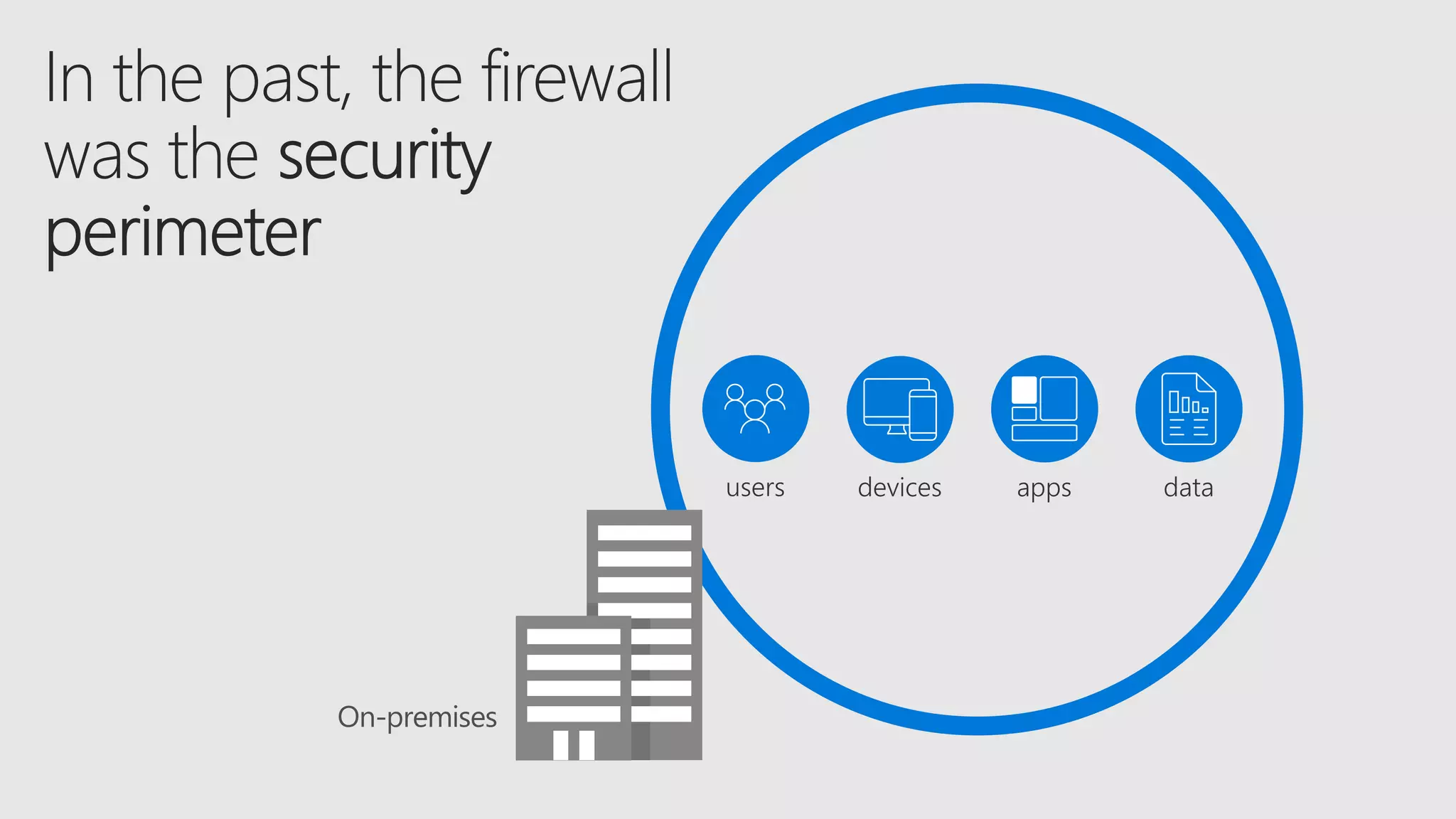
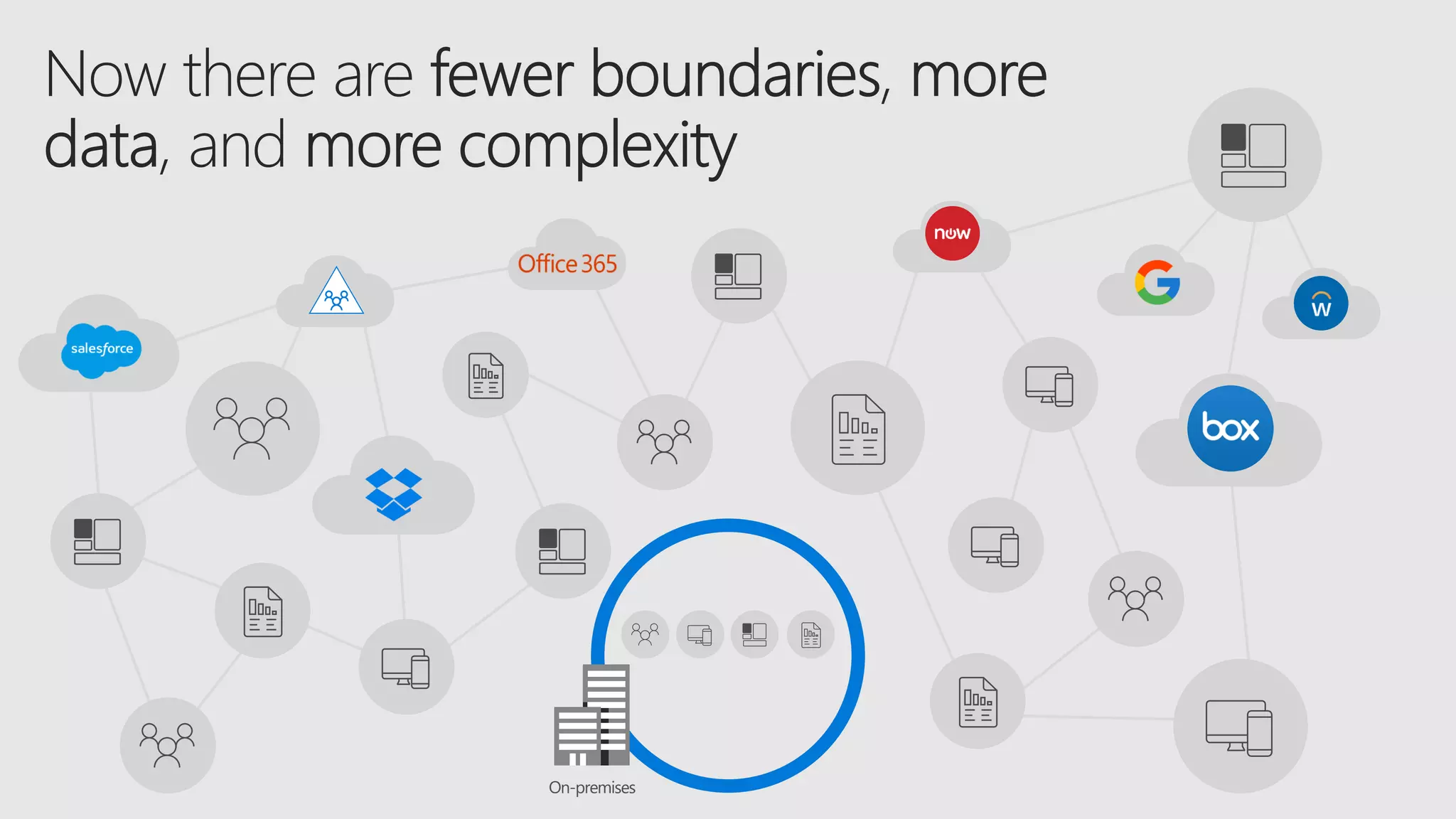
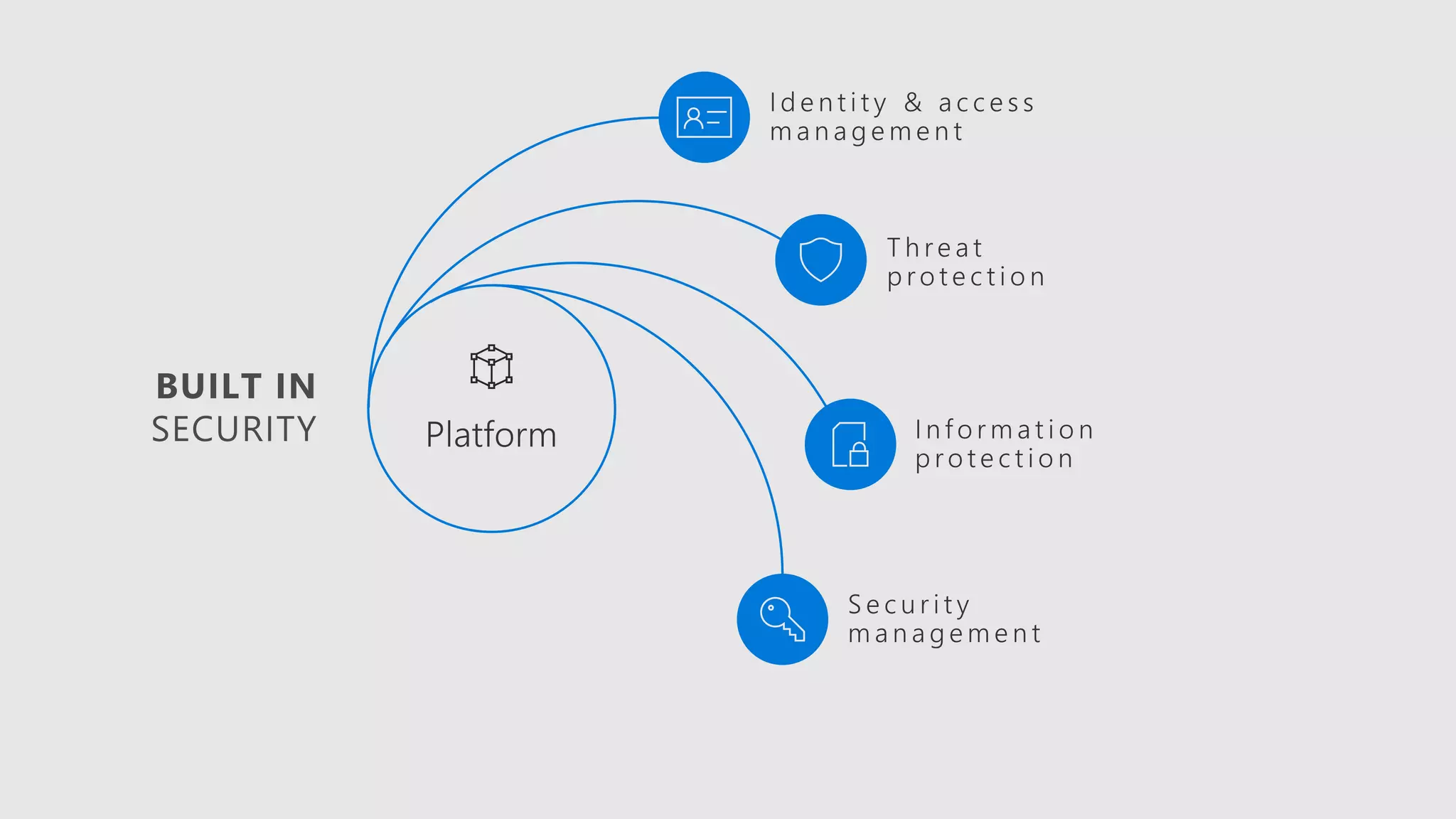
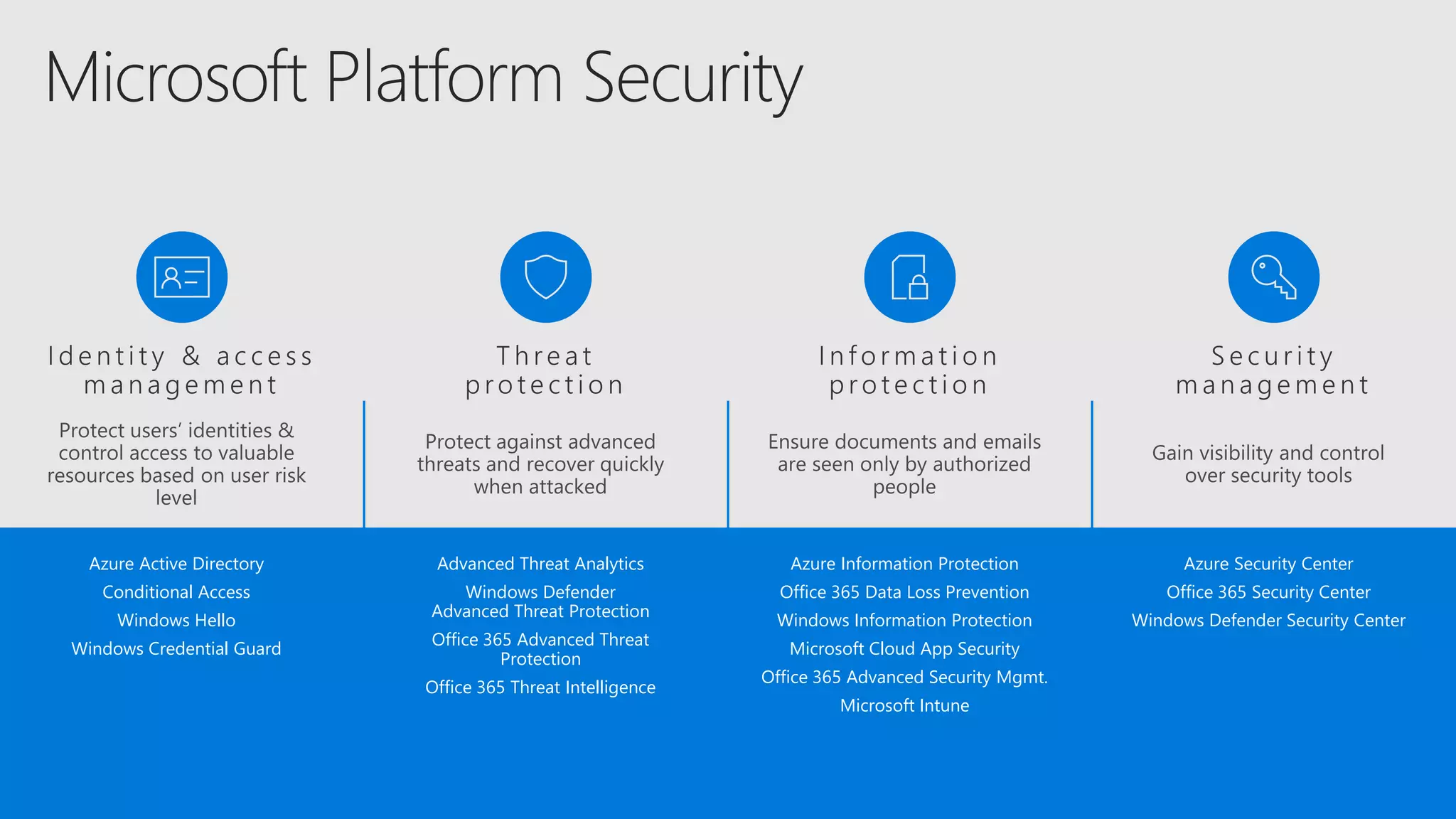
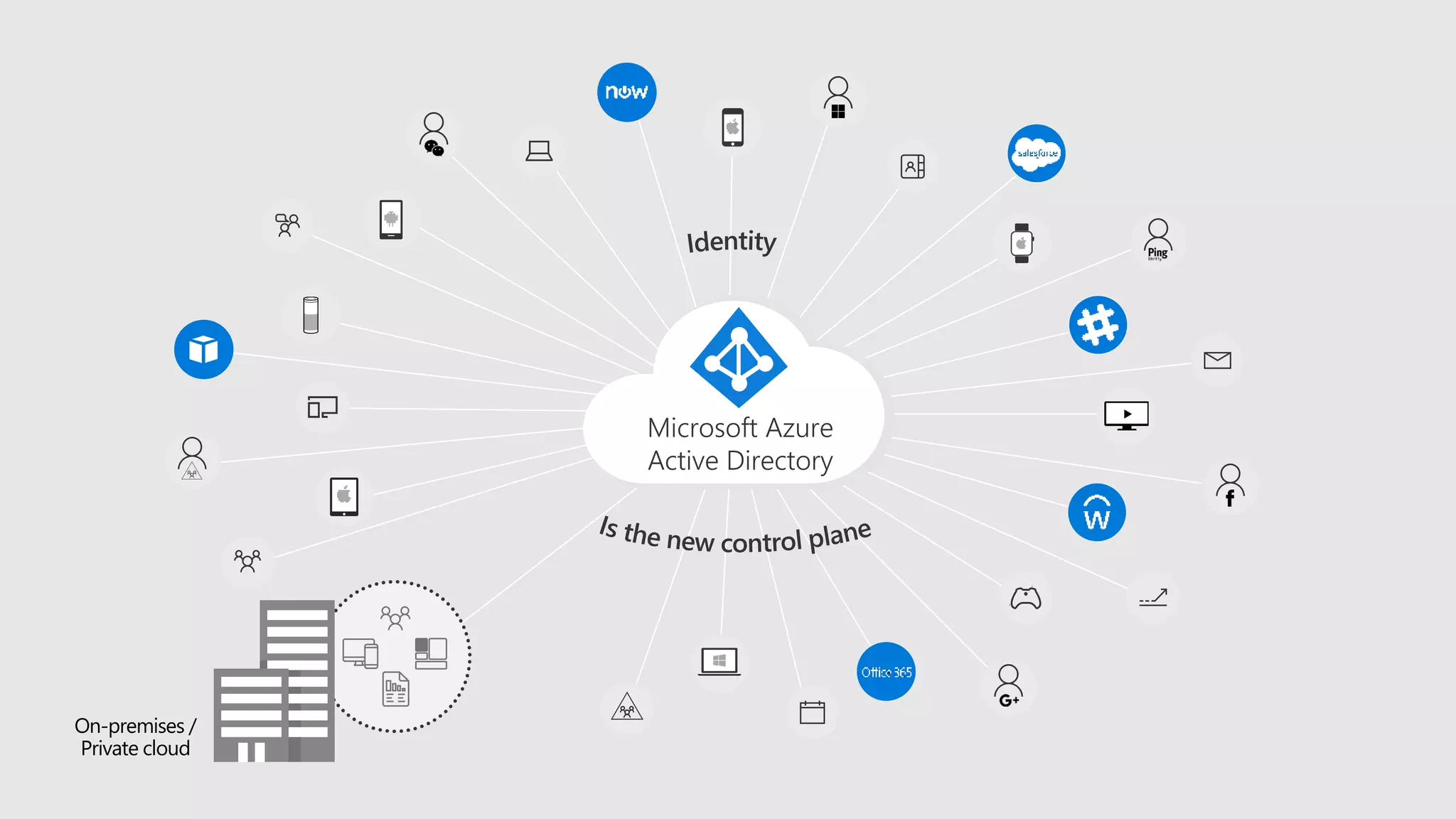
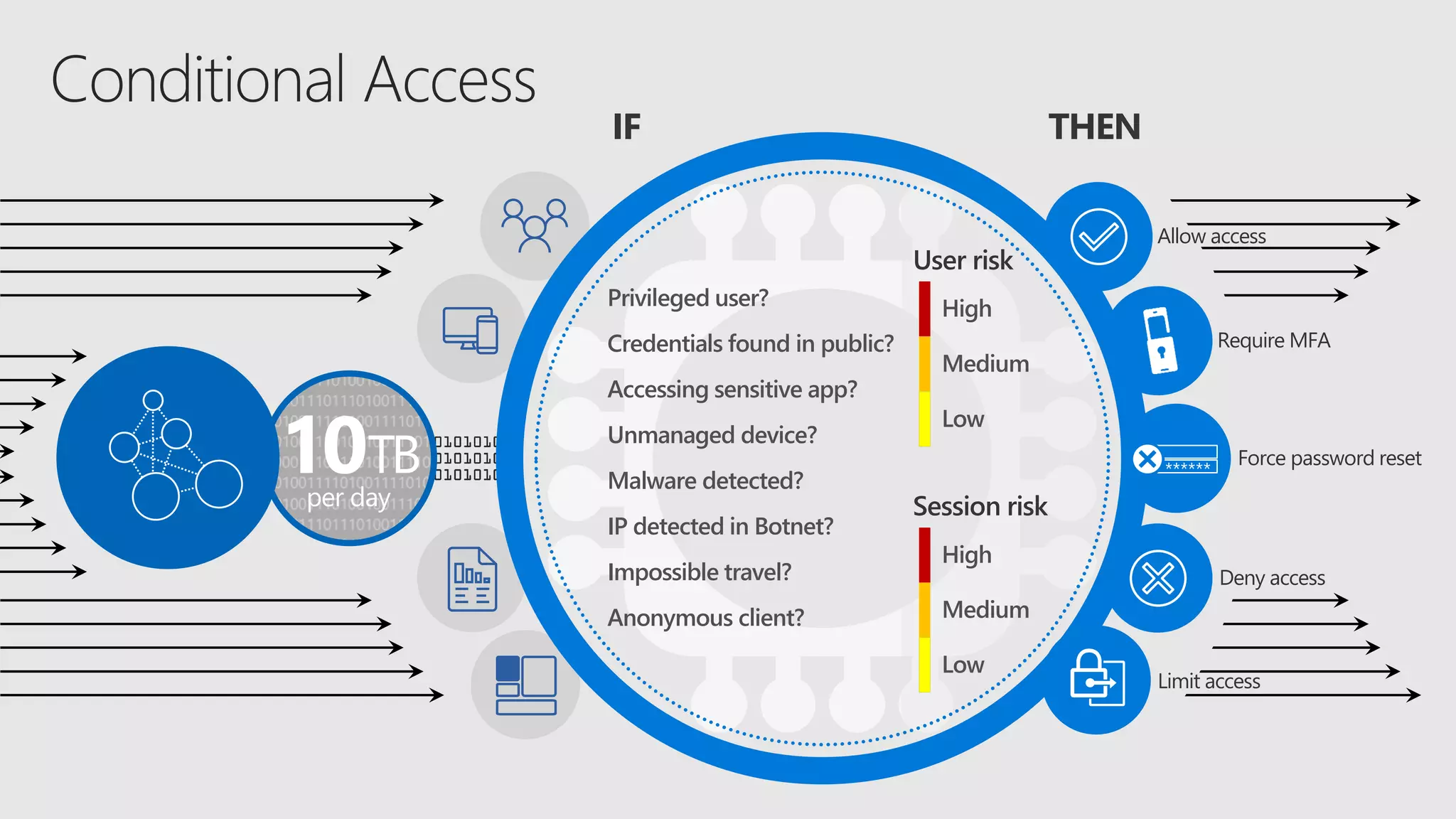
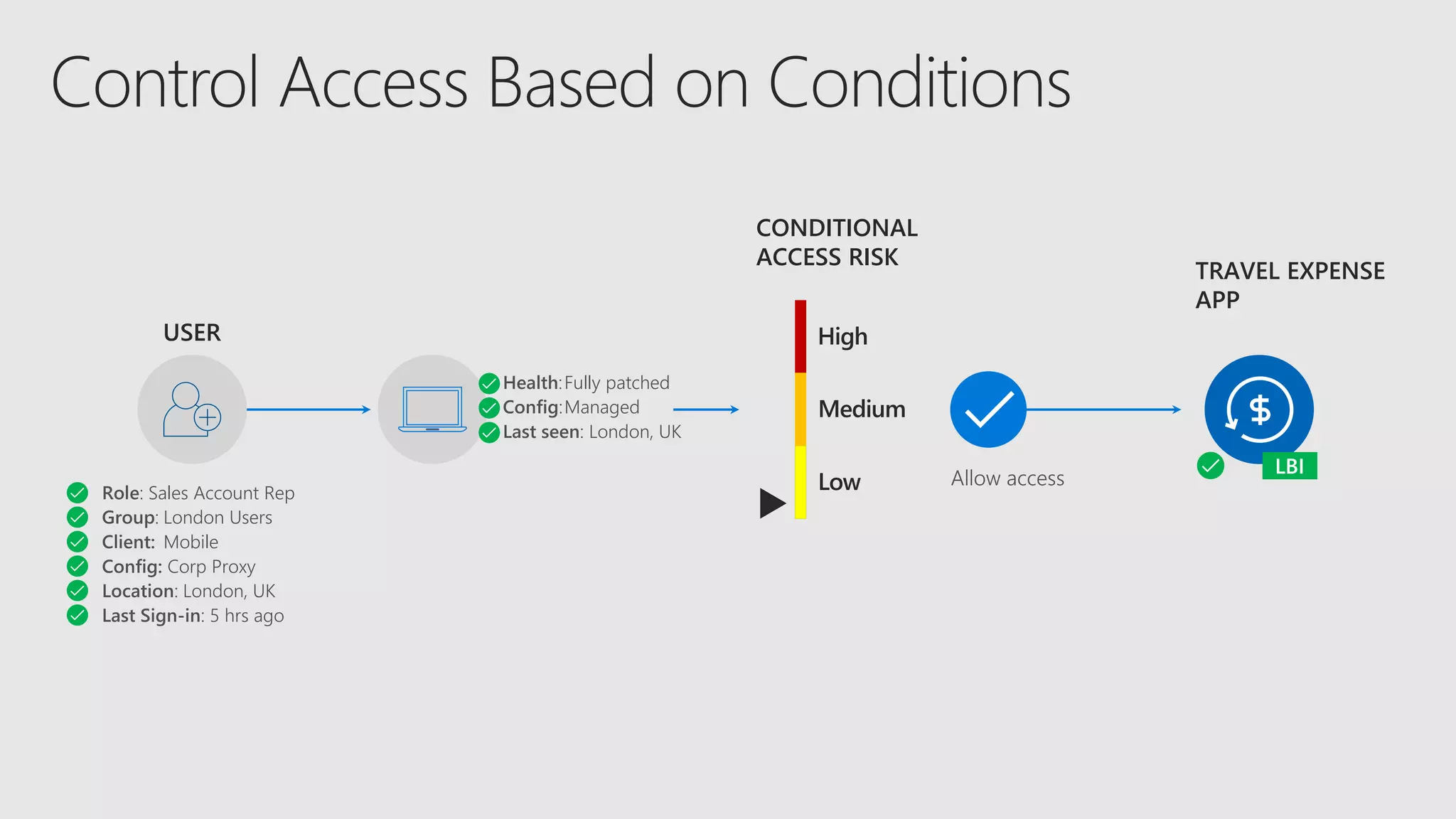
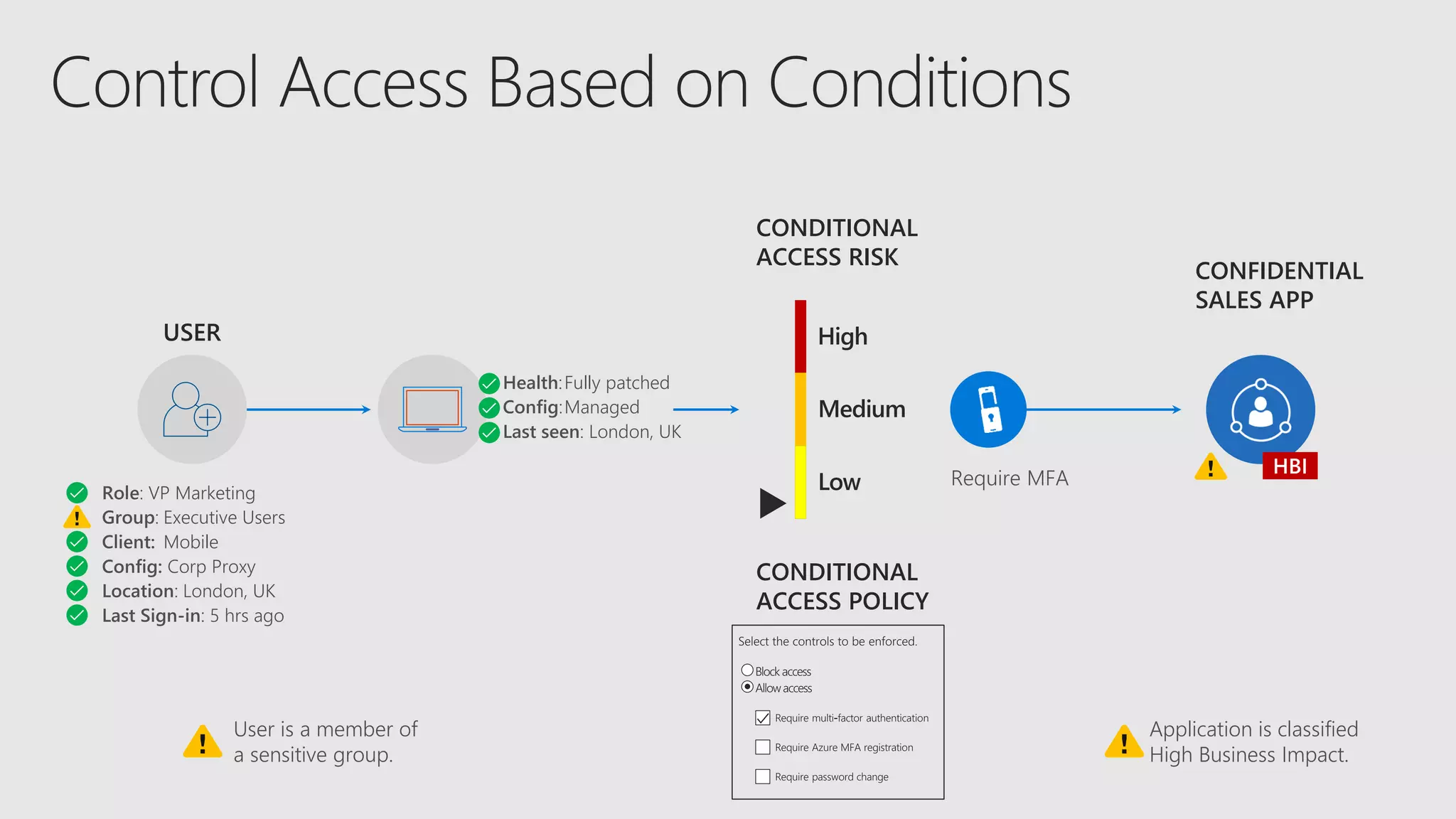
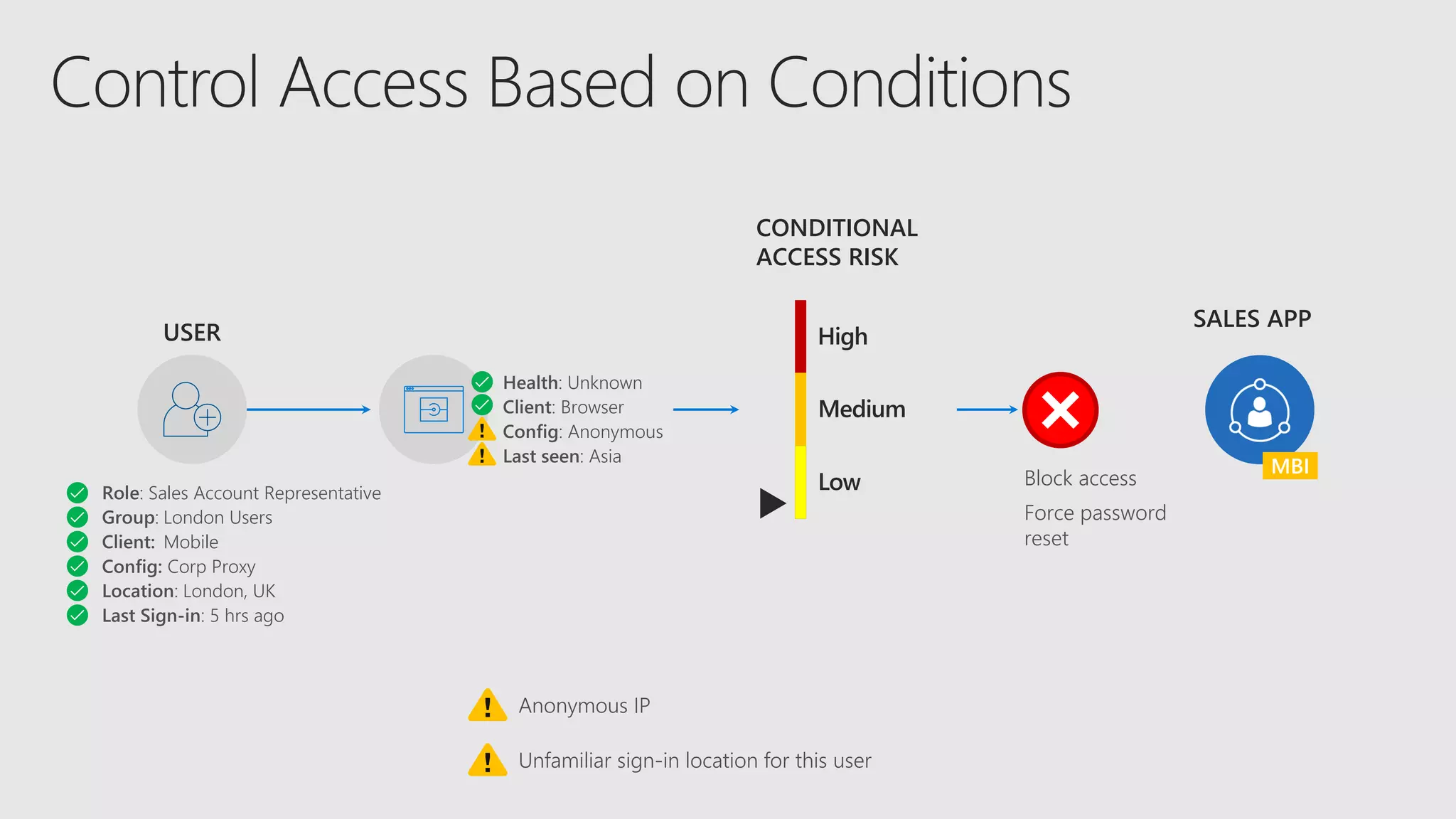
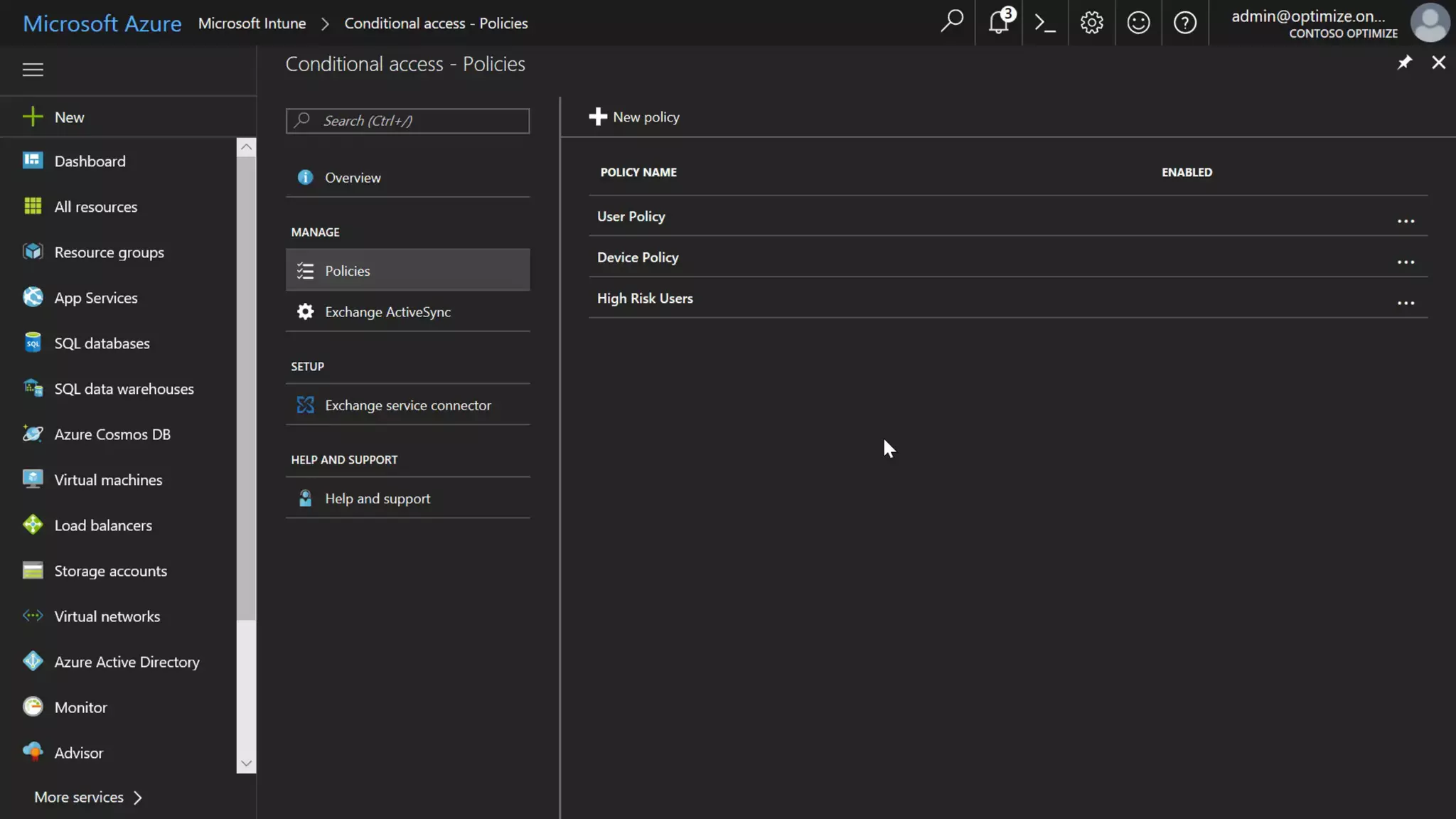
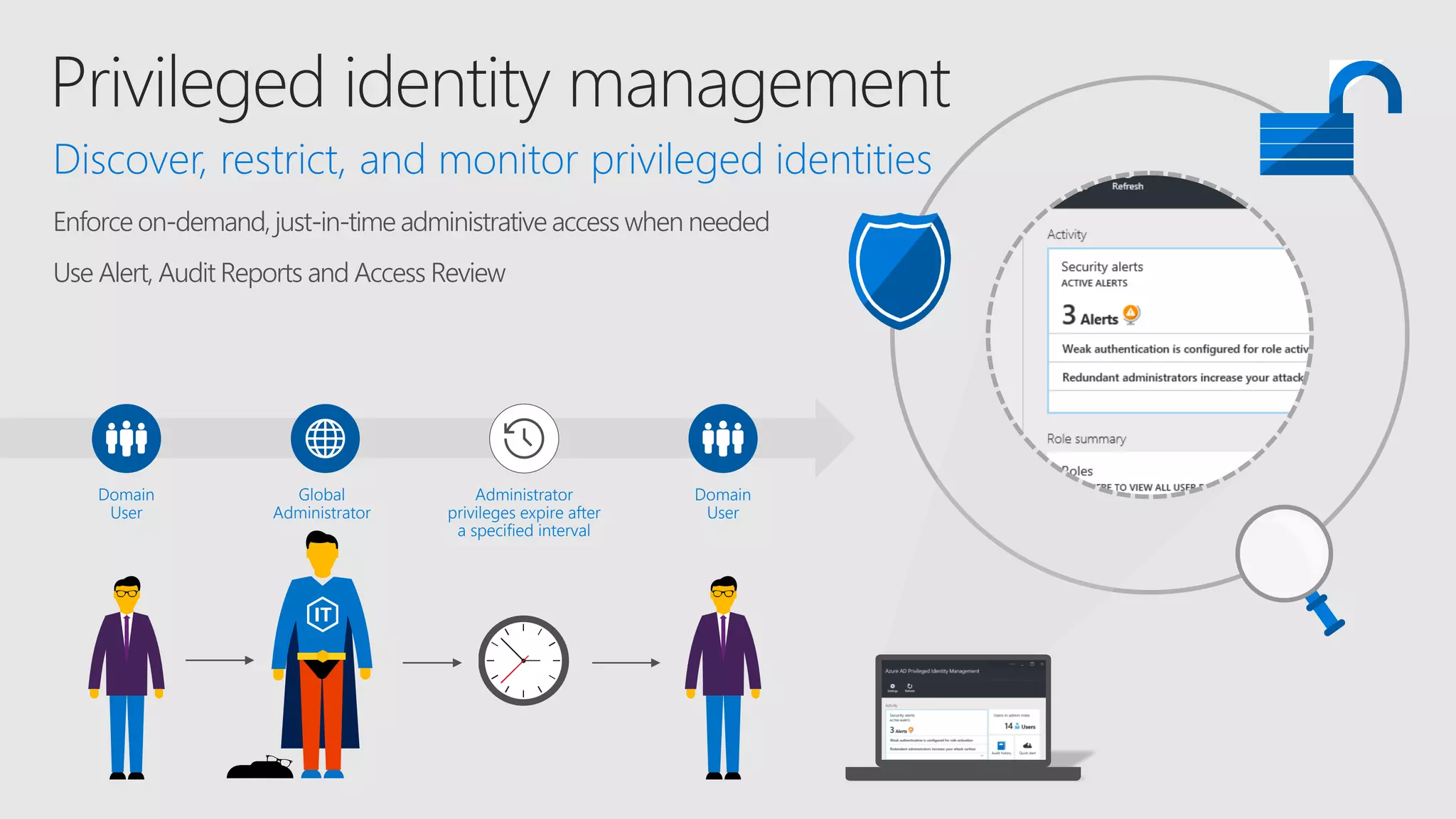
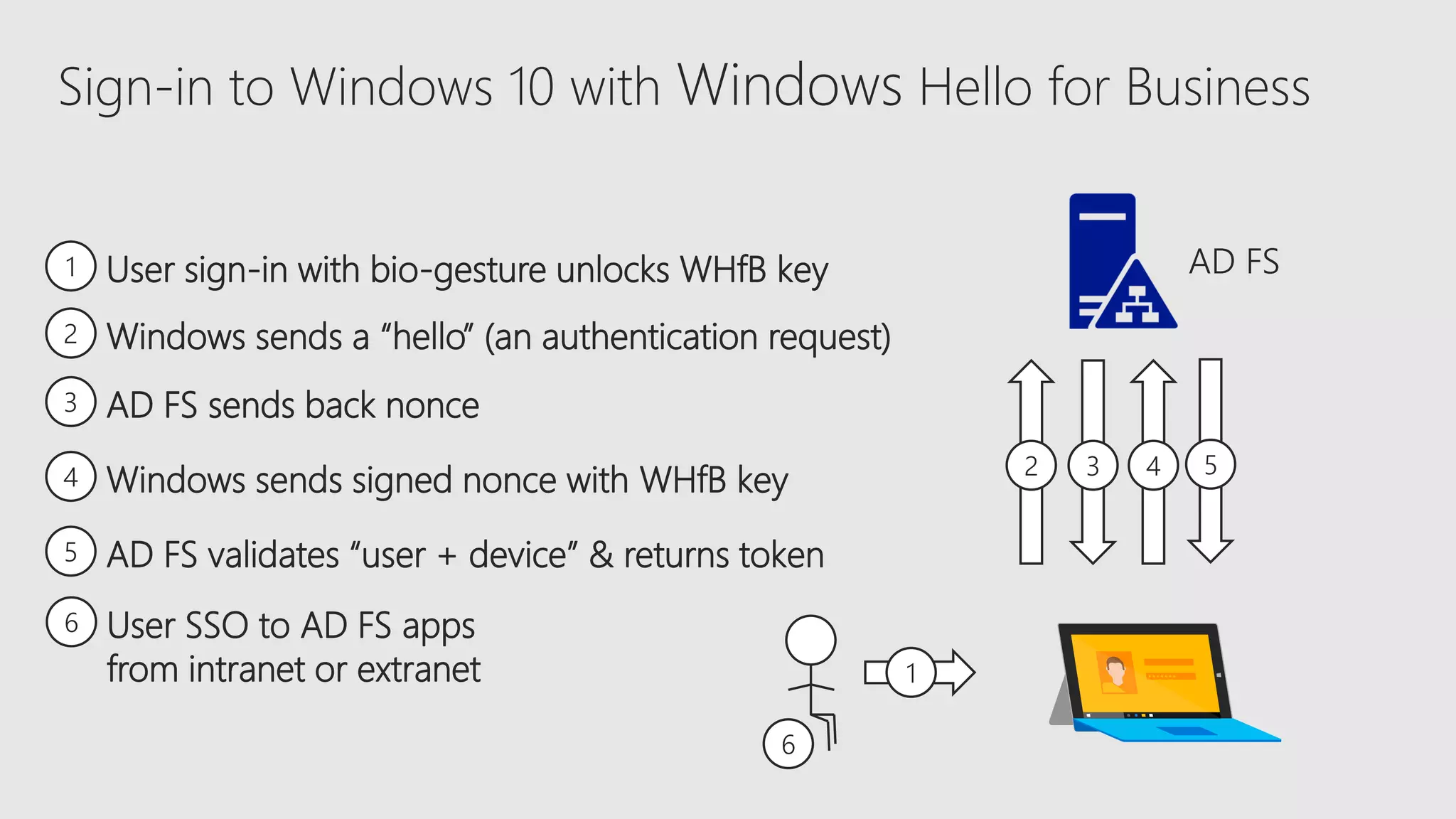
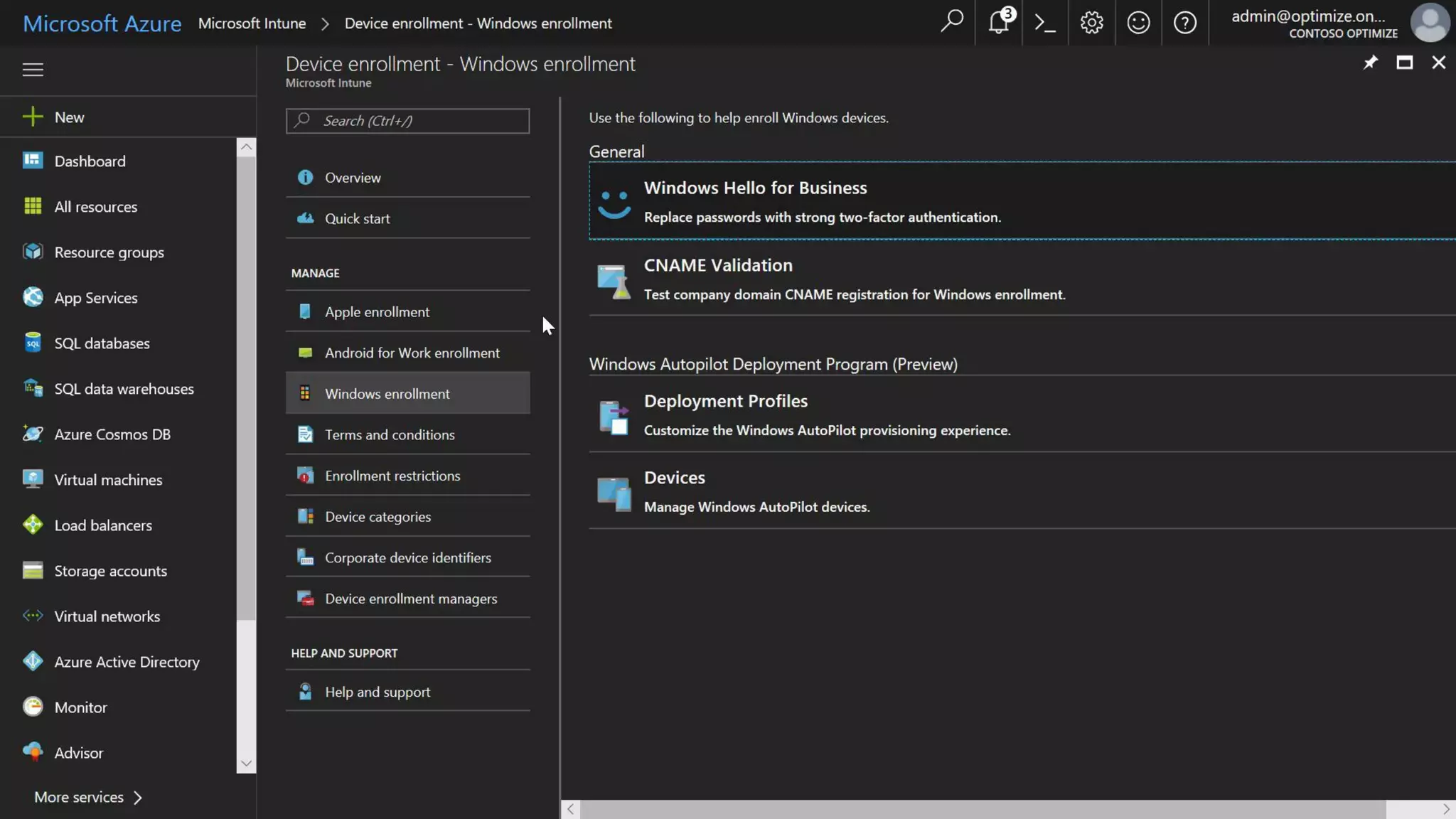
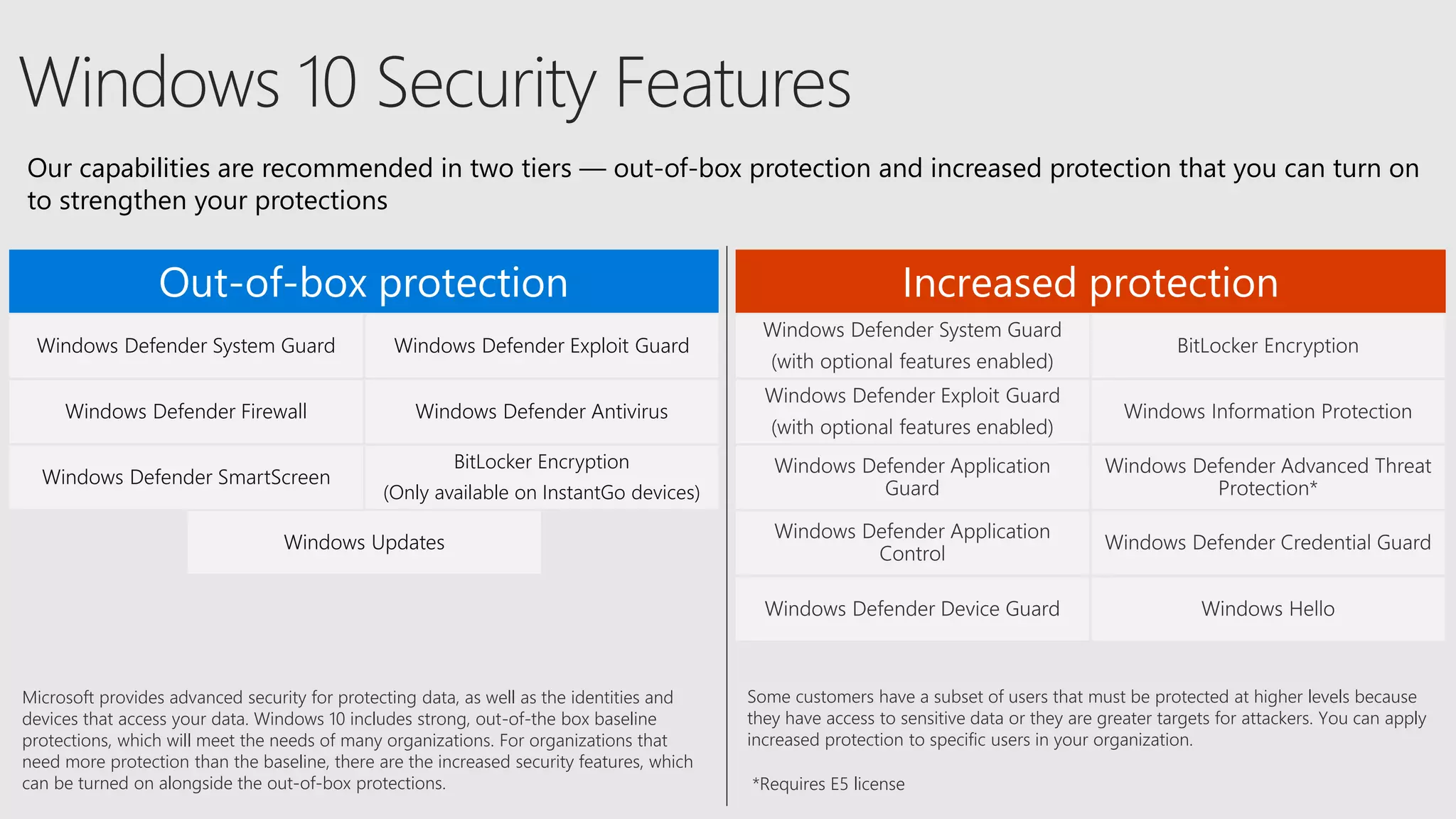
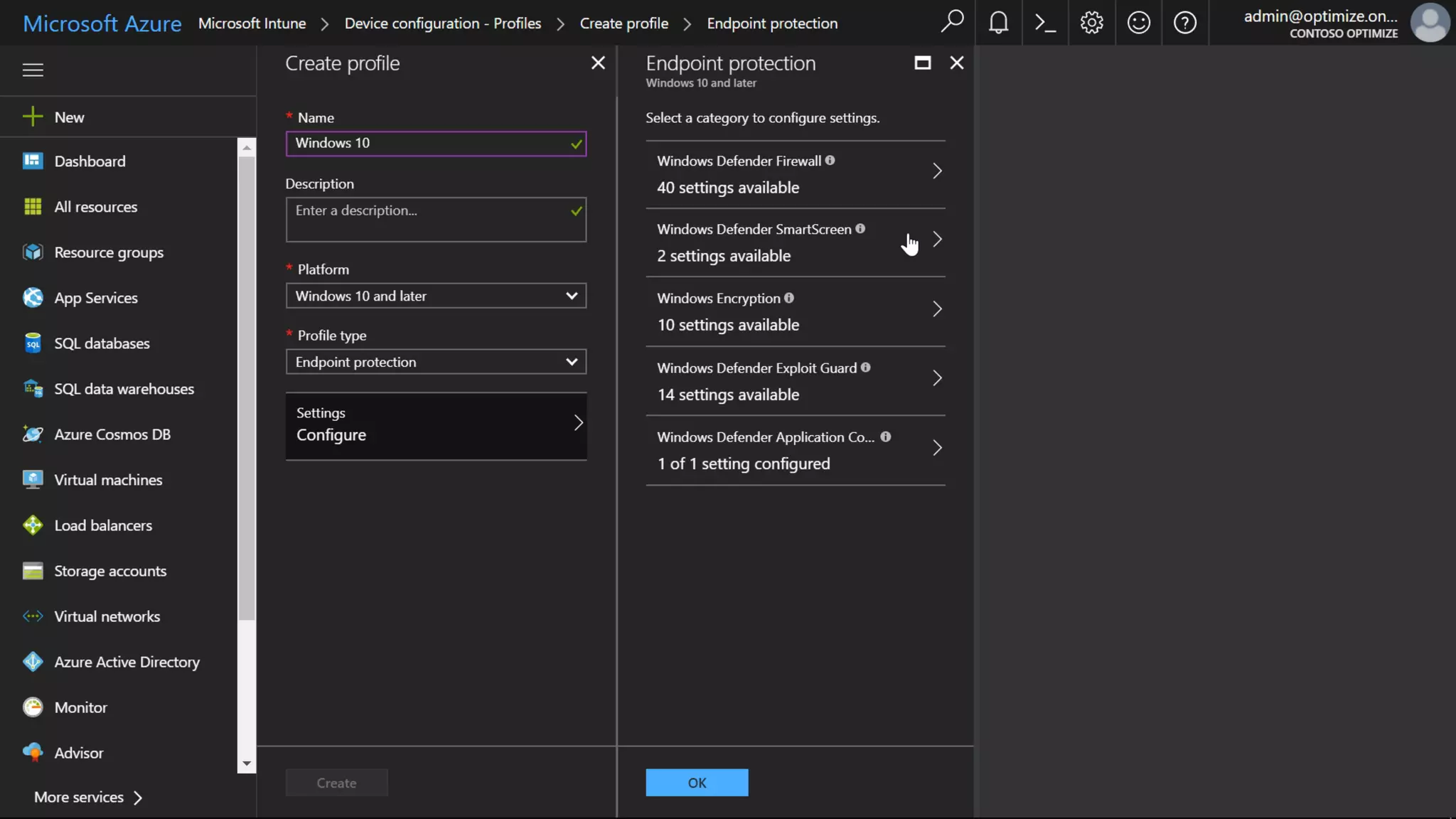
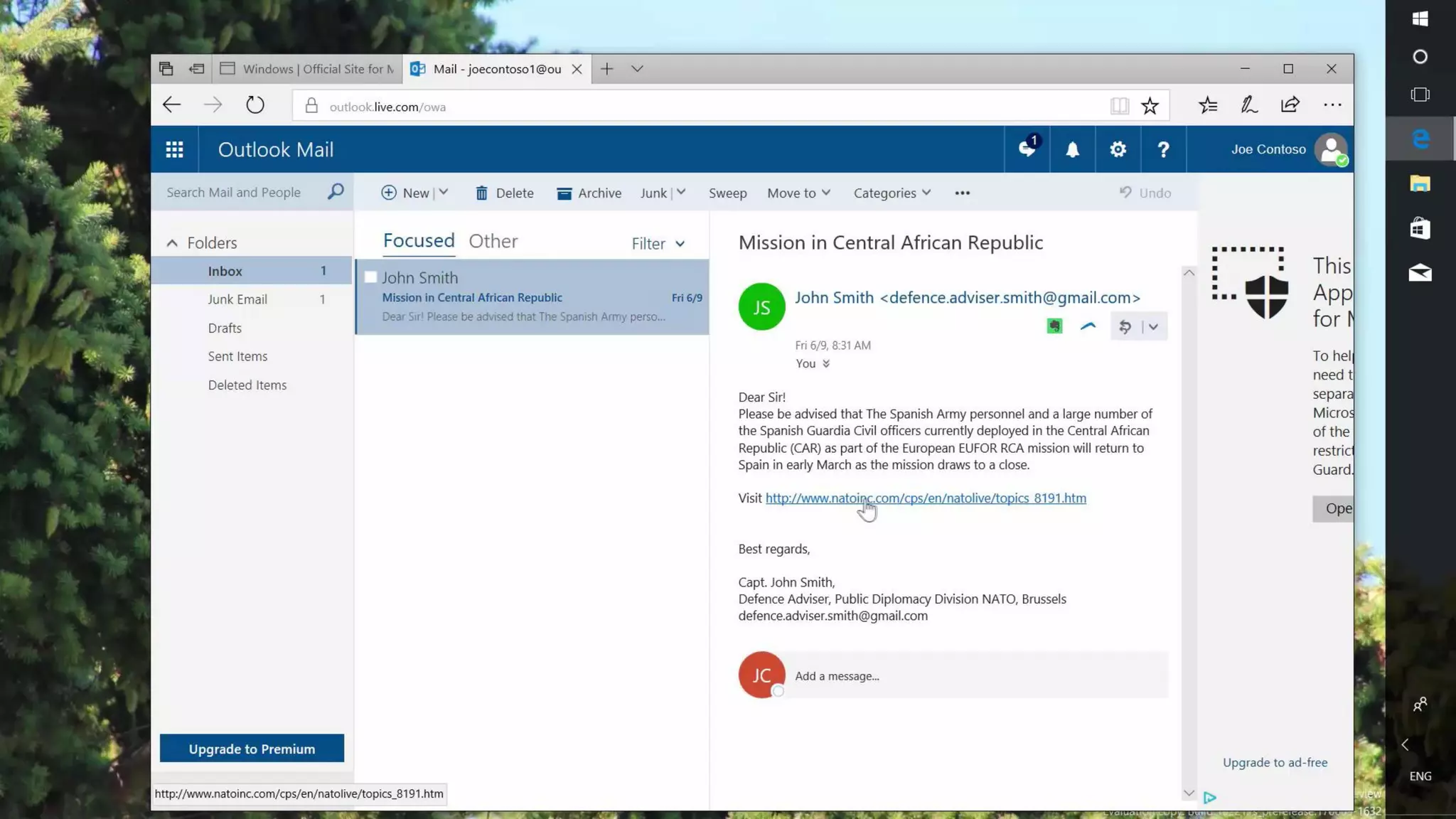
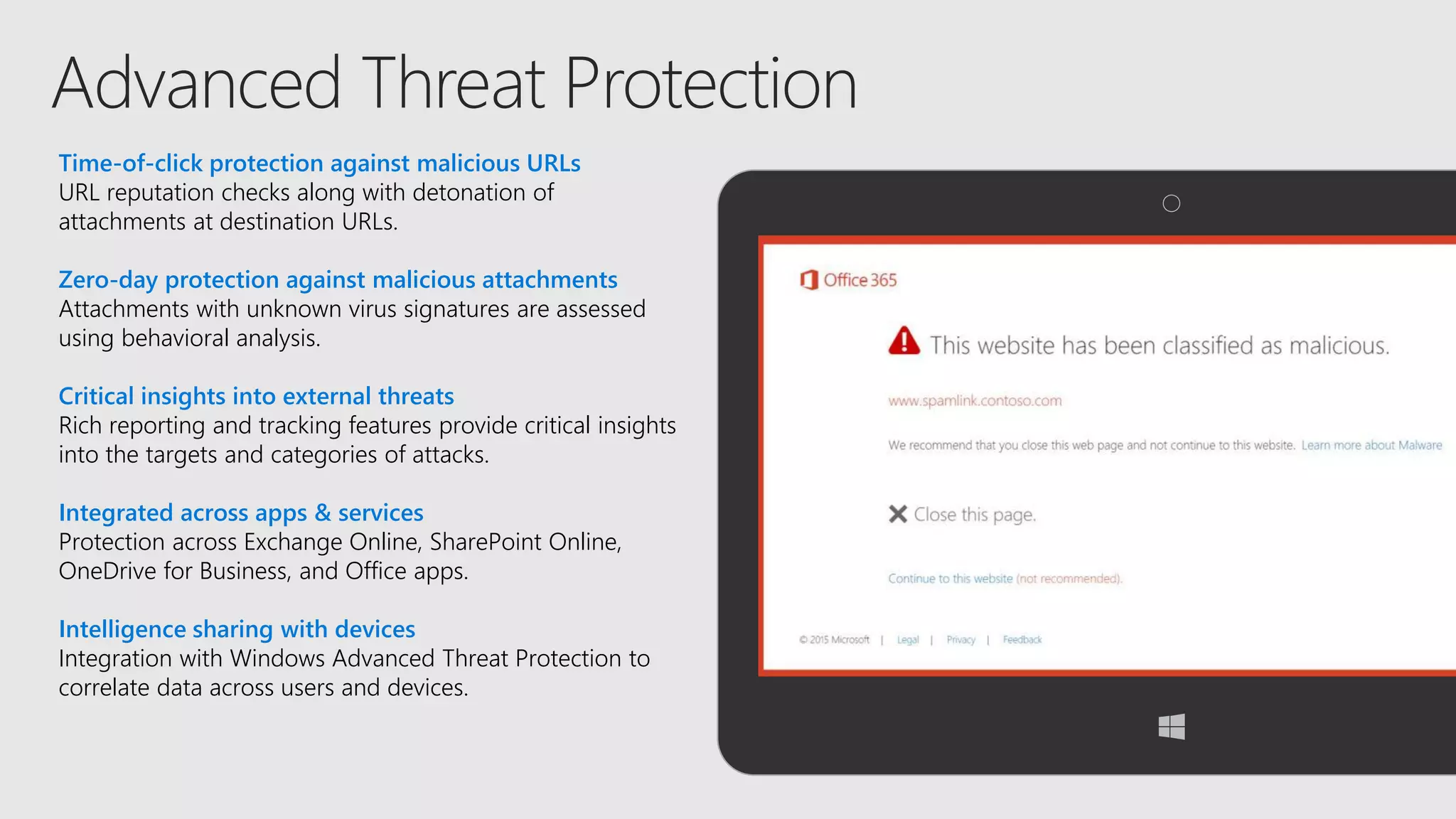
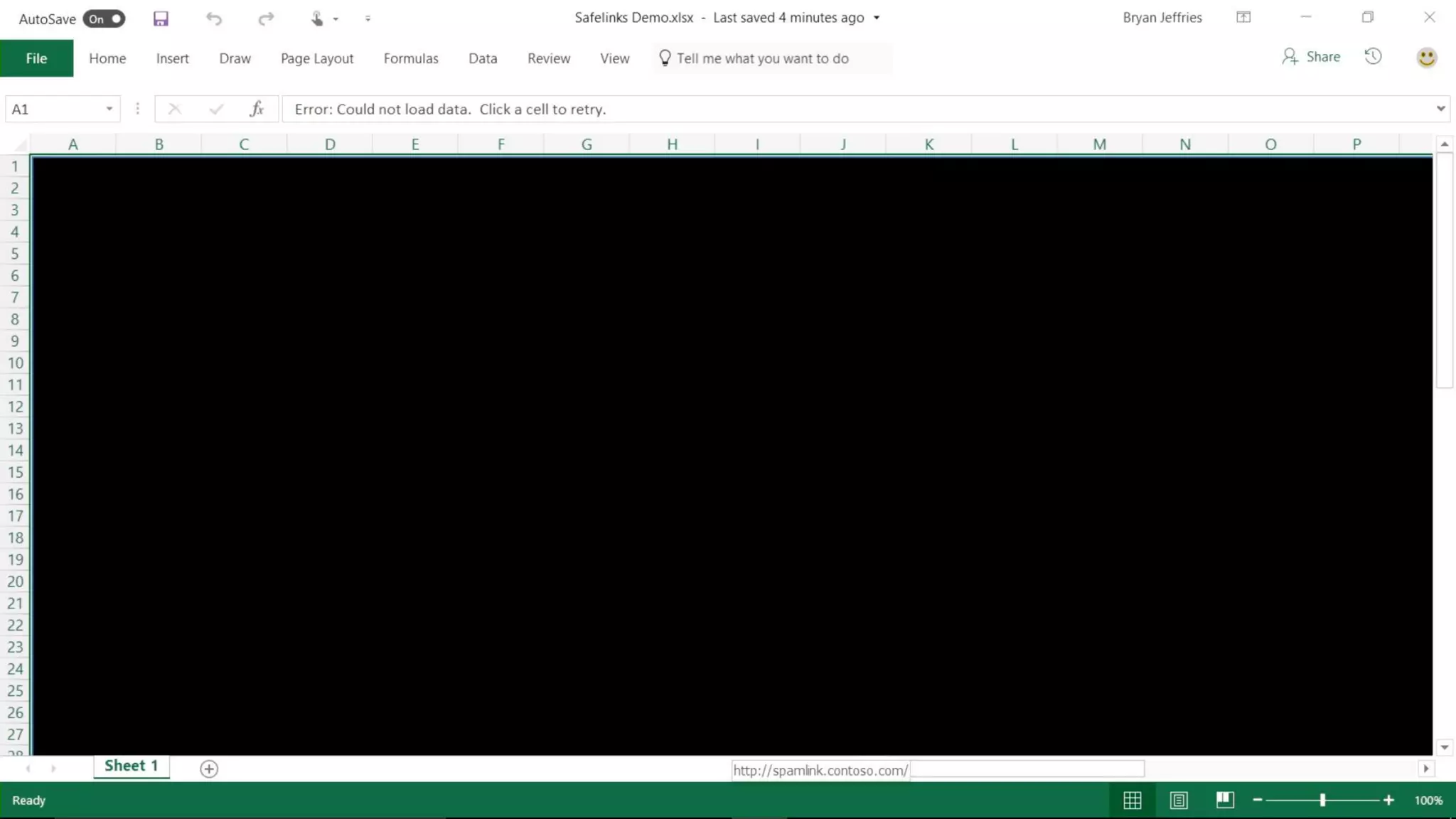
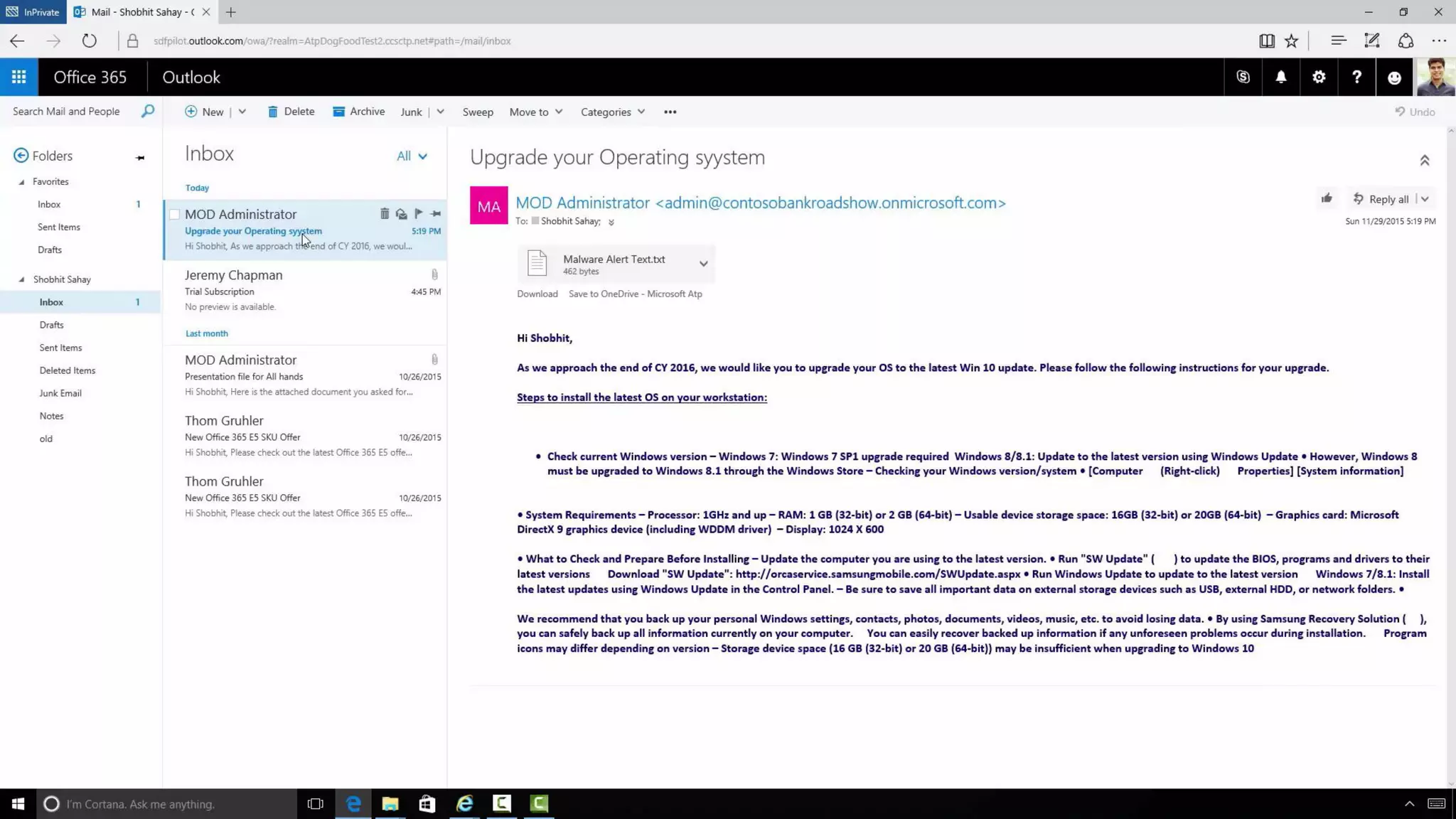
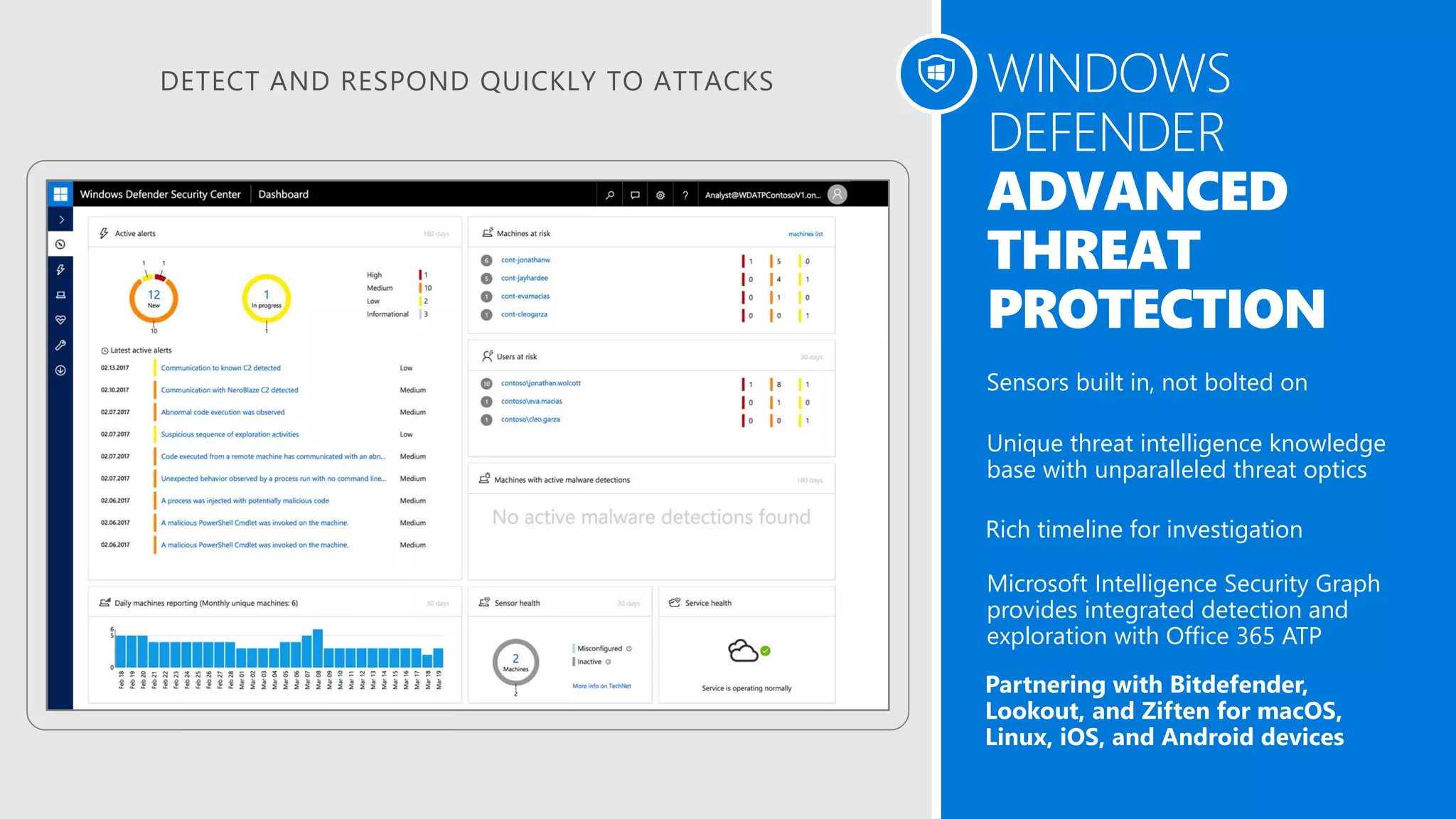
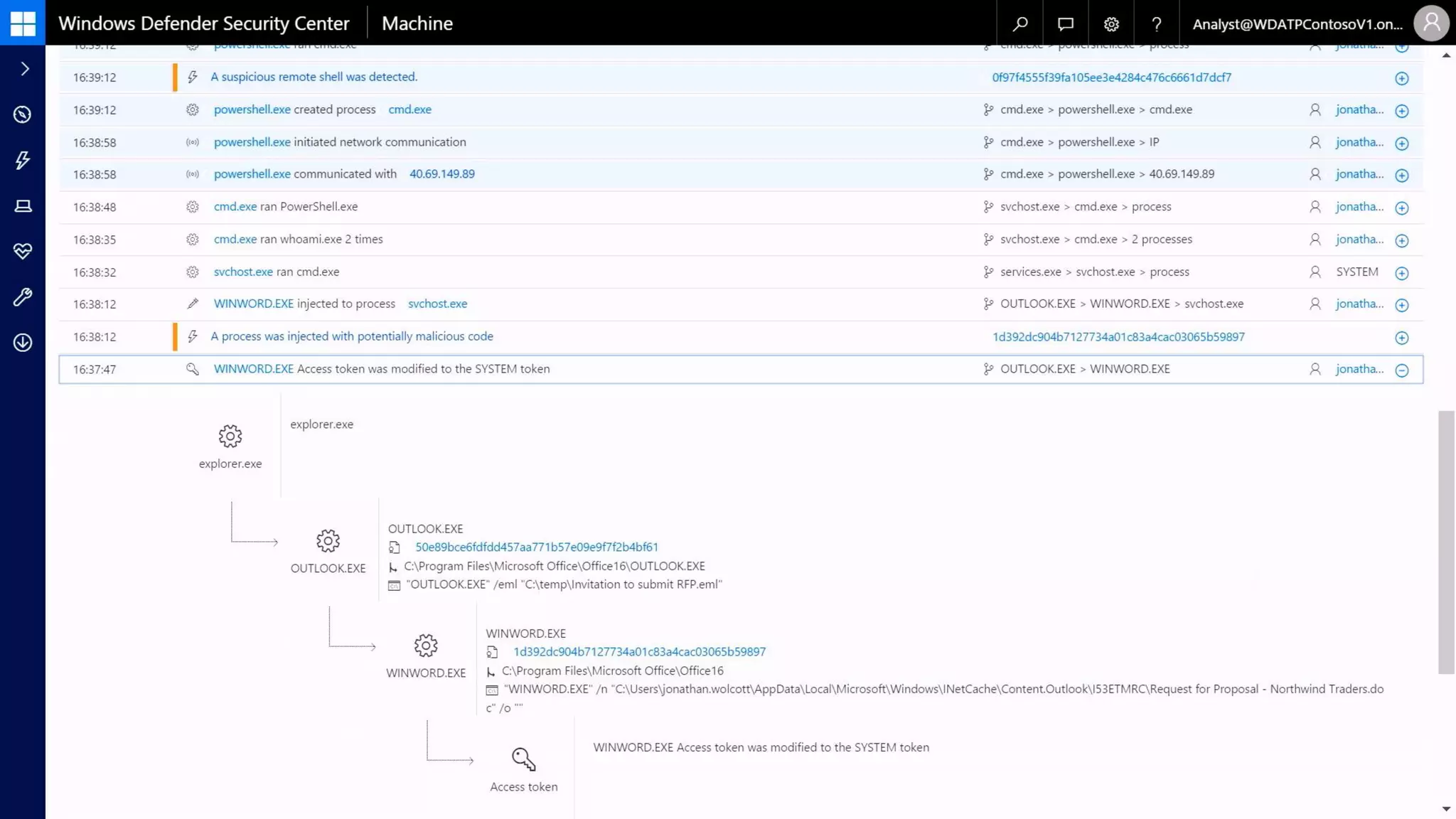
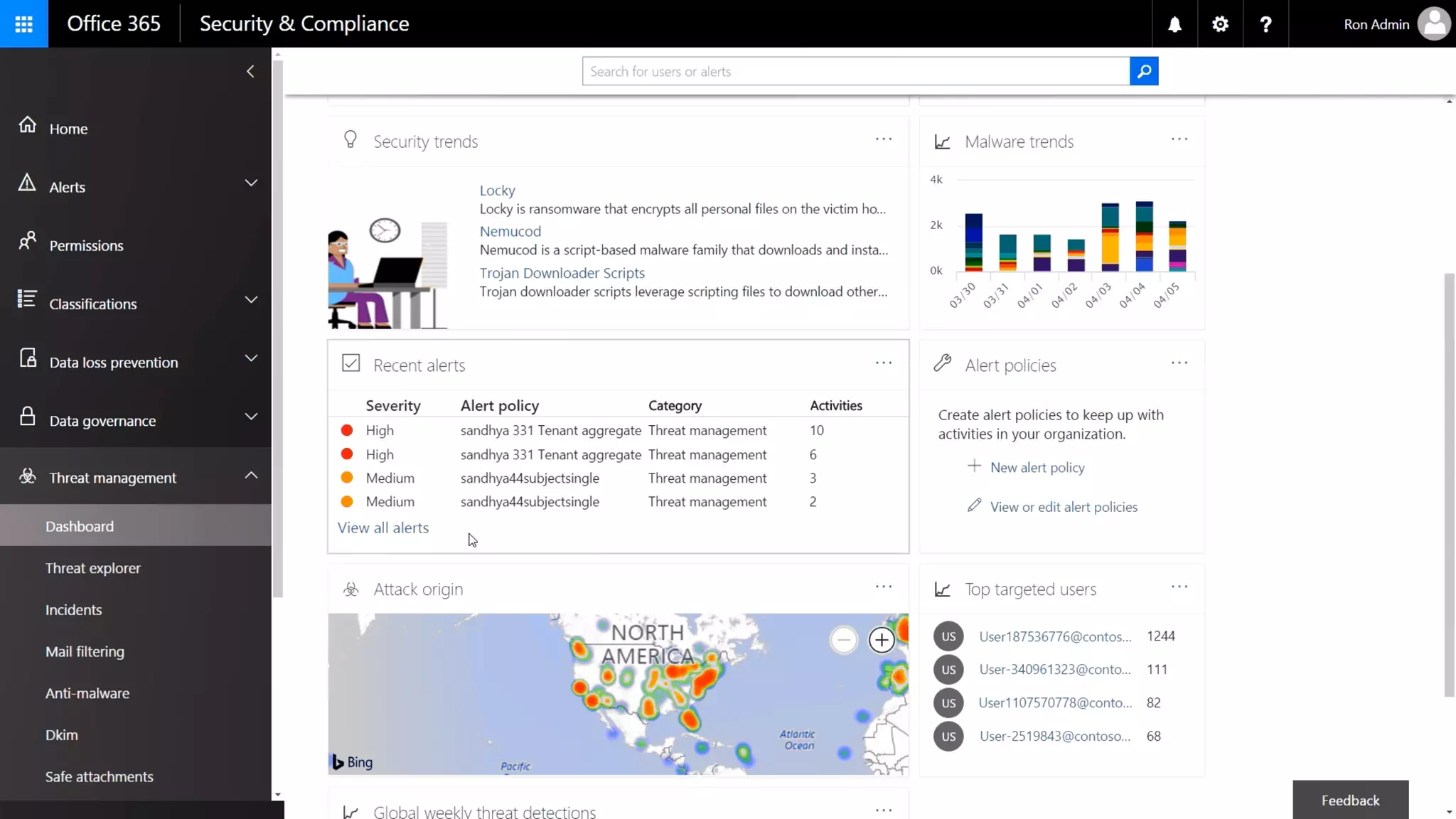
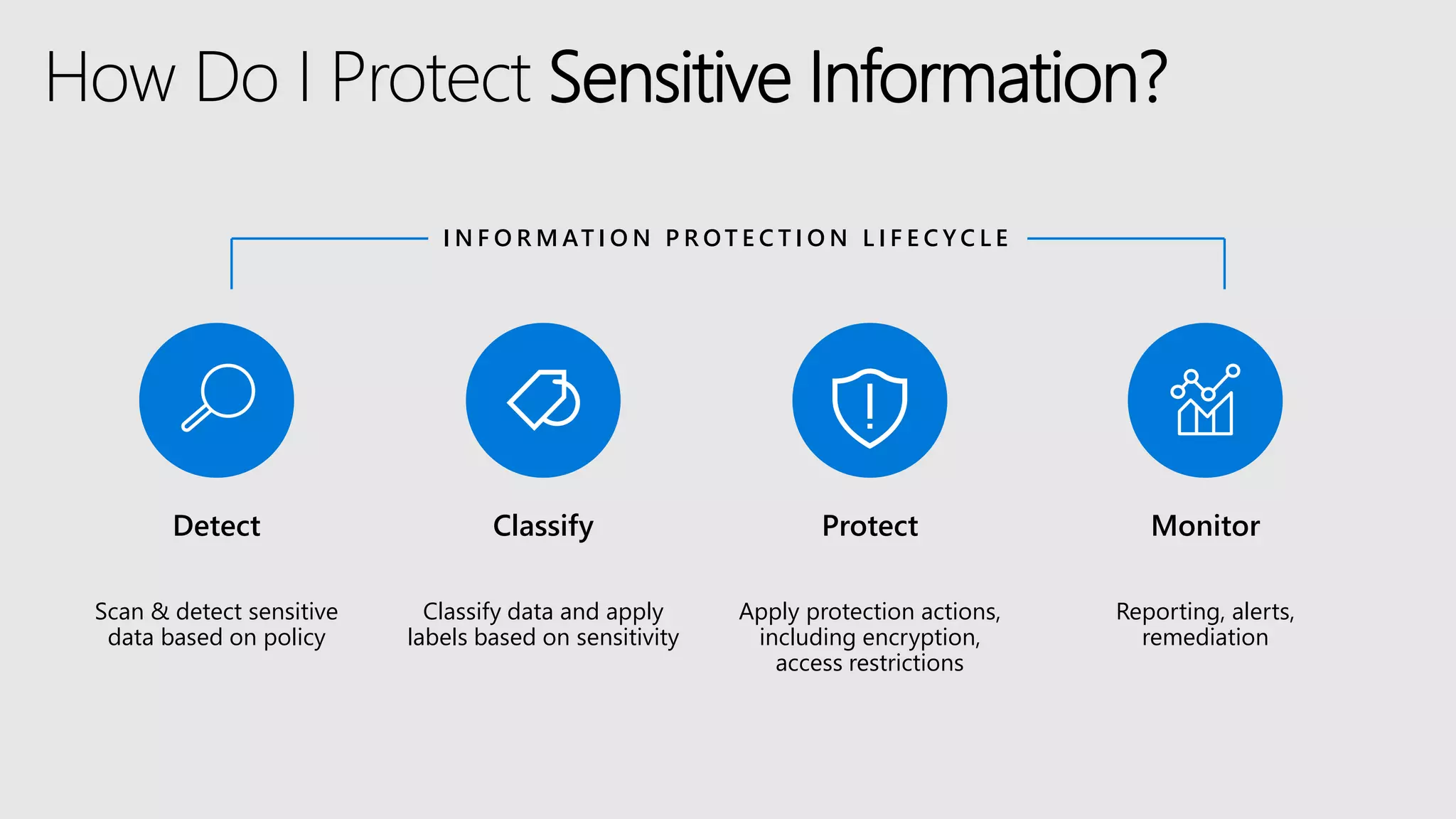
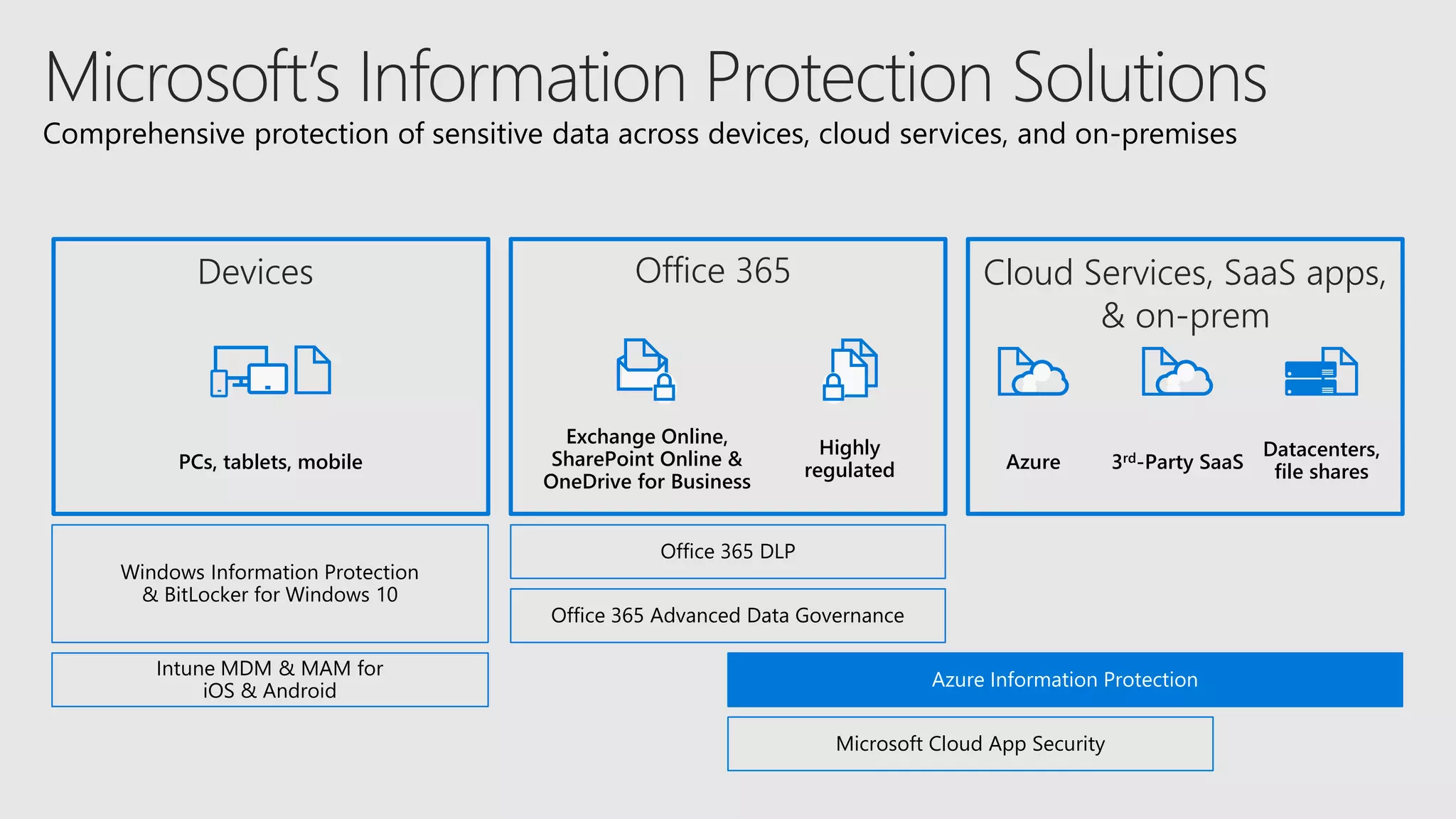
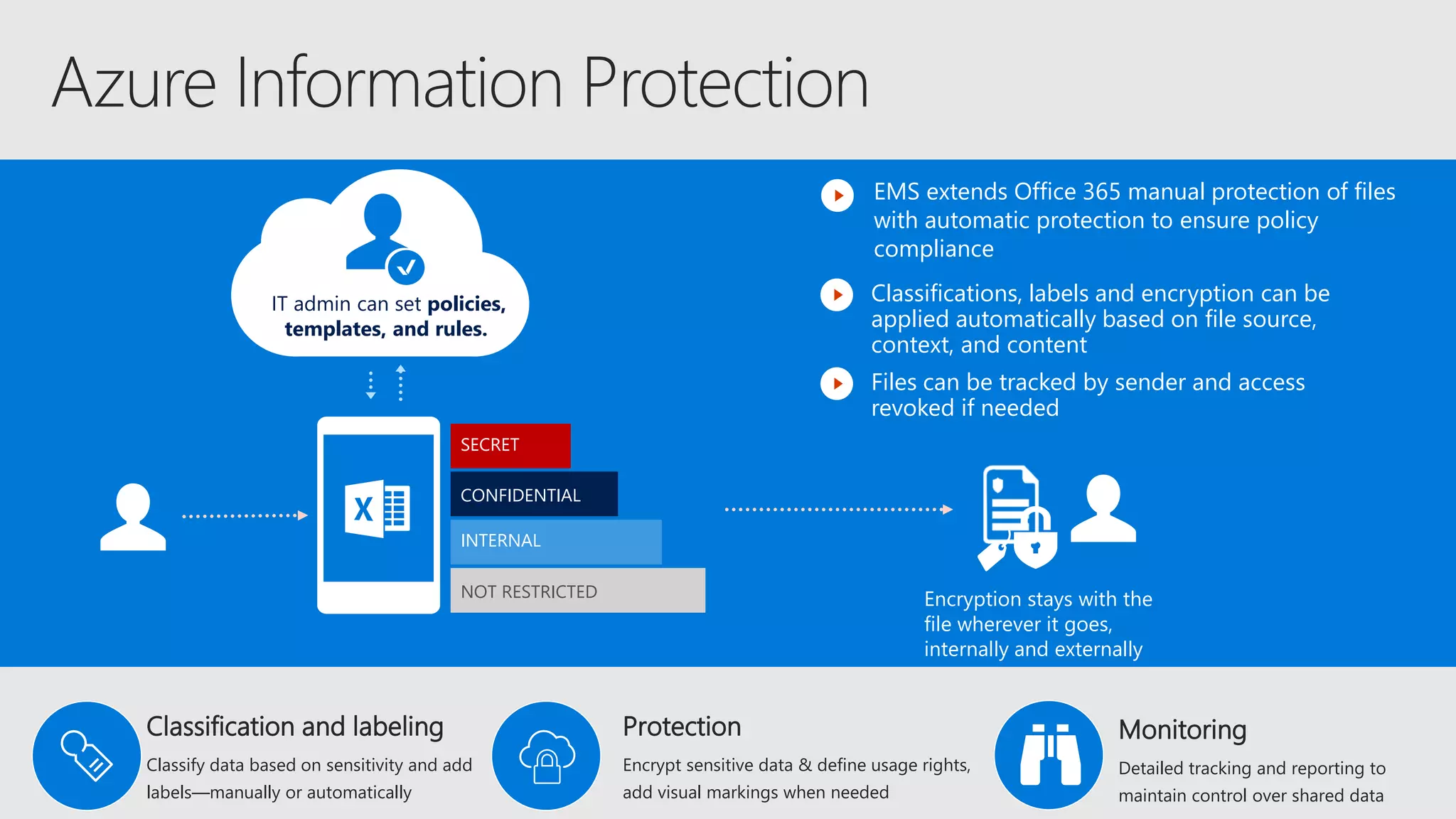
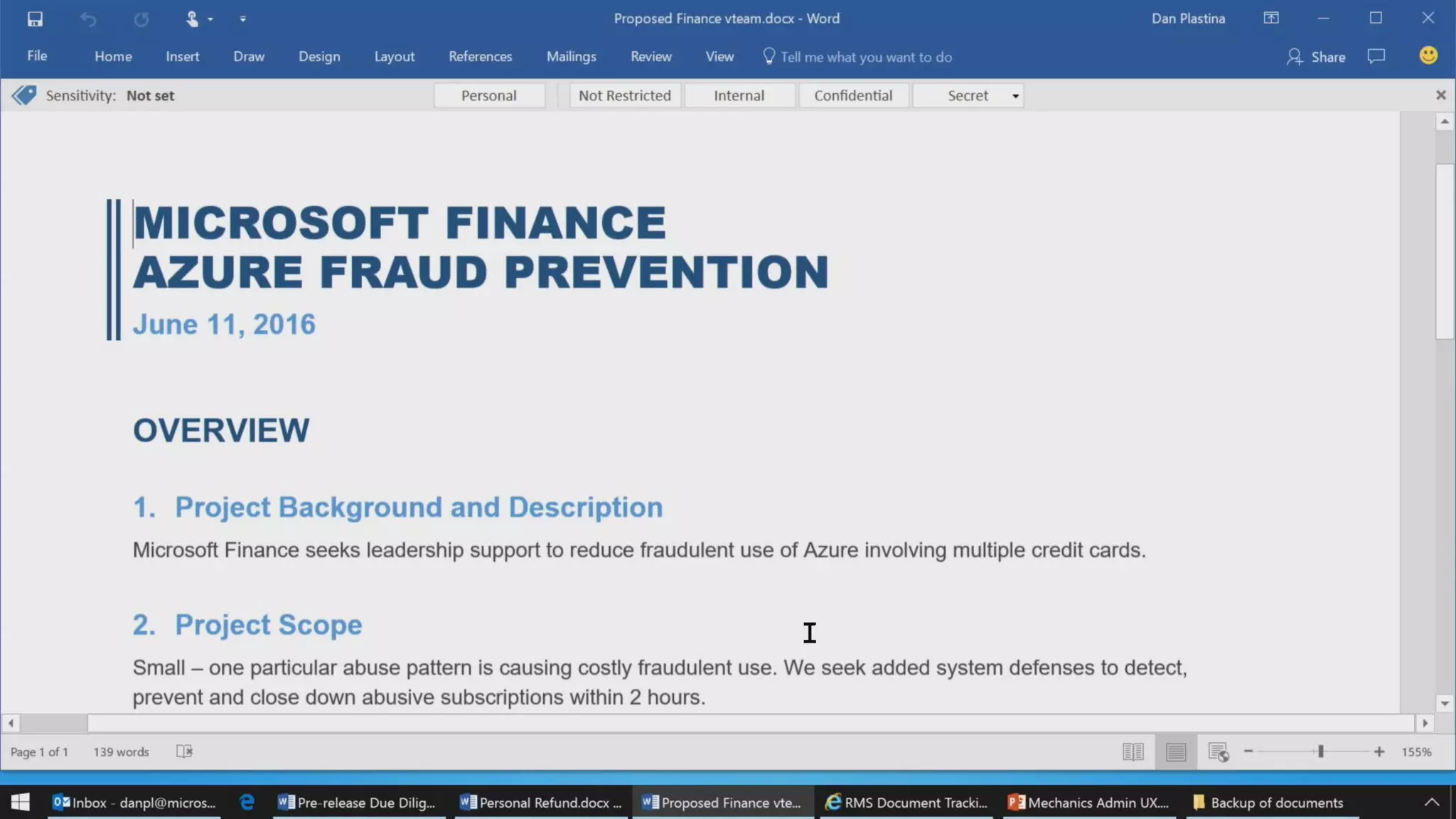
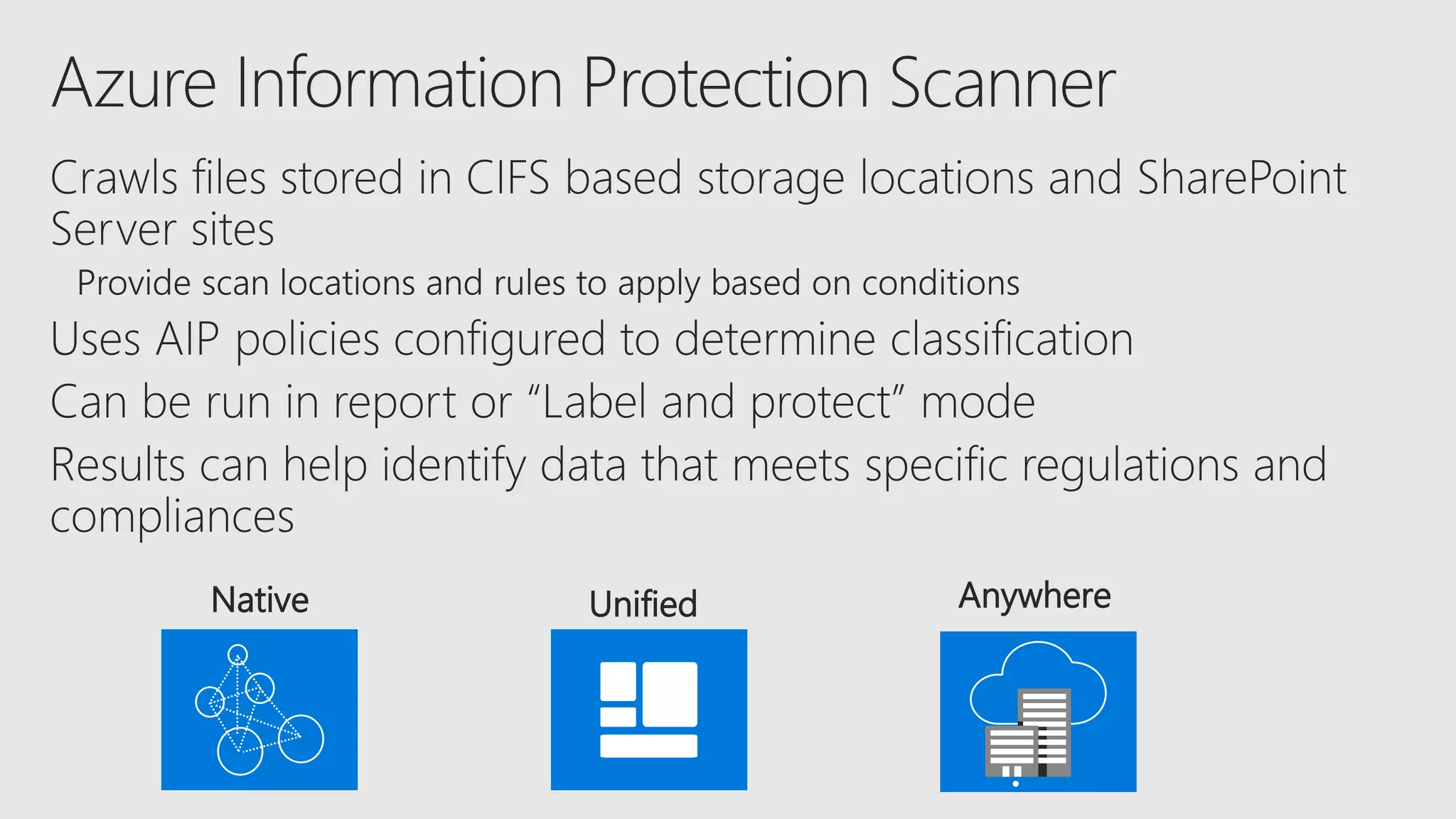
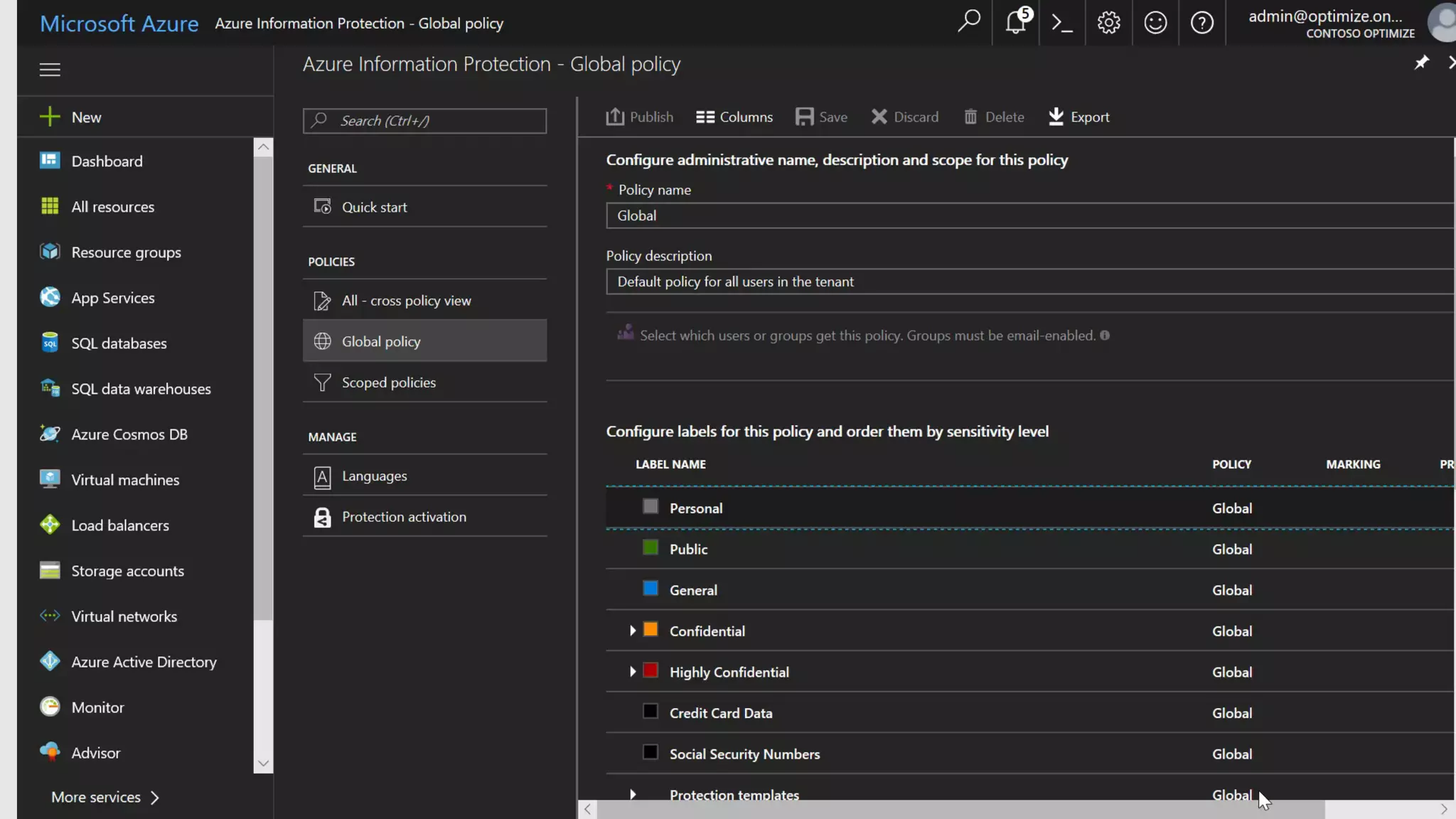
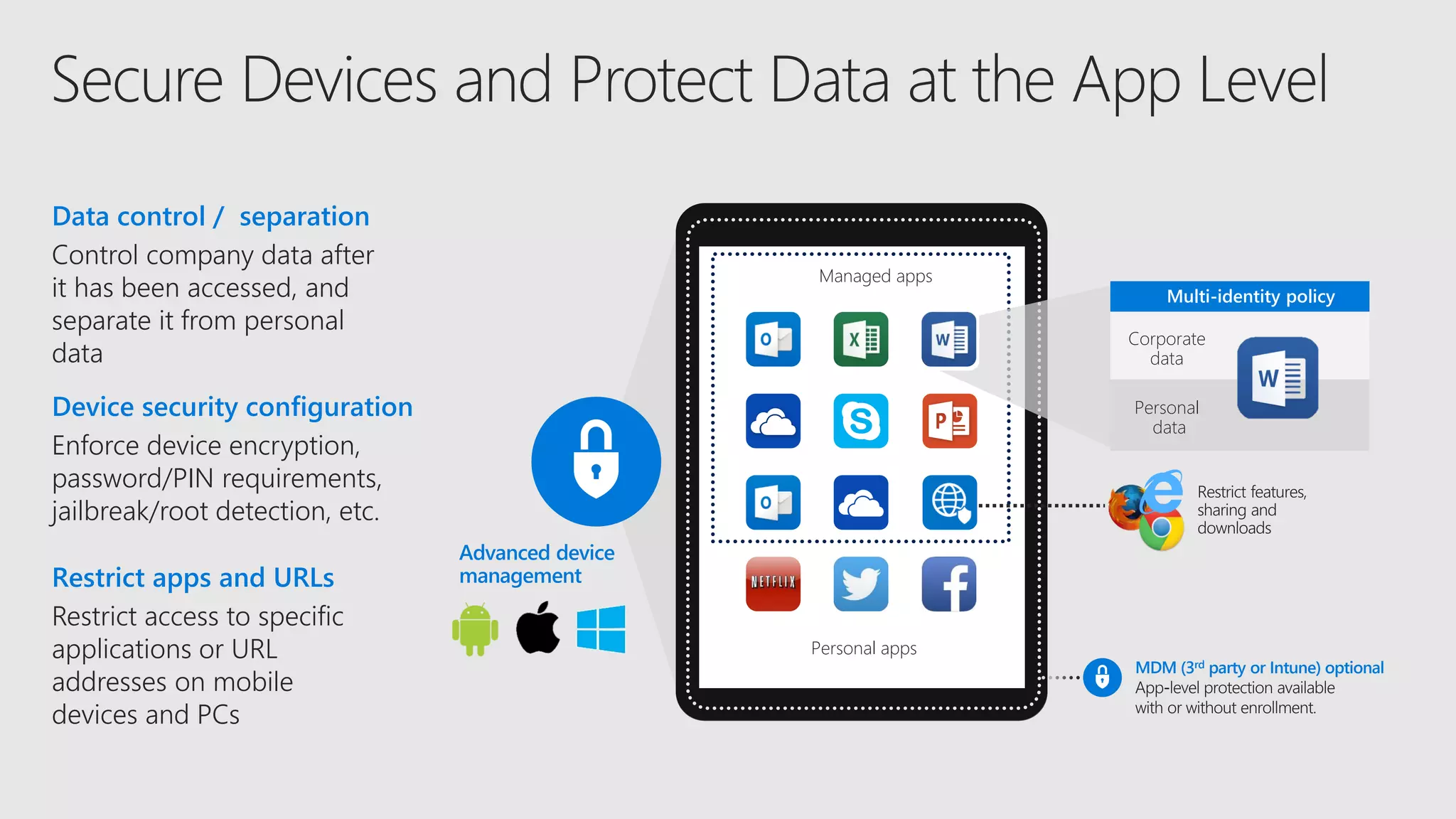
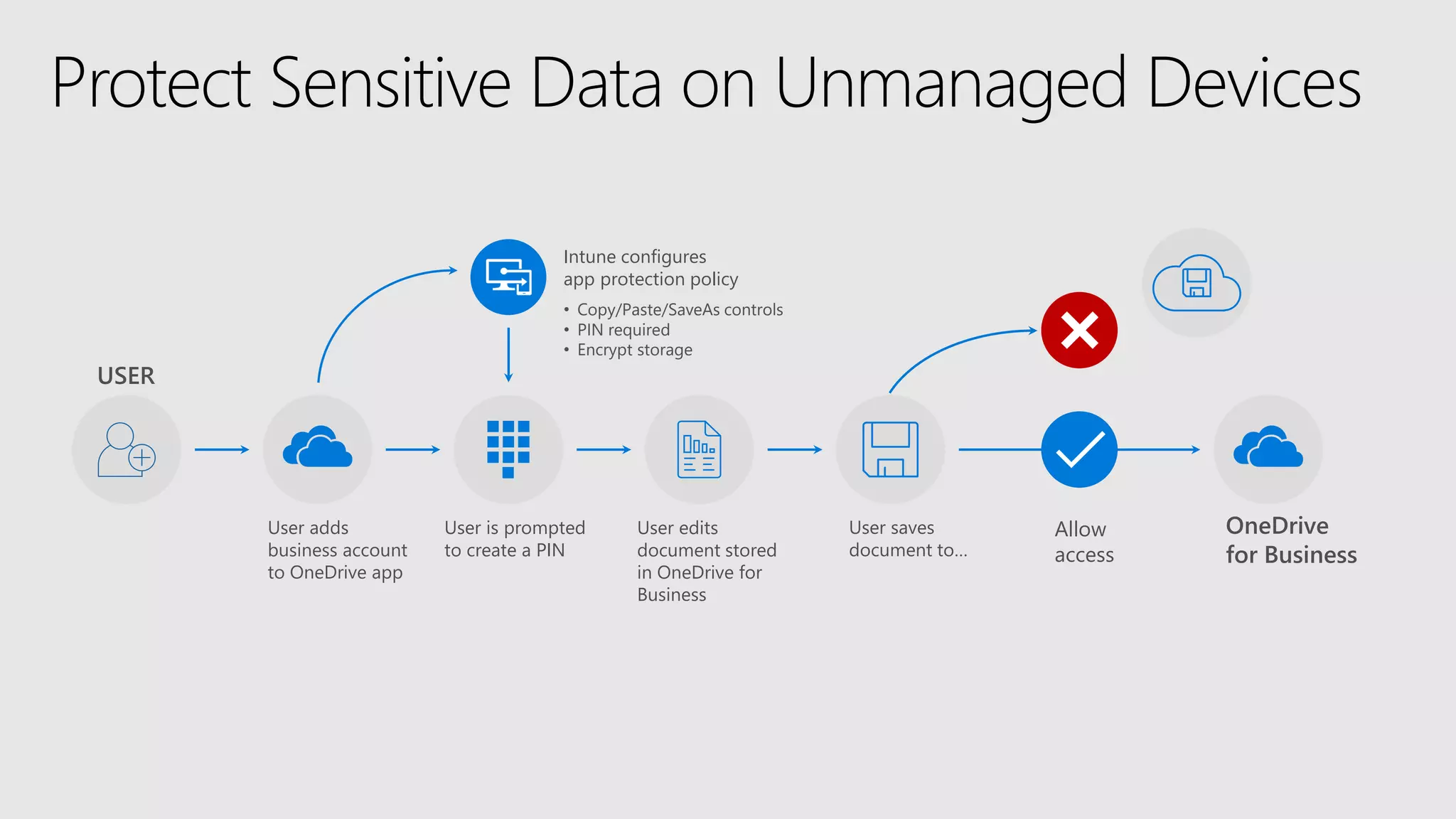
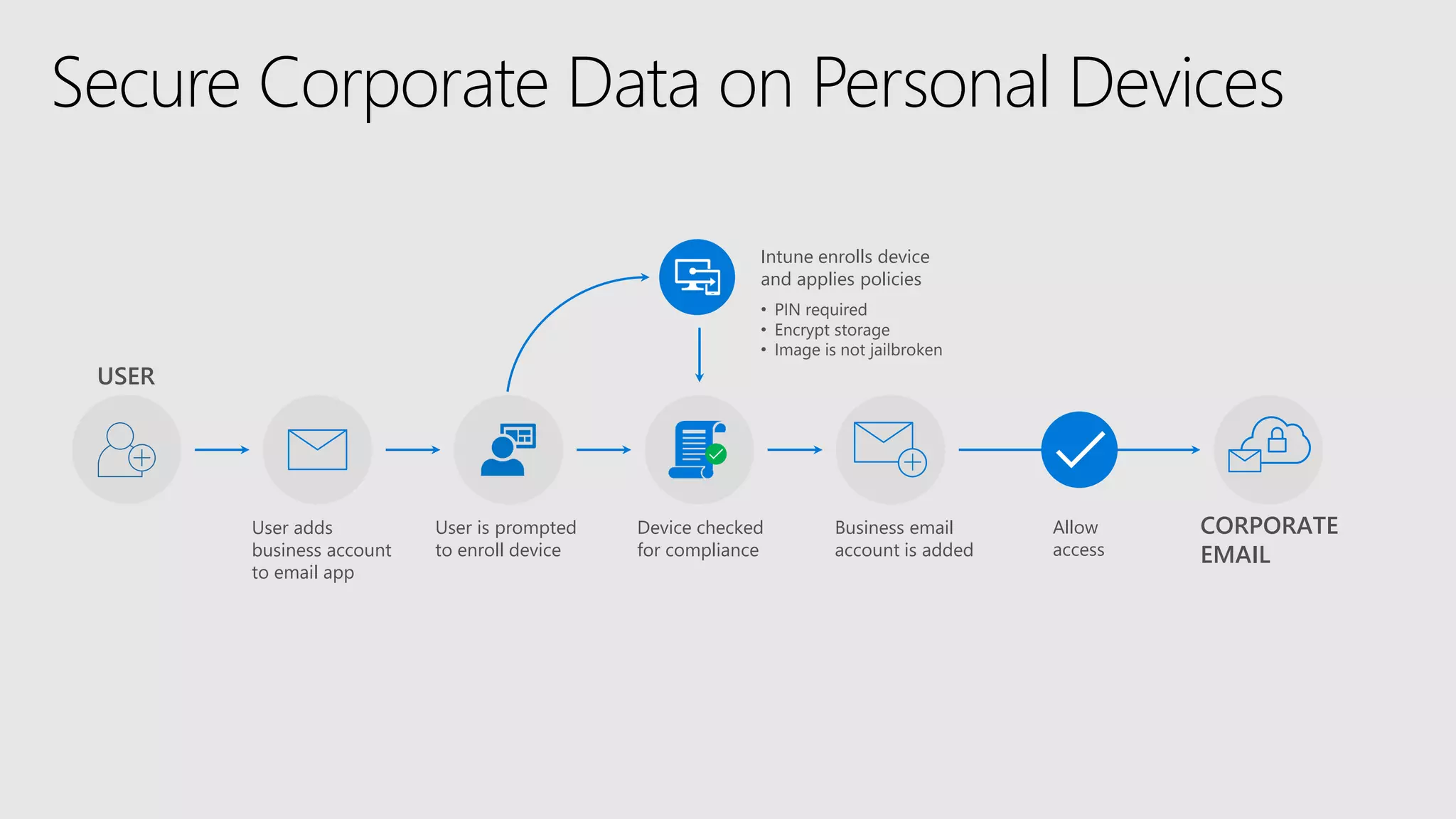
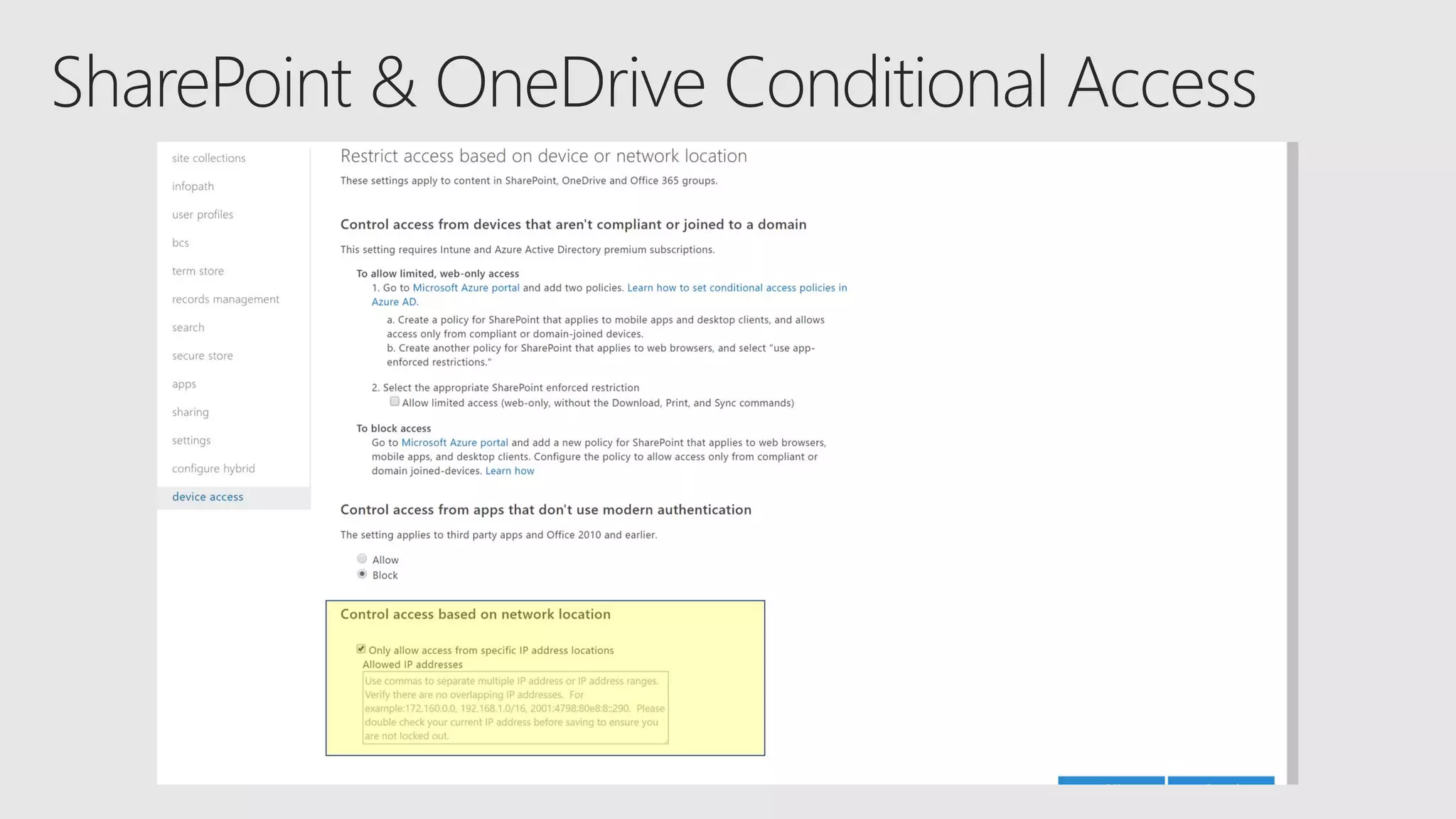
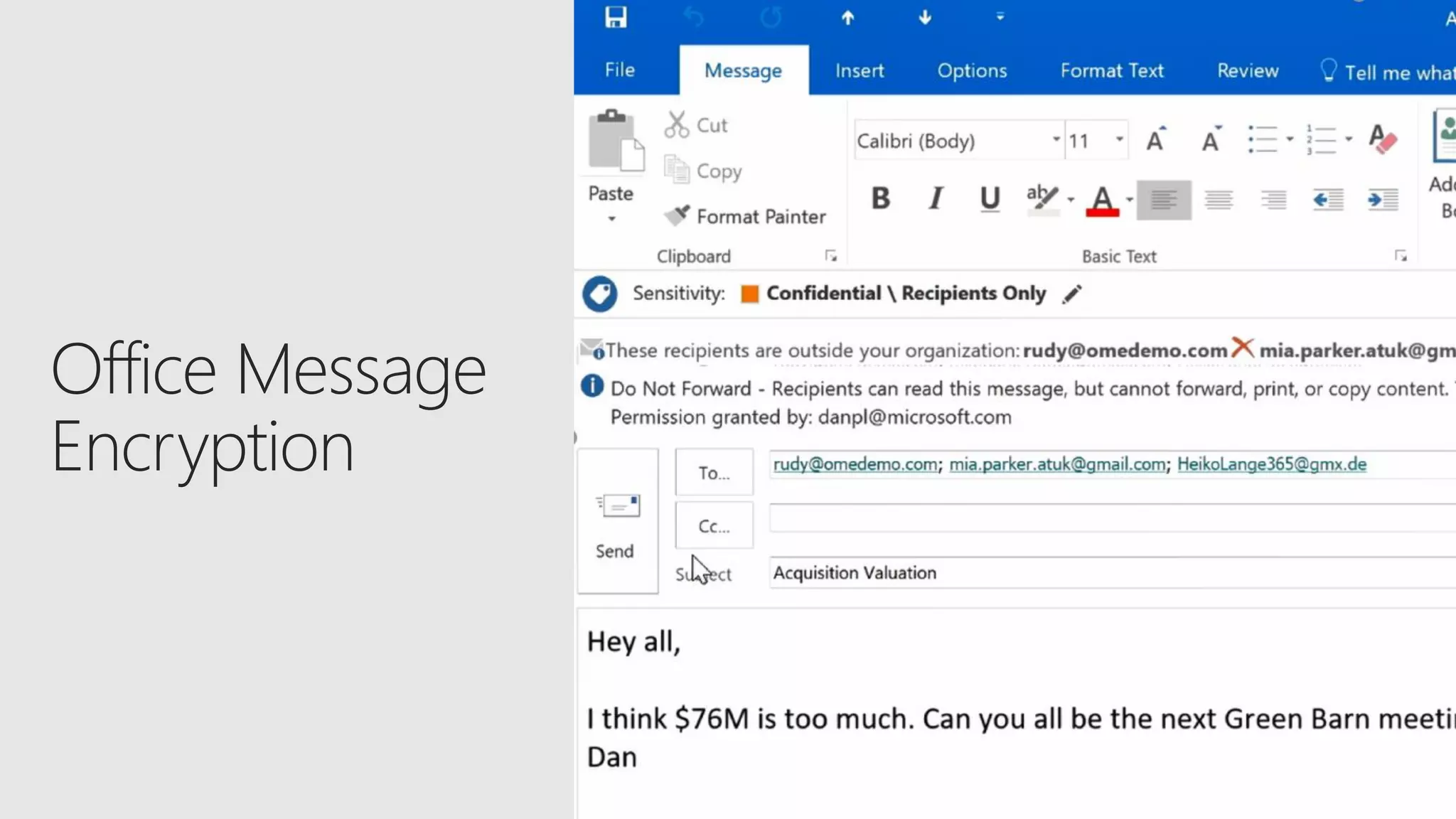
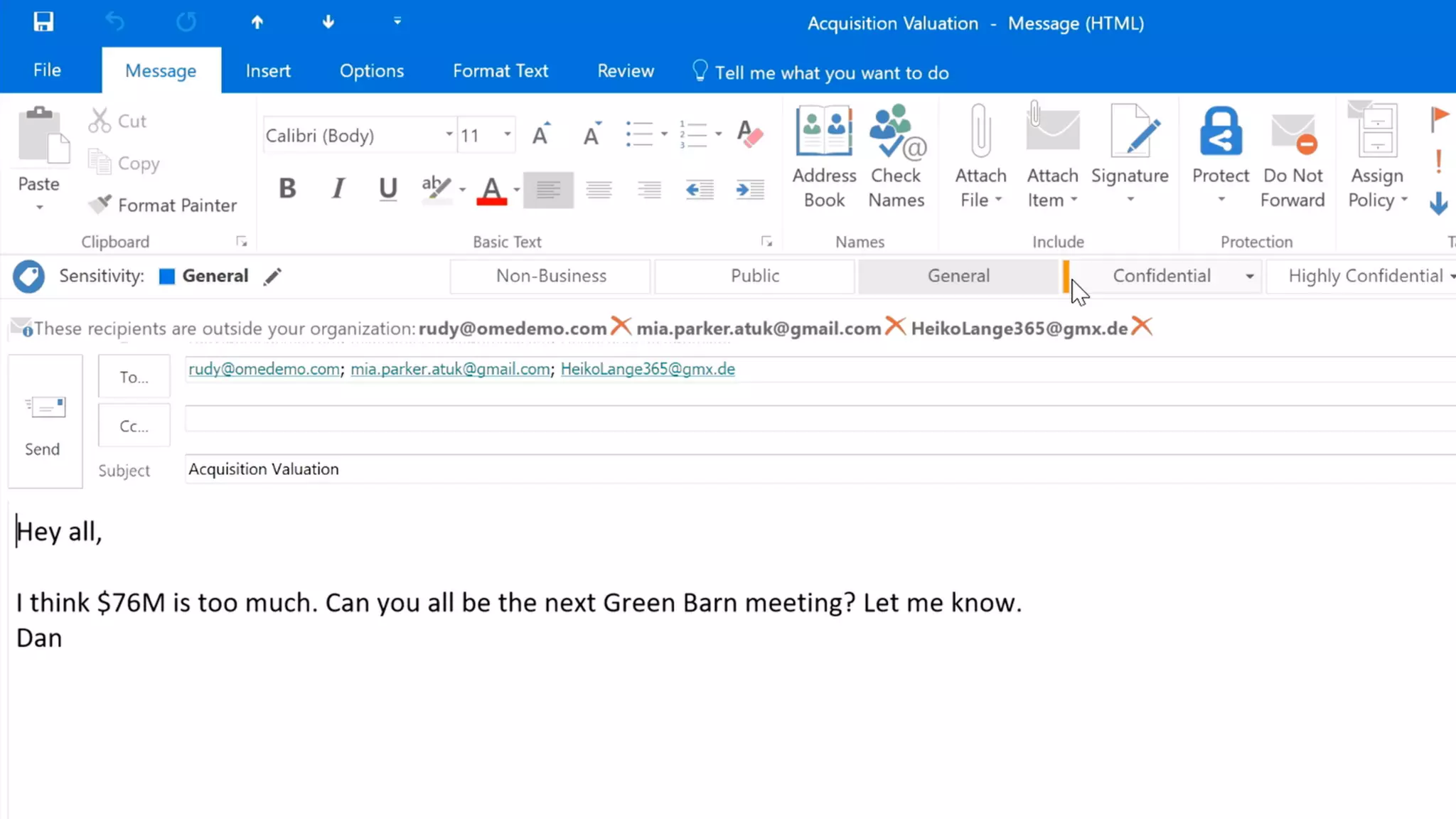
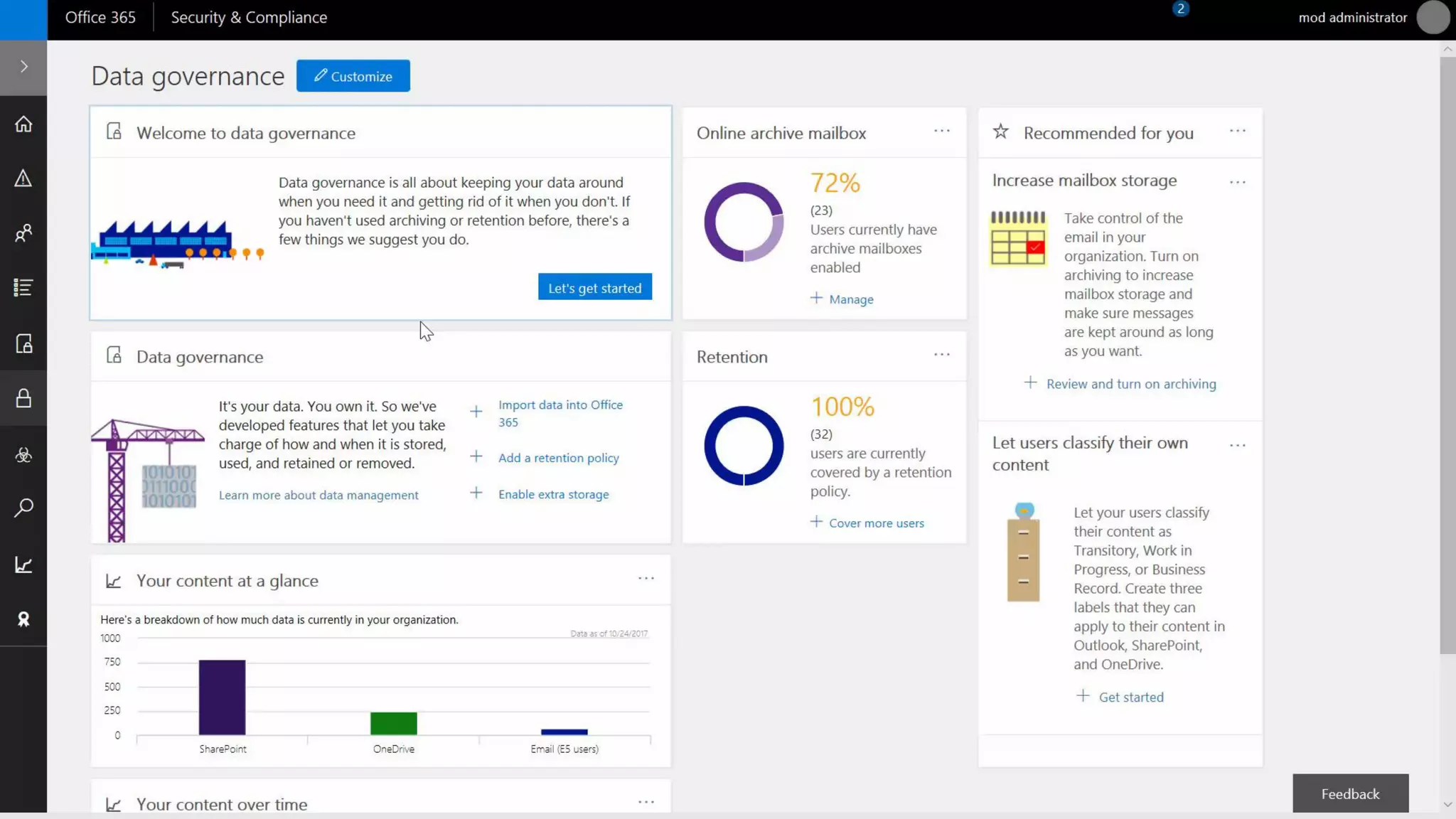
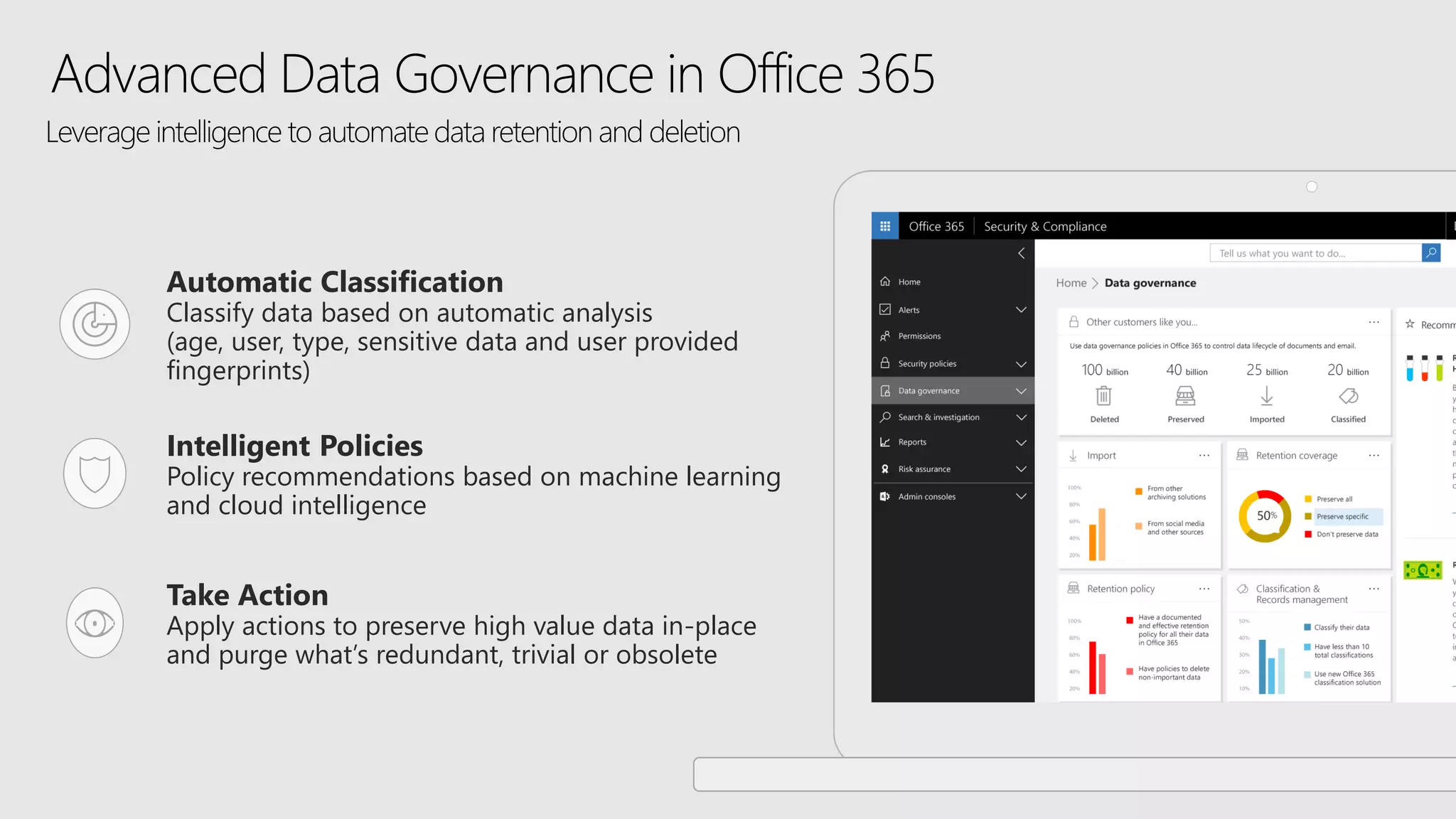
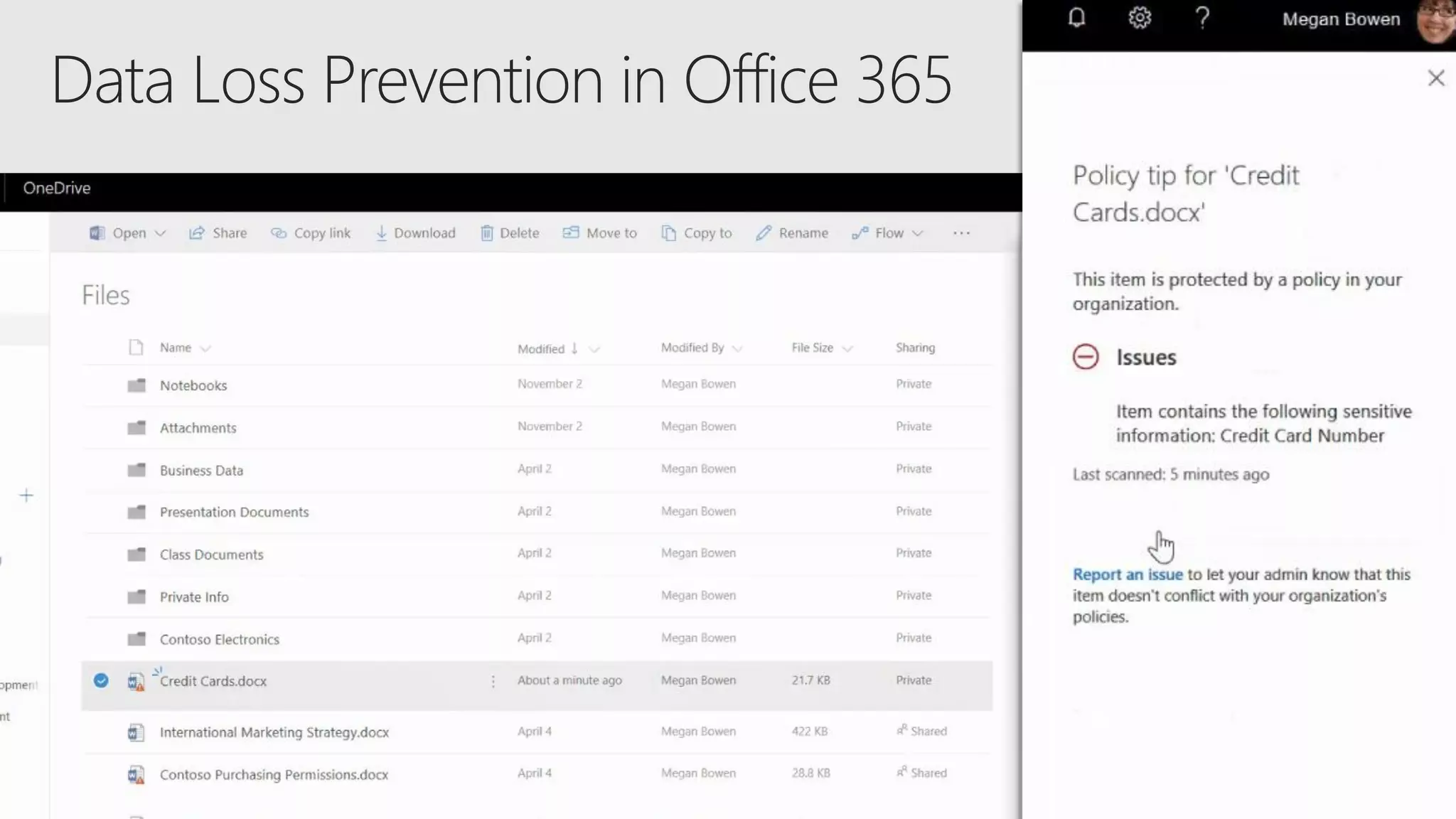
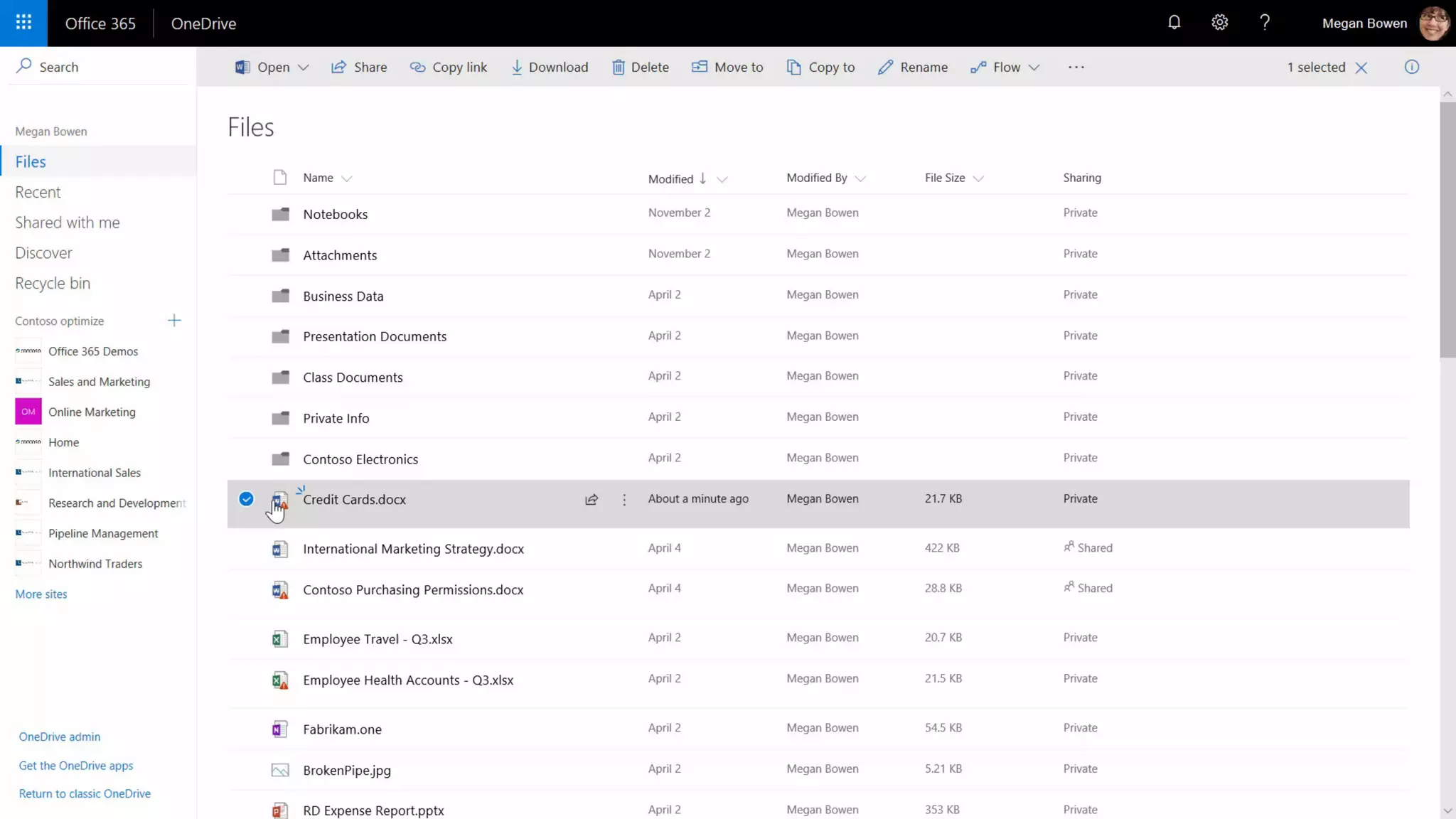
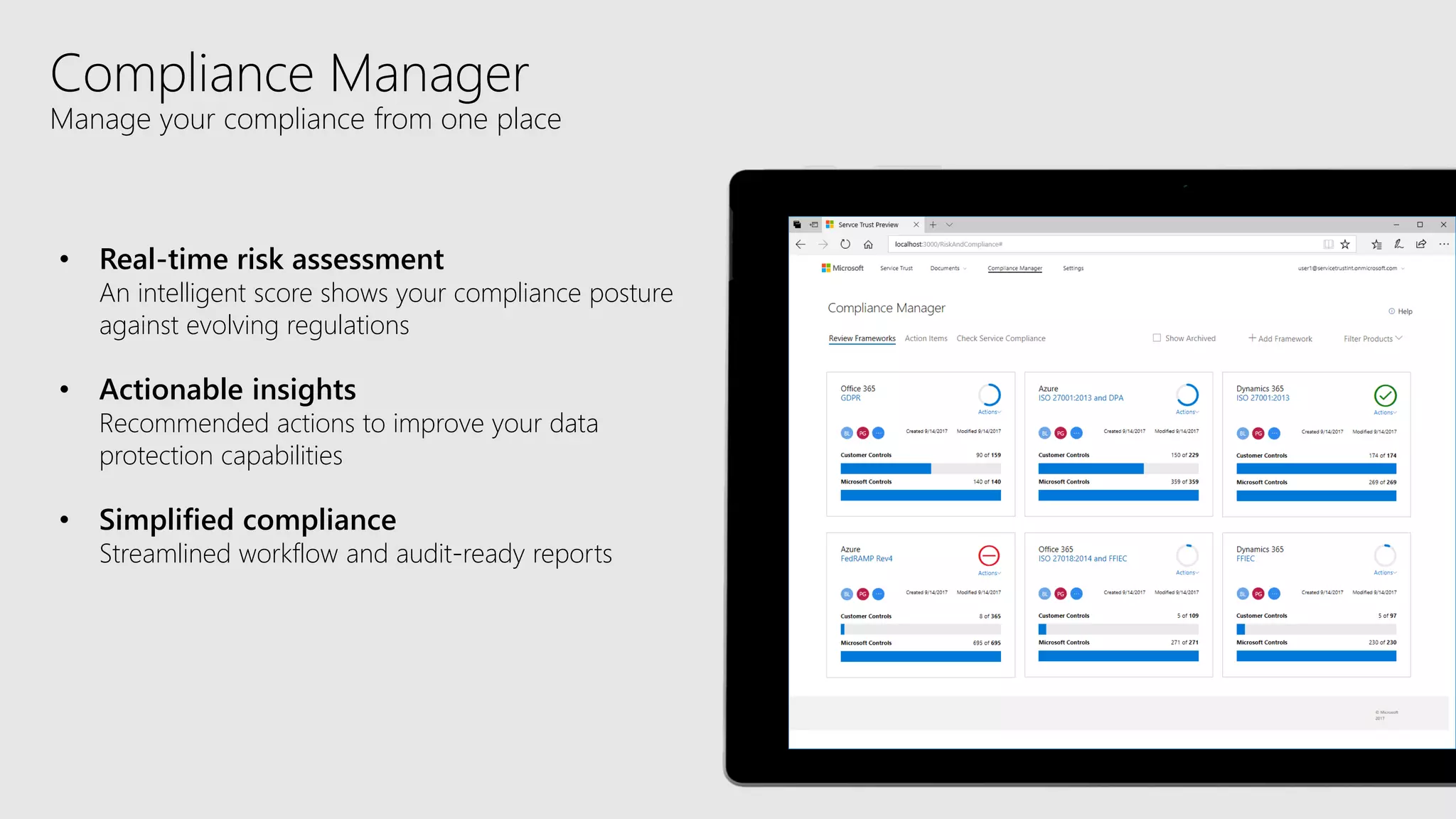
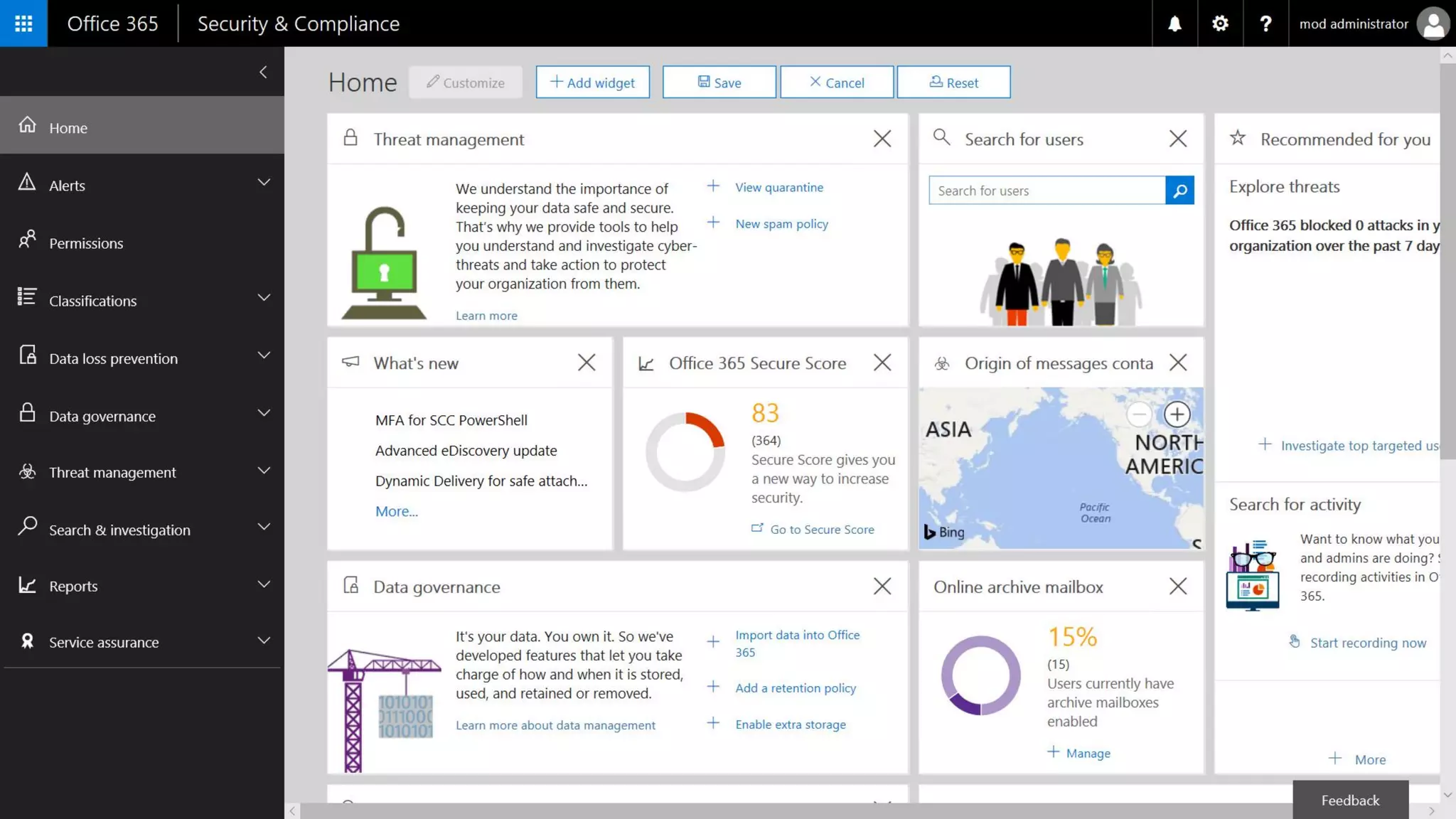
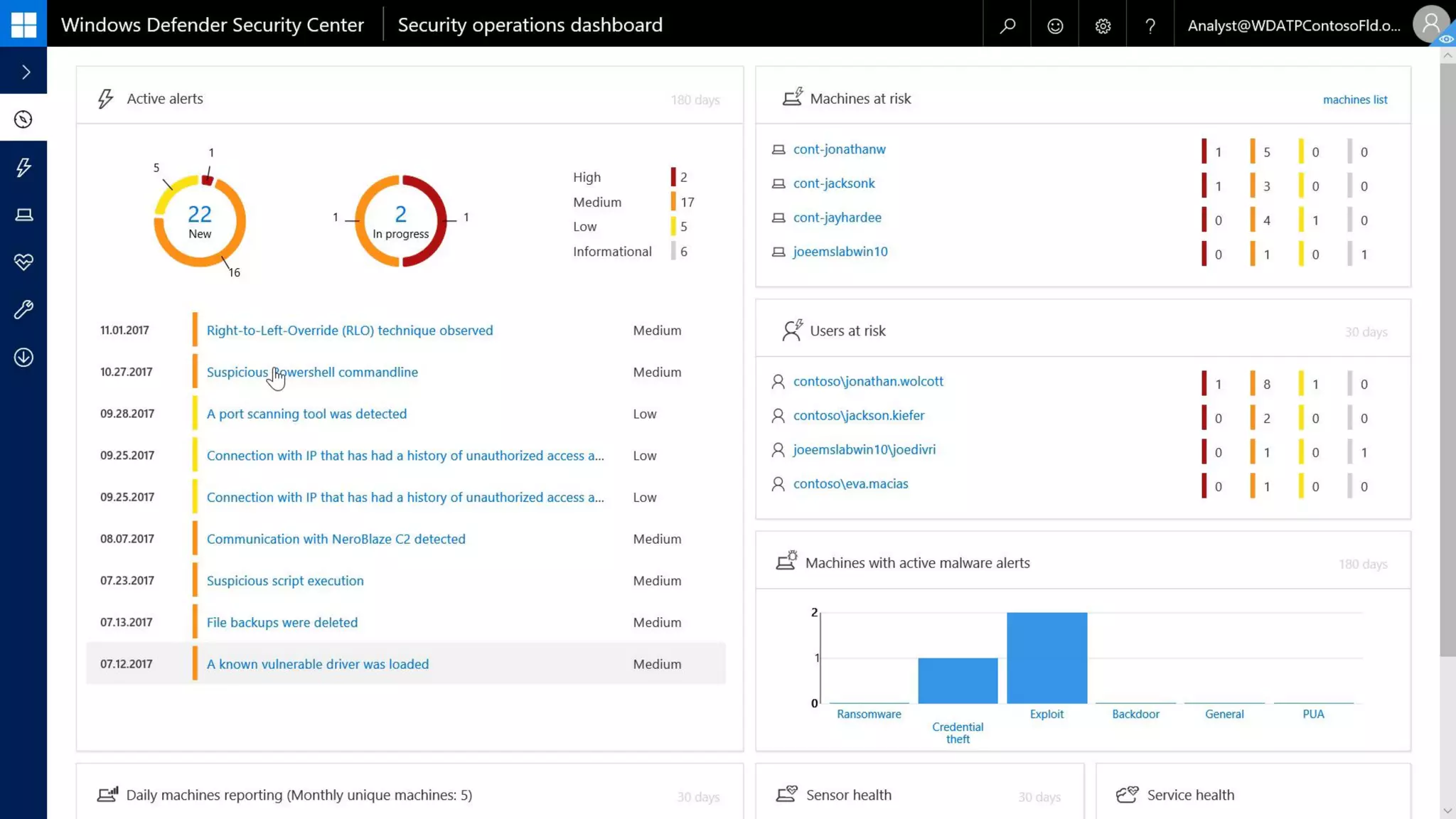
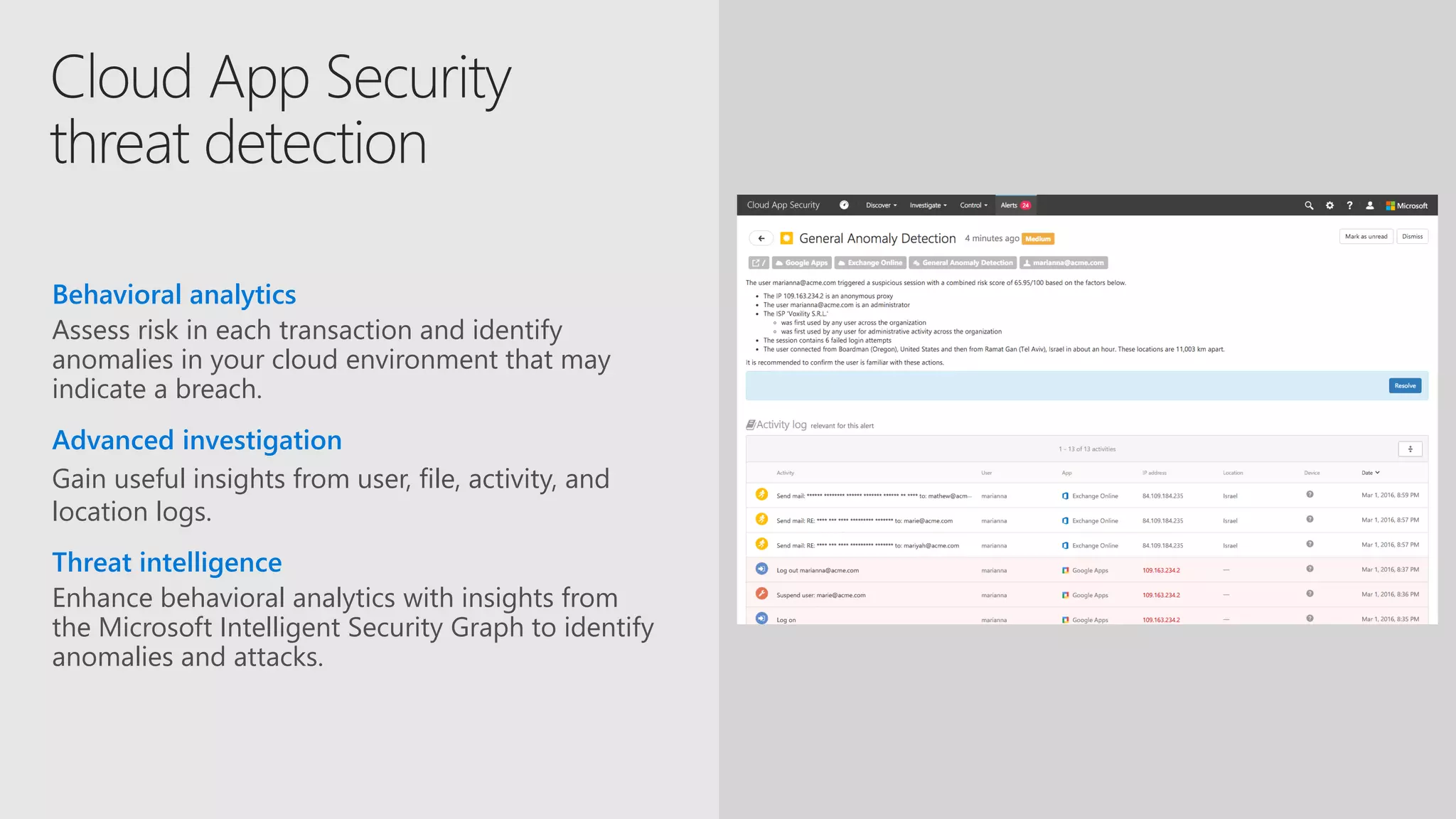
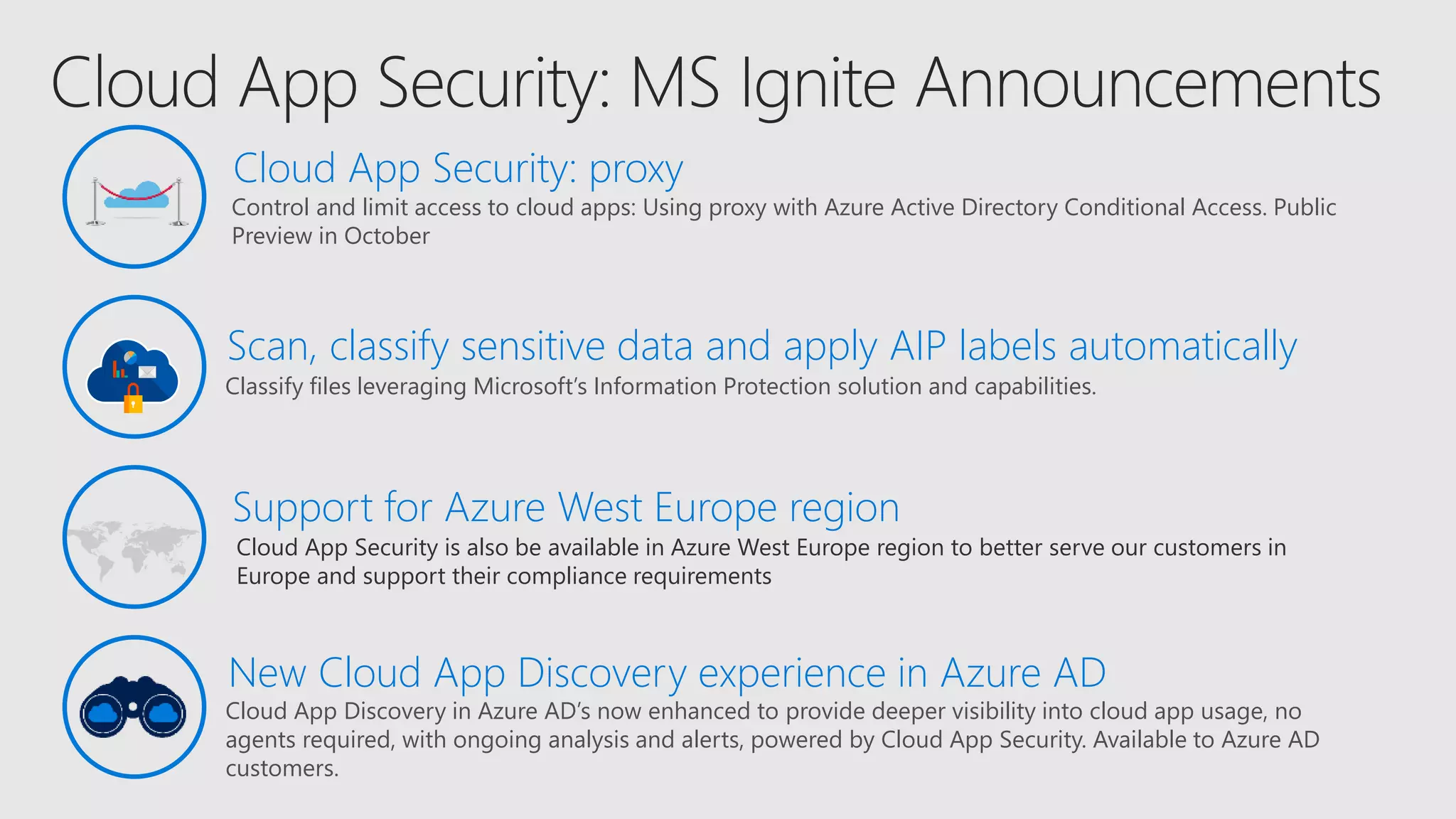
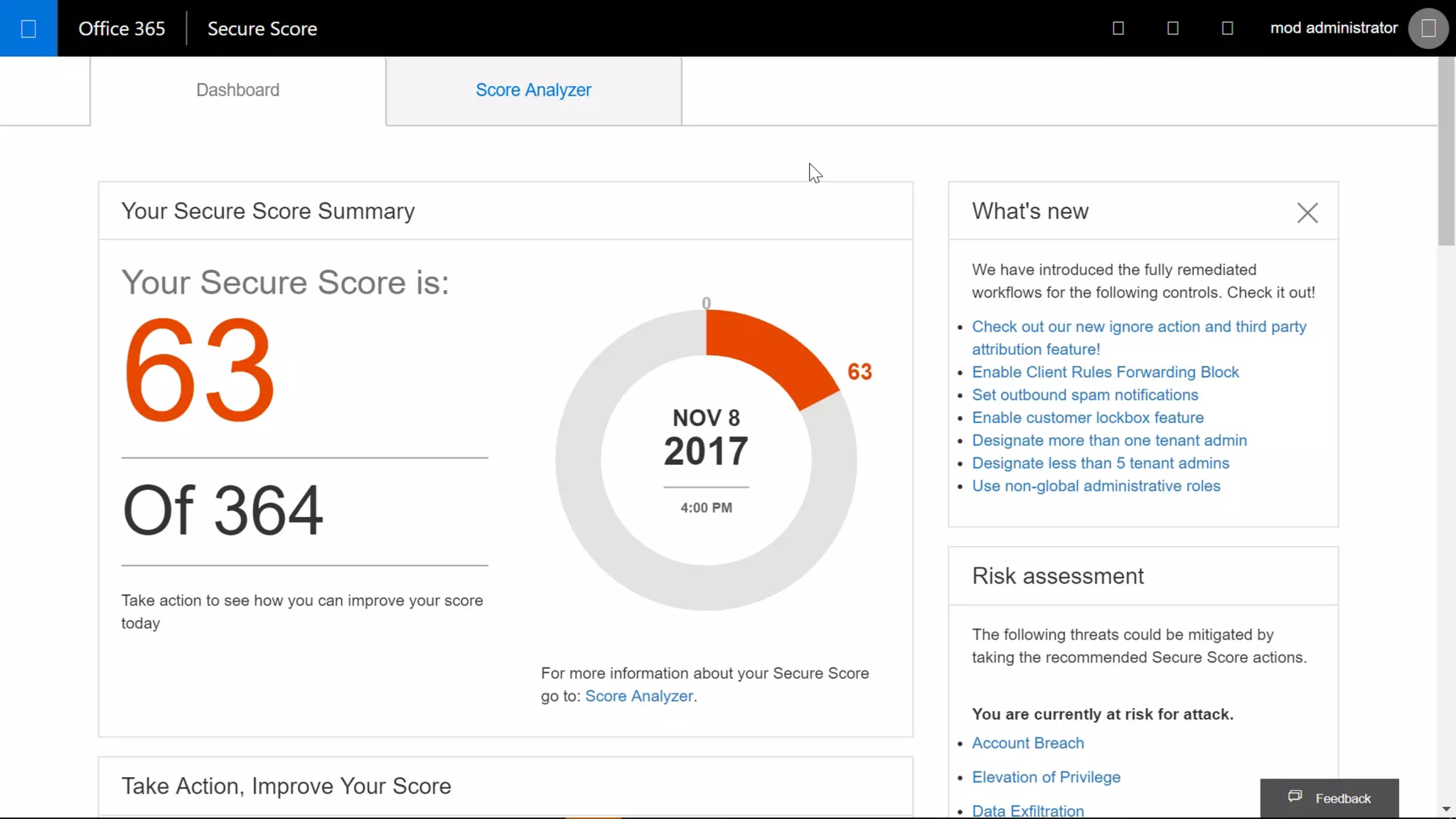
AOS Kuala Lumpur 2018 is an independent community event featuring 12 Microsoft MVPs and 14 international speakers across 18 sessions focused on Azure, Office 365, and SharePoint. The event emphasizes advanced security measures within Microsoft 365, including data protection strategies such as Azure Information Protection, conditional access, and device management. Additionally, it highlights tools for threat detection and response along with compliance management for safeguarding sensitive data.