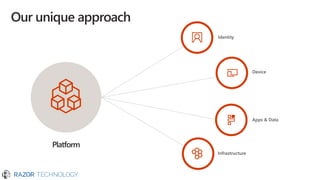
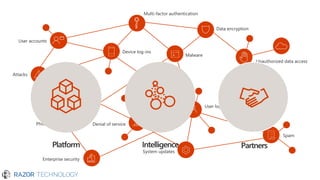
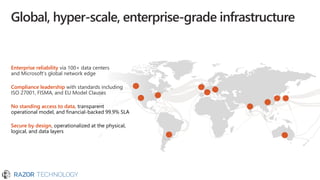
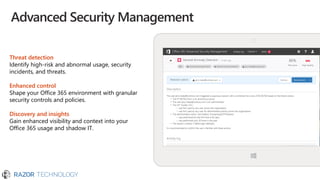
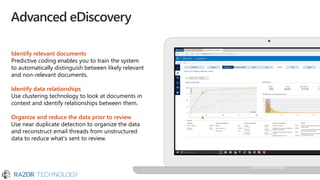
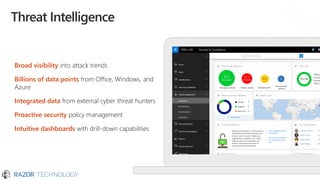
The document outlines Microsoft's commitment to security and data protection, emphasizing their enterprise security platform, compliance with various regulations, and the measures they take to safeguard customer data. It details the challenges faced by organizations, such as data breaches and inadequate data governance, and describes Microsoft's extensive security features, including threat intelligence and advanced data governance. Microsoft advocates for data privacy, ensures customer data ownership, and follows strict protocols for accessing and managing customer data, particularly in light of global regulations like GDPR.