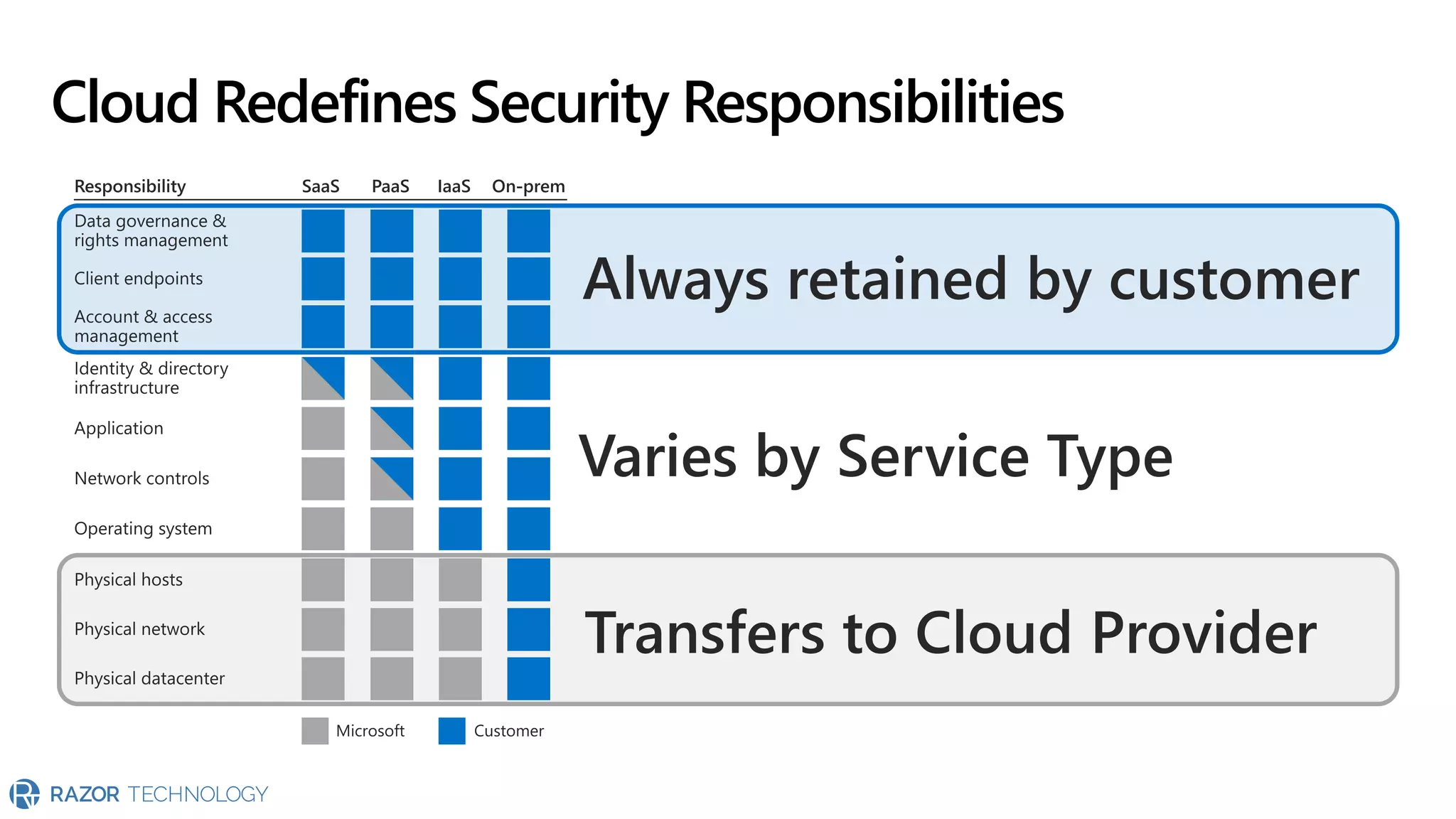
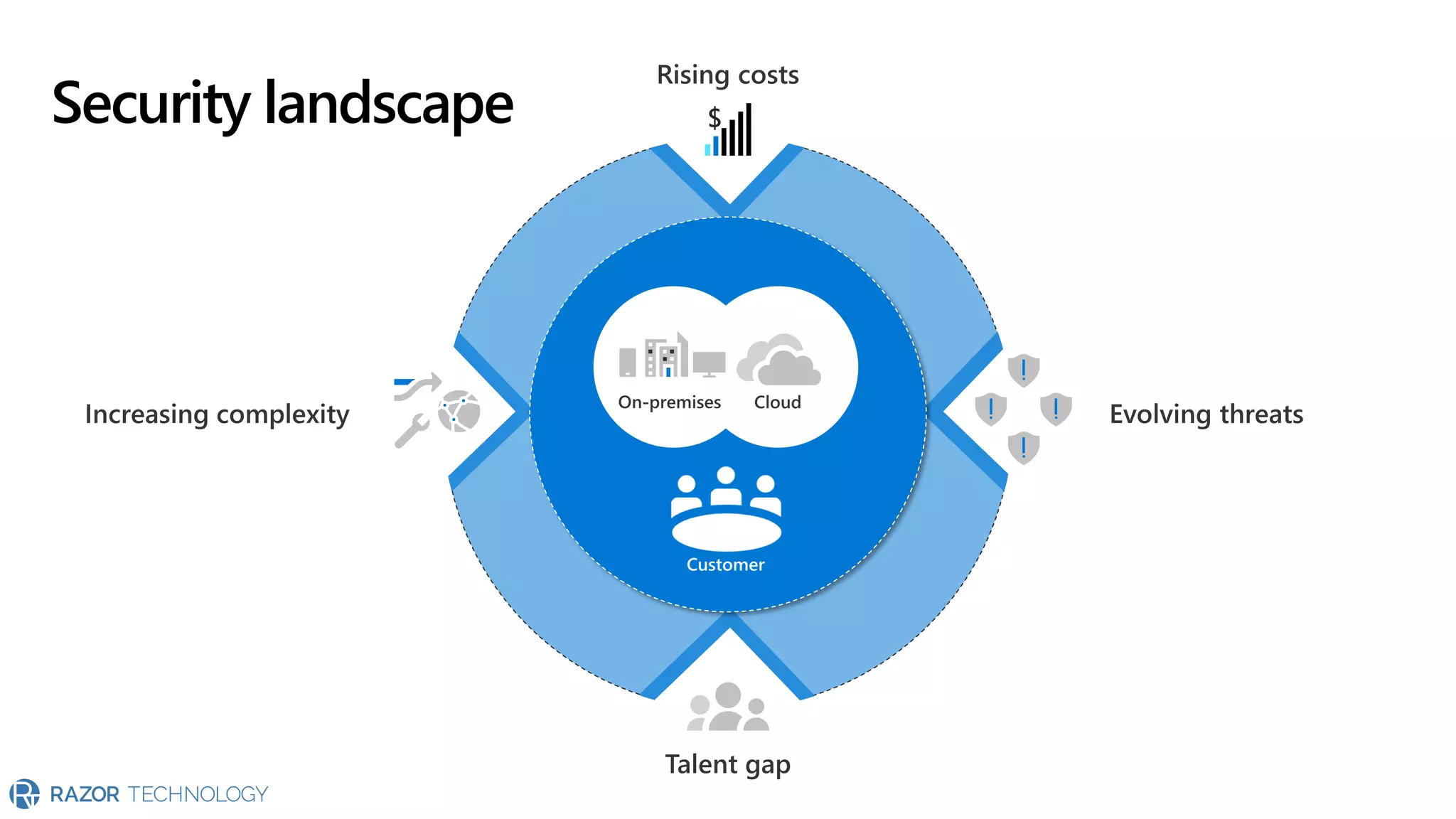
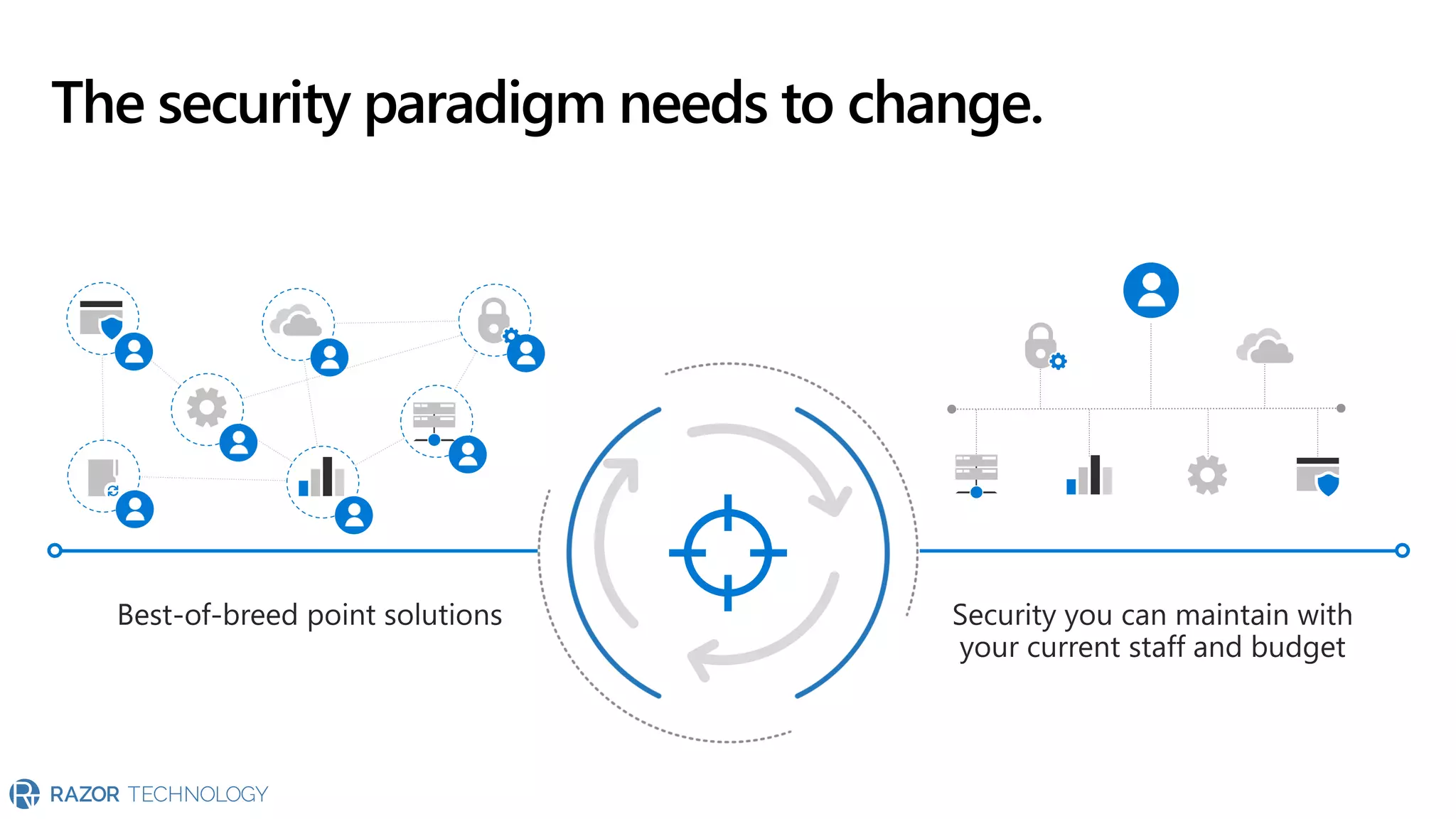
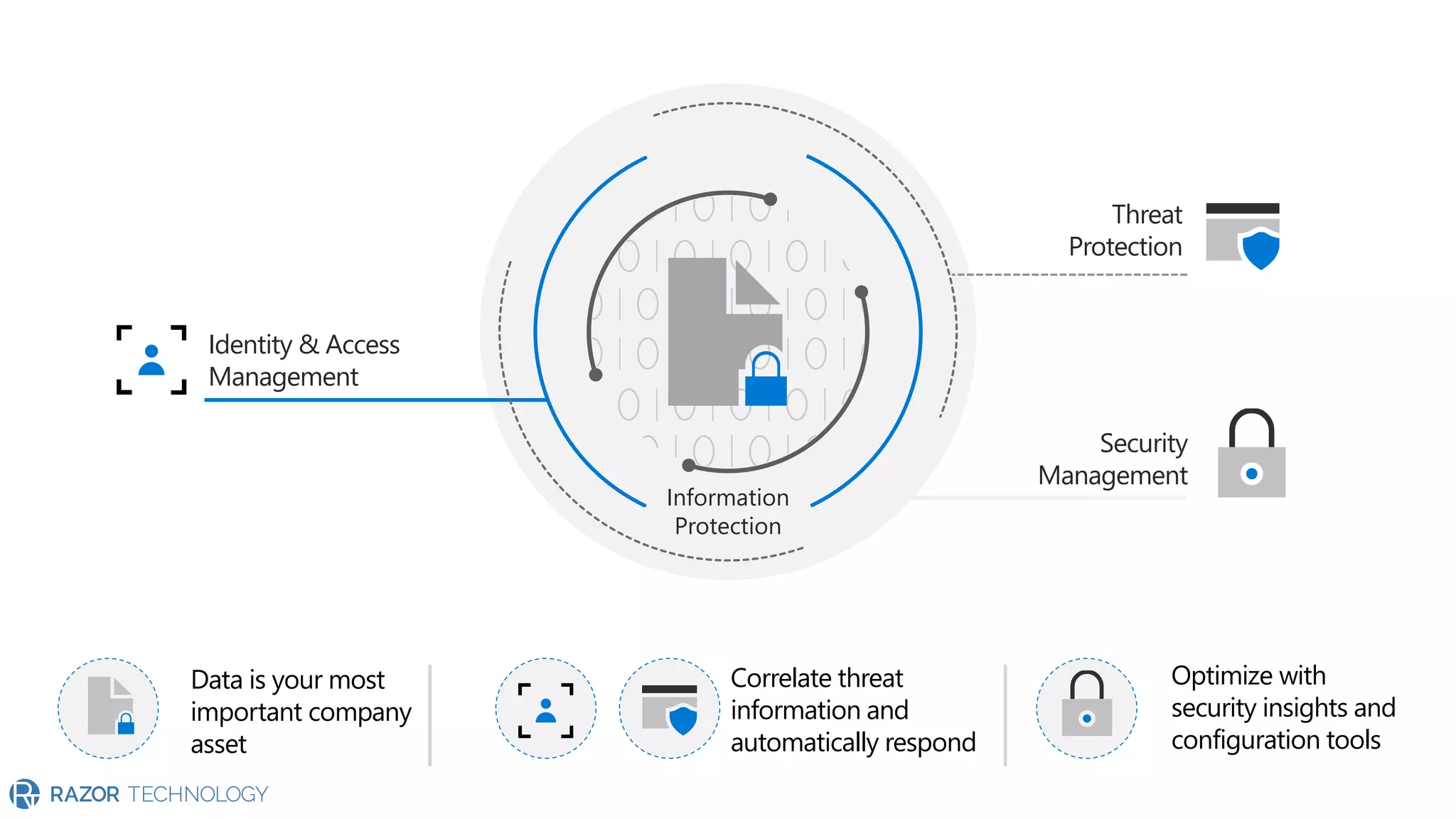
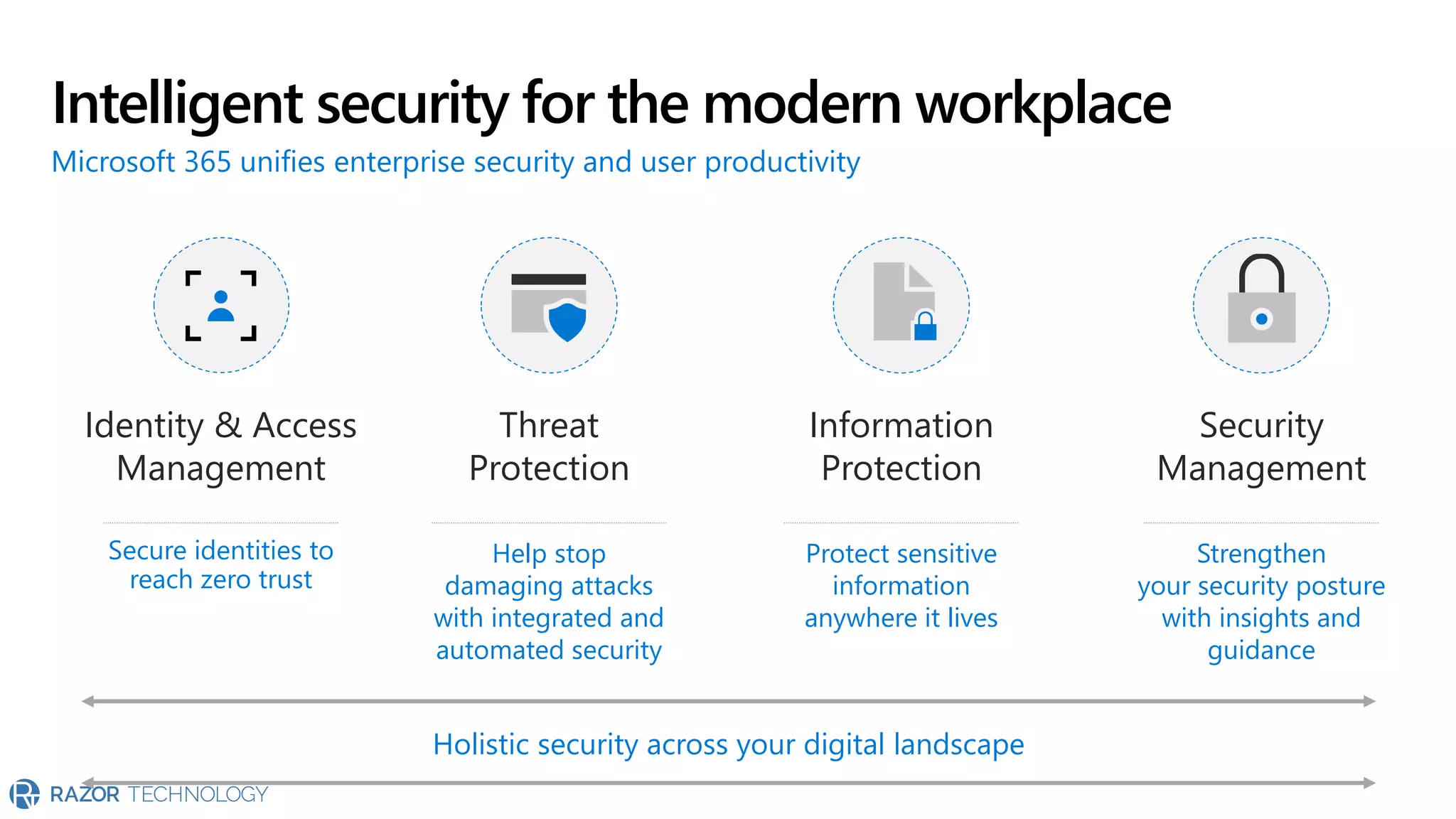
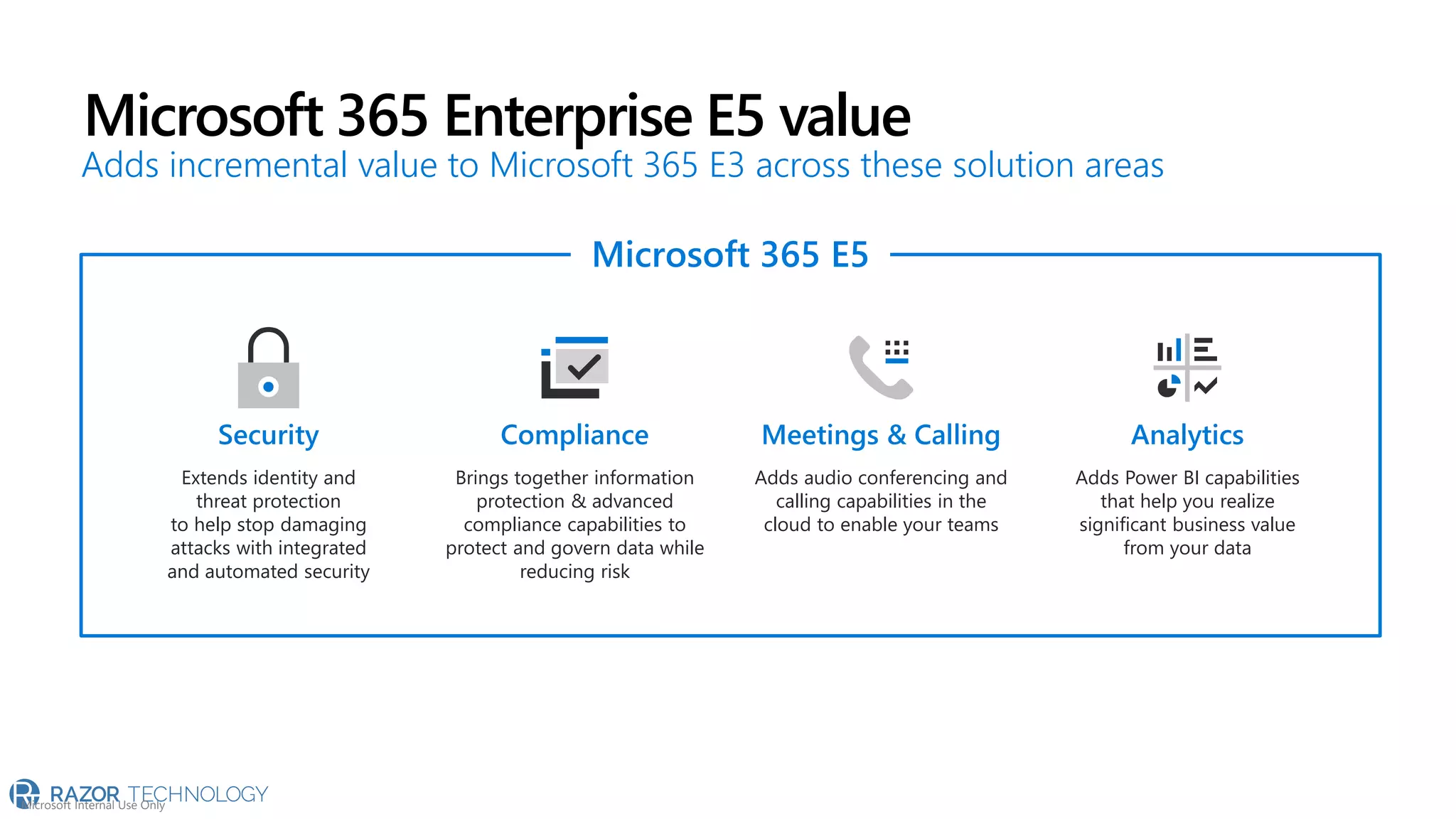
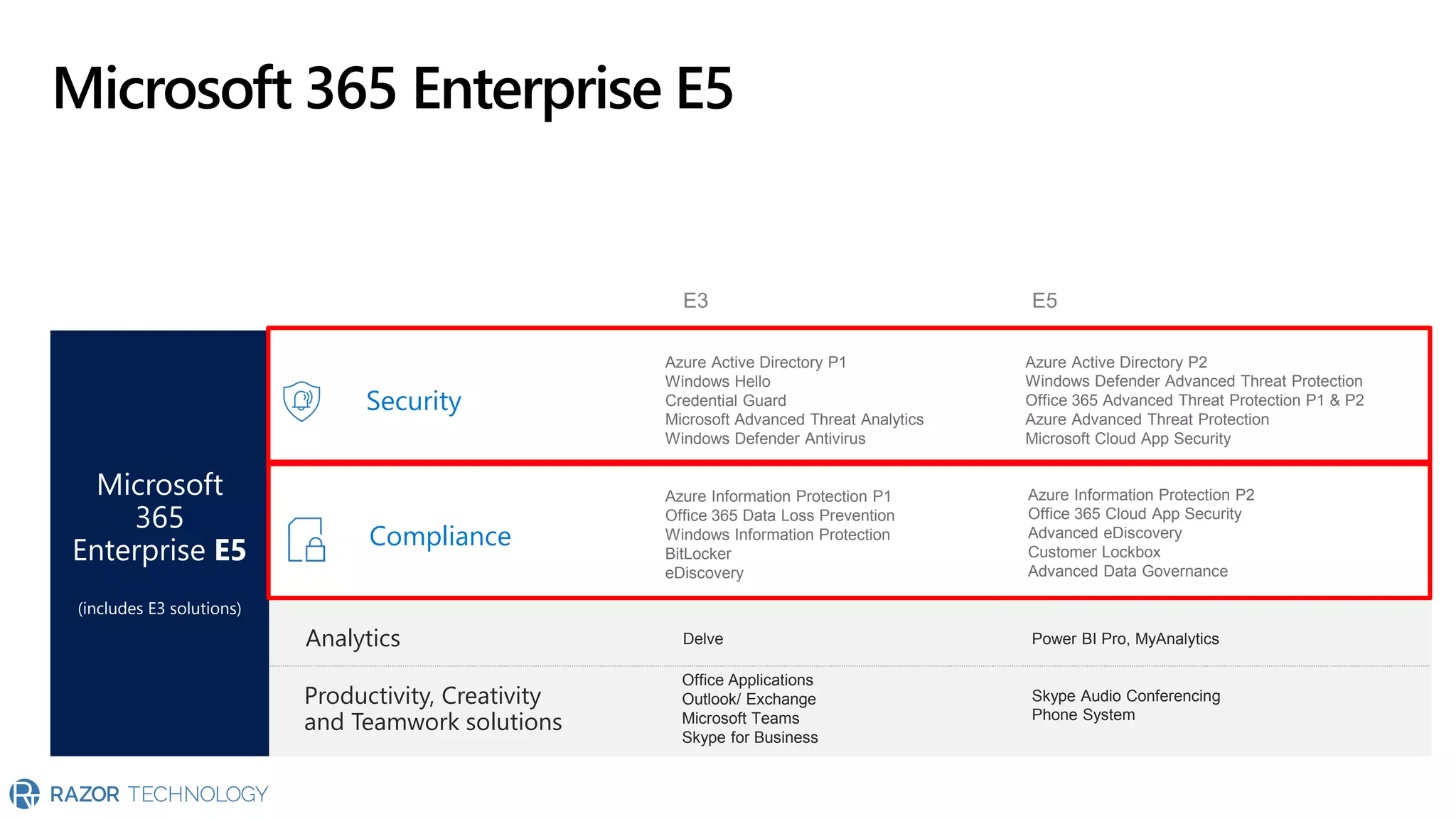
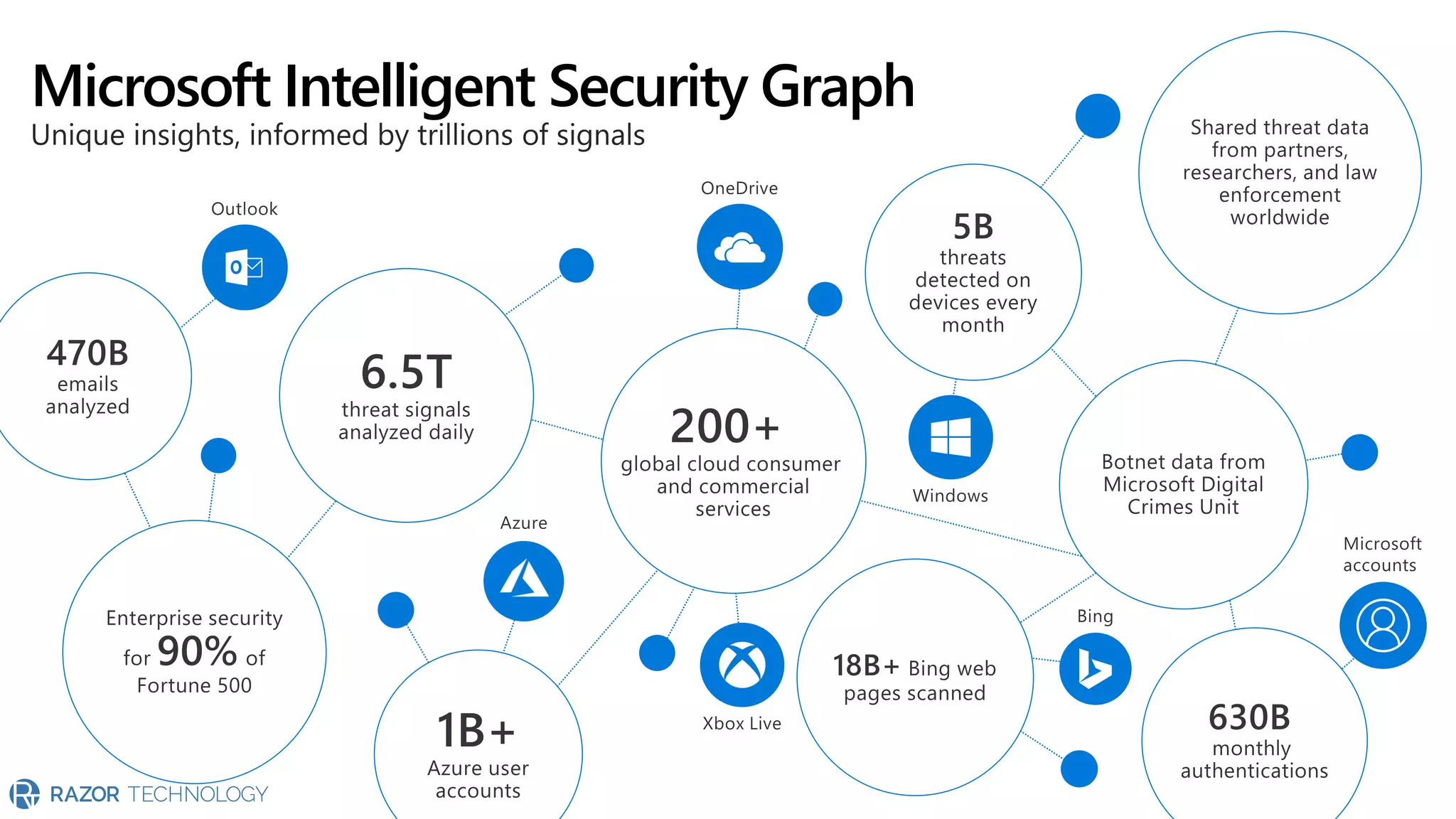
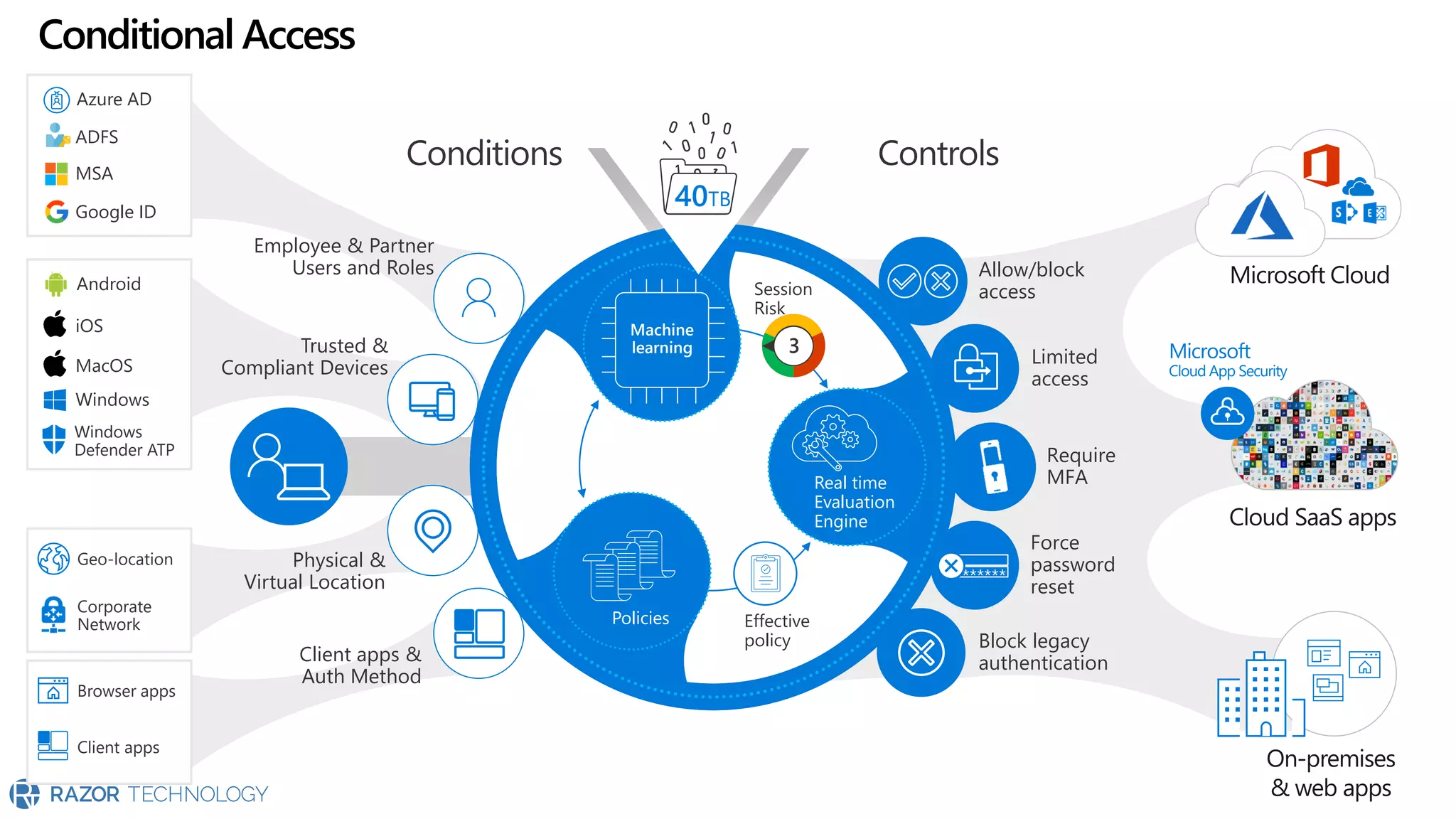
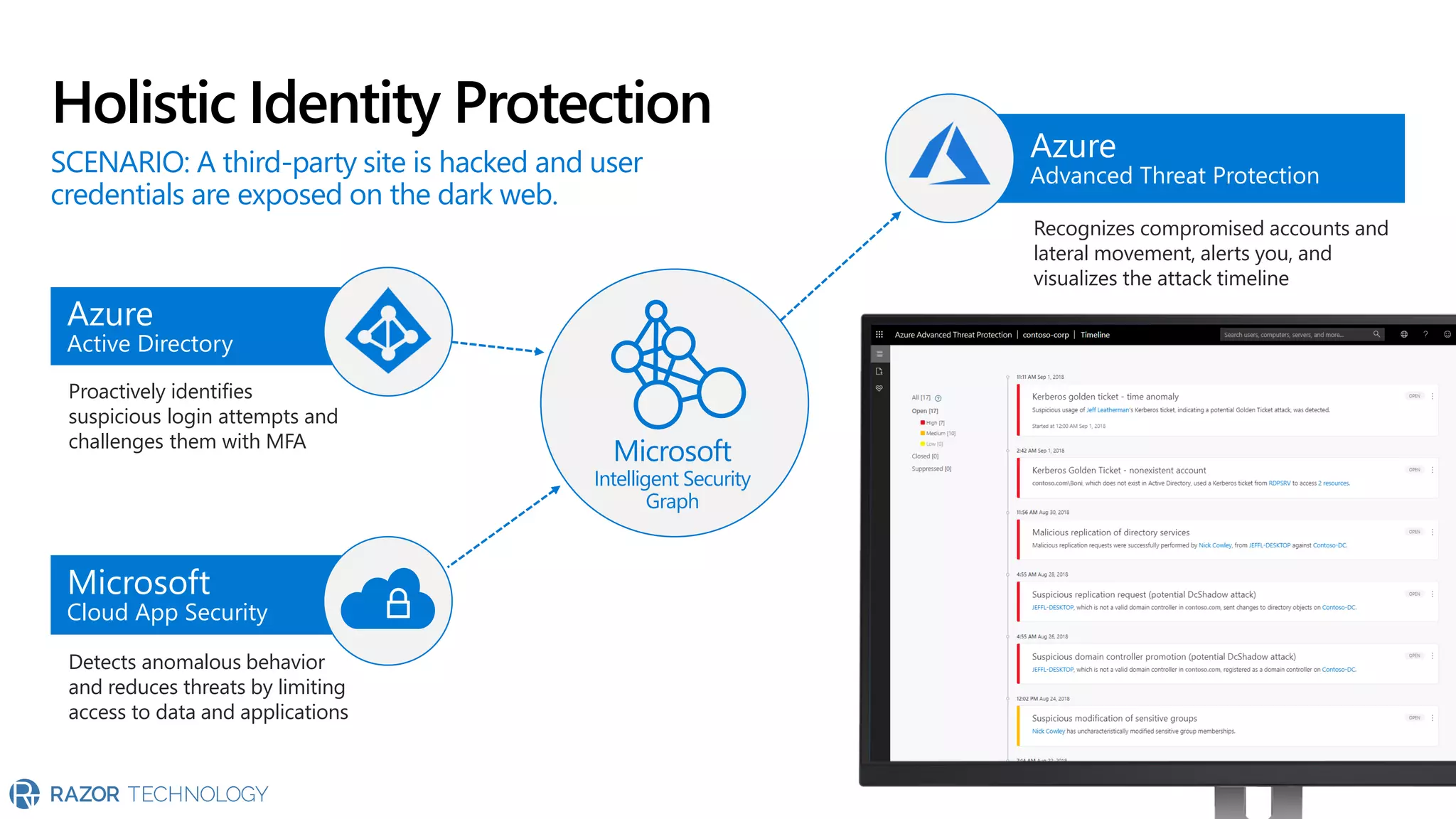
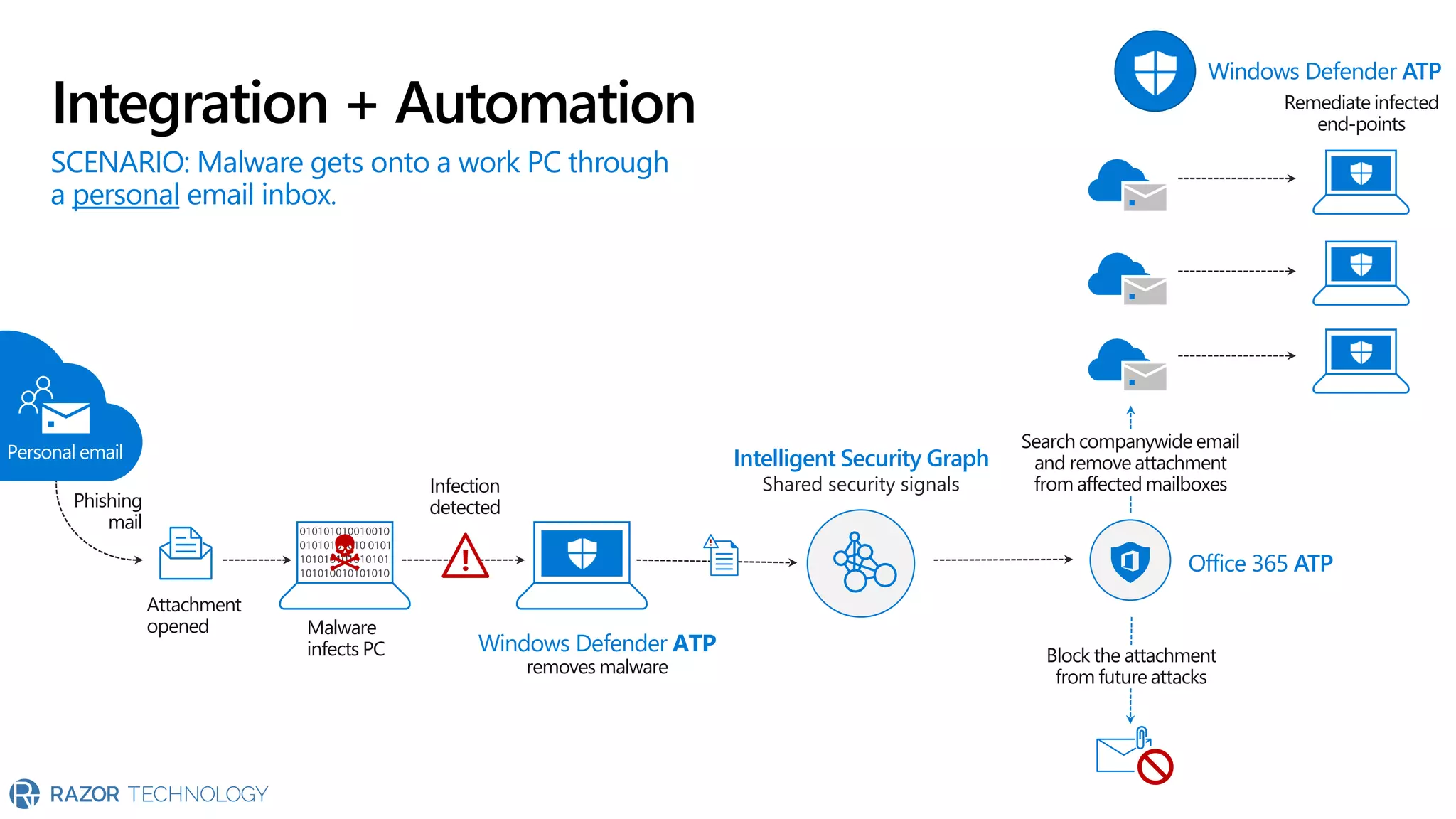
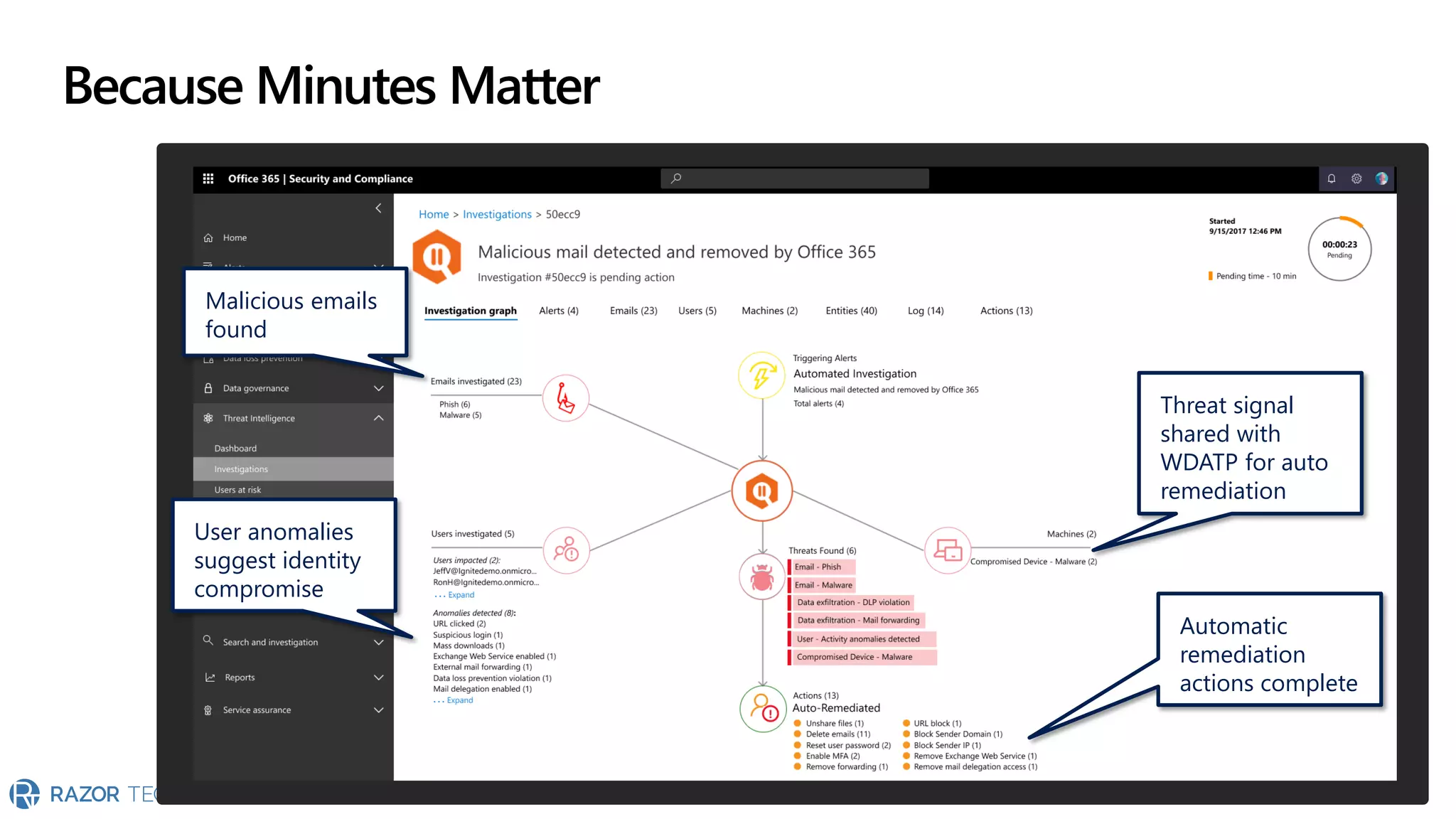
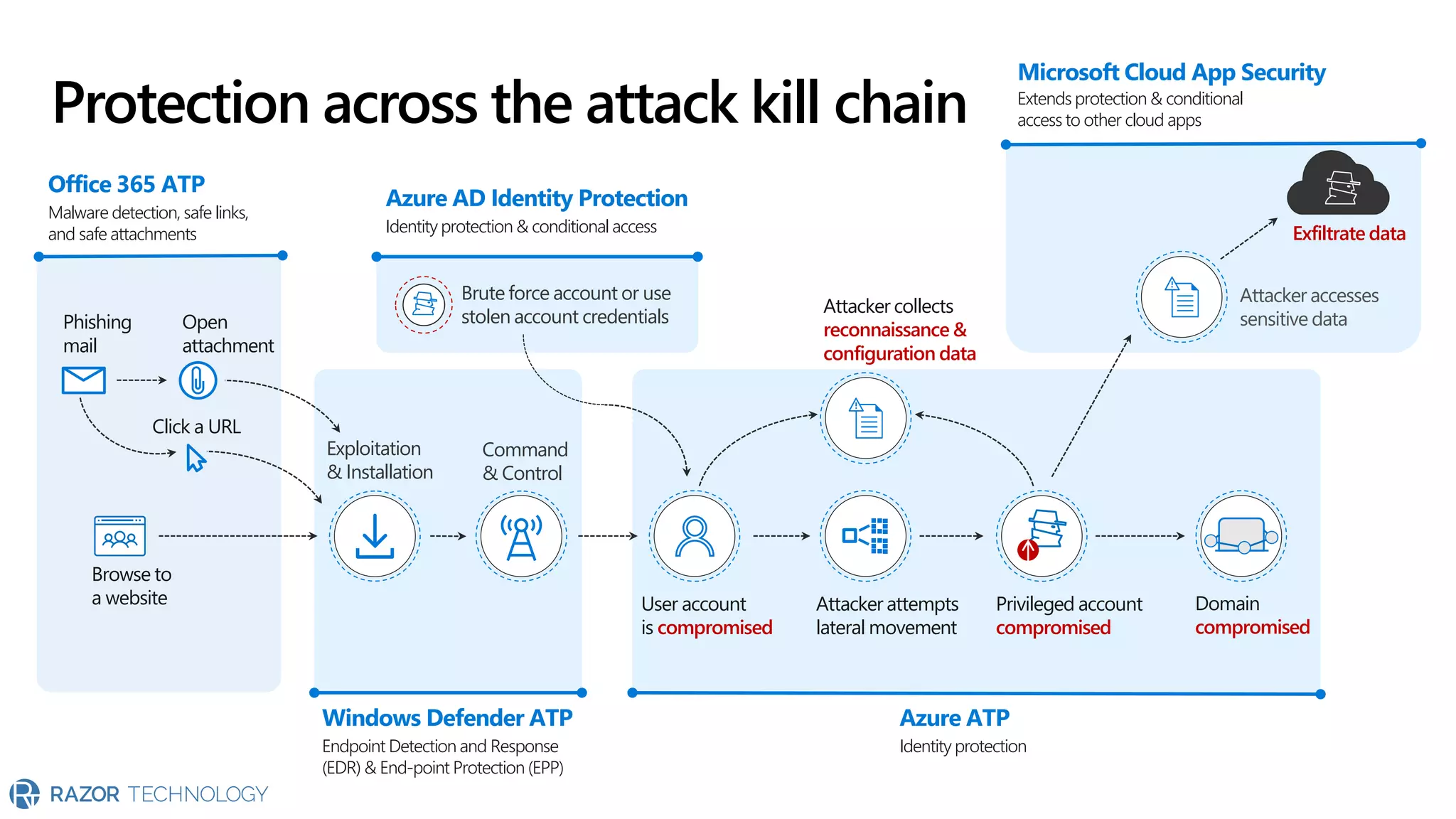
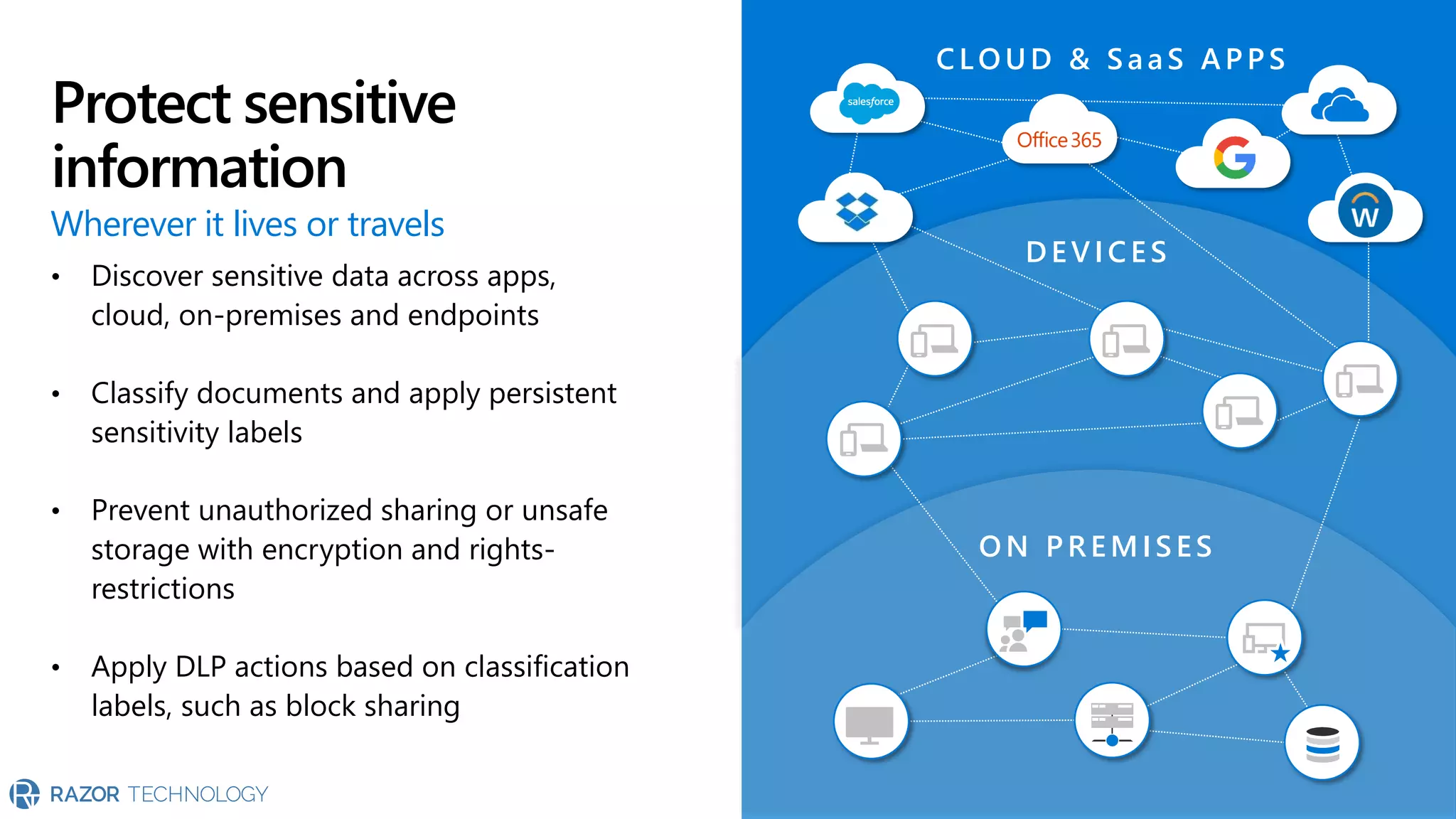
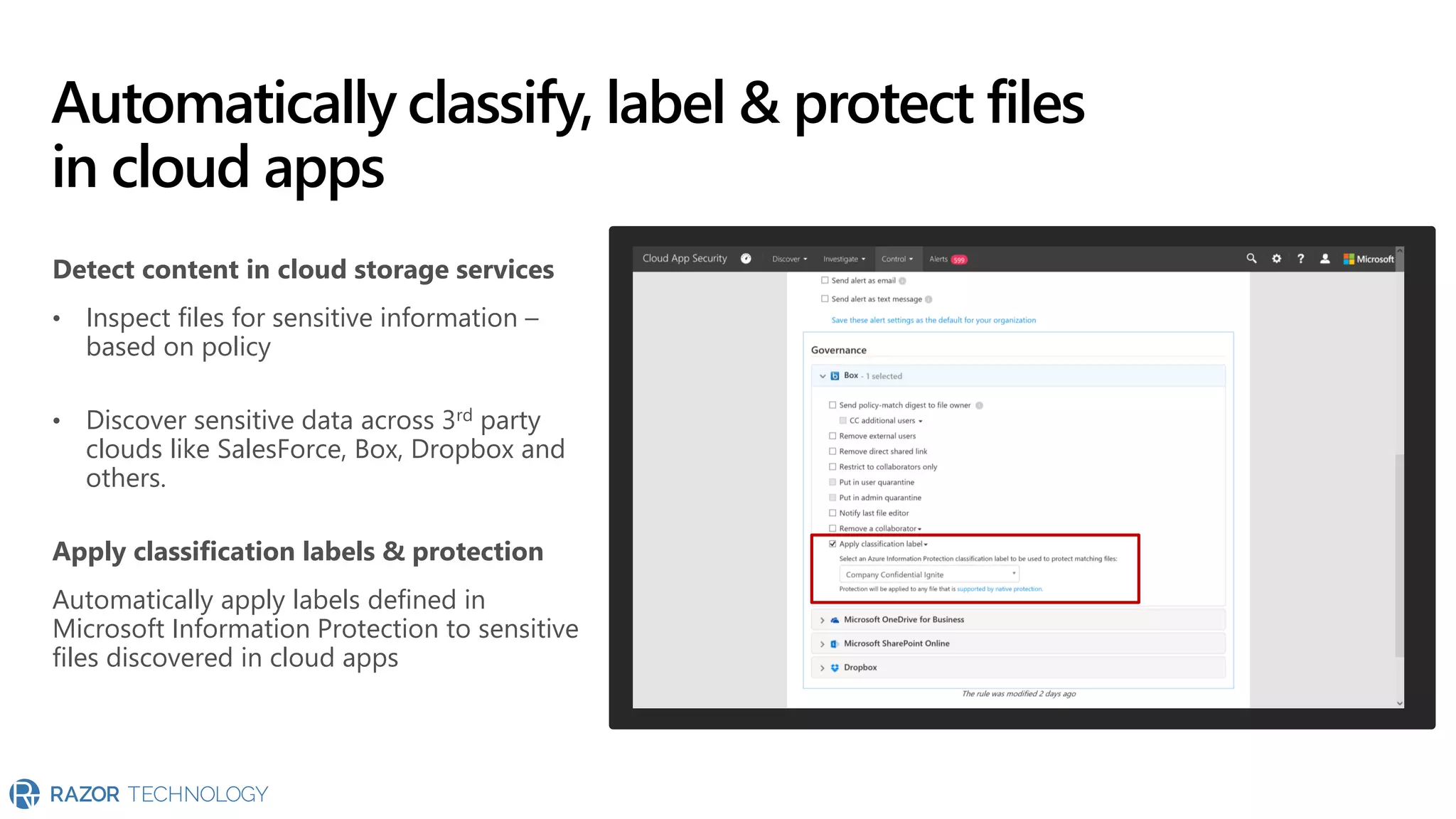
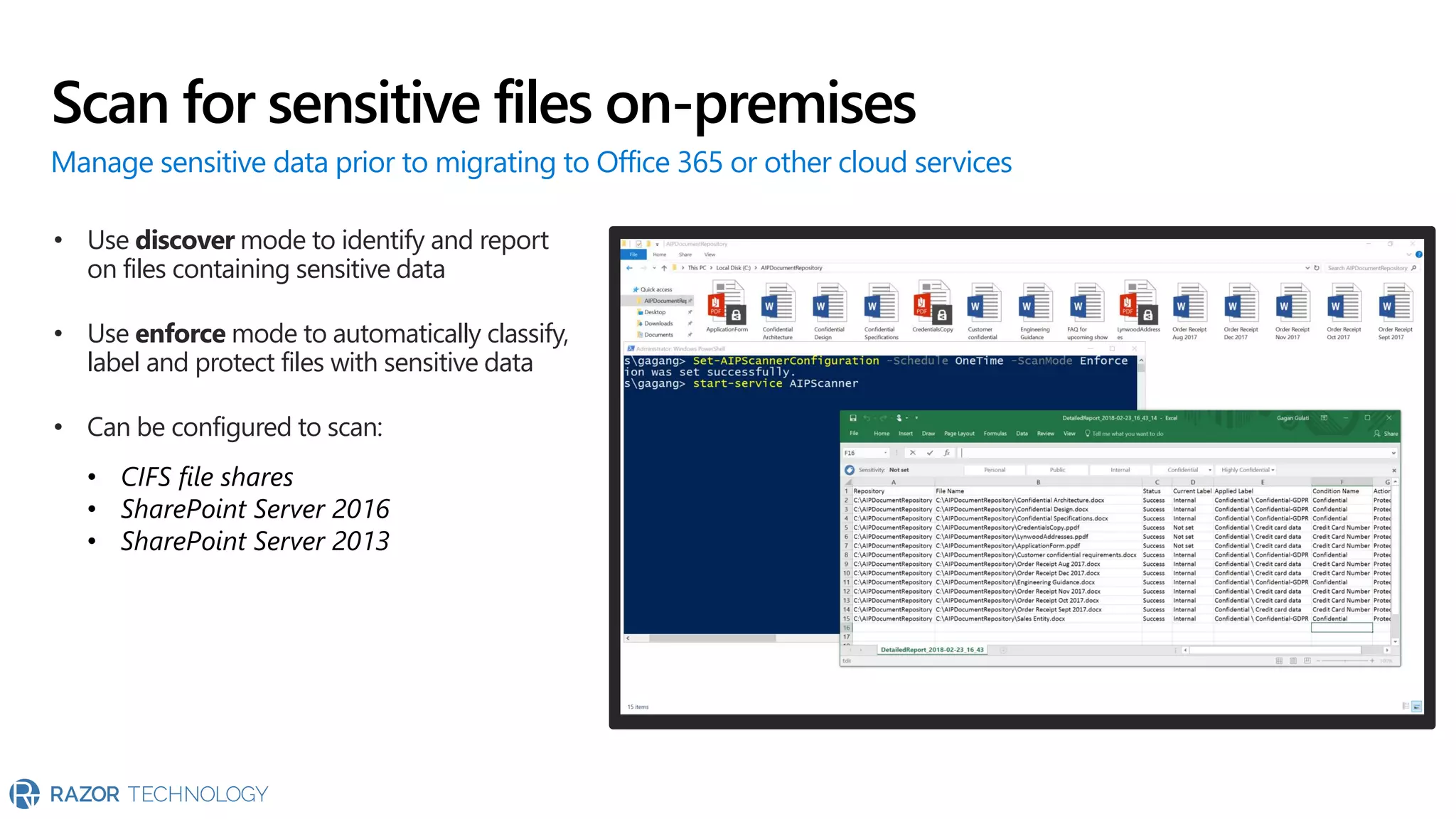
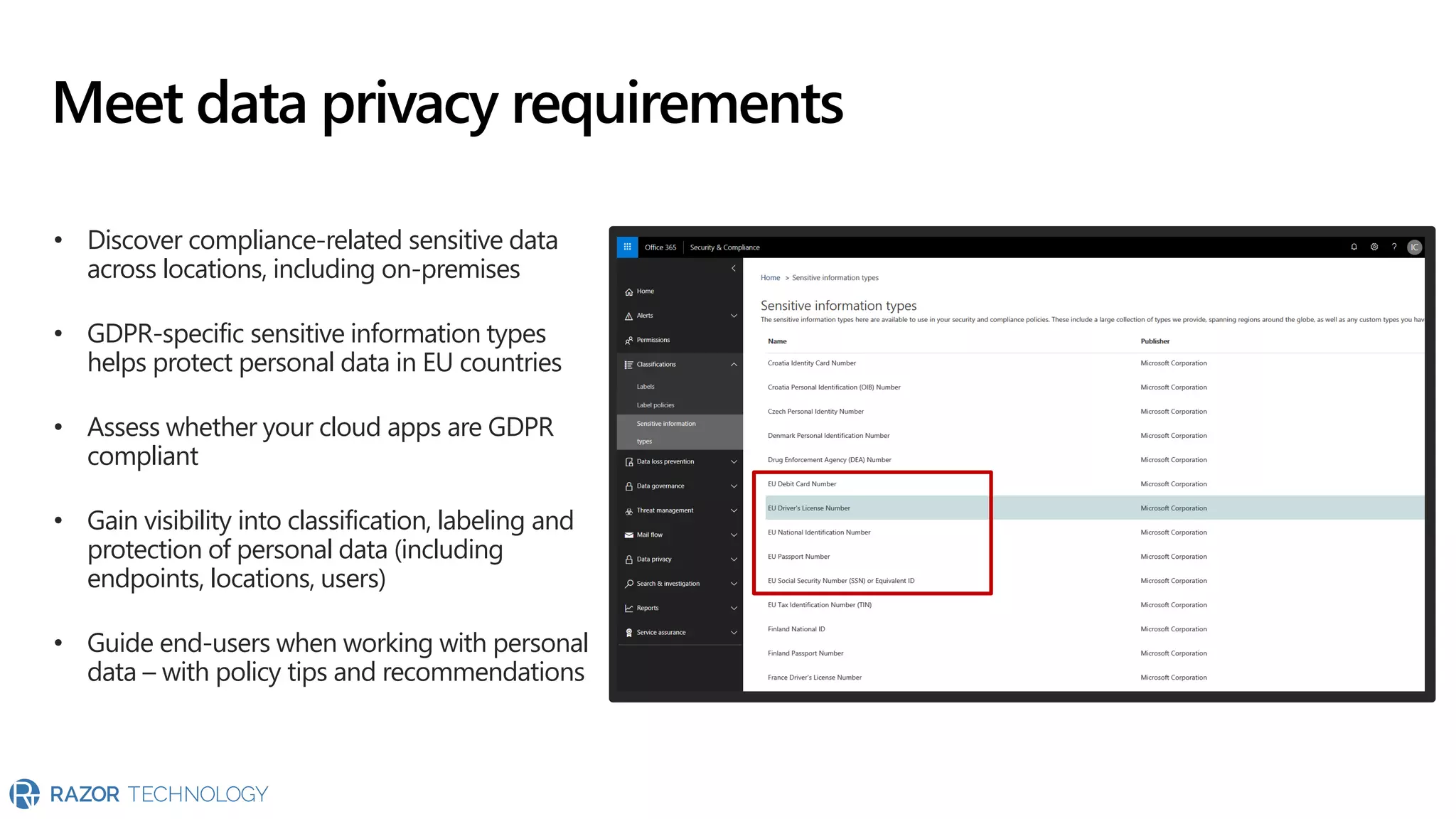
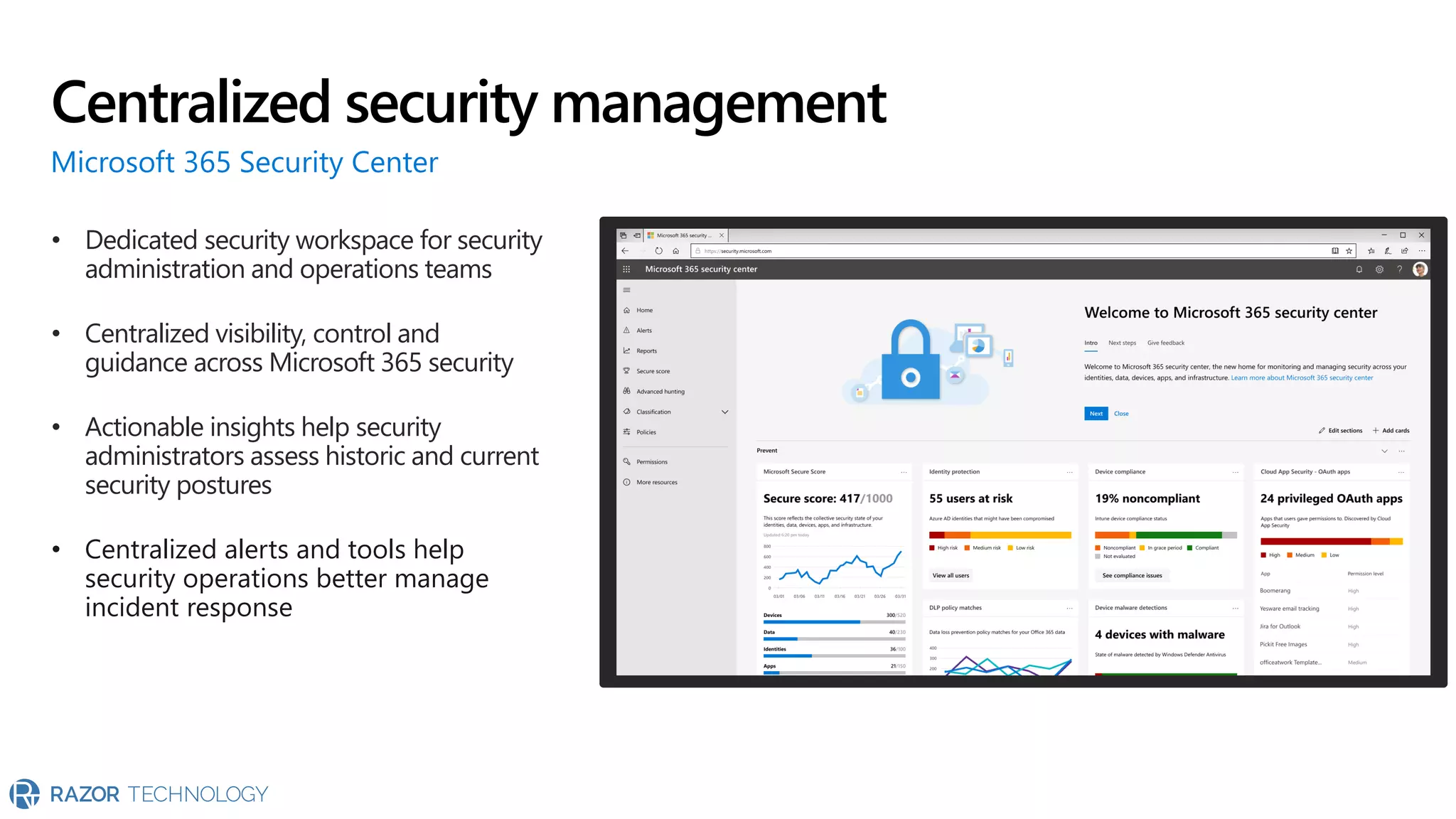
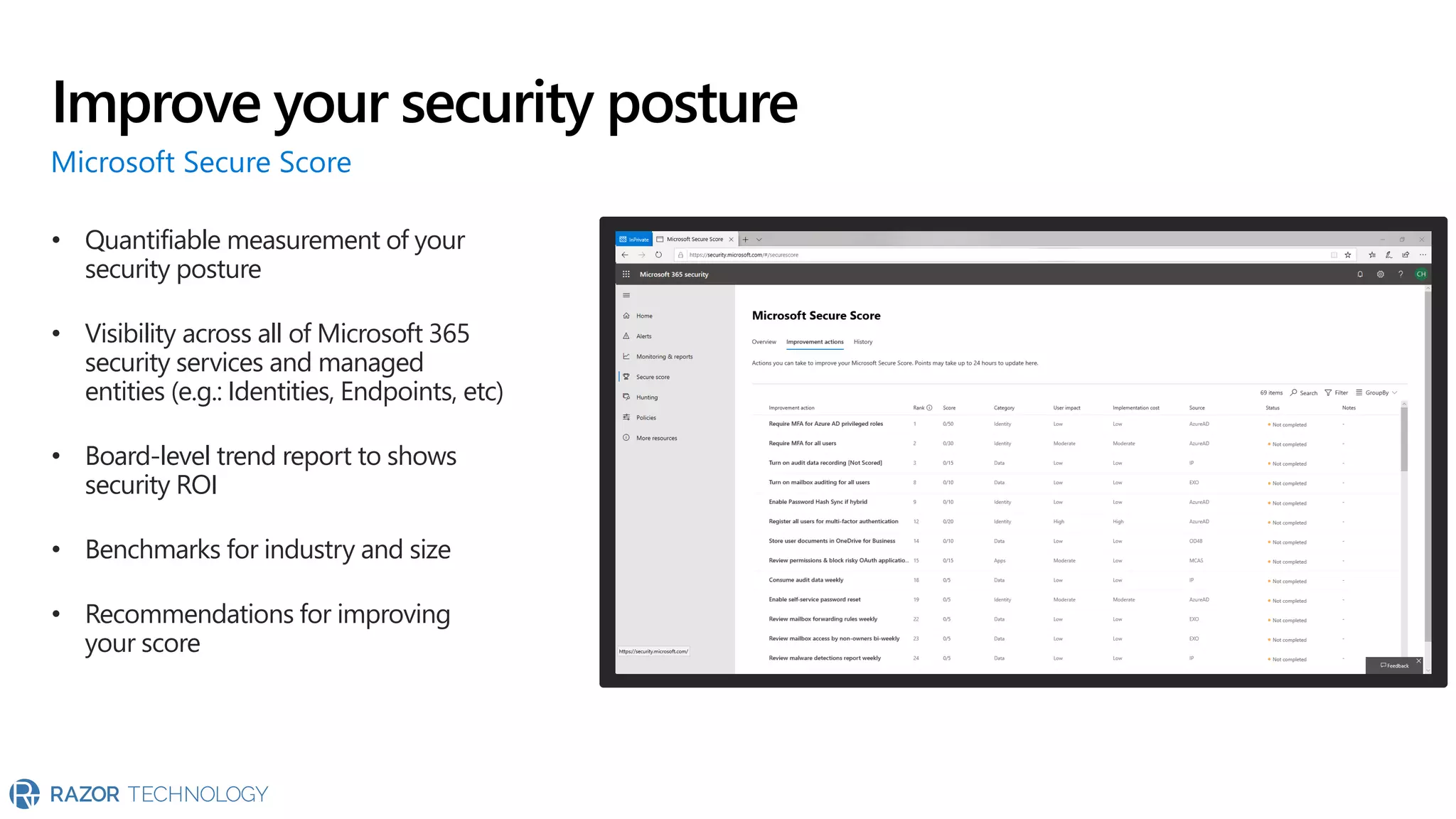
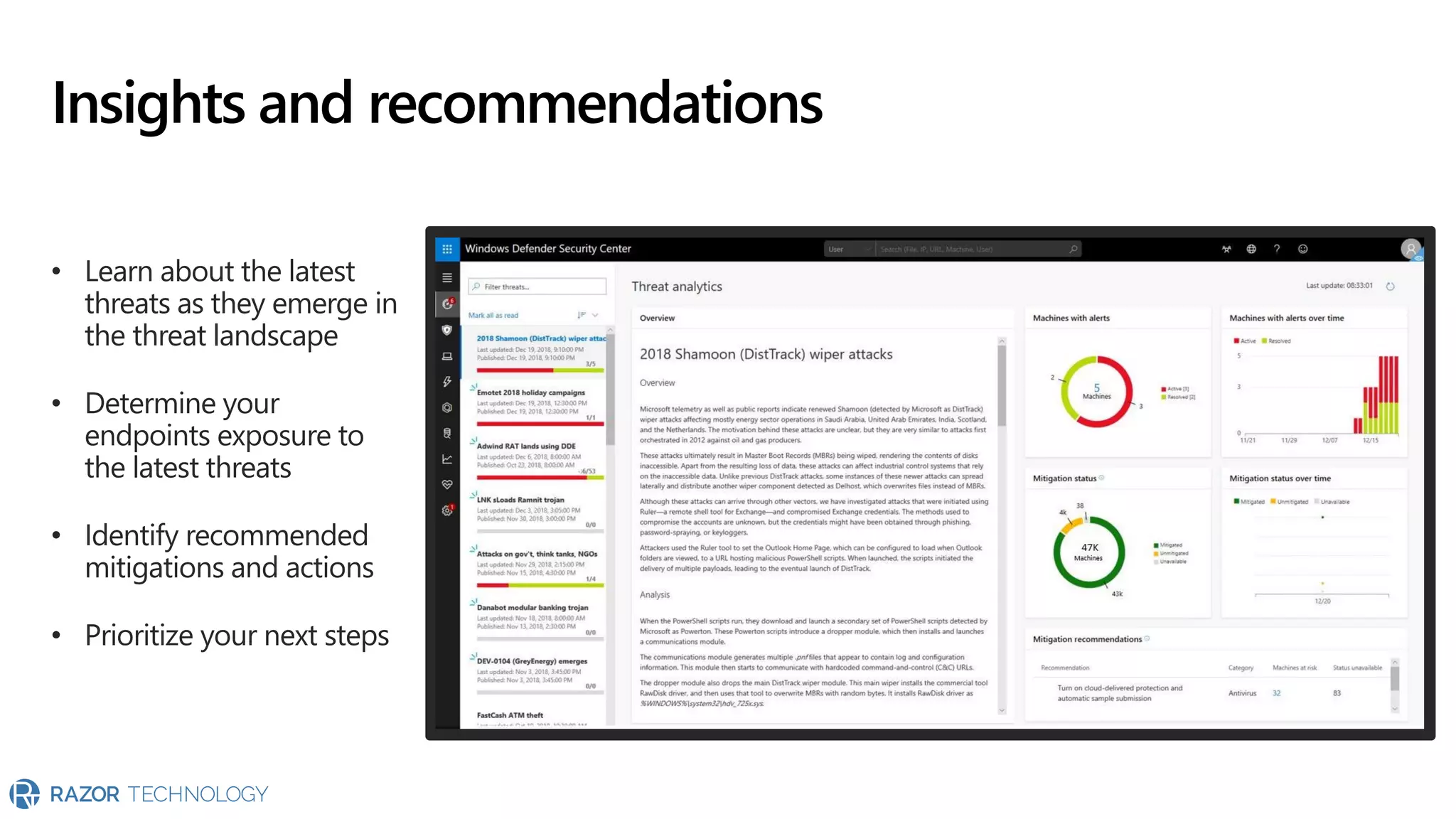
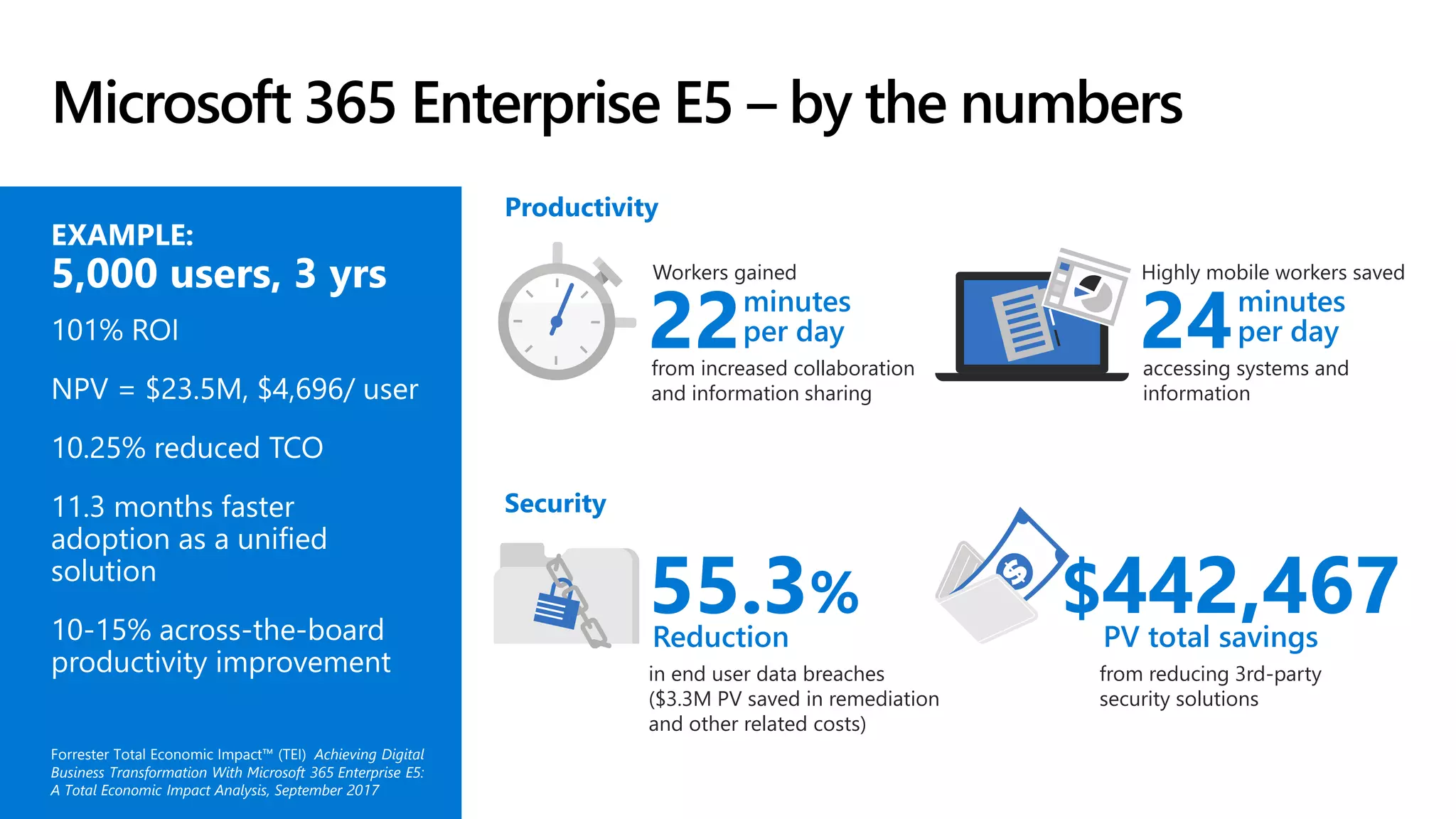
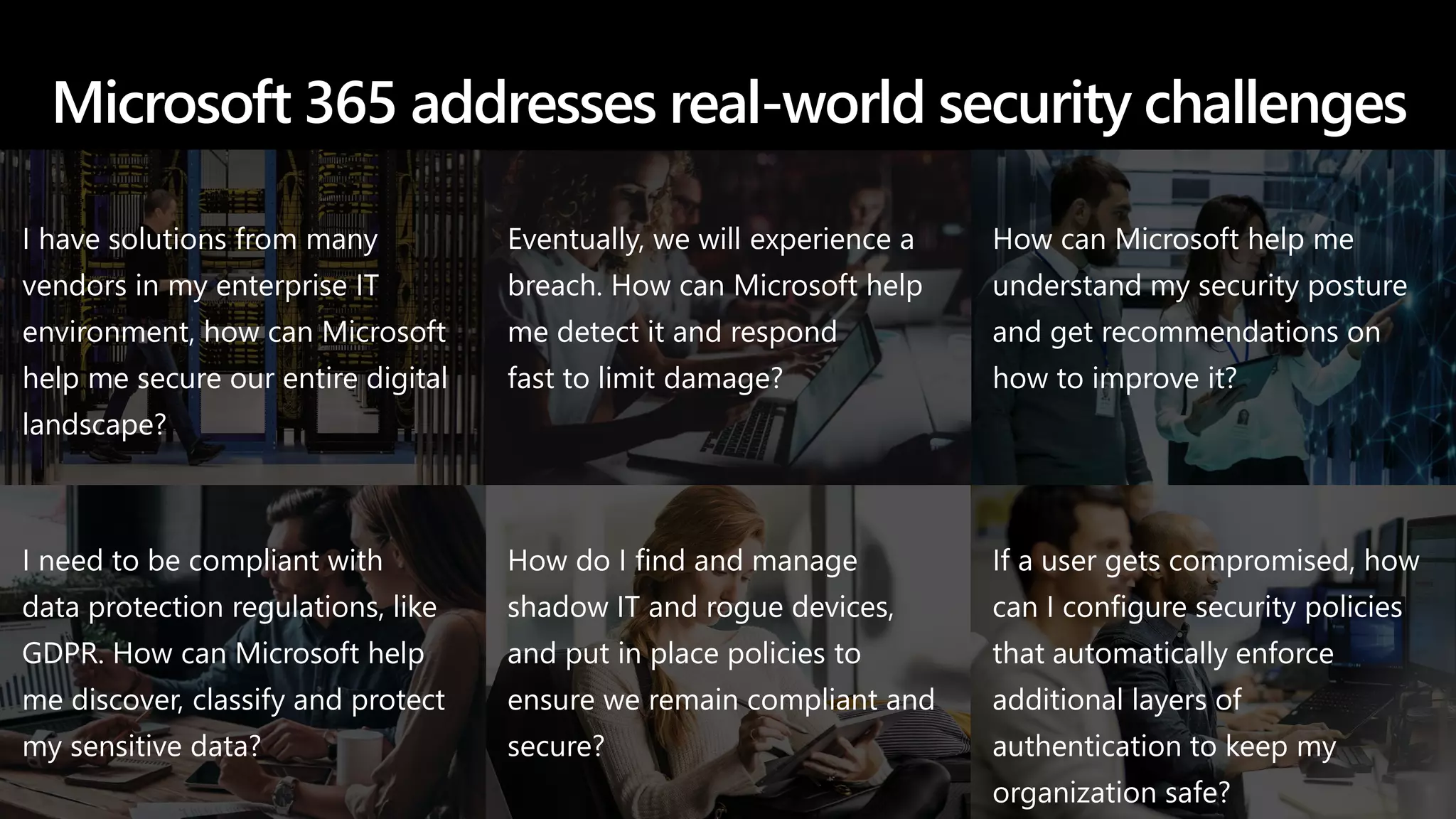
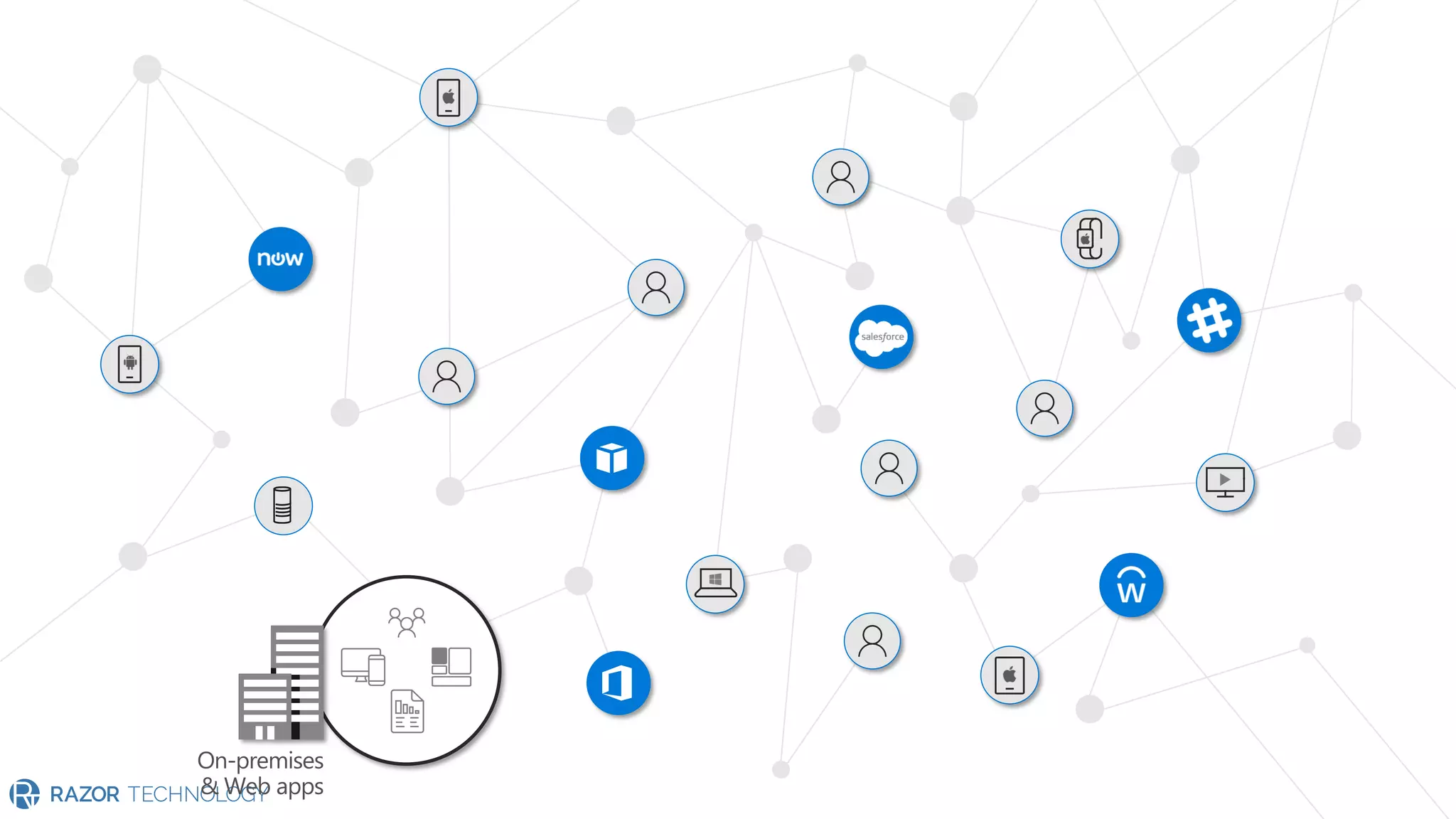
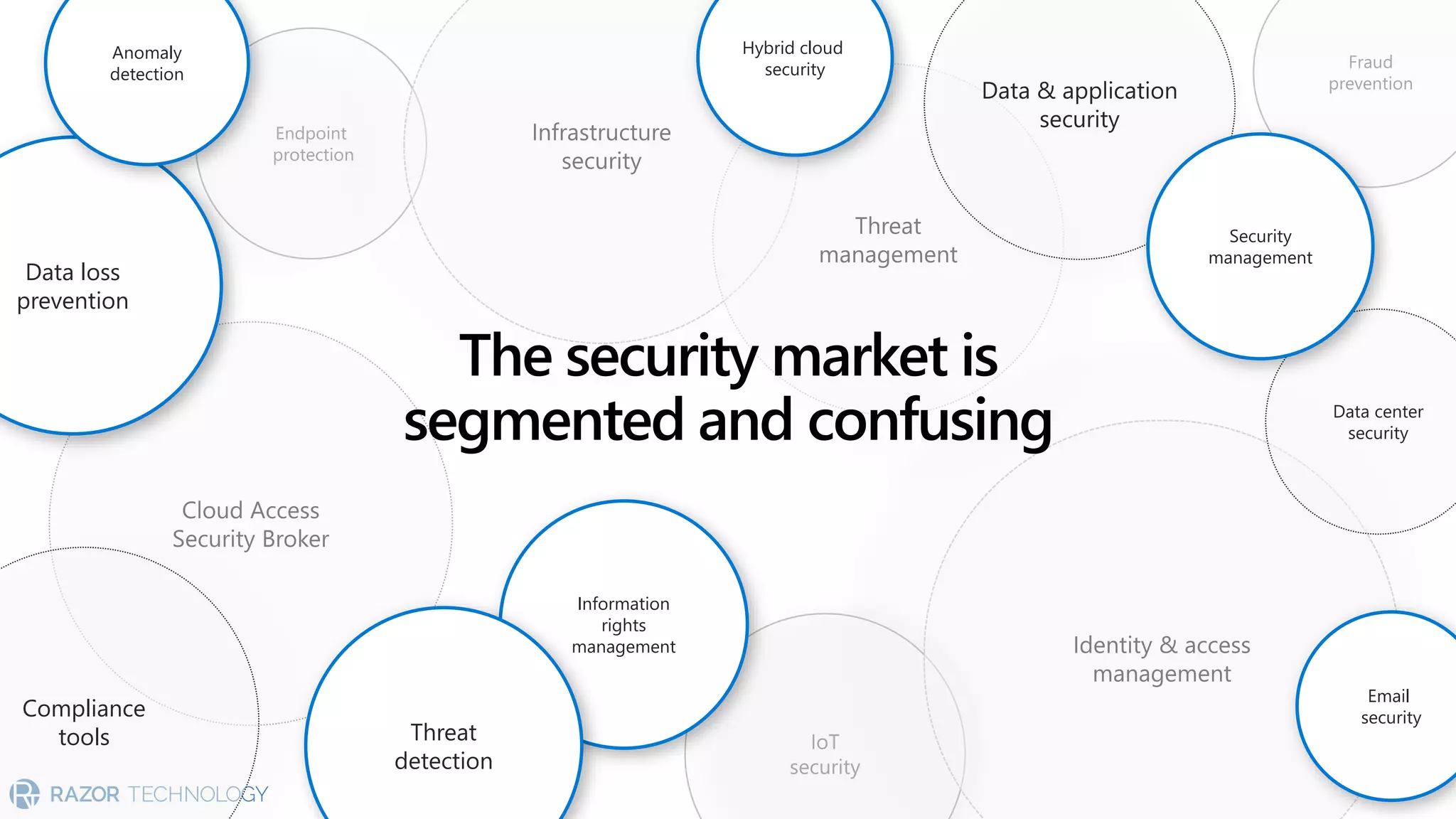
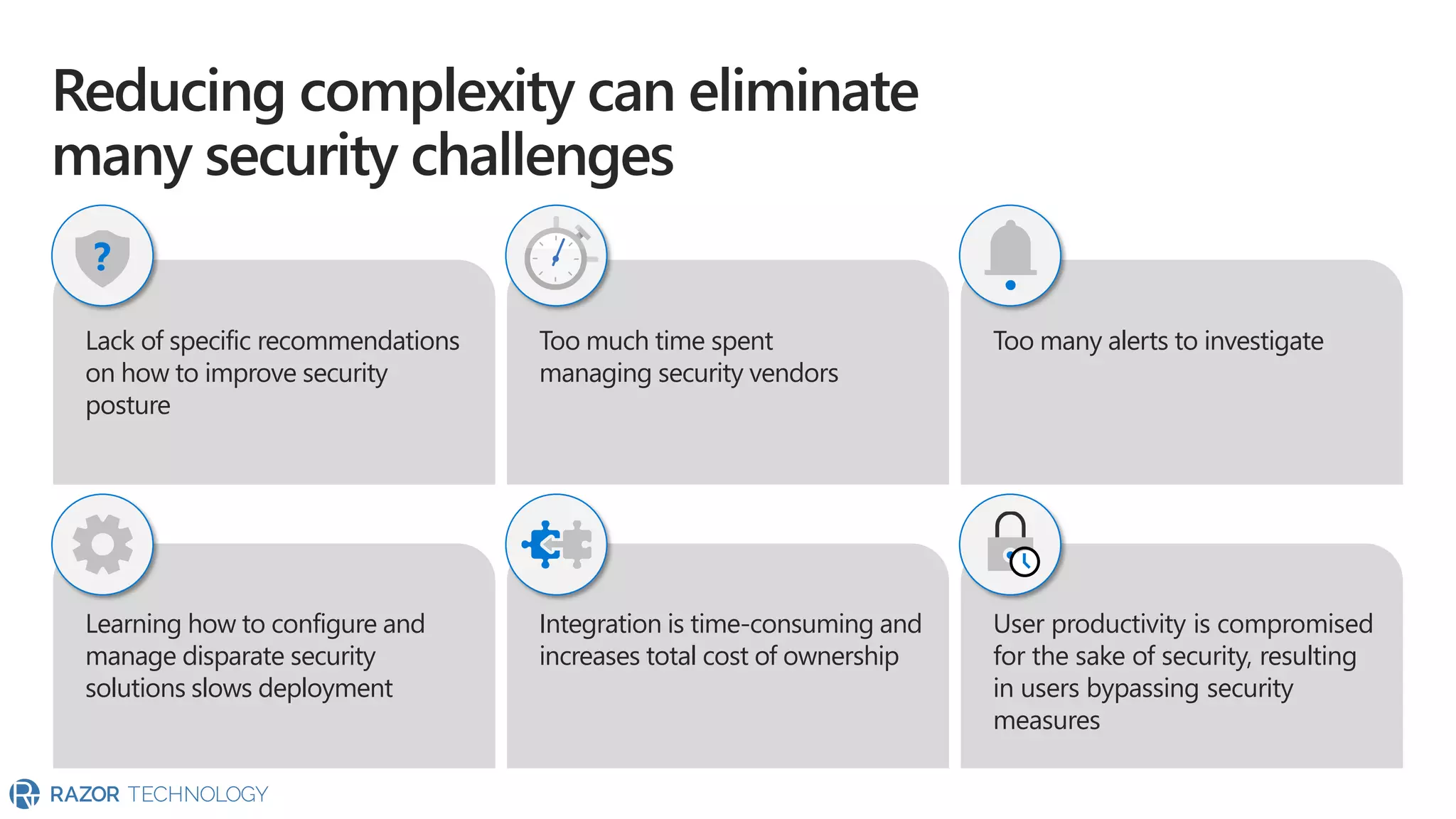
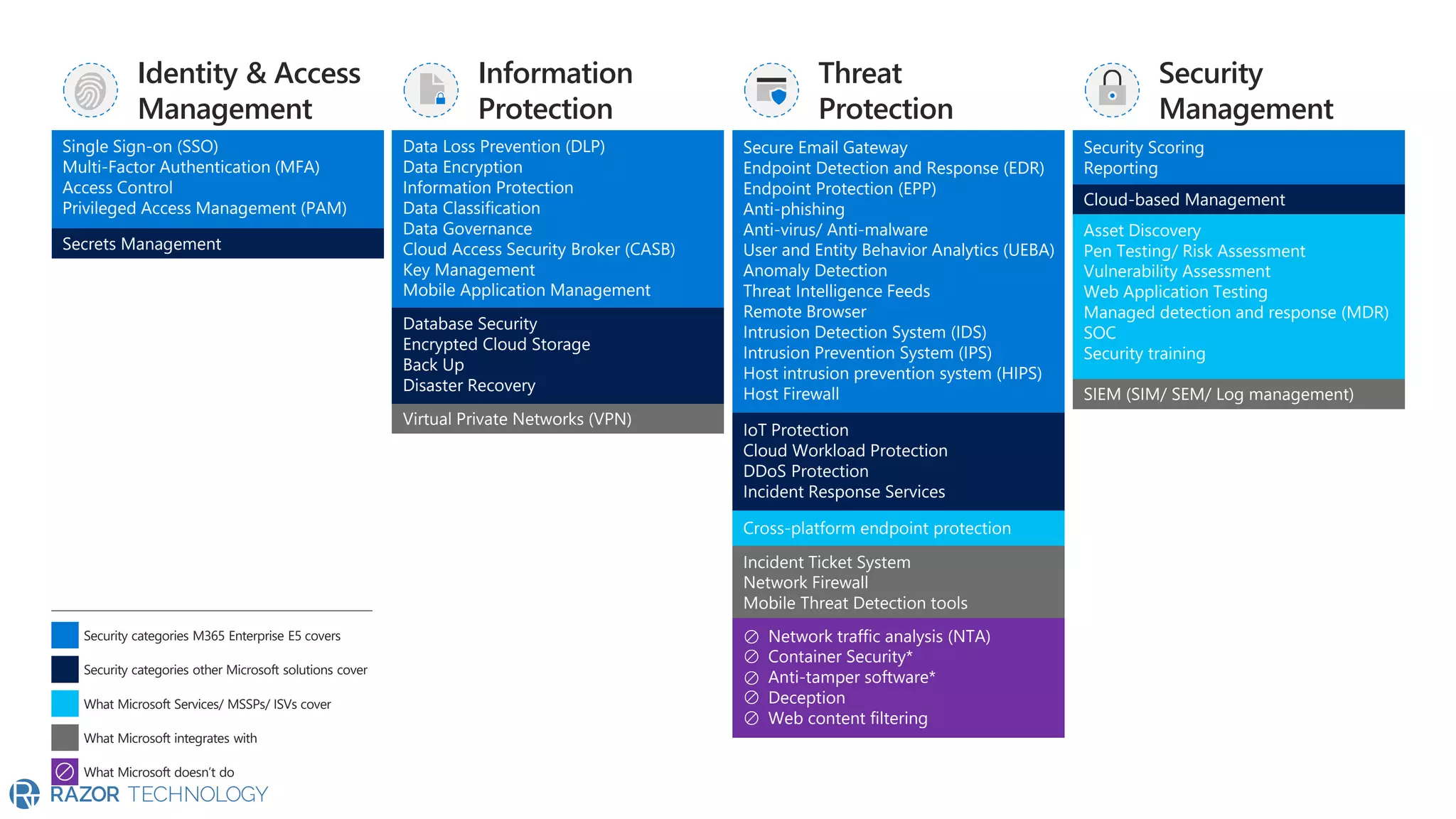
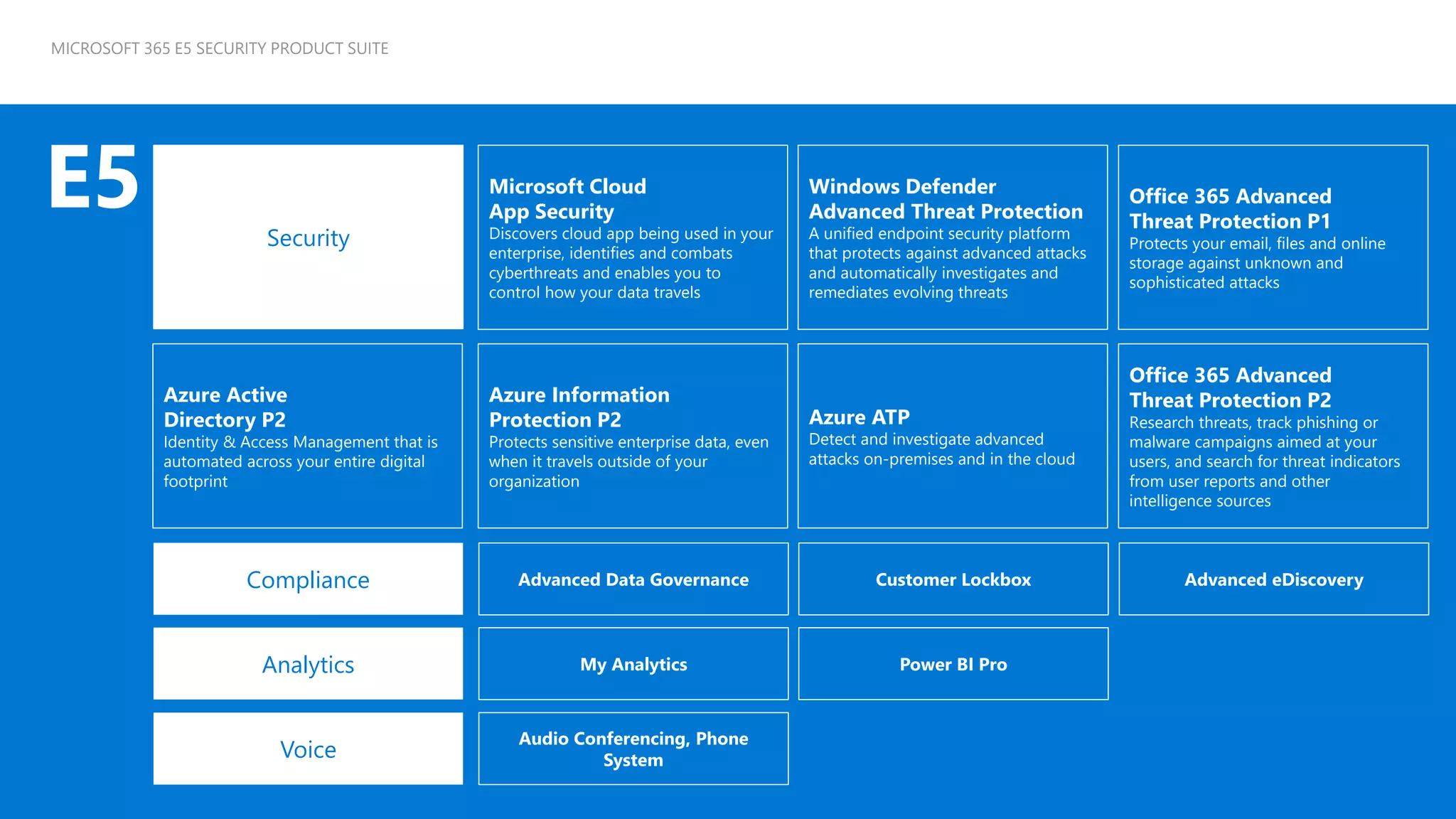
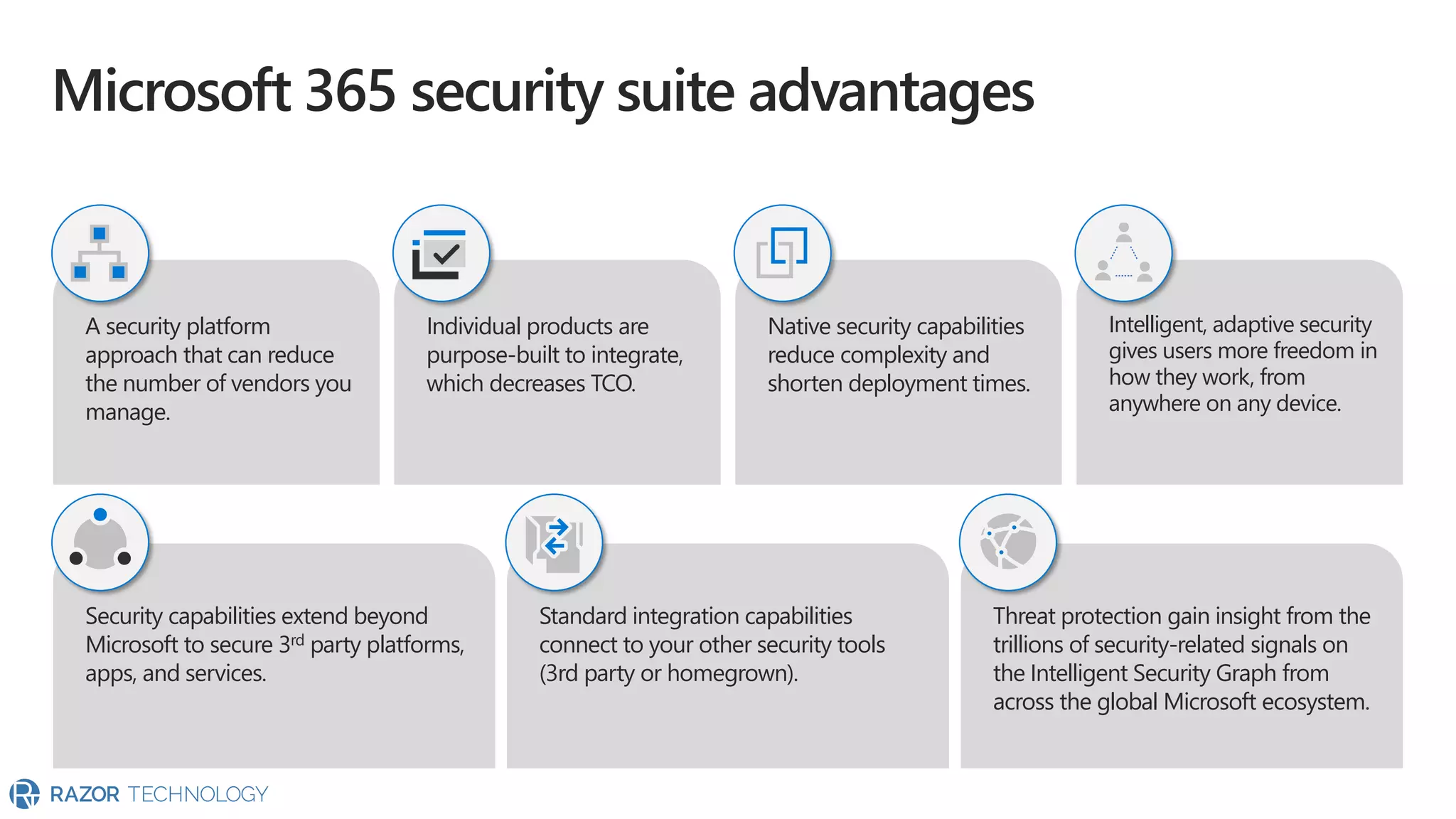
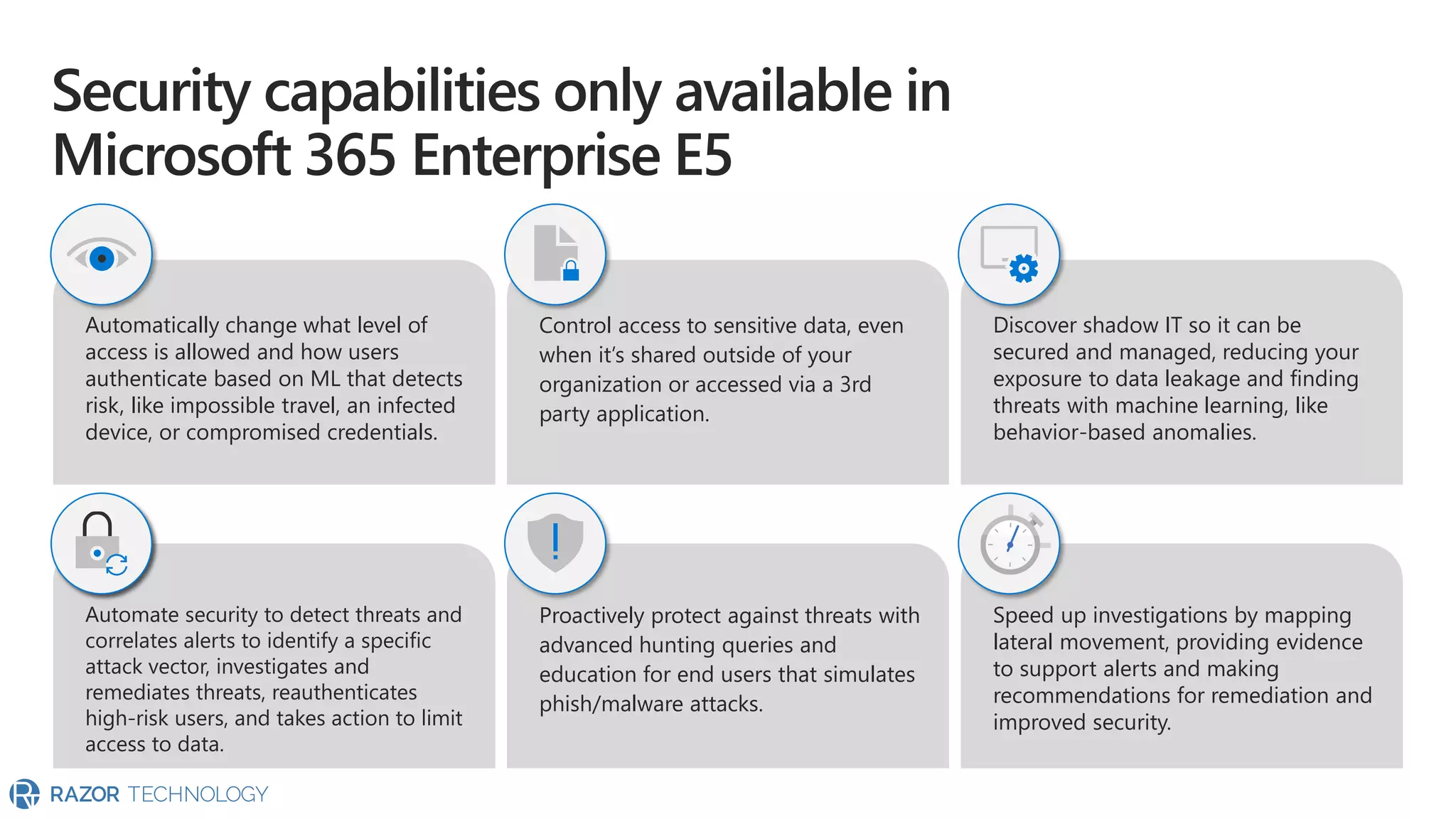
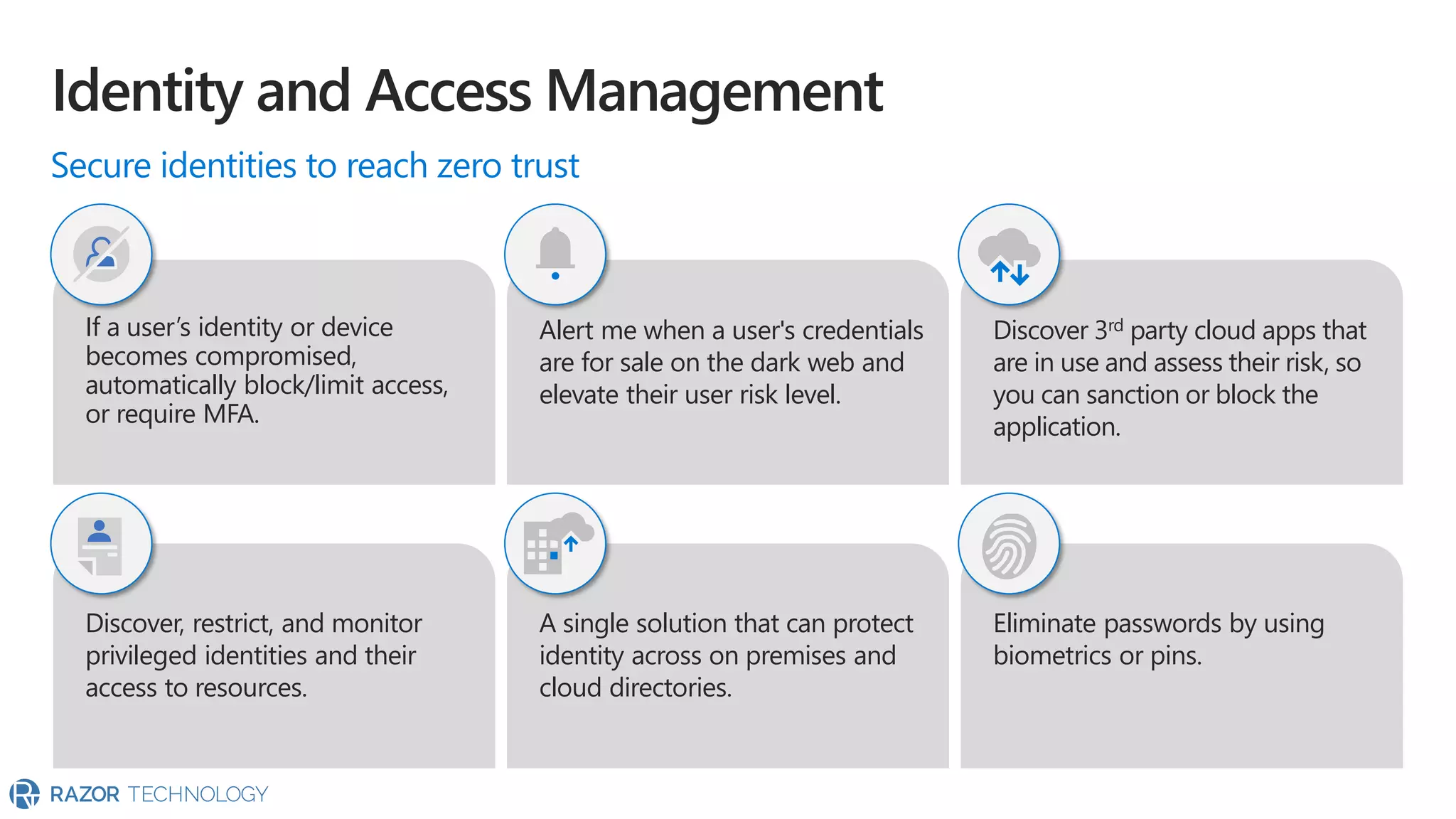
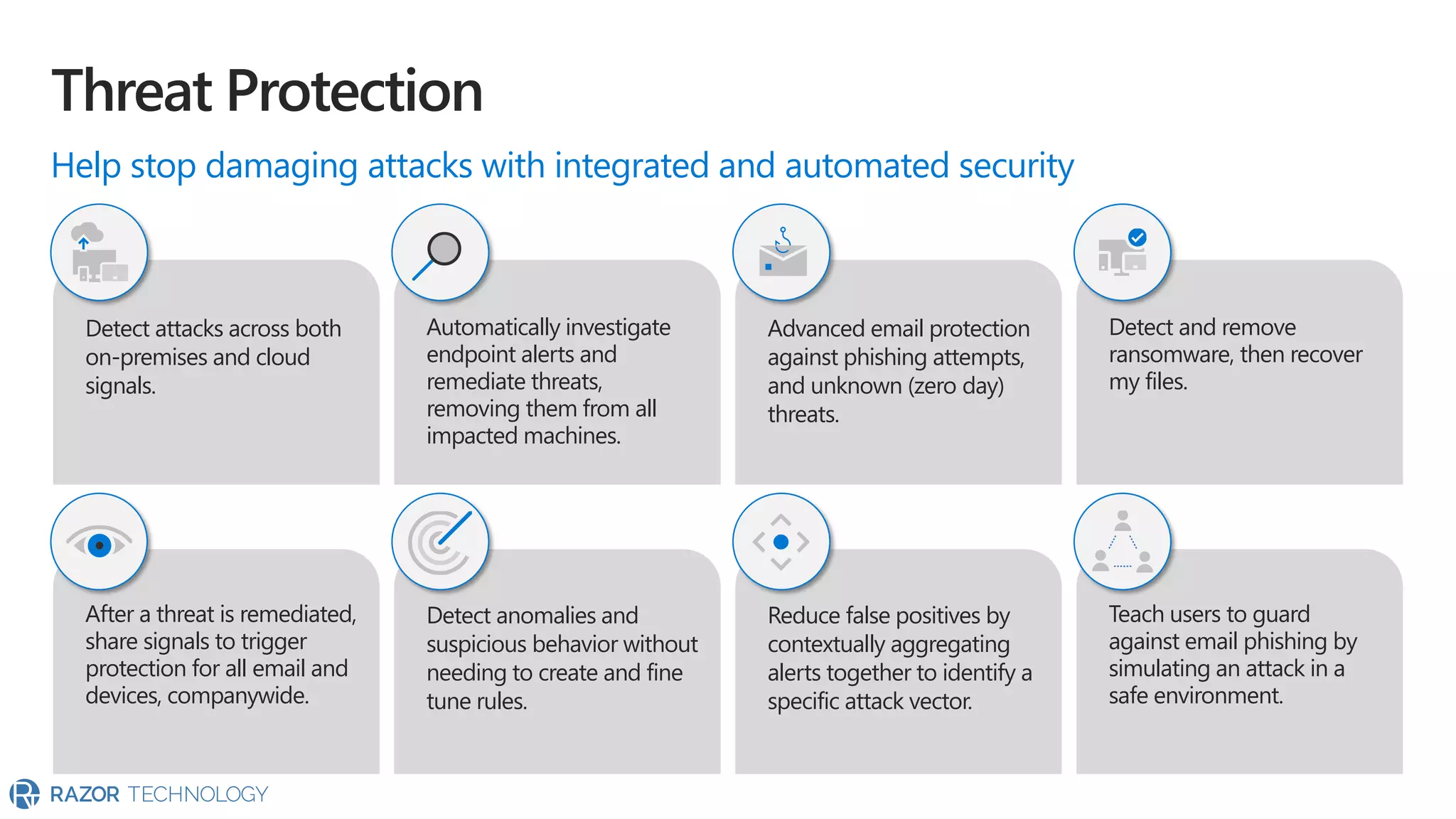
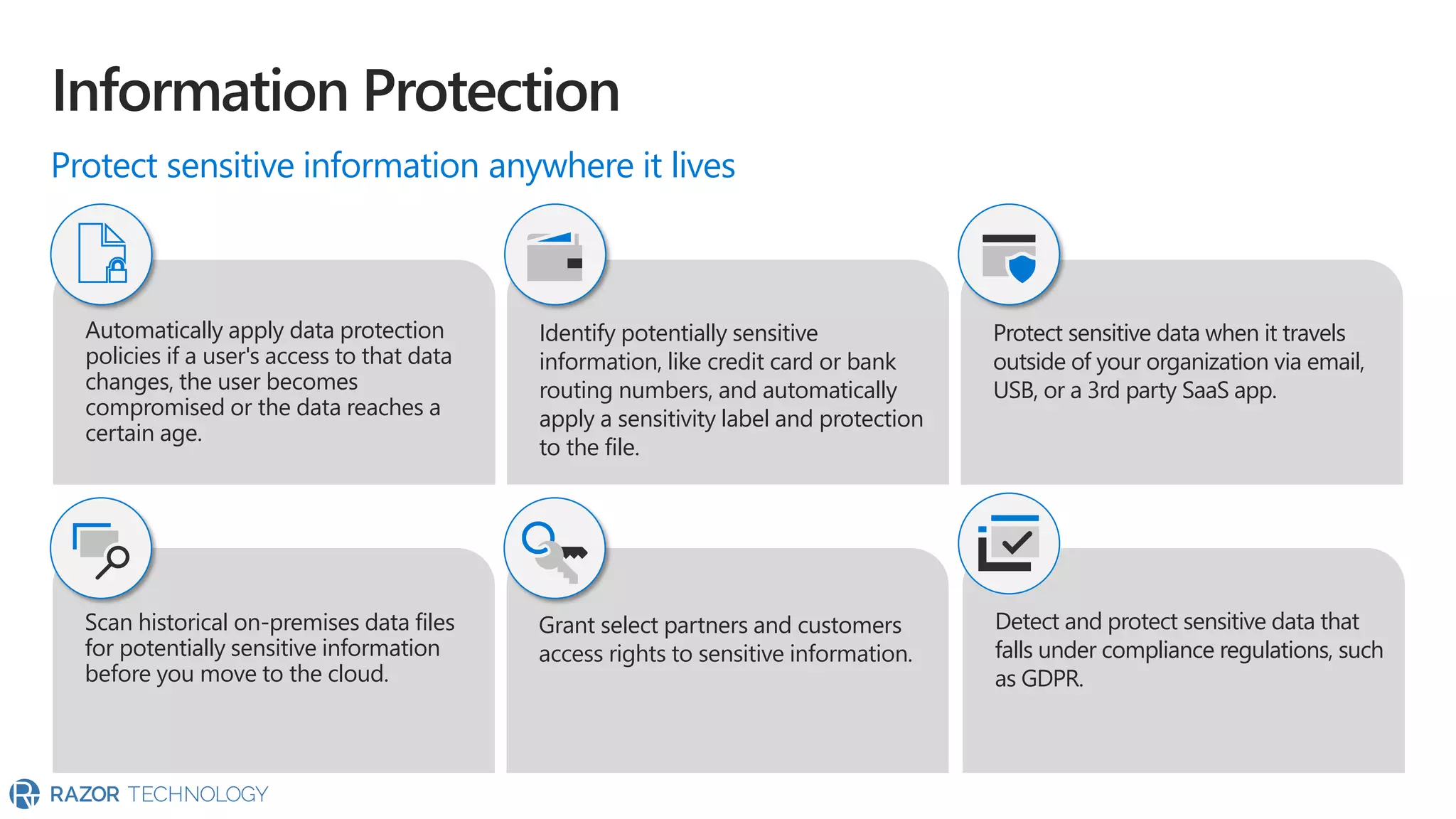
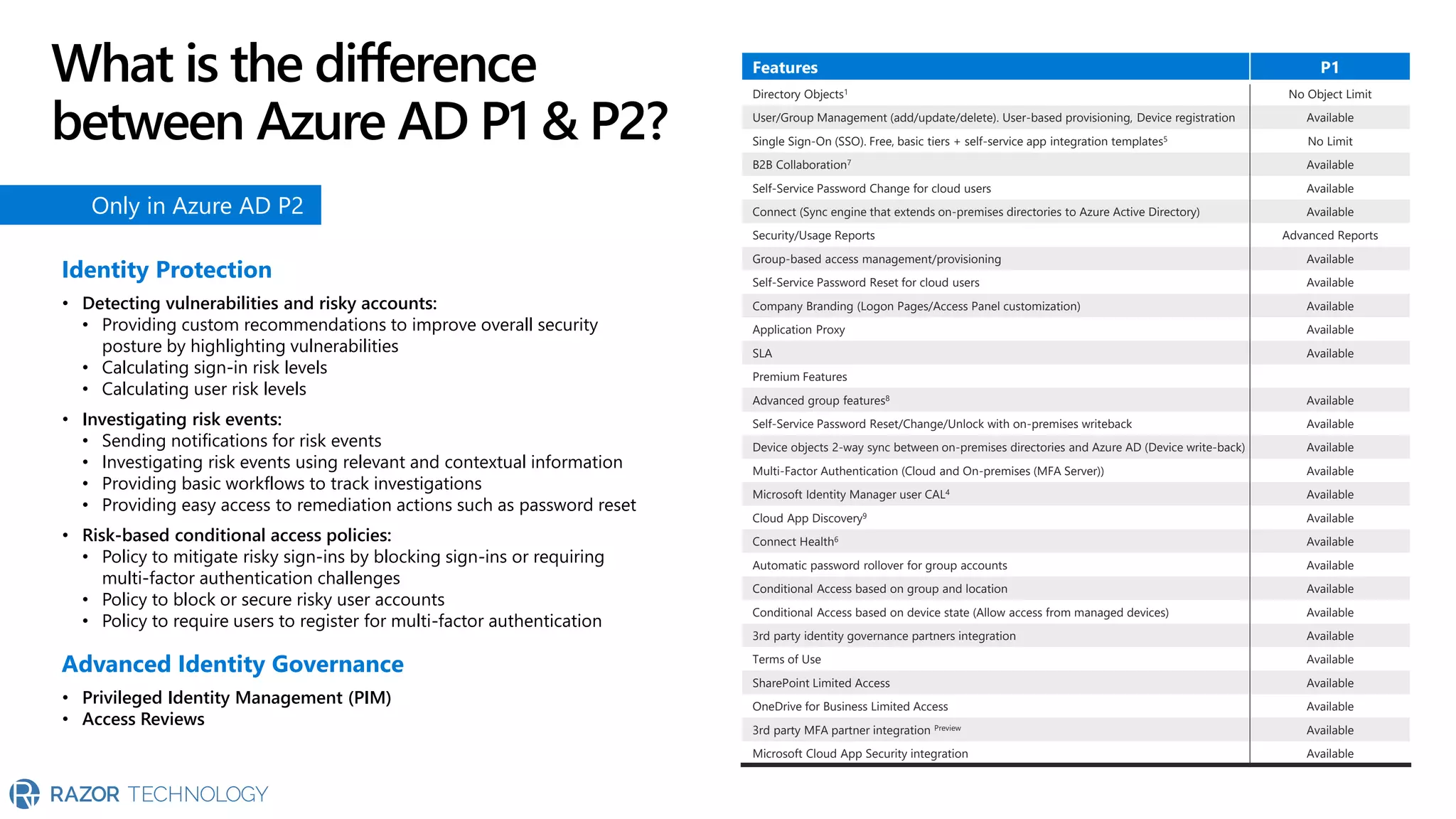
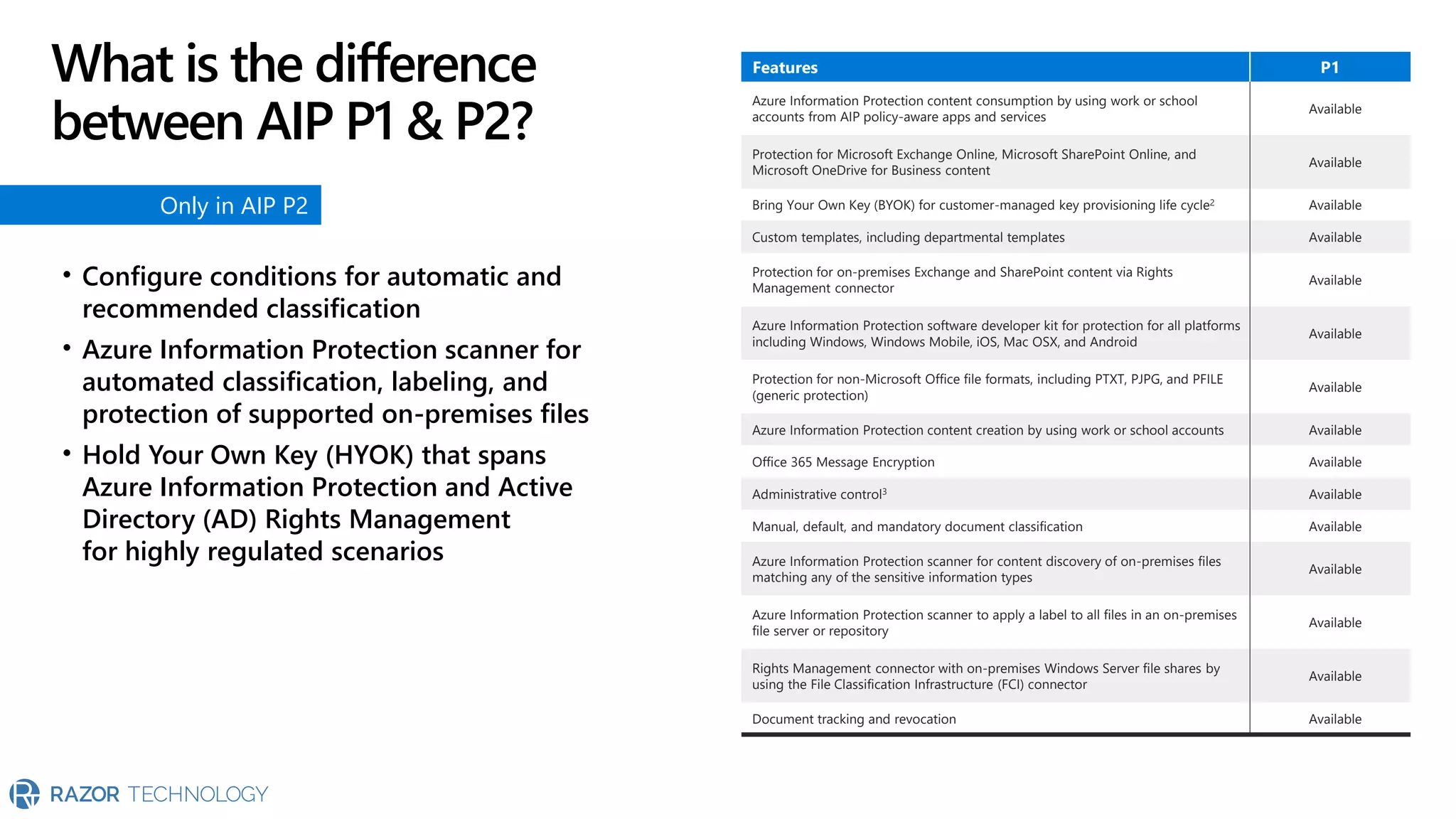
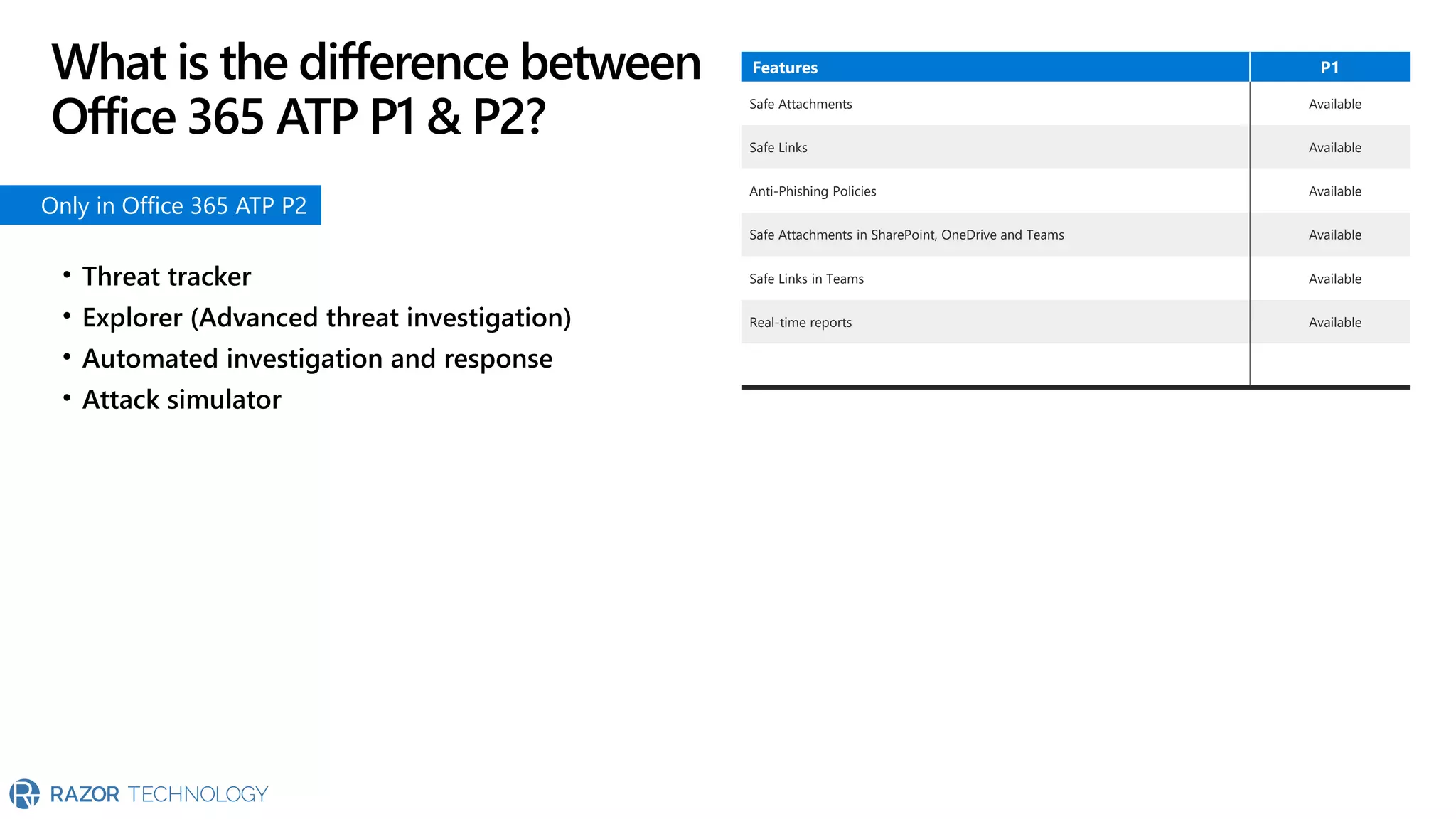
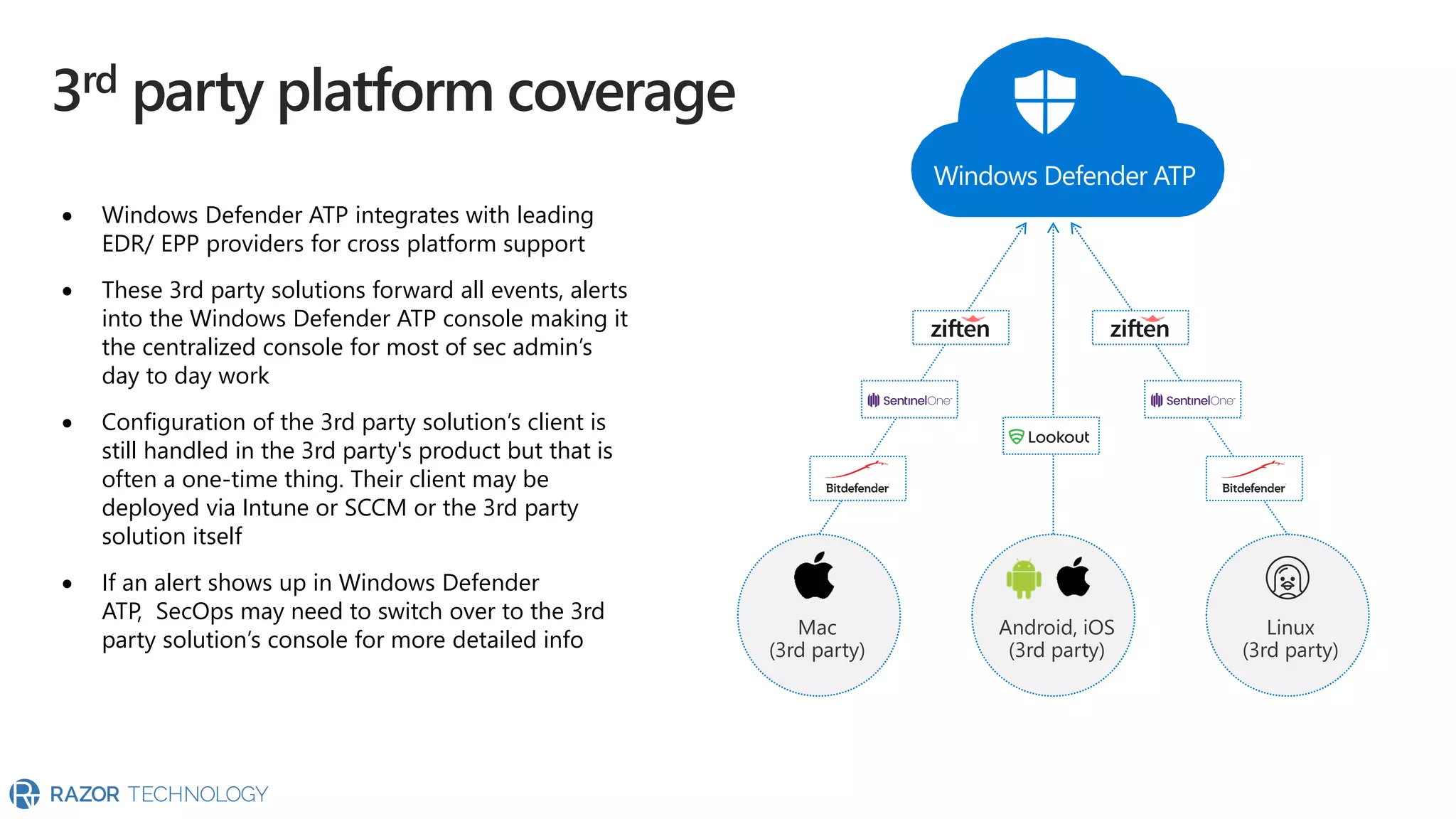
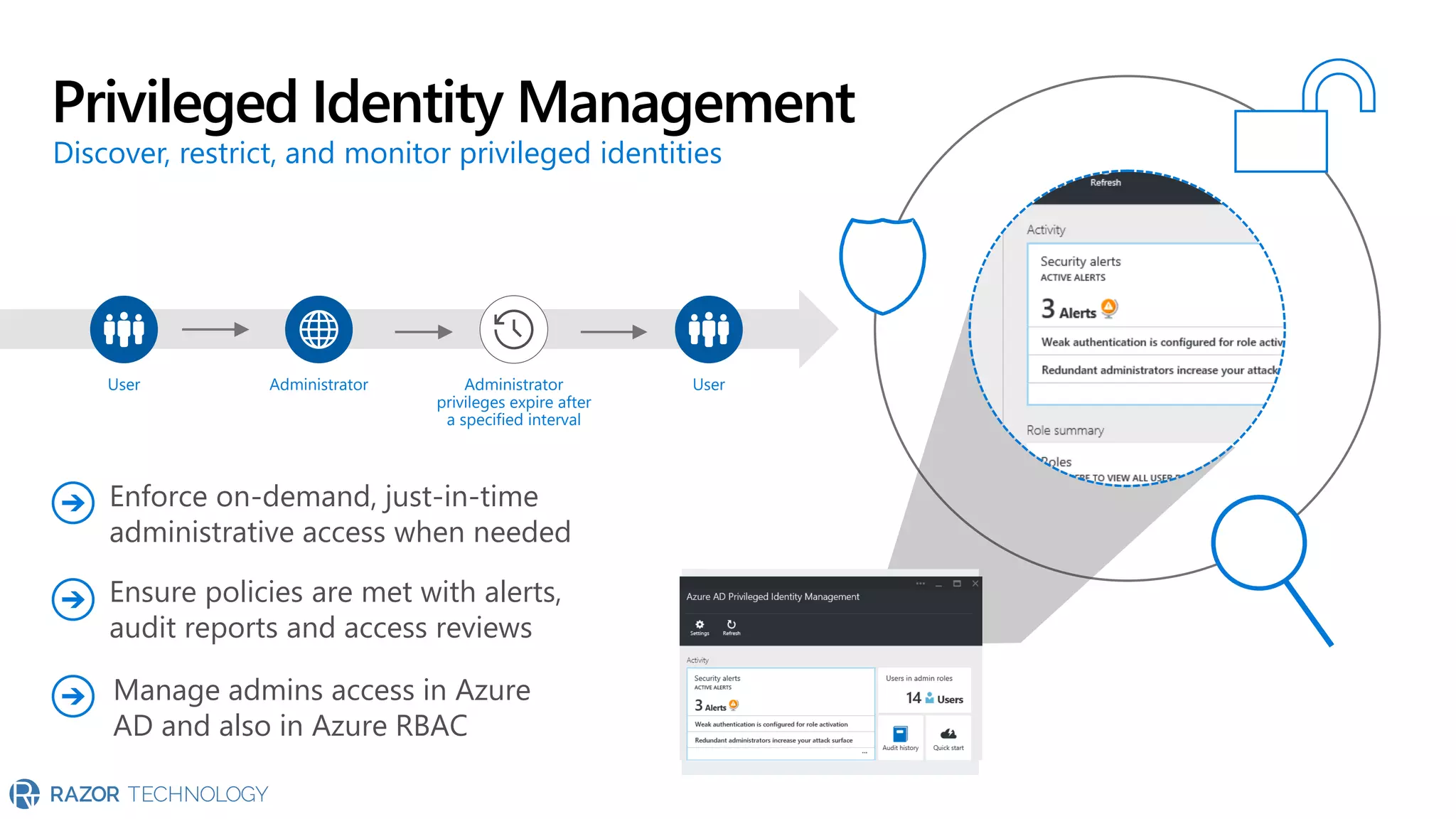
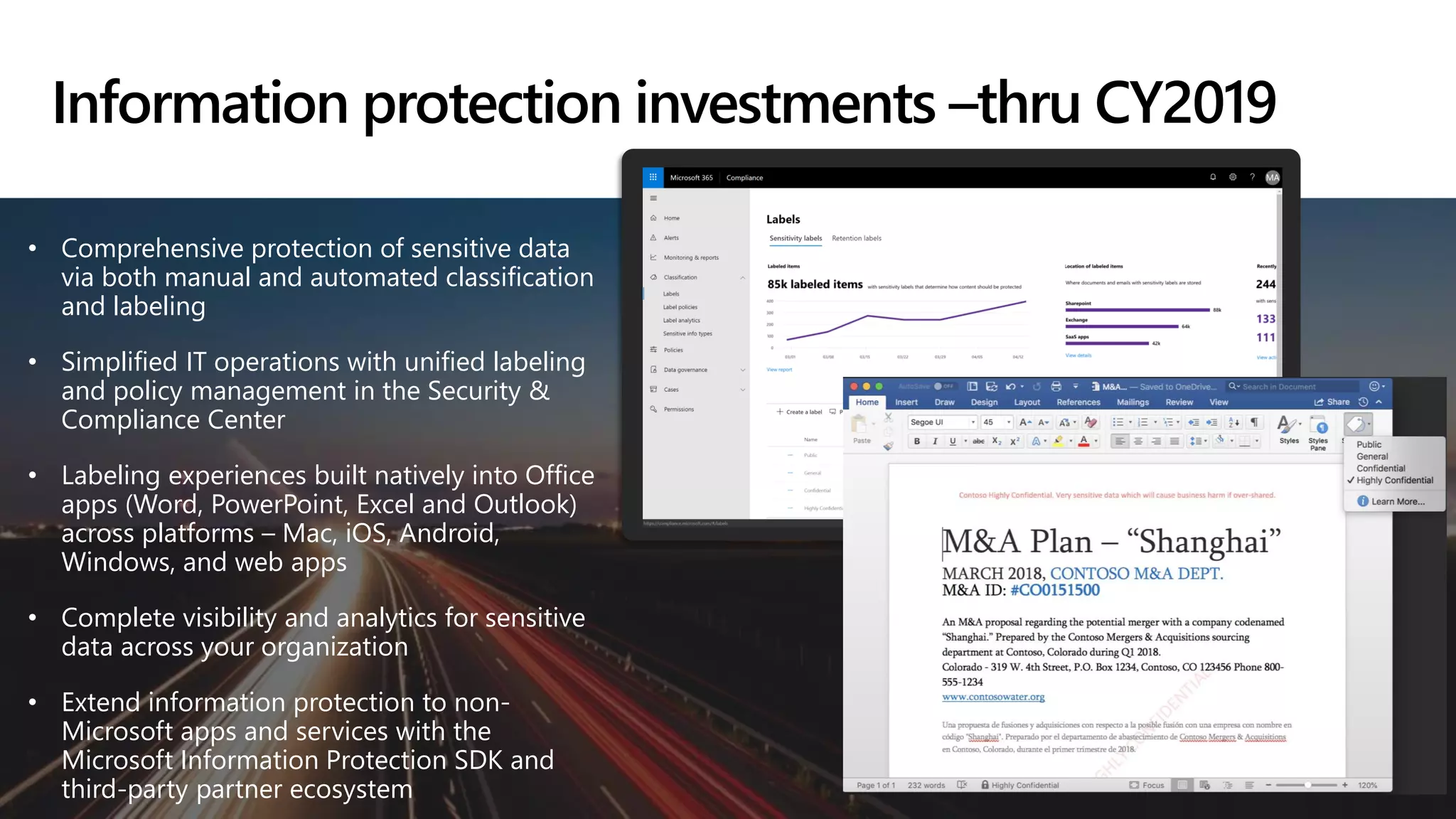
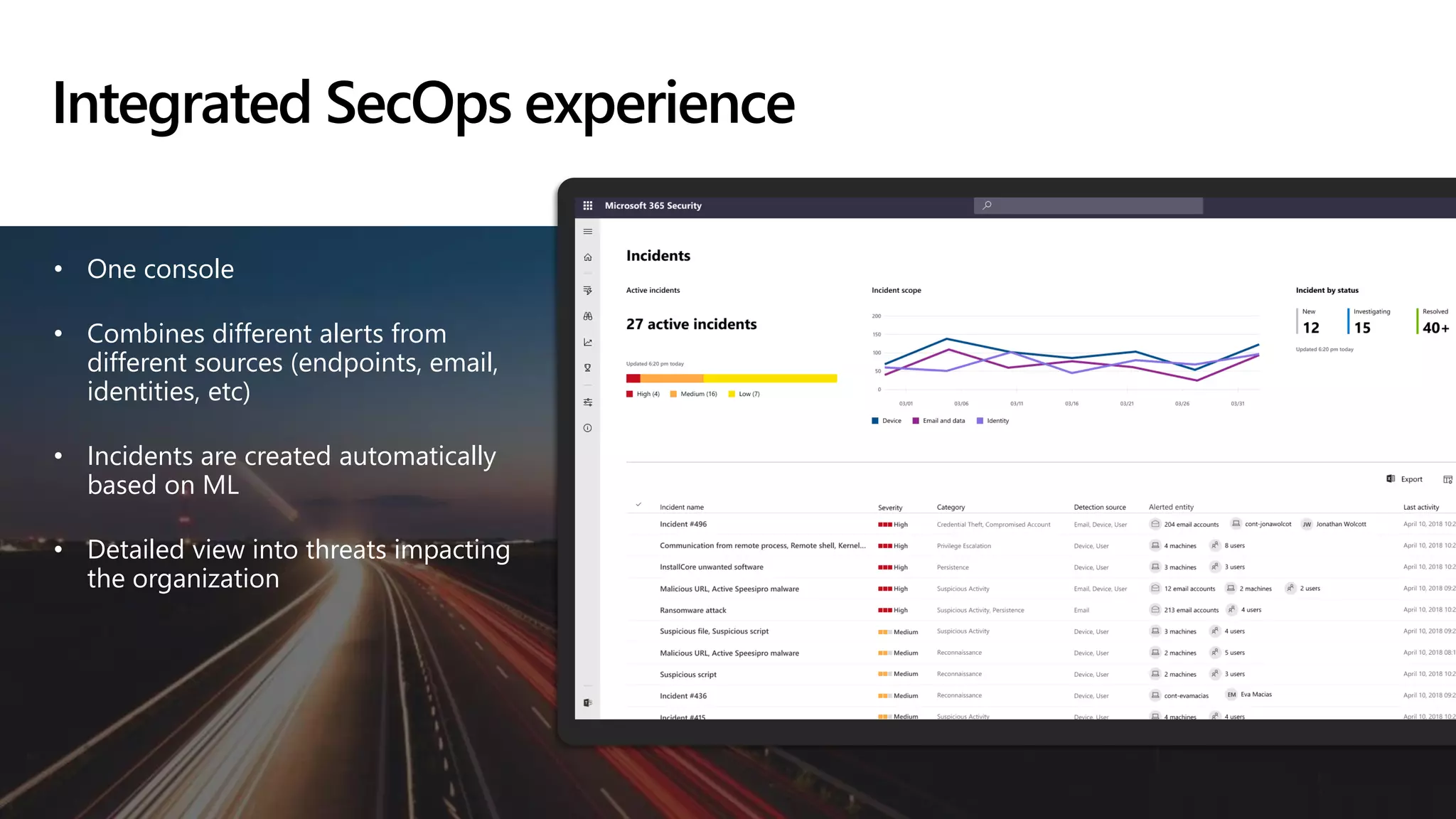
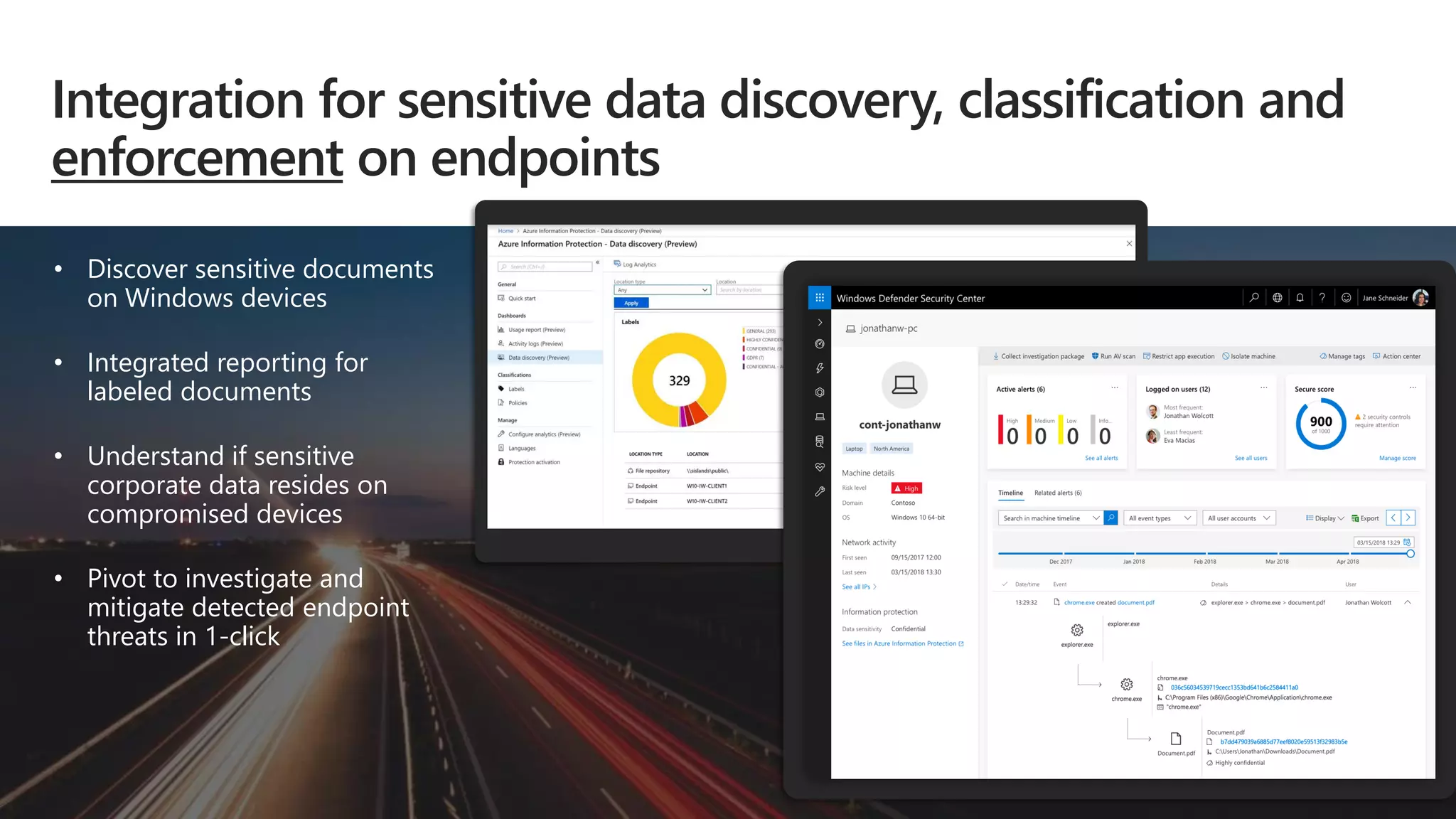
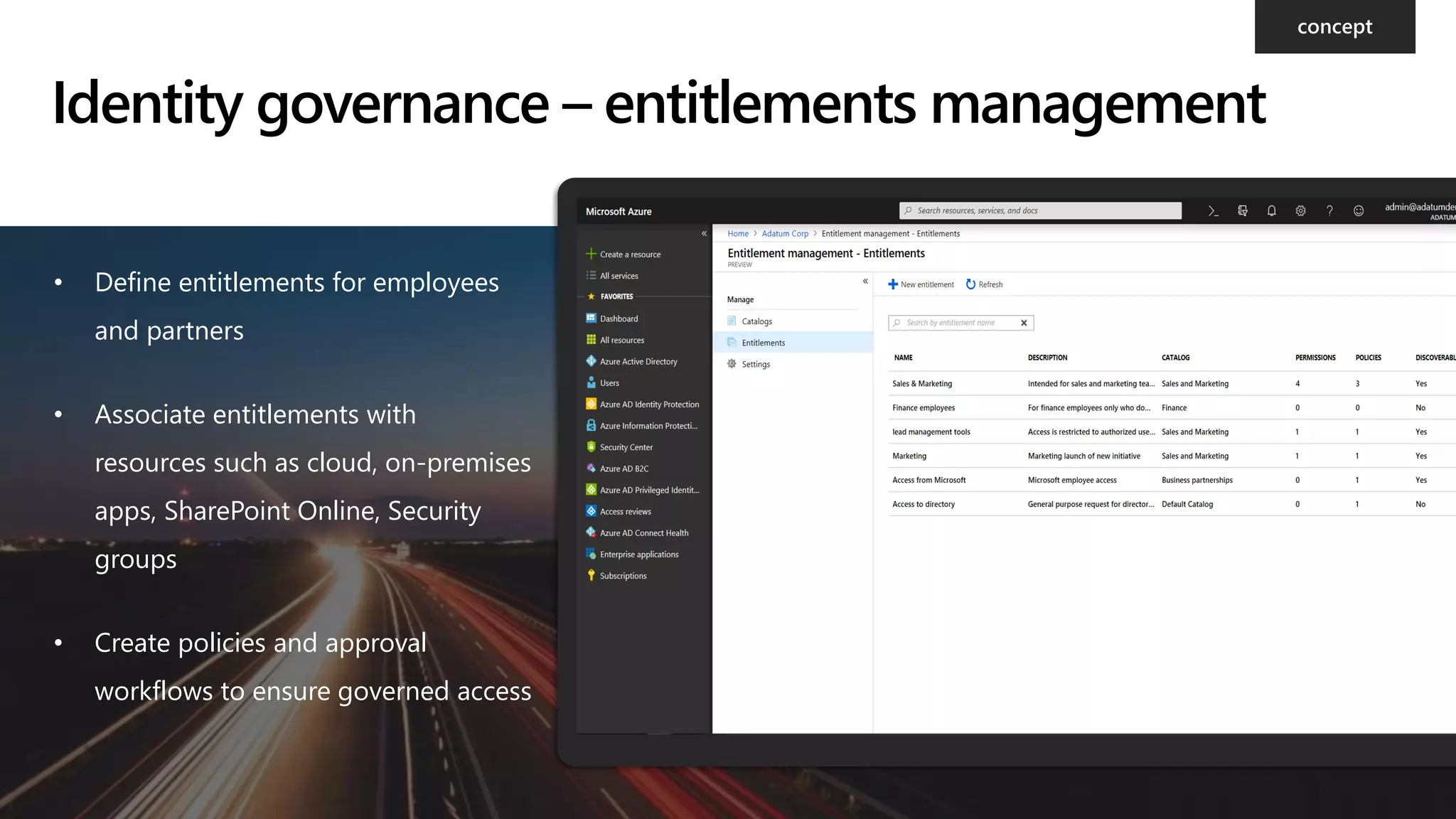
The document provides an overview of Microsoft 365 Enterprise E5's security features which aim to simplify security management against rising cyber threats. It emphasizes the integration of native security capabilities, reduced complexity, and improved visibility for organizations, enabling efficient threat protection and data governance. Key benefits include automated security responses, identity management, compliance facilitation, and holistic protection across the digital landscape.