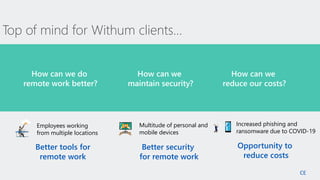
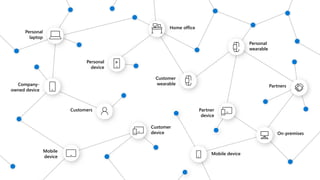
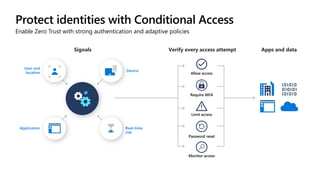
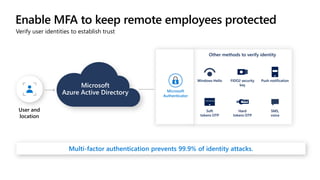
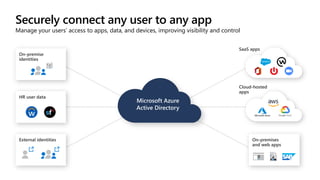
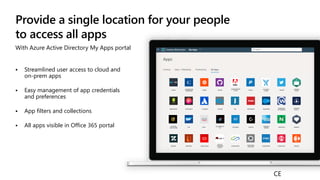
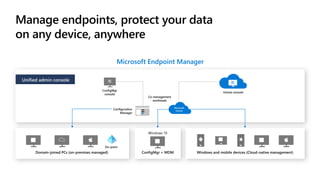
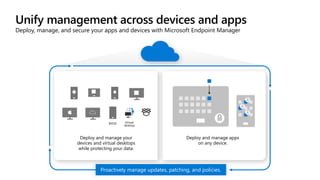
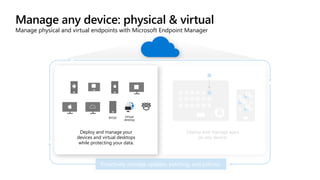
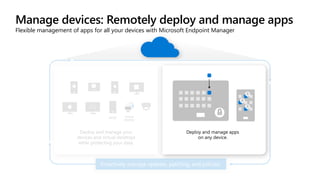
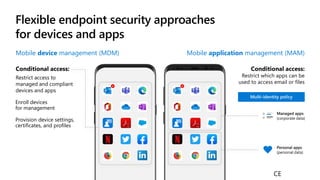
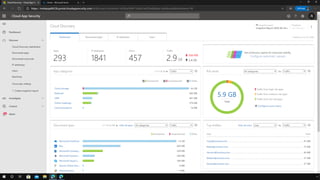
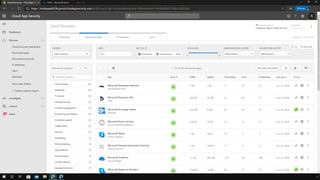
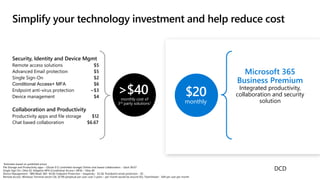
The document outlines a webinar on securing a remote workforce using Microsoft Cloud technologies, focusing on identity security, device management, and application security. It features experts discussing strategies to enhance remote work security while optimizing costs and improving productivity. Key topics include multi-factor authentication, conditional access, and Microsoft Endpoint Manager for device management.