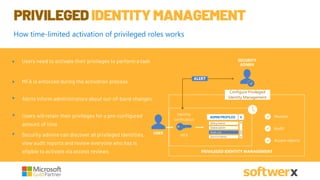
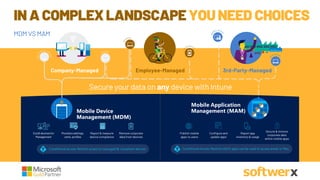
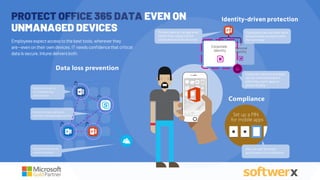
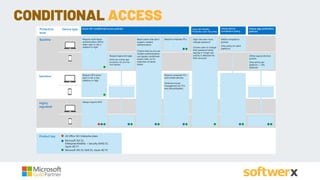
The document discusses managing vulnerabilities in Microsoft 365, highlighting the importance of leveraging existing security features and providing a roadmap for comprehensive security. It emphasizes the necessity of advanced threat protection, identity and access management, and mobile device management to protect against rising incidents of account compromises. Additionally, it offers practical recommendations for enhancing security posture through tools like multi-factor authentication and data loss prevention strategies.