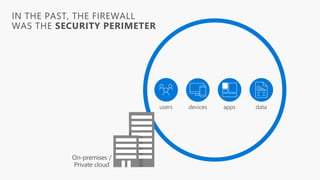
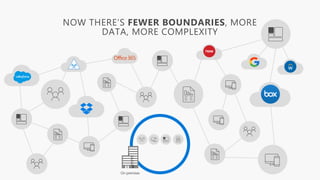
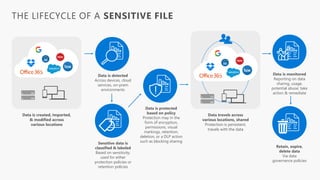
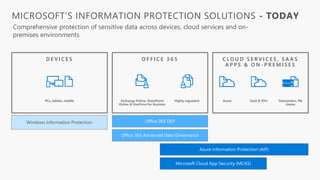
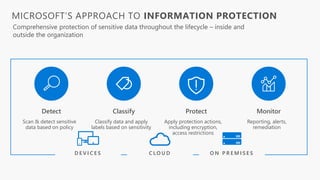
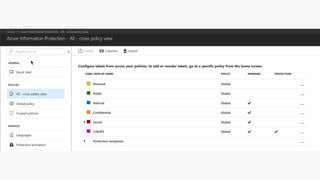
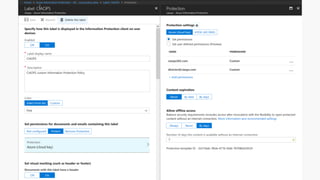
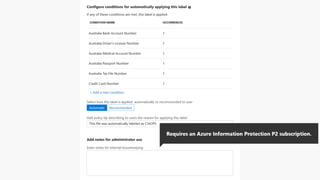
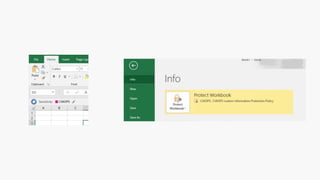
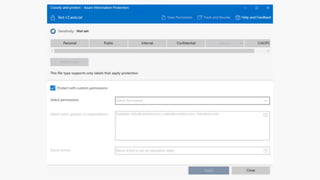
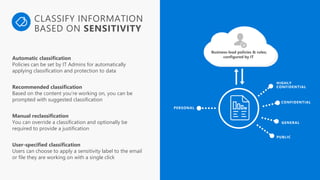
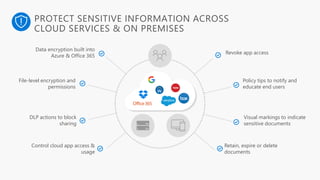
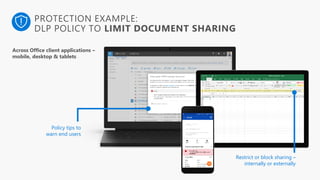
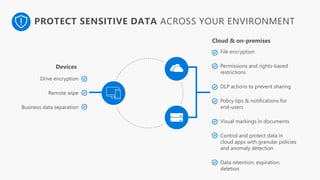
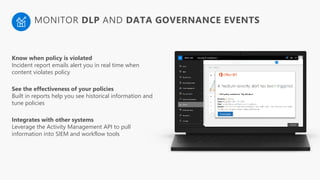
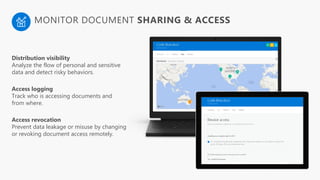
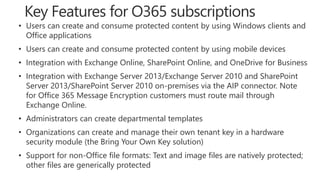
Detect, classify, and protect sensitive information across cloud services and on-premises environments. Microsoft's solutions can scan for sensitive data, classify it based on sensitivity levels, and apply protections like encryption, access restrictions, and policies. Administrators can monitor protection events, access, and sharing for control and to tune policies.