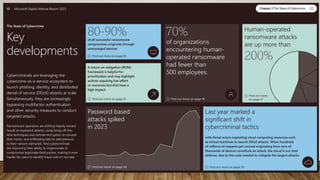
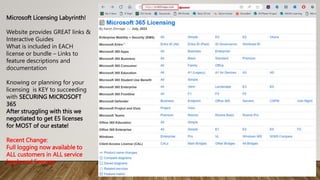
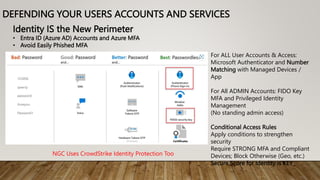
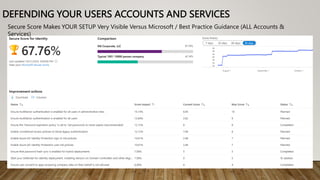
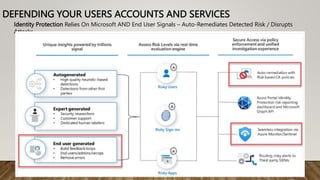
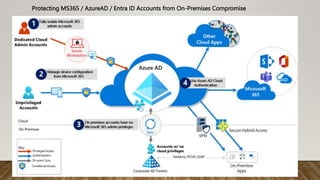
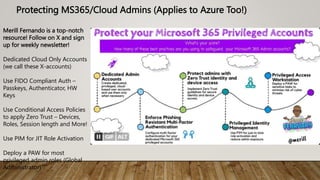
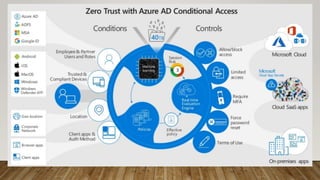
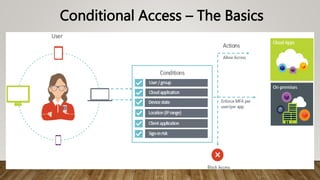
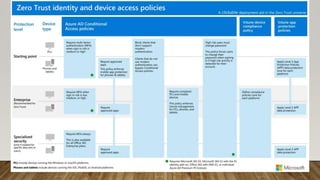
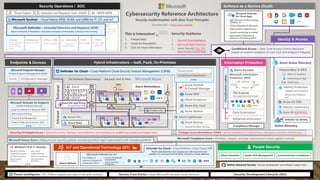
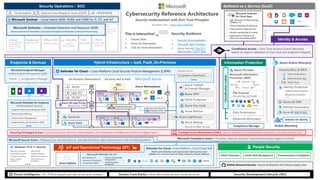
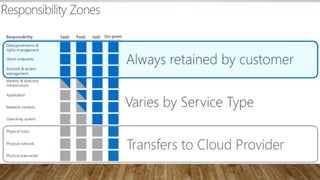
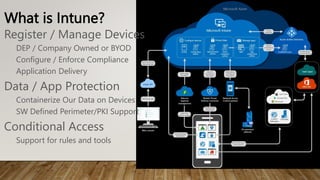
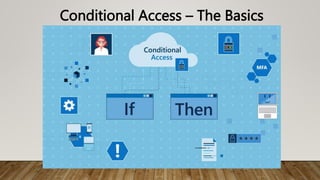
The document provides guidance on securing Microsoft 365 services through tools like Conditional Access policies and Zero Trust concepts. It recommends emphasizing identity security using Azure AD, enforcing multi-factor authentication, and applying Conditional Access rules. The document also provides references to security advisors and resources like books, blogs, and Twitter accounts that provide best practices for securing Microsoft 365.