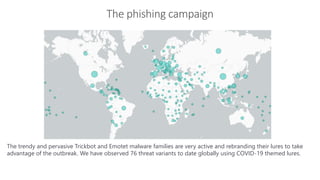
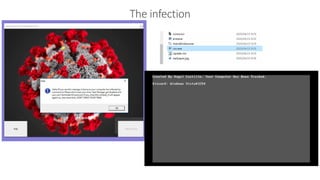
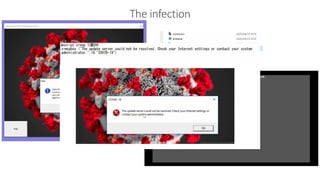
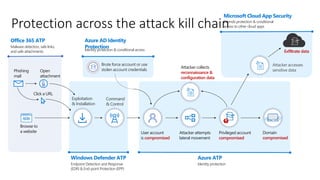
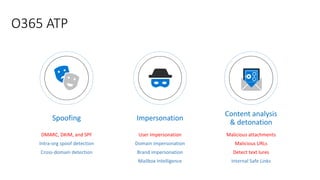
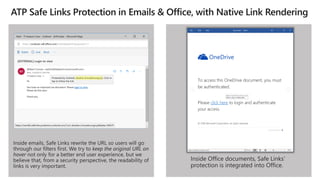
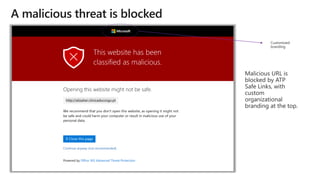
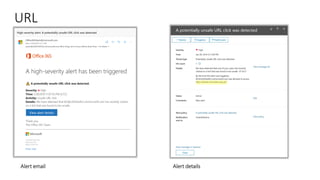
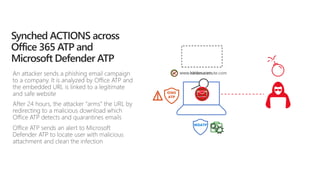
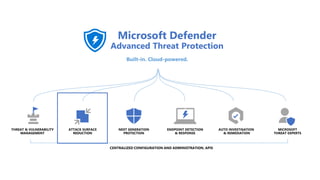
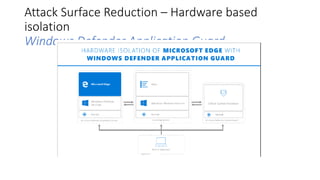
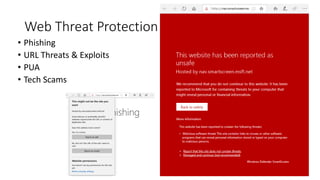
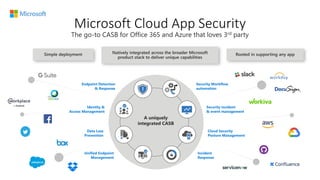
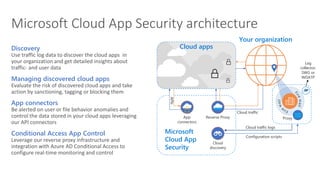
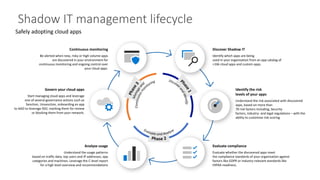
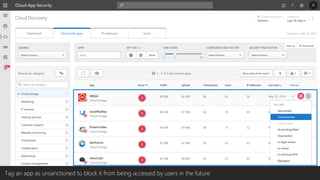
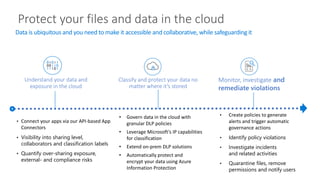
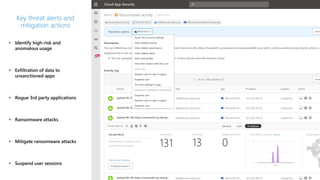
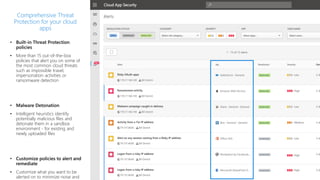
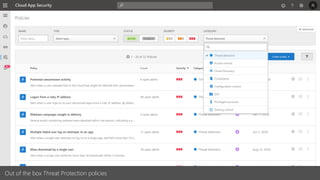
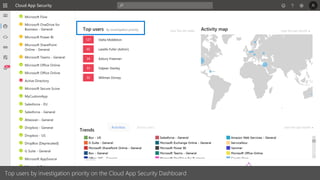
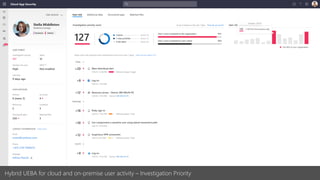
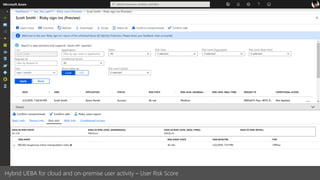
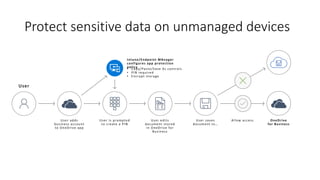
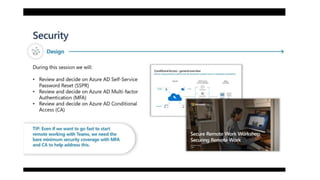
The document discusses best practices for securing remote work during the COVID-19 pandemic. It describes how cybercriminals are taking advantage of COVID-19 fears through phishing campaigns. It then provides tips on protecting infrastructure and identities, including enabling multi-factor authentication and conditional access. Finally, it summarizes a Secure Remote Work workshop that examines how to protect data and detect threats across cloud apps and devices.