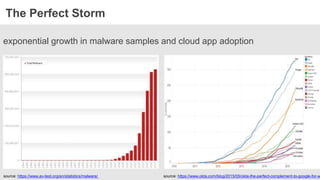
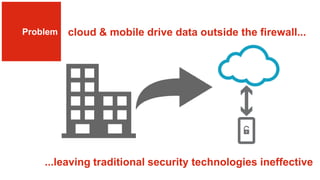
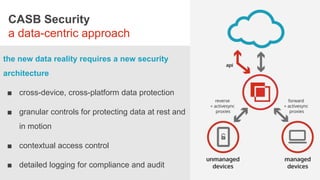
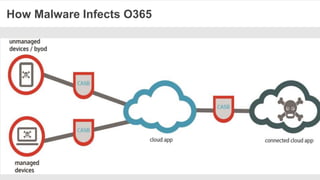
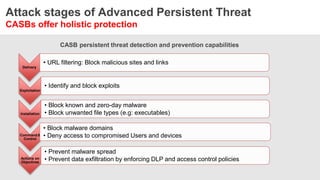
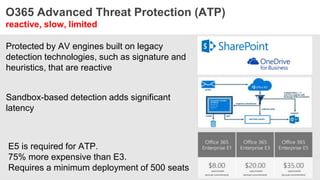
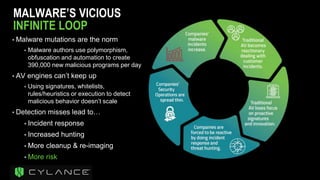
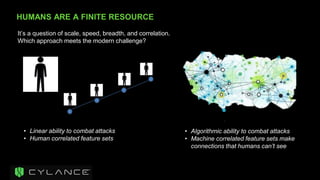
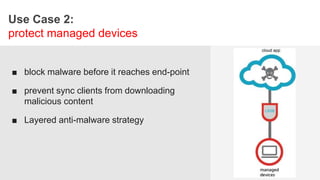
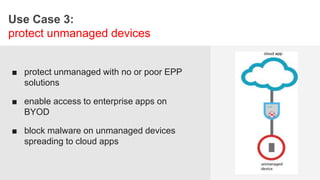
The document discusses the necessity of a new security strategy for cloud and mobile environments, emphasizing the inadequacy of traditional security methods against the rise of malware and advanced persistent threats. It outlines the capabilities of Cloud Access Security Brokers (CASBs) for holistic data protection, including detailed logging, contextual access control, and advanced threat detection via AI. Additionally, it highlights the importance of proactive malware protection and behavioral analysis to combat rapidly evolving threats effectively.