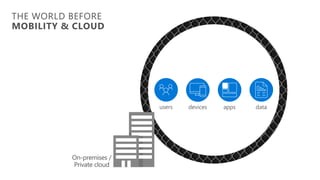
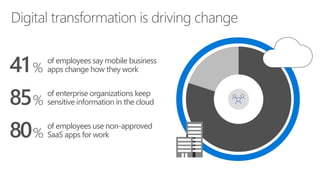
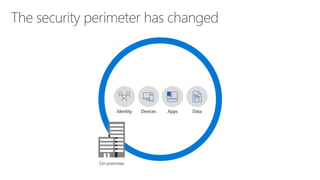
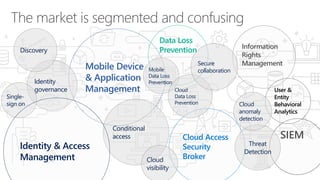
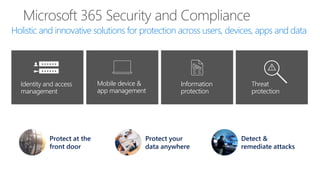
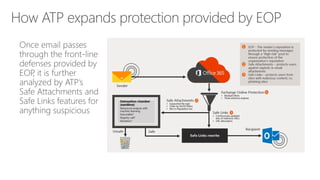
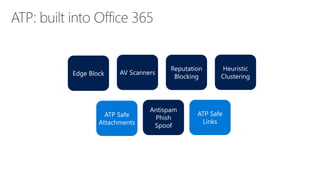
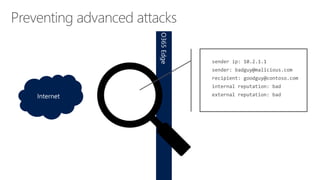
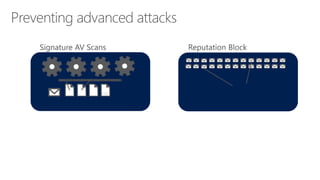
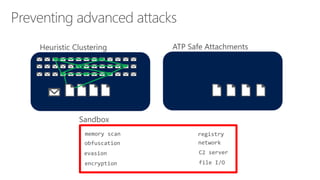
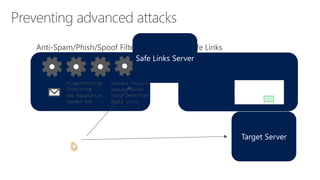
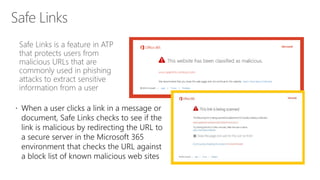
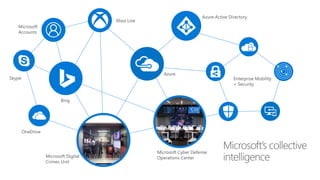
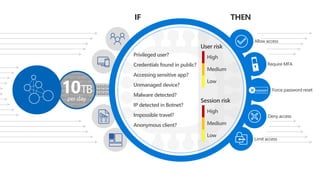
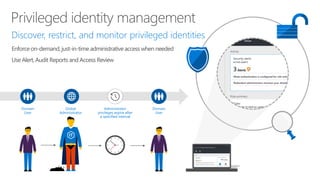
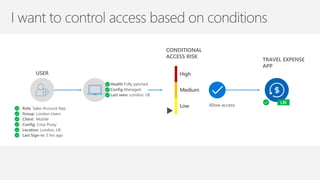
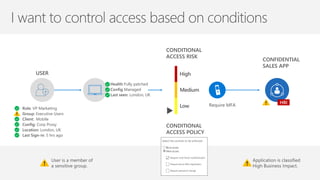
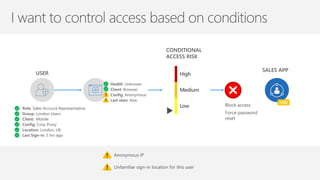
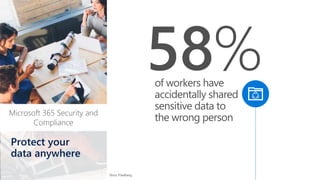
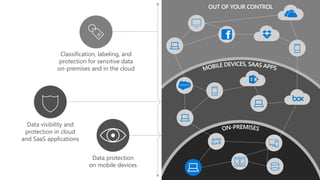
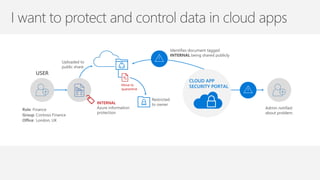
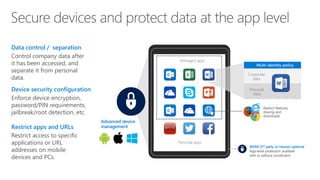
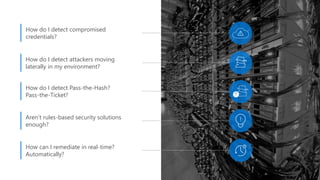
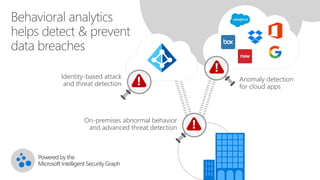
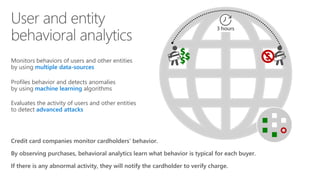
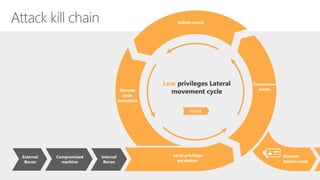
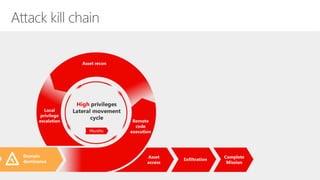
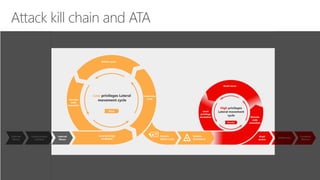
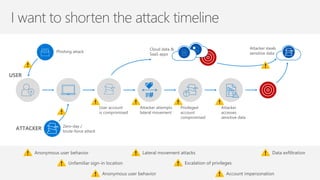
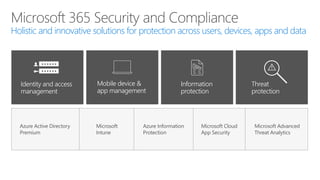
The document discusses security challenges in a mobile-first, cloud-first world where data, users, devices, and apps are distributed across on-premises, private cloud, public cloud, and mobile environments. It outlines how traditional perimeter-based security is no longer effective and Microsoft 365 provides a holistic solution to protect organizations at the front door, detect and remediate attacks, and protect data anywhere it goes.