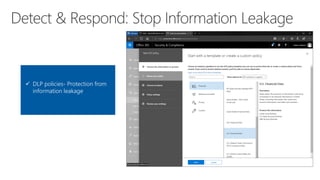
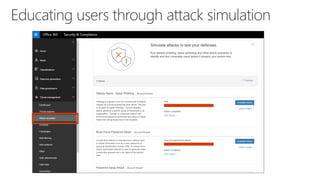
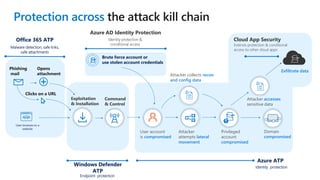
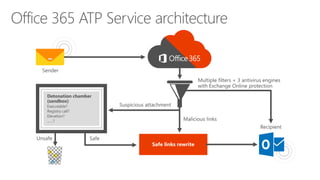
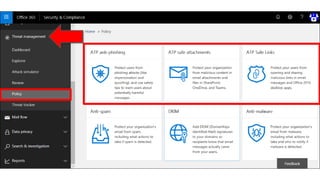
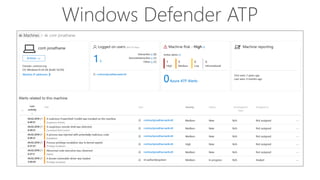
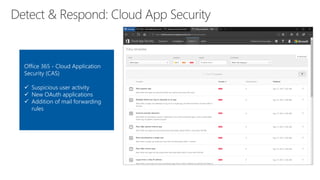
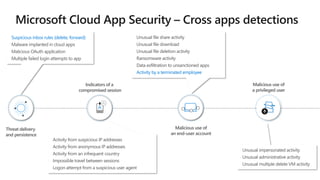
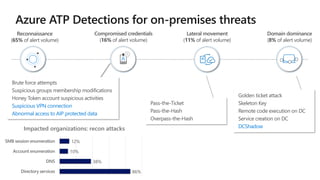
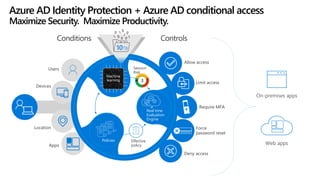
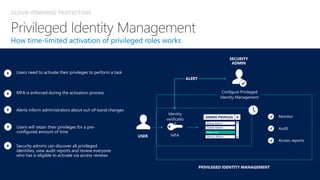
The document provides details about a Microsoft 365 webinar held in December 2019, covering updates, security challenges, and best practices. Key topics include the increase in identity attacks, securing cloud apps, and features like data loss prevention and encrypted messaging. Resources and links for further information and training on Microsoft 365 are also shared.