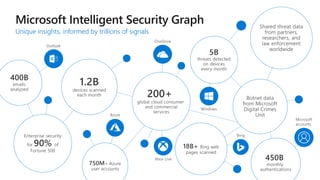
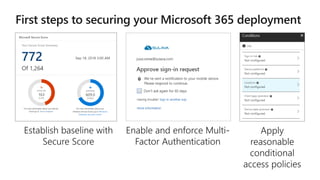
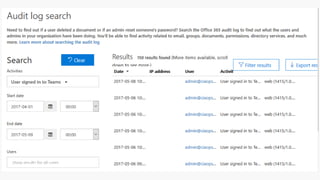
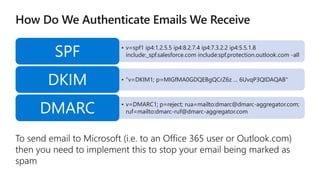
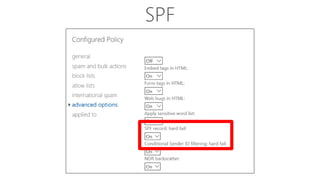
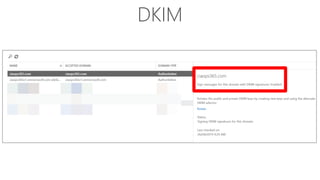
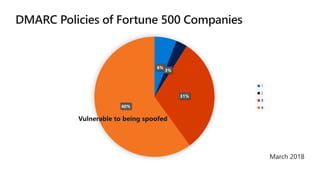
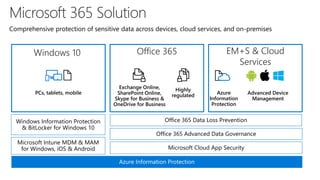
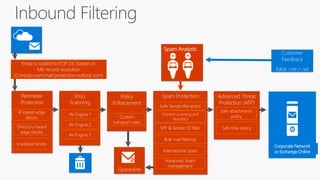
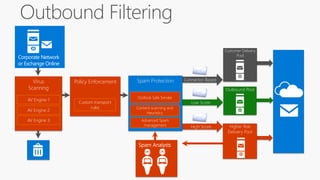
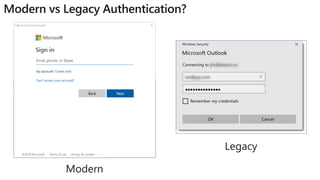
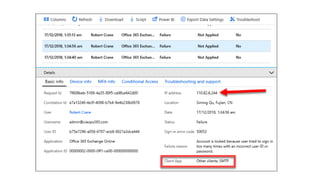
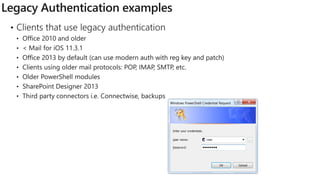
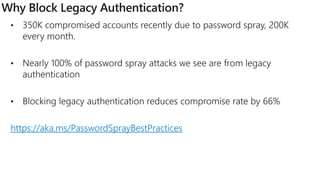
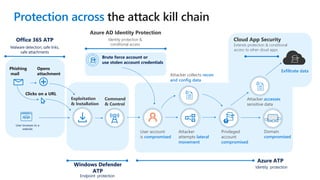
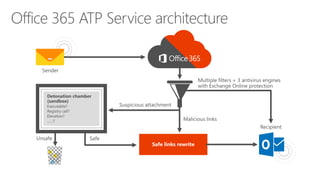
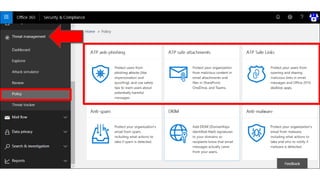
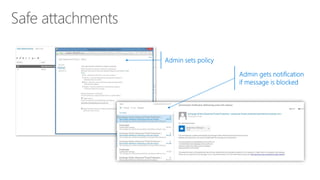
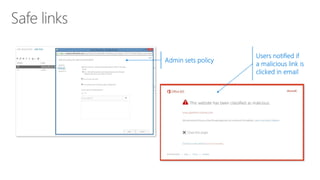
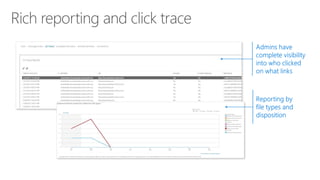
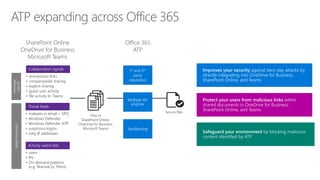
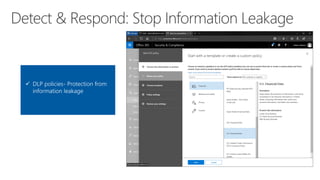
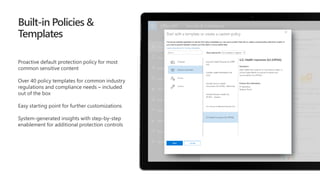
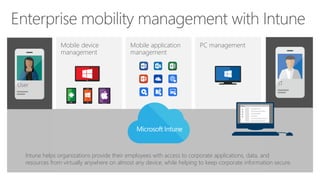
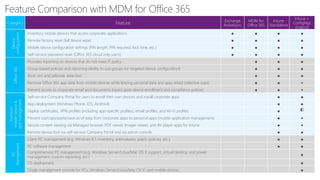
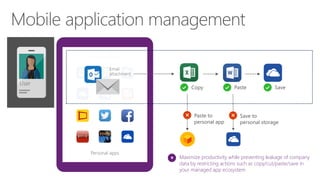
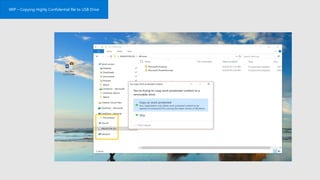
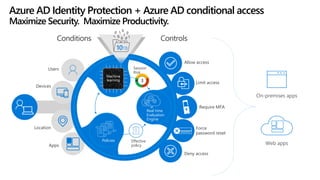
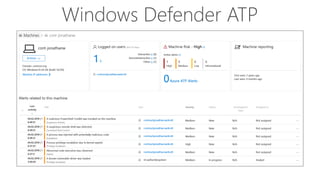
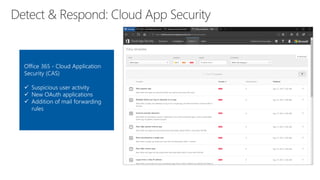
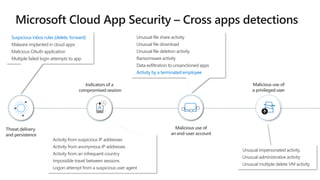
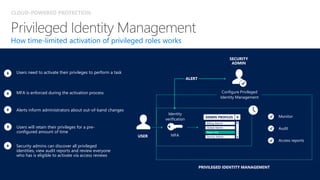
The document discusses security challenges for businesses and how Microsoft 365 solutions provide defense in depth across devices, apps, and identity. It highlights growing threats like phishing, password spraying, and account takeovers. Microsoft uses intelligence from trillions of signals to detect anomalies and threats. The solutions incorporate multi-factor authentication, conditional access policies, advanced threat protection, information protection, and more to help secure organizations.