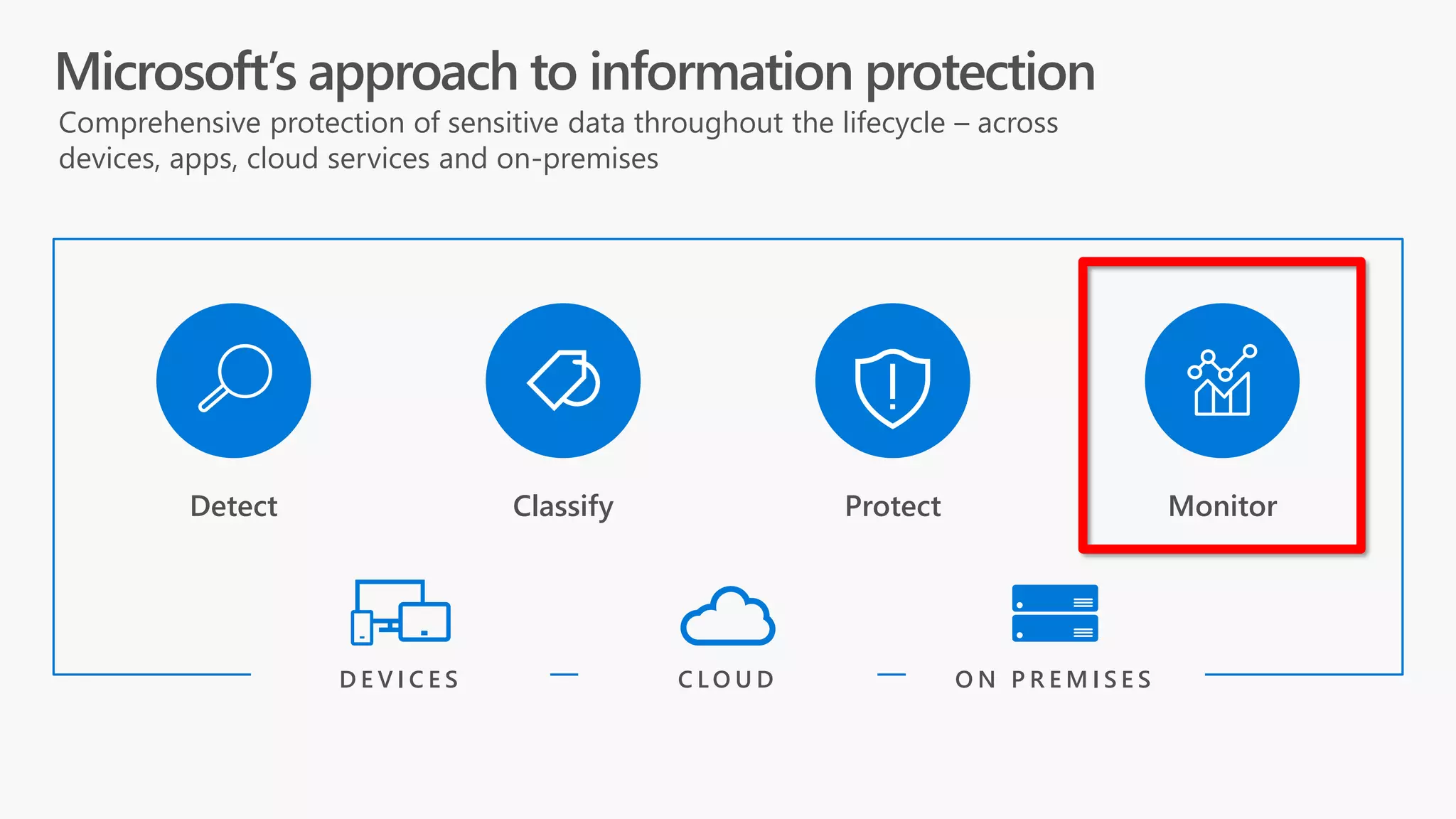
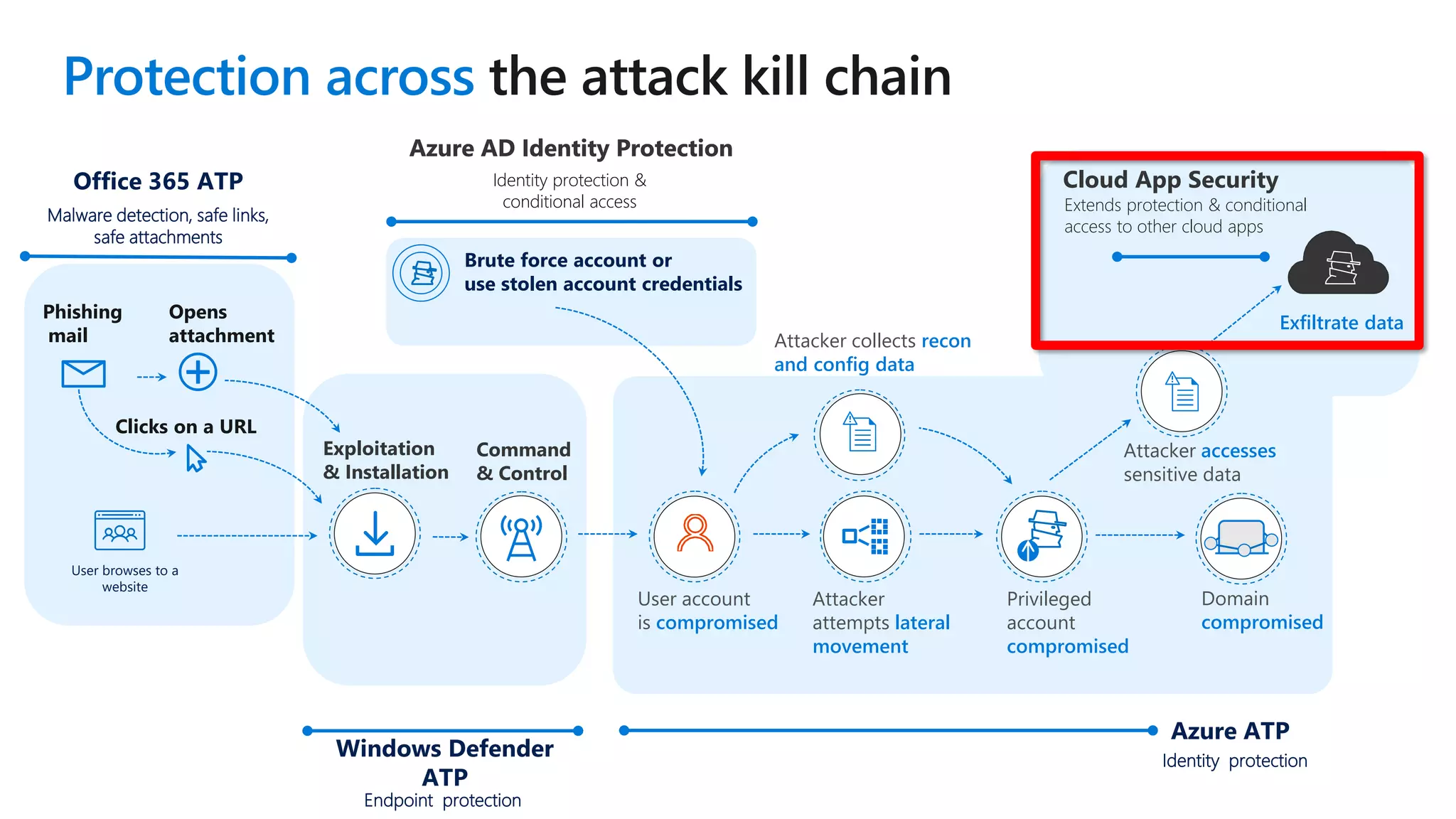
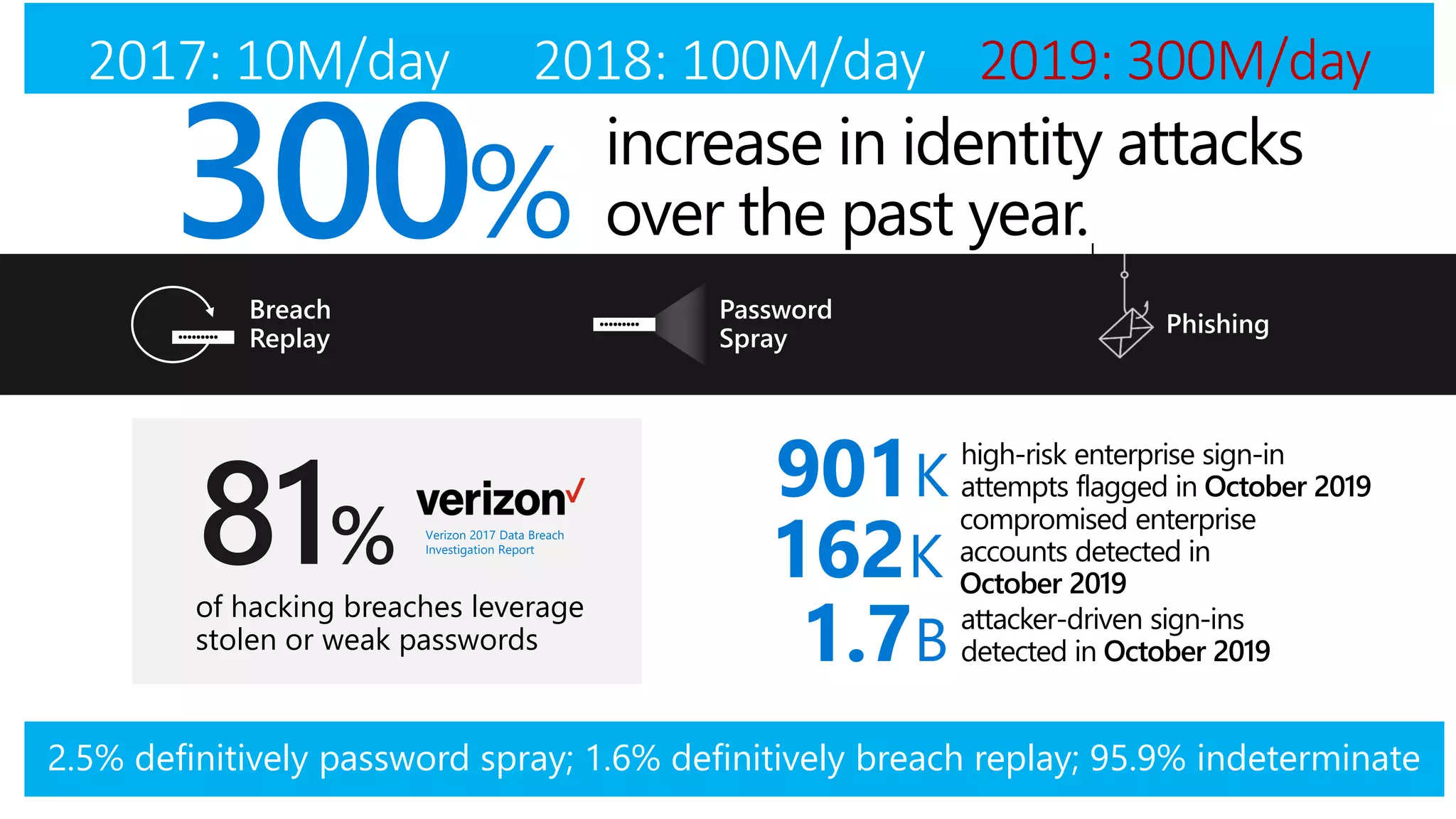
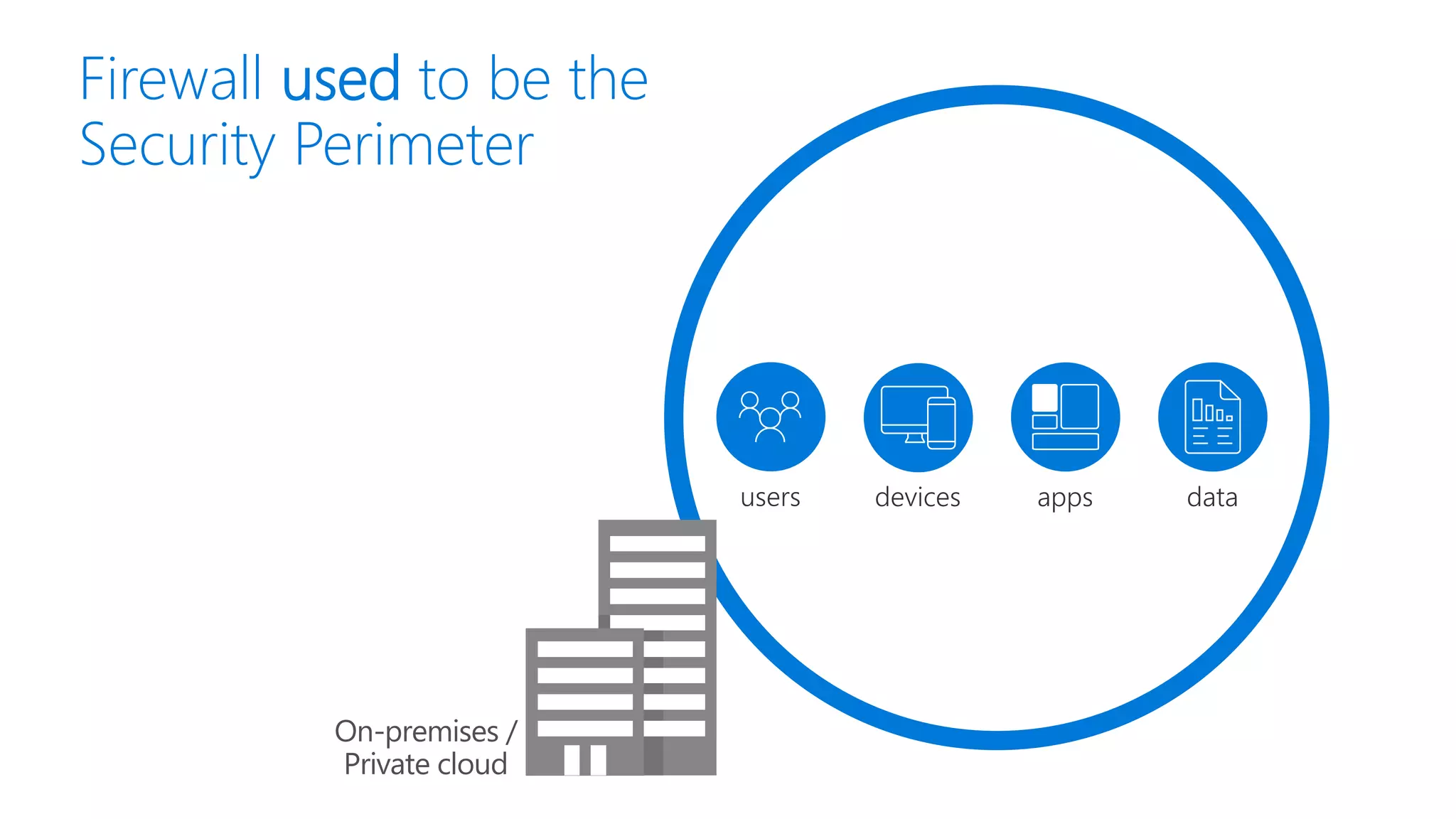
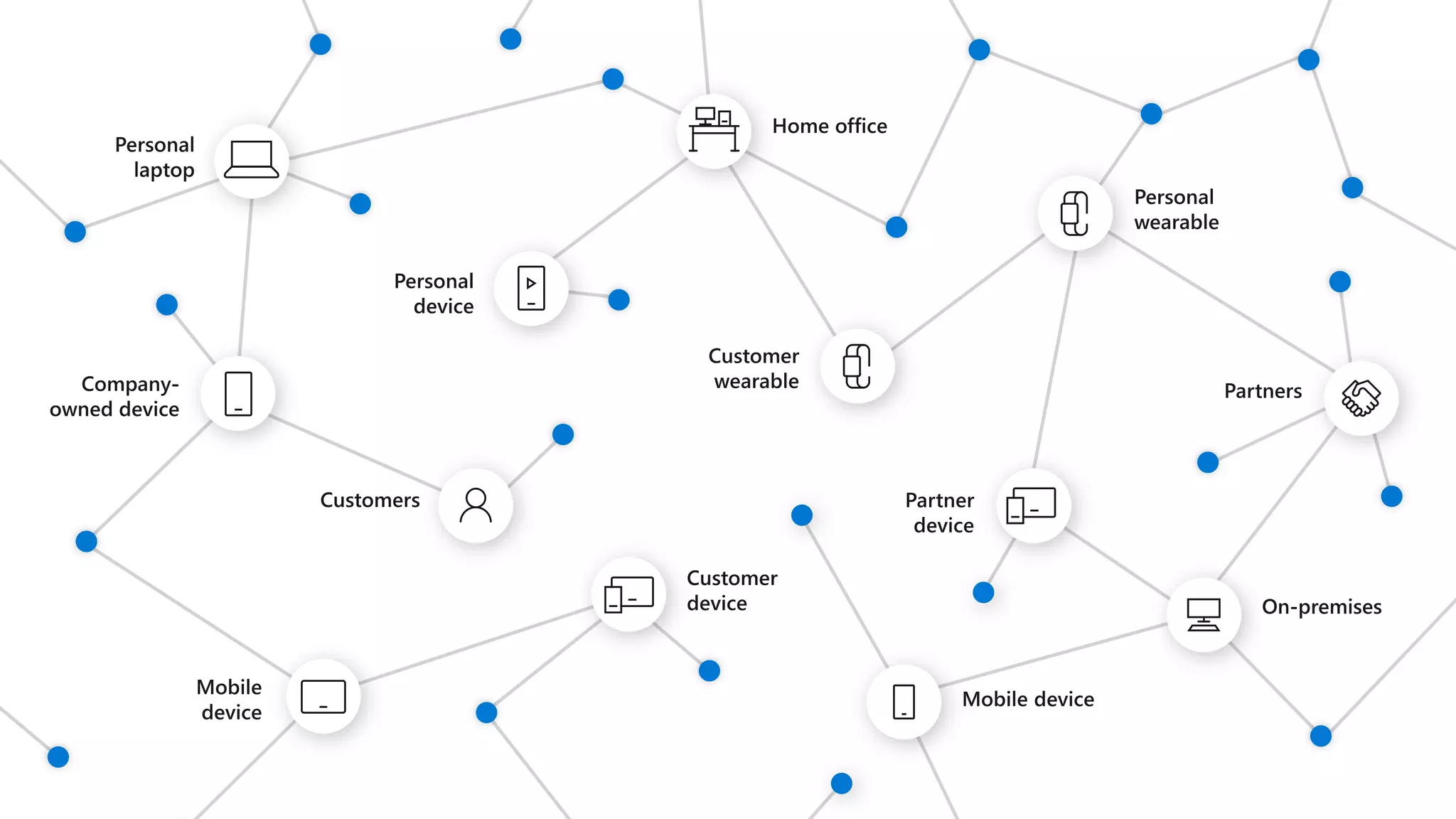
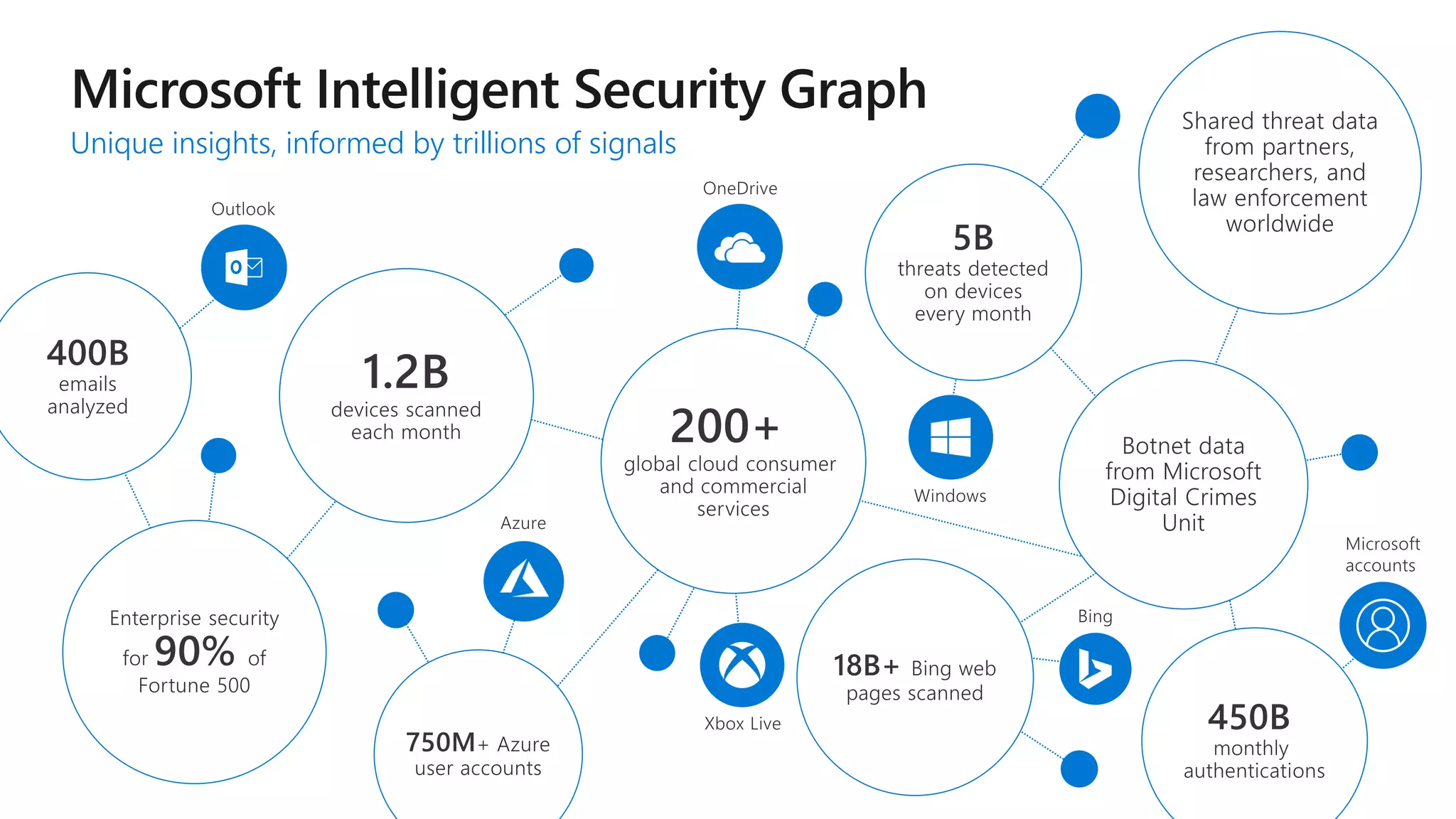
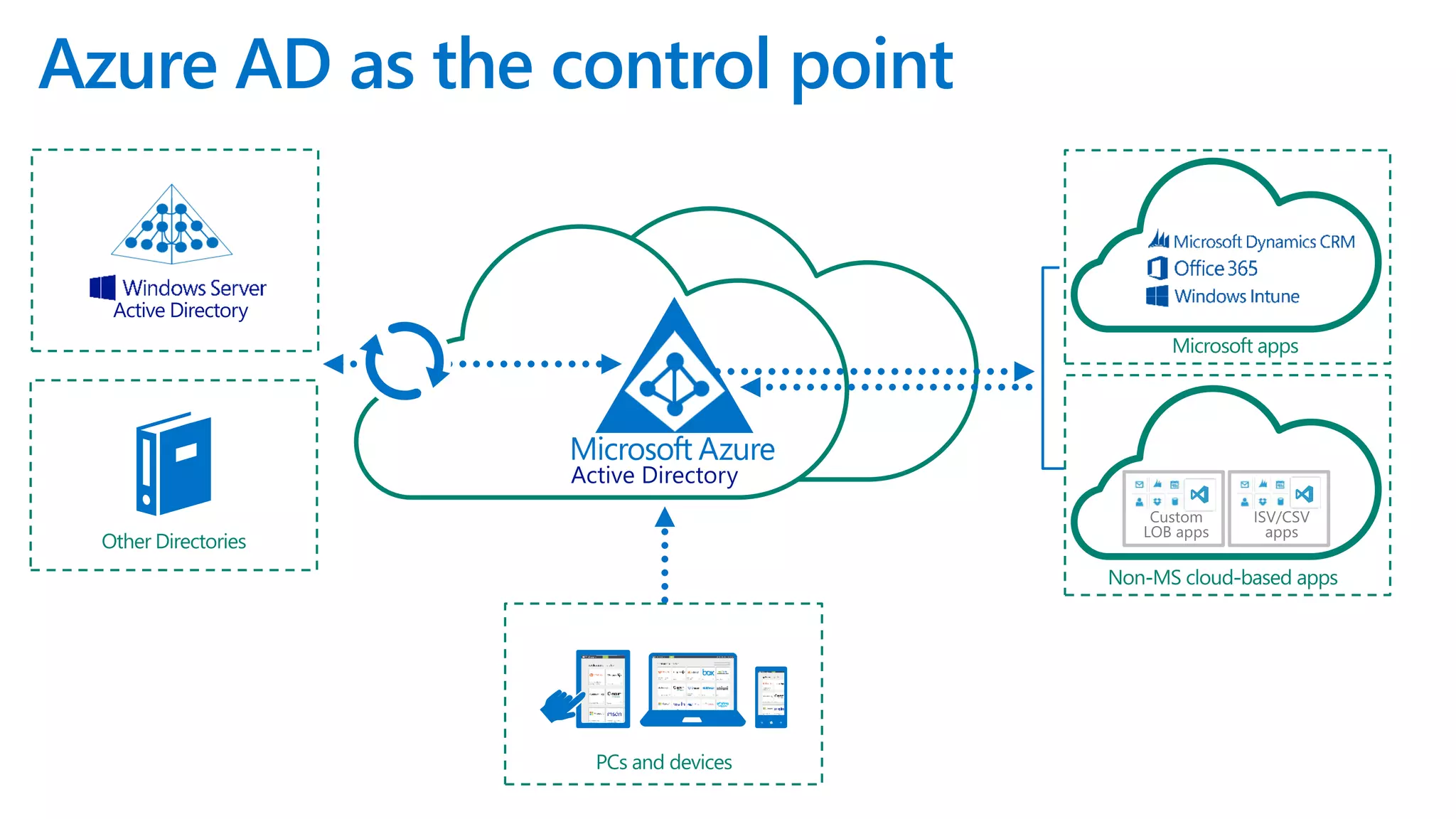
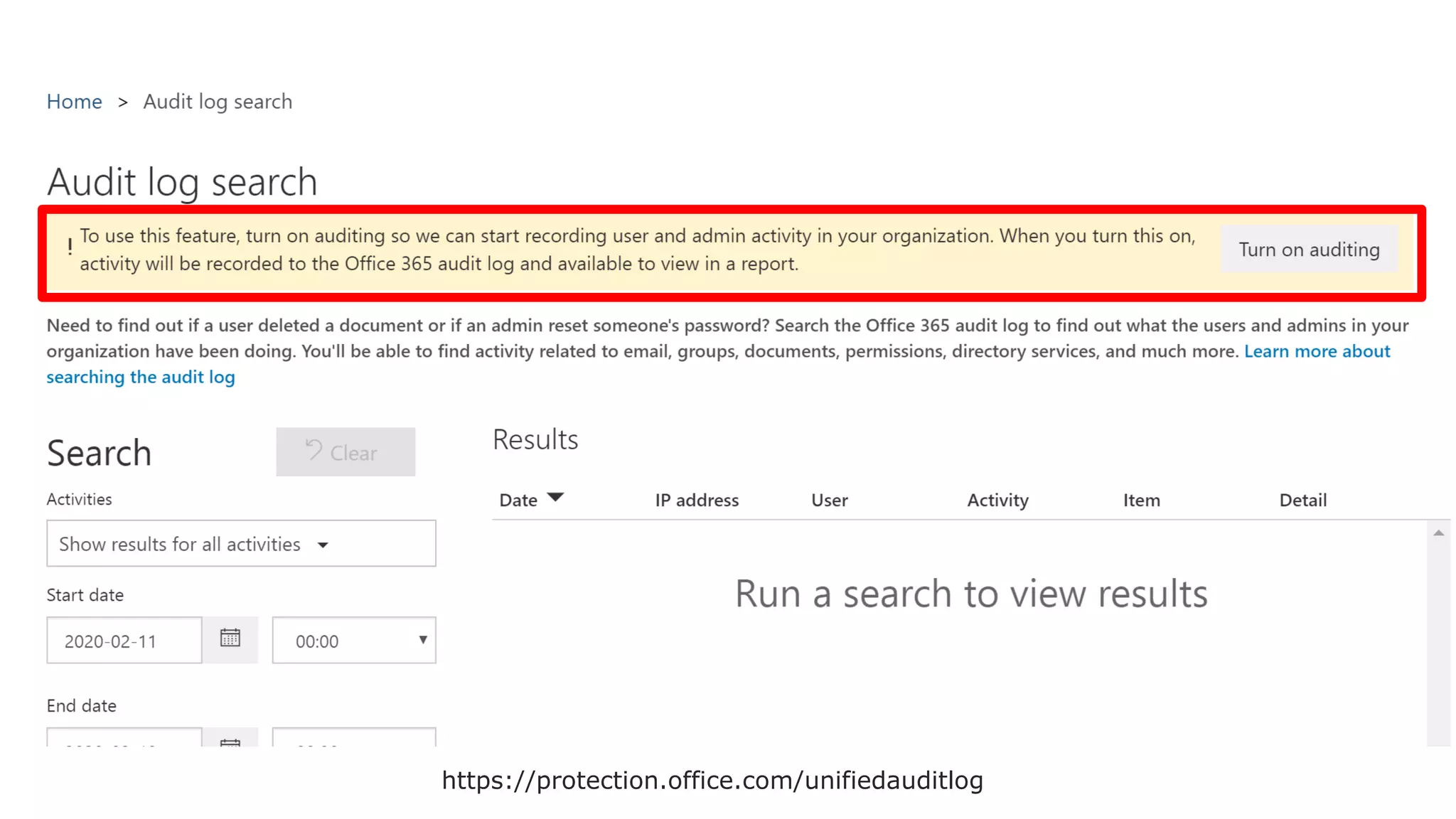
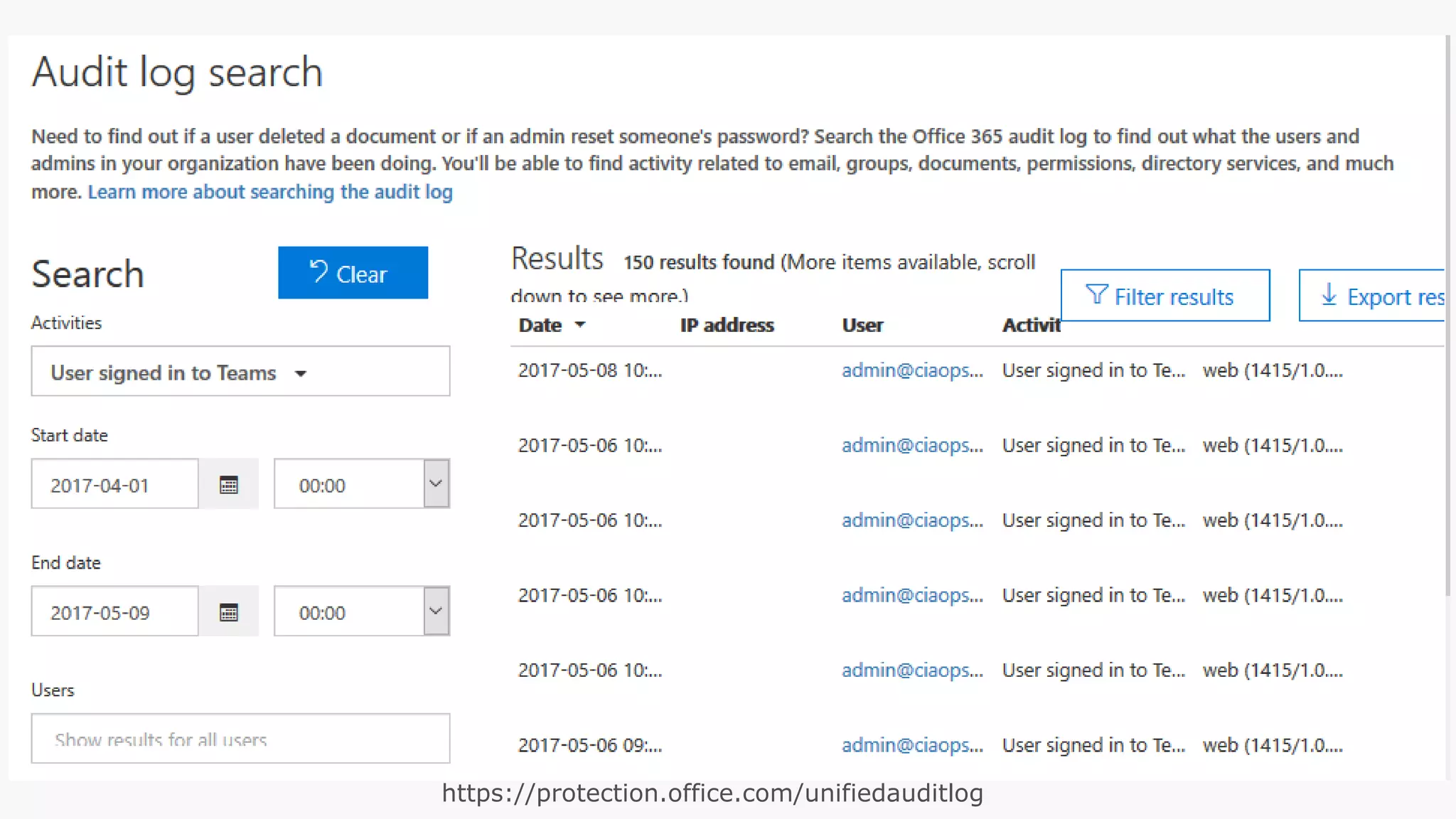
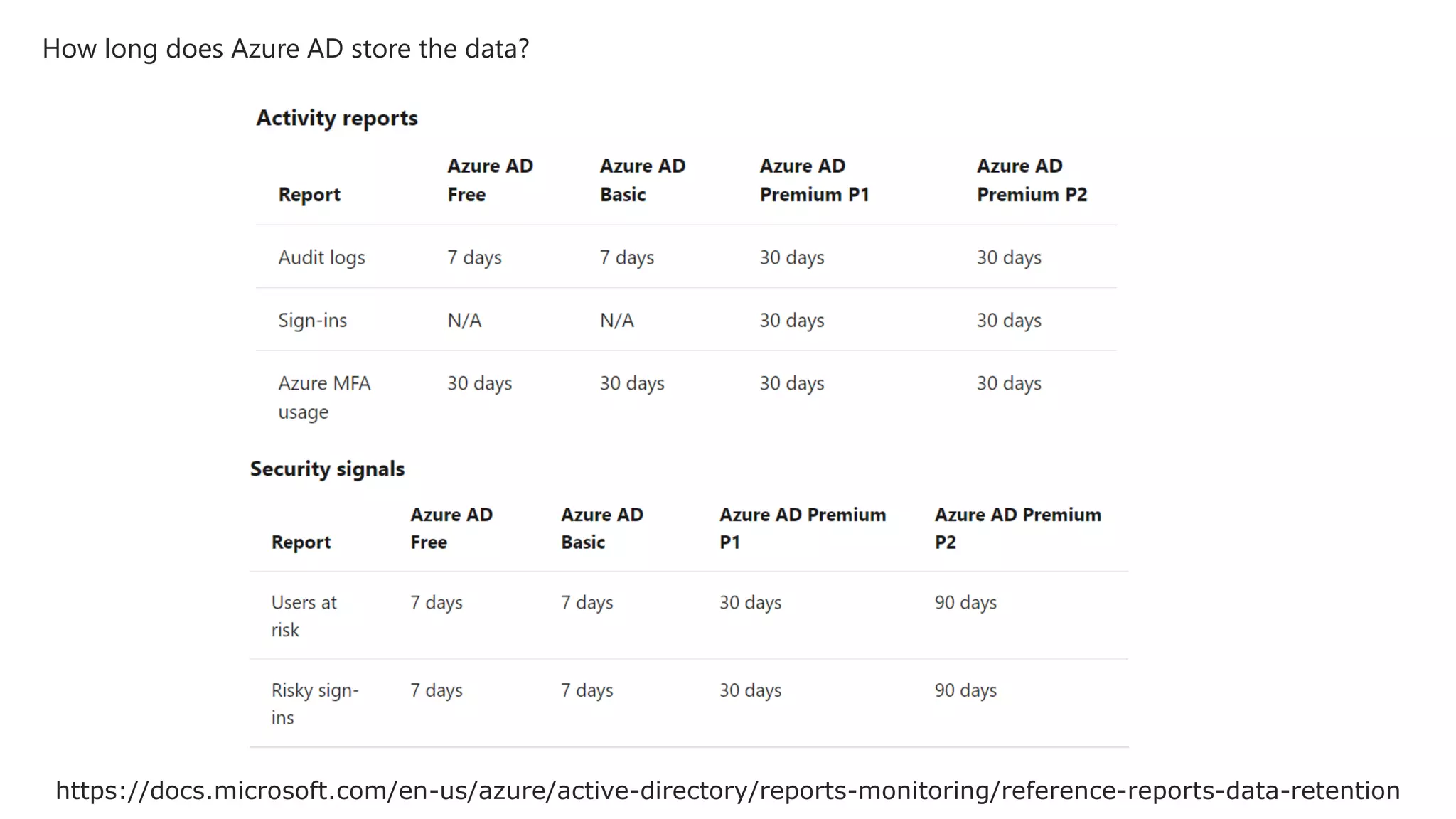
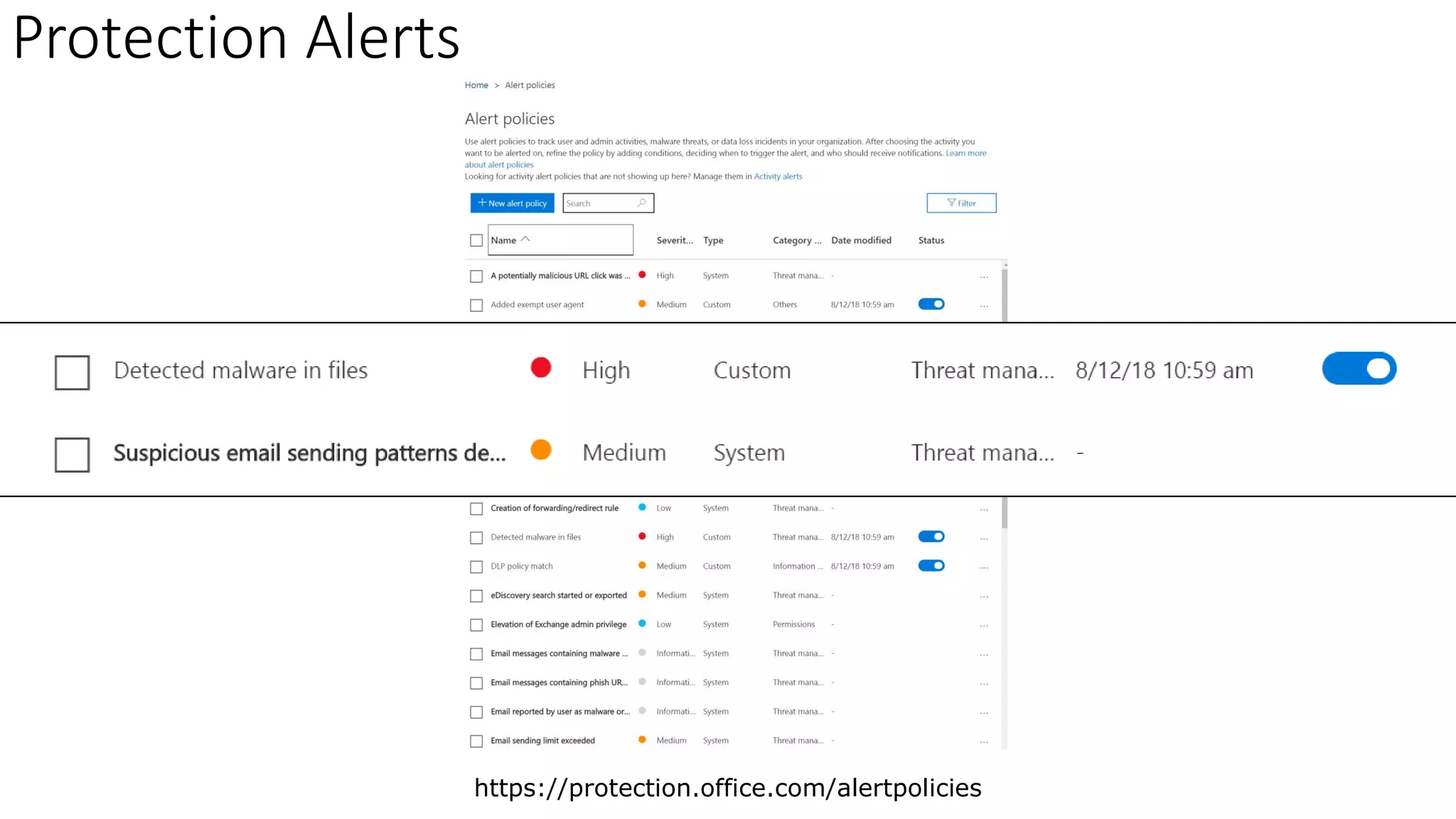
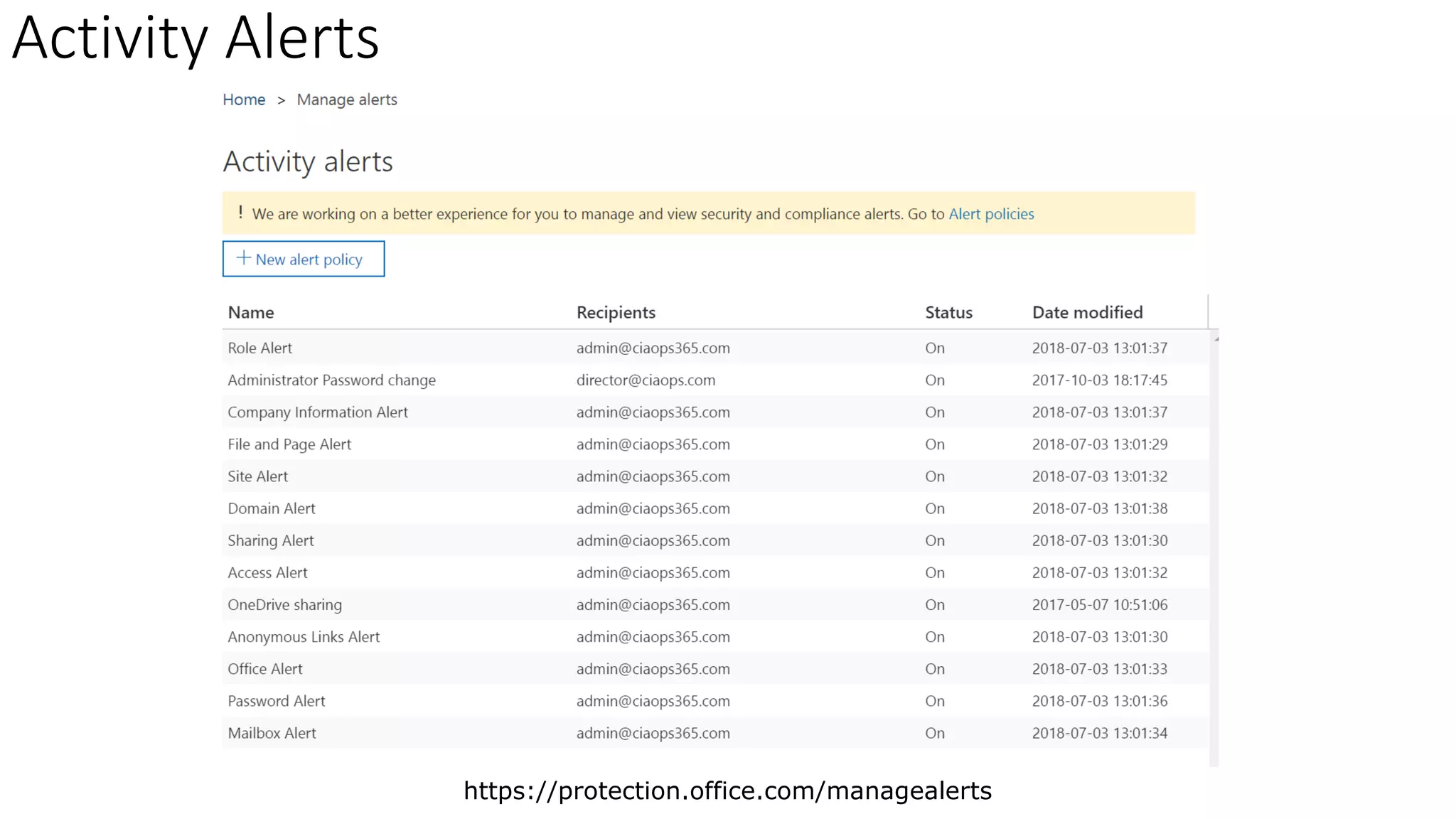
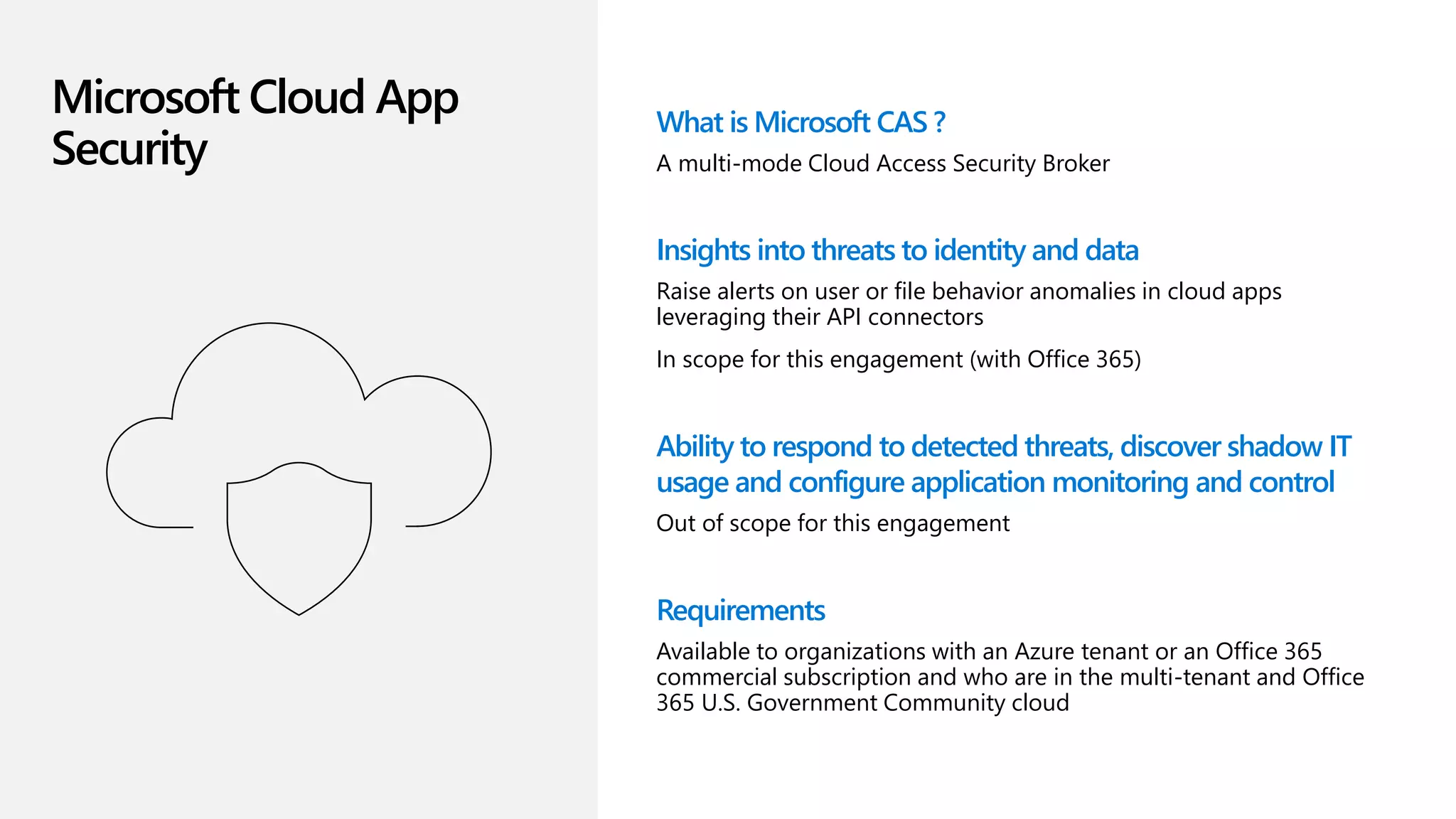
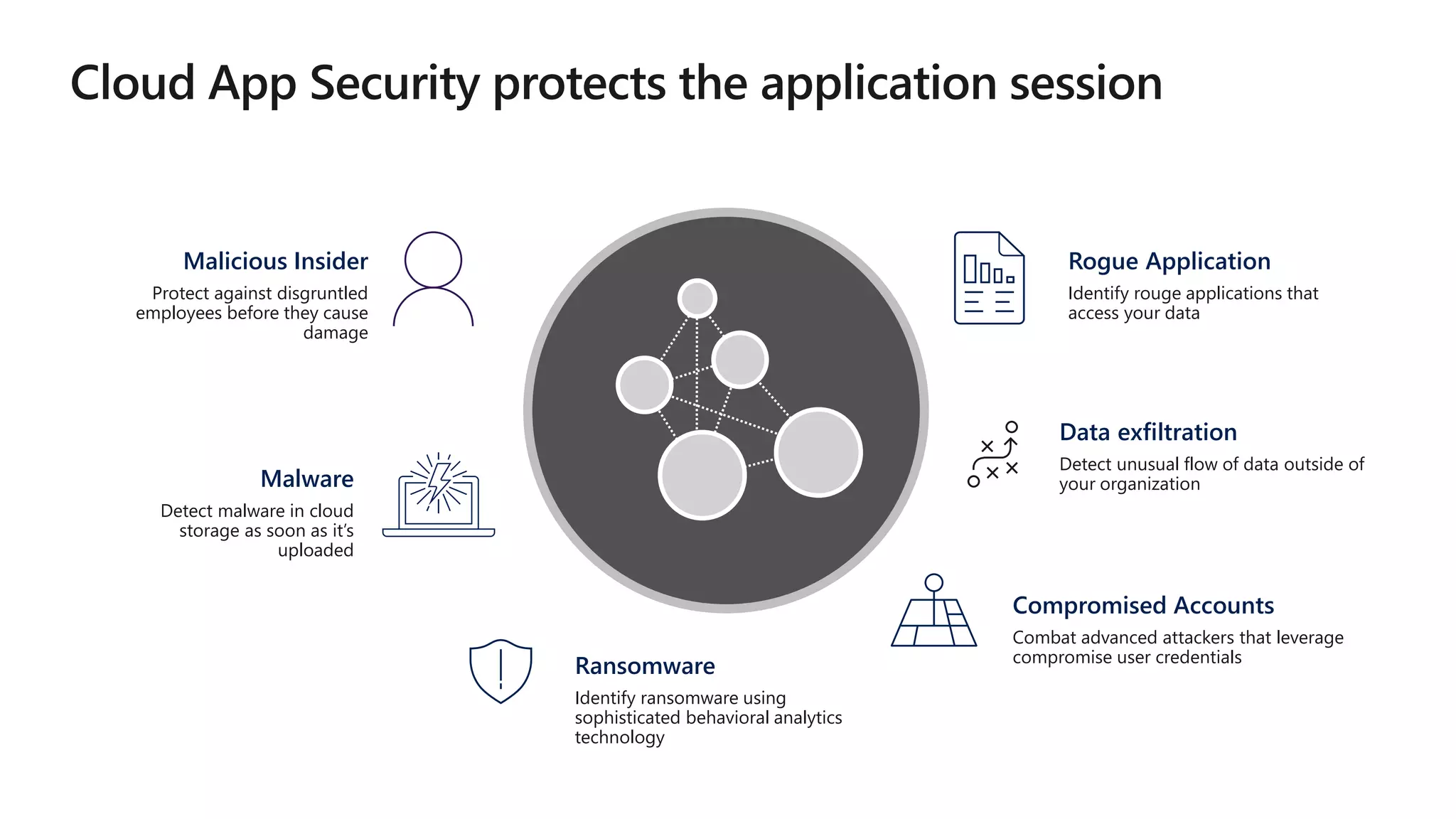
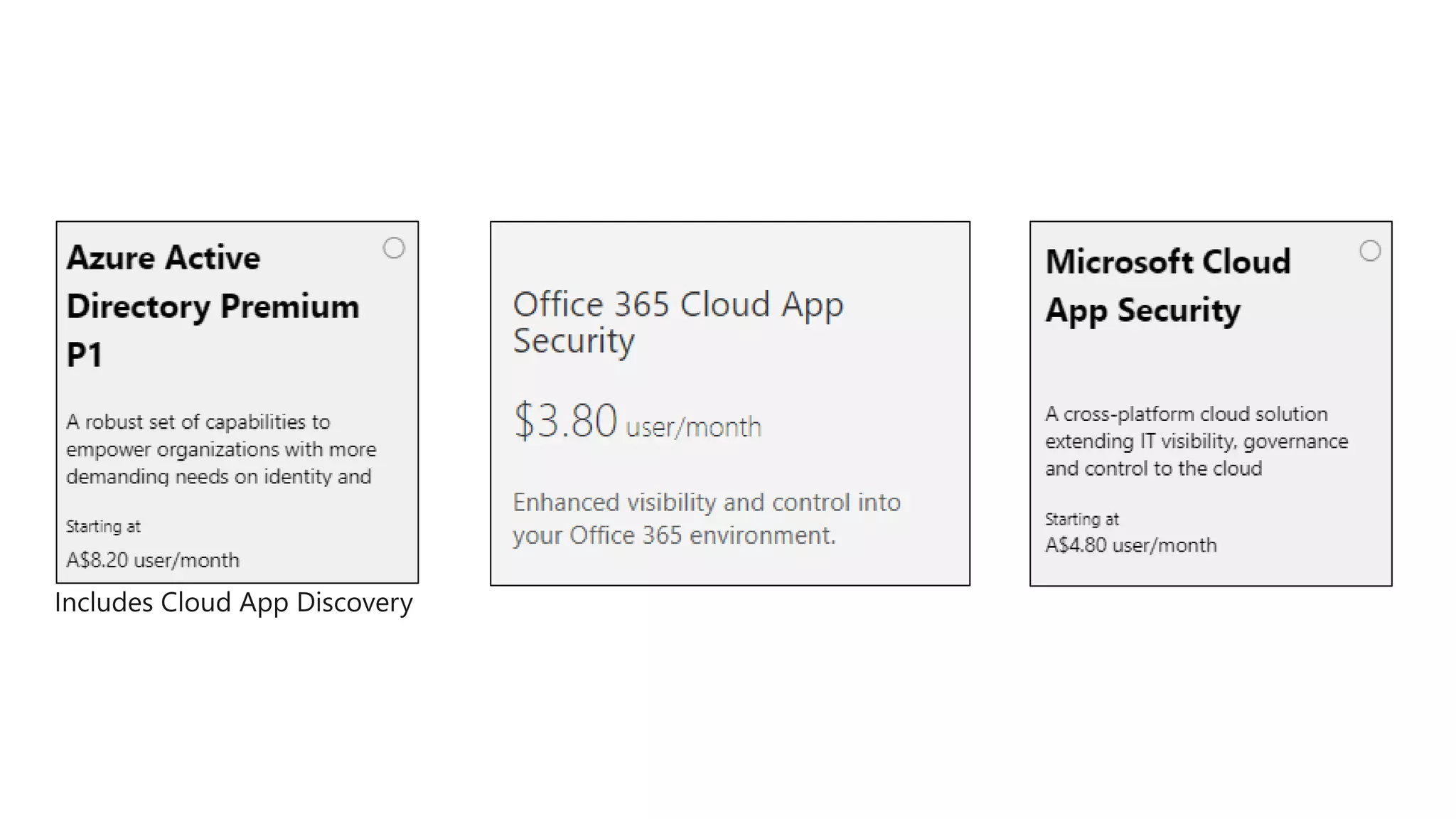
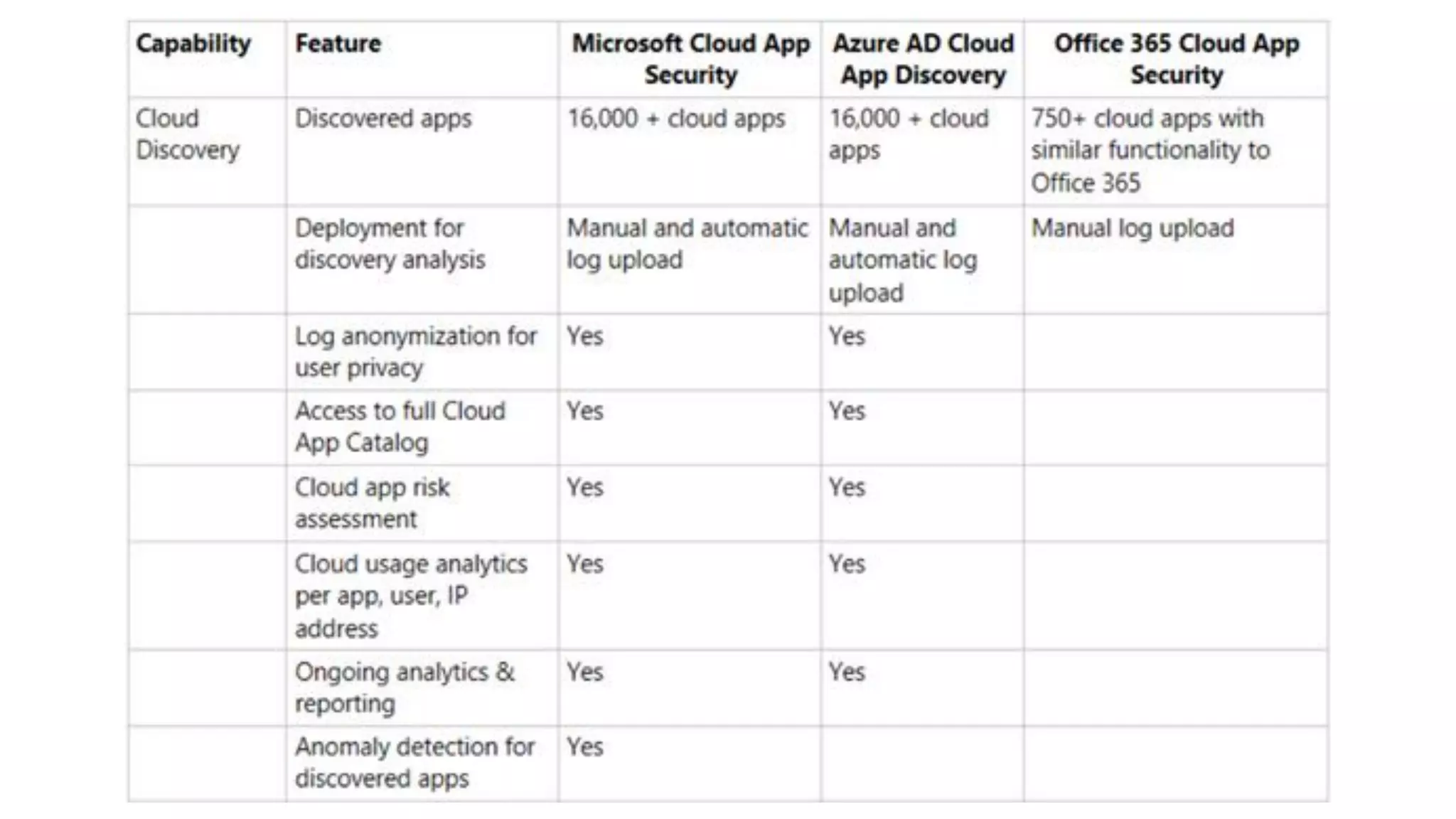
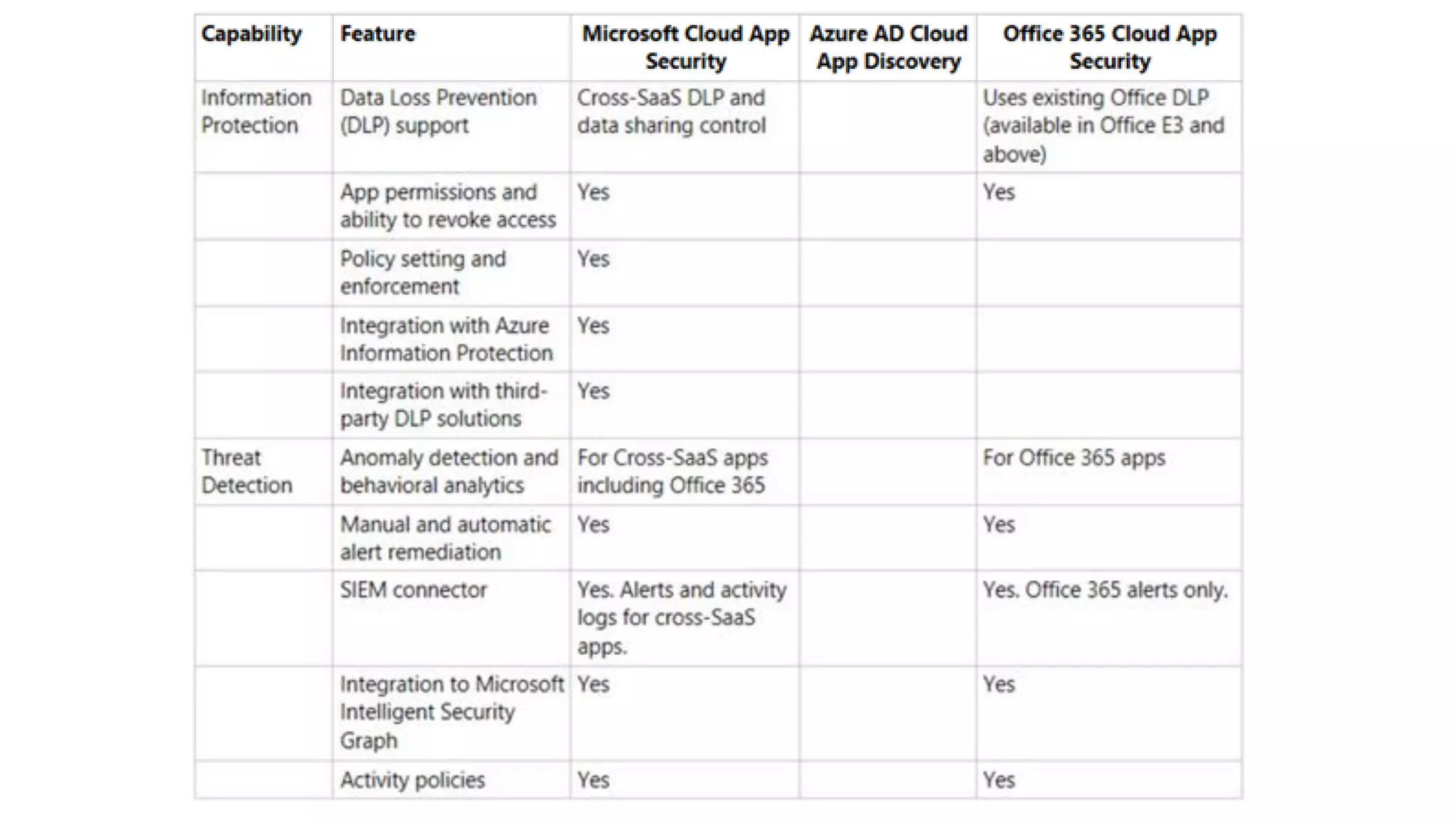
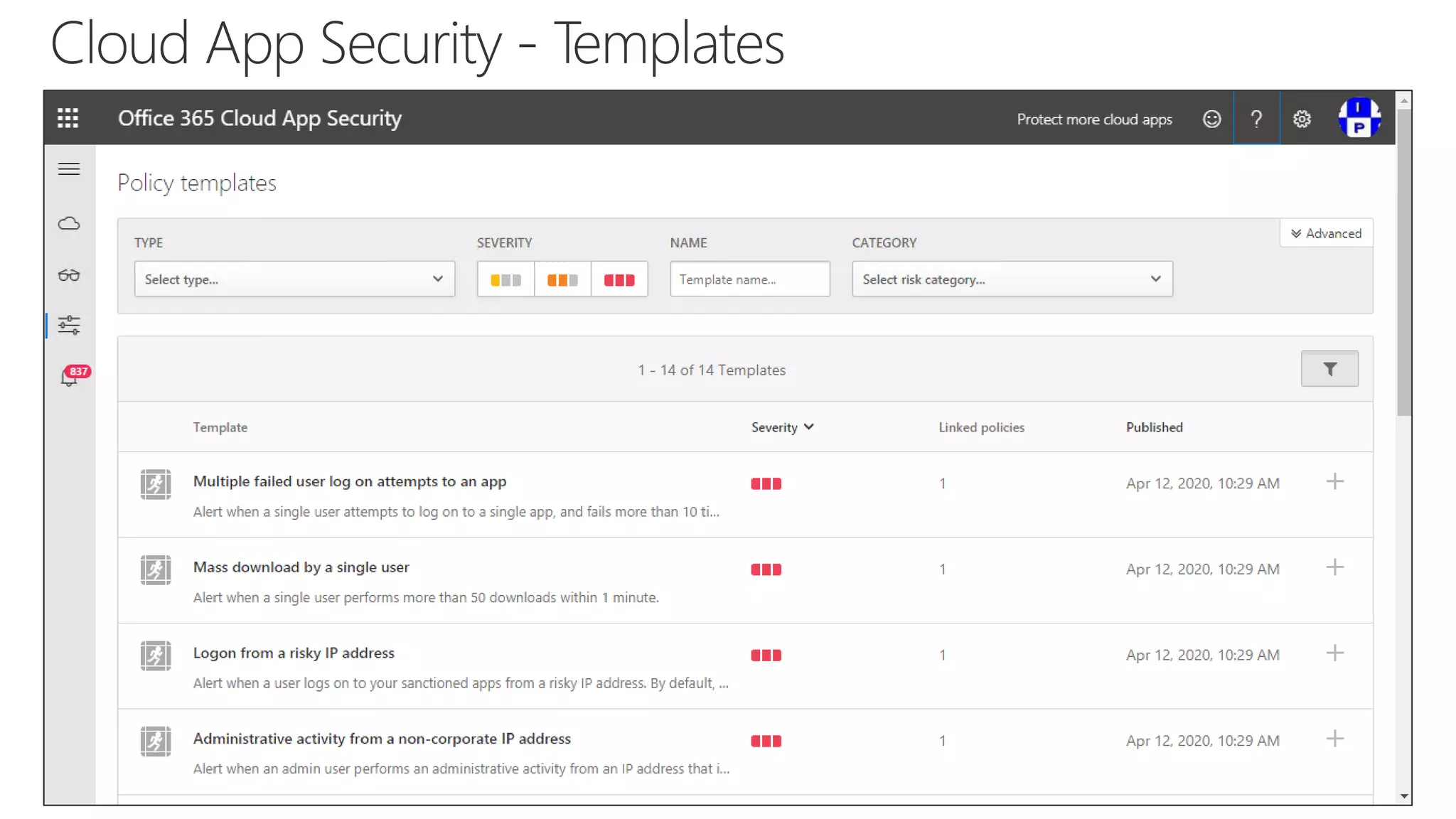
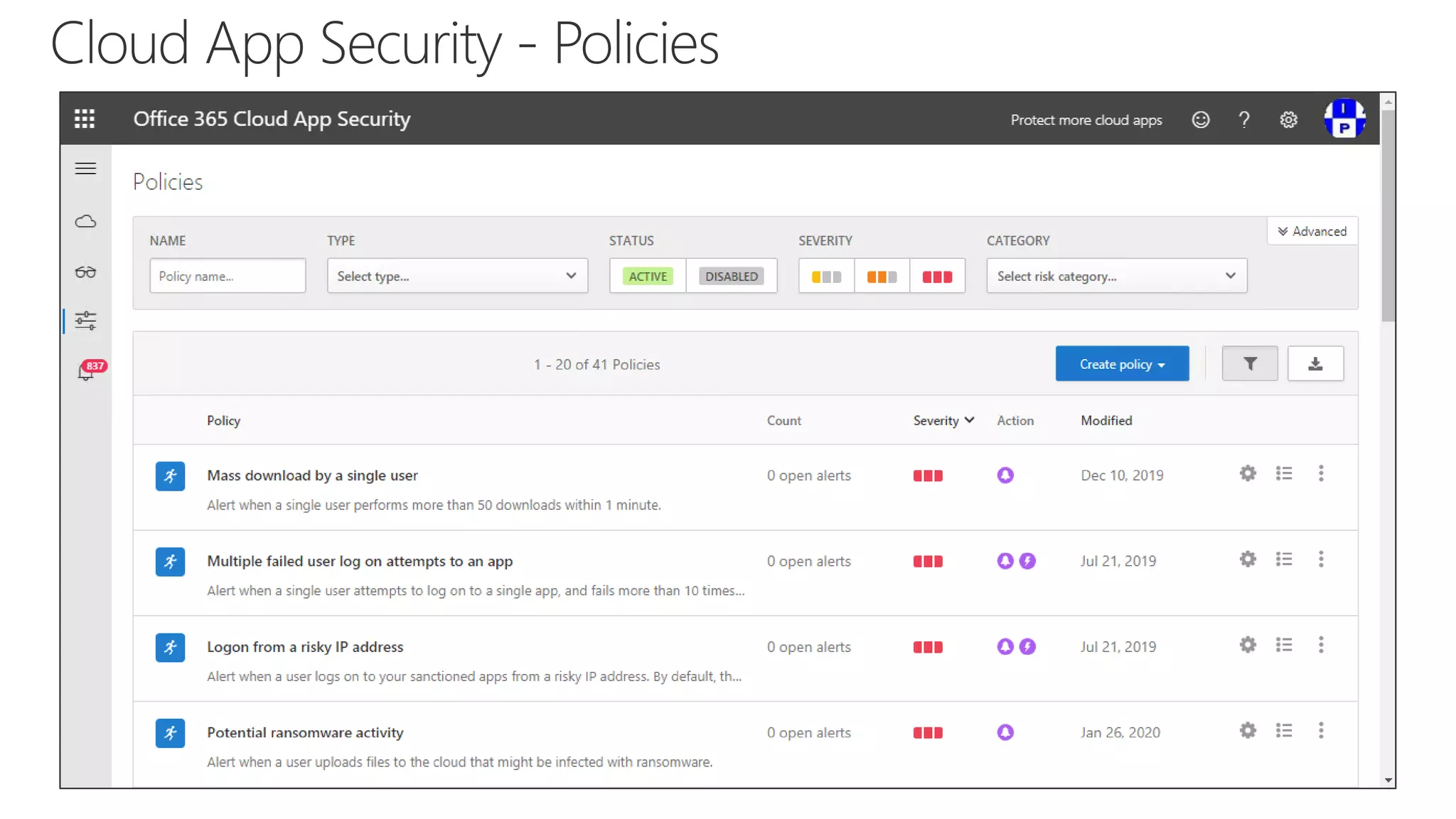
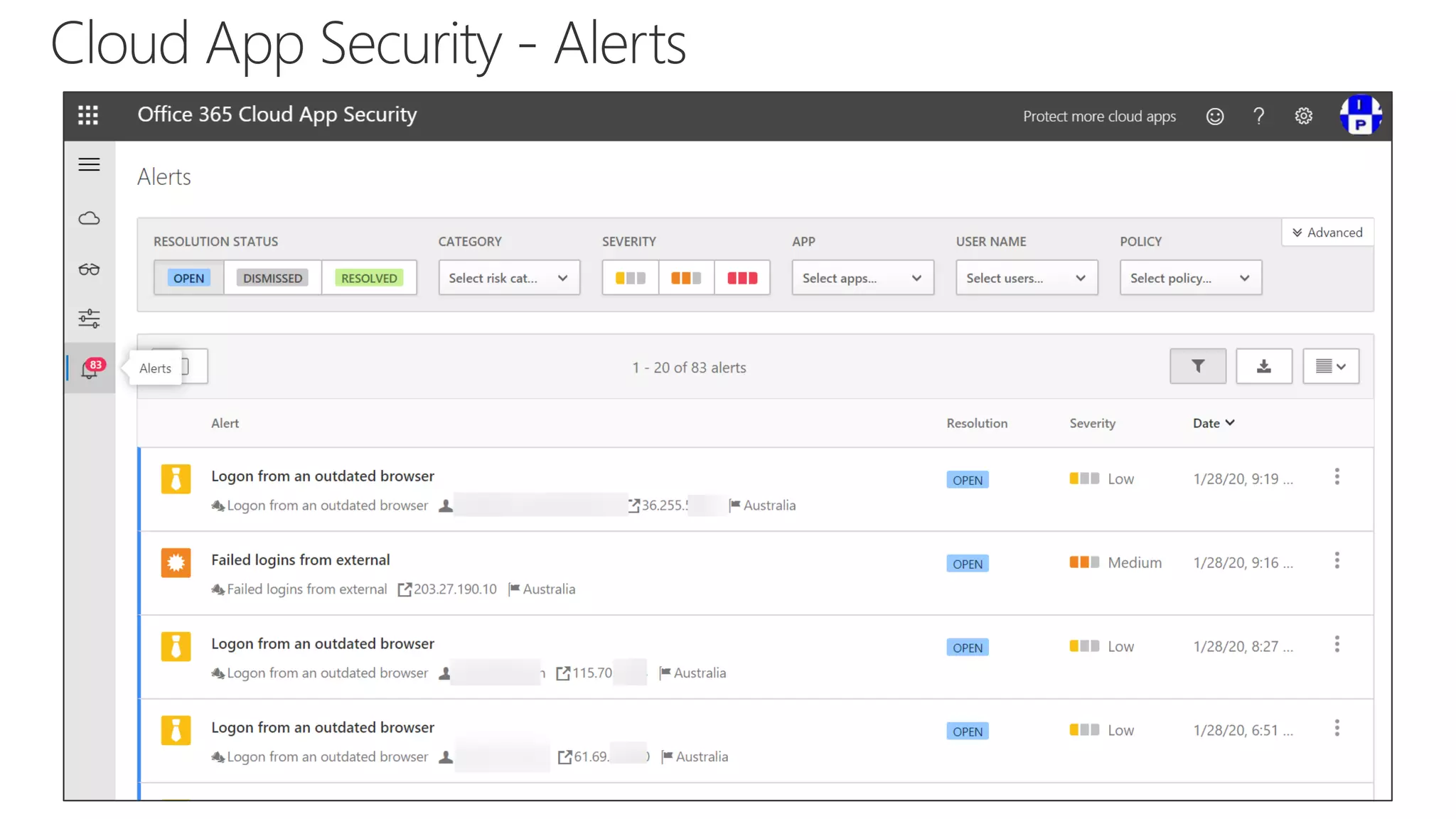
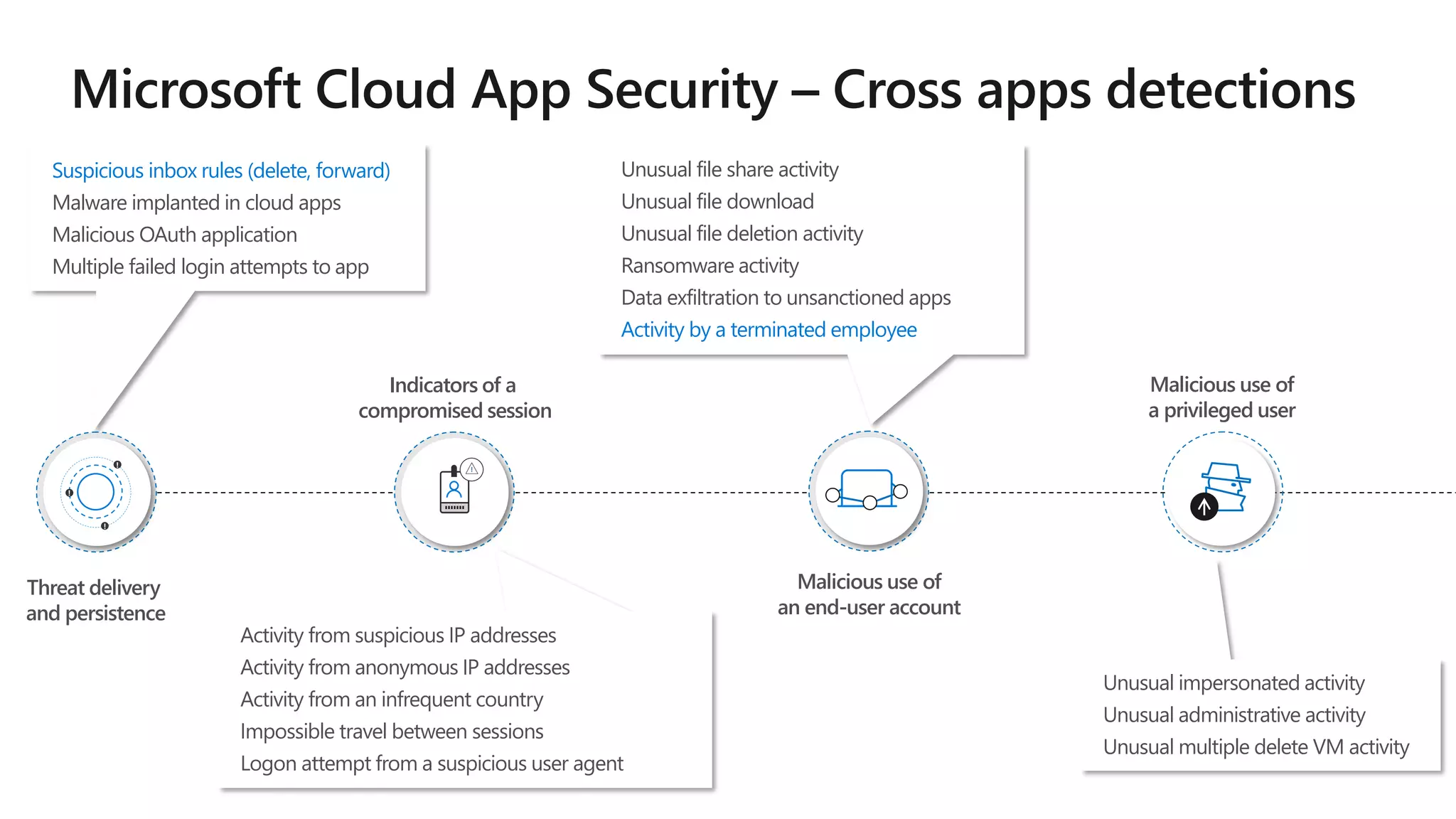
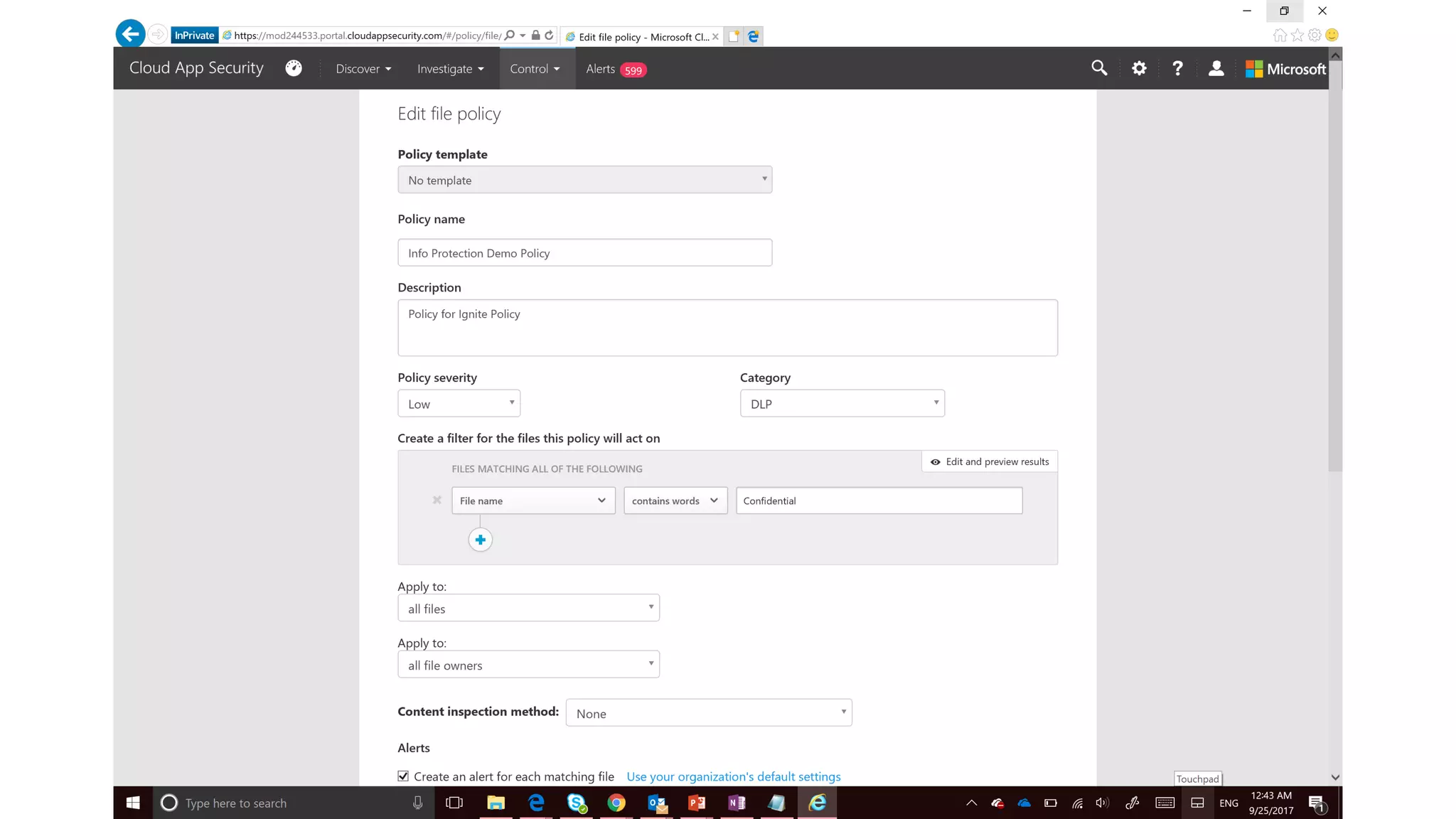
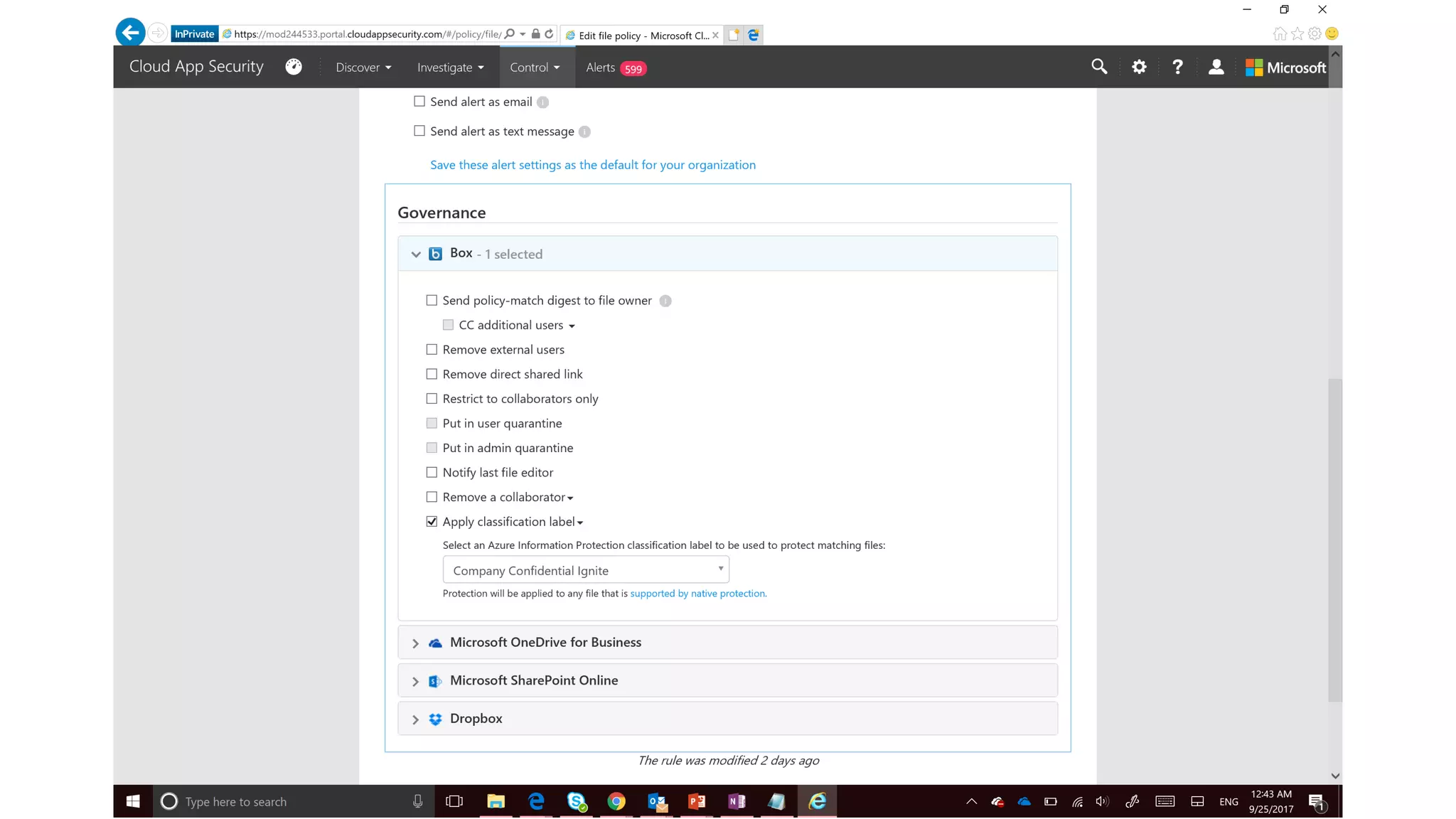
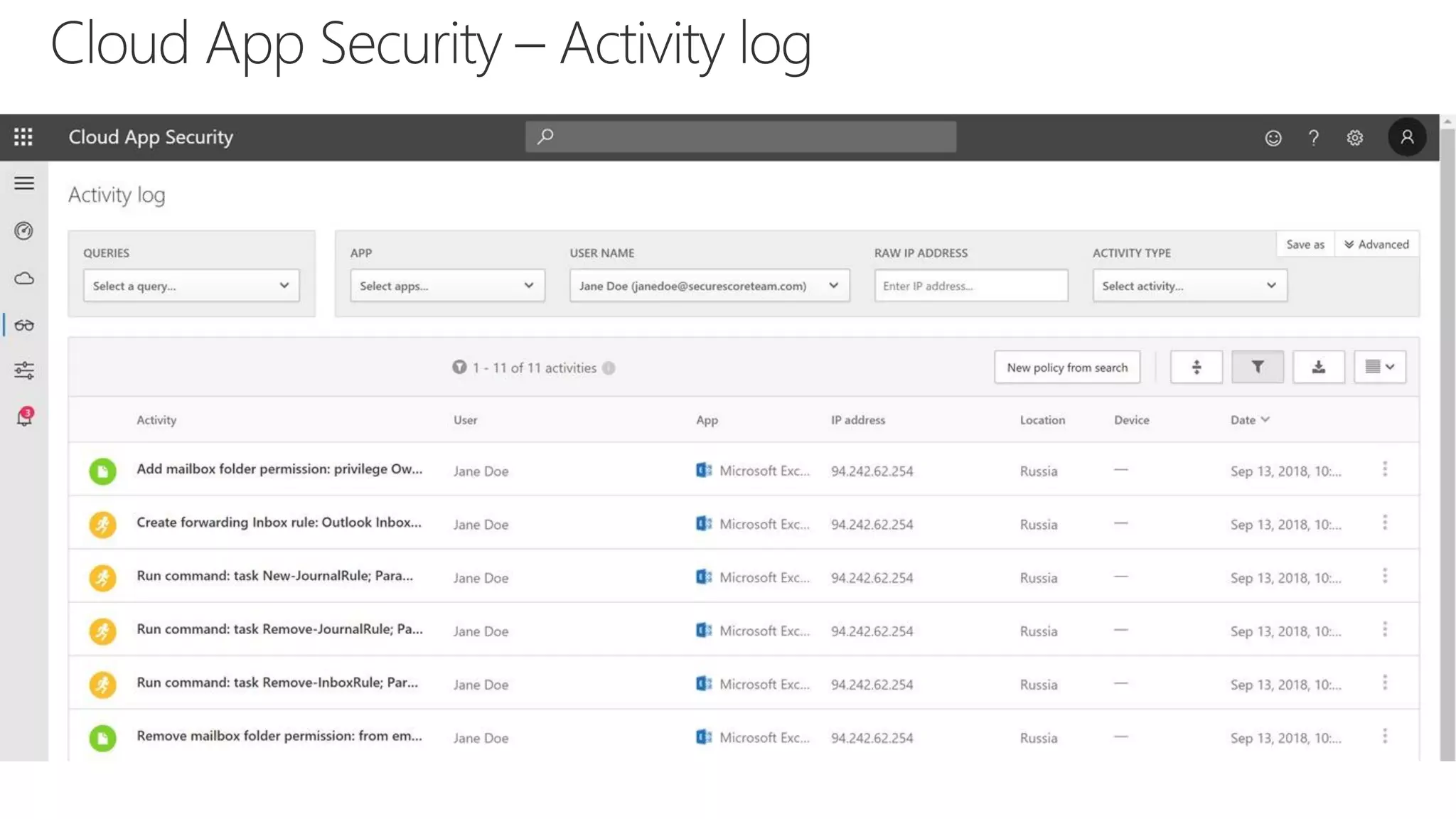
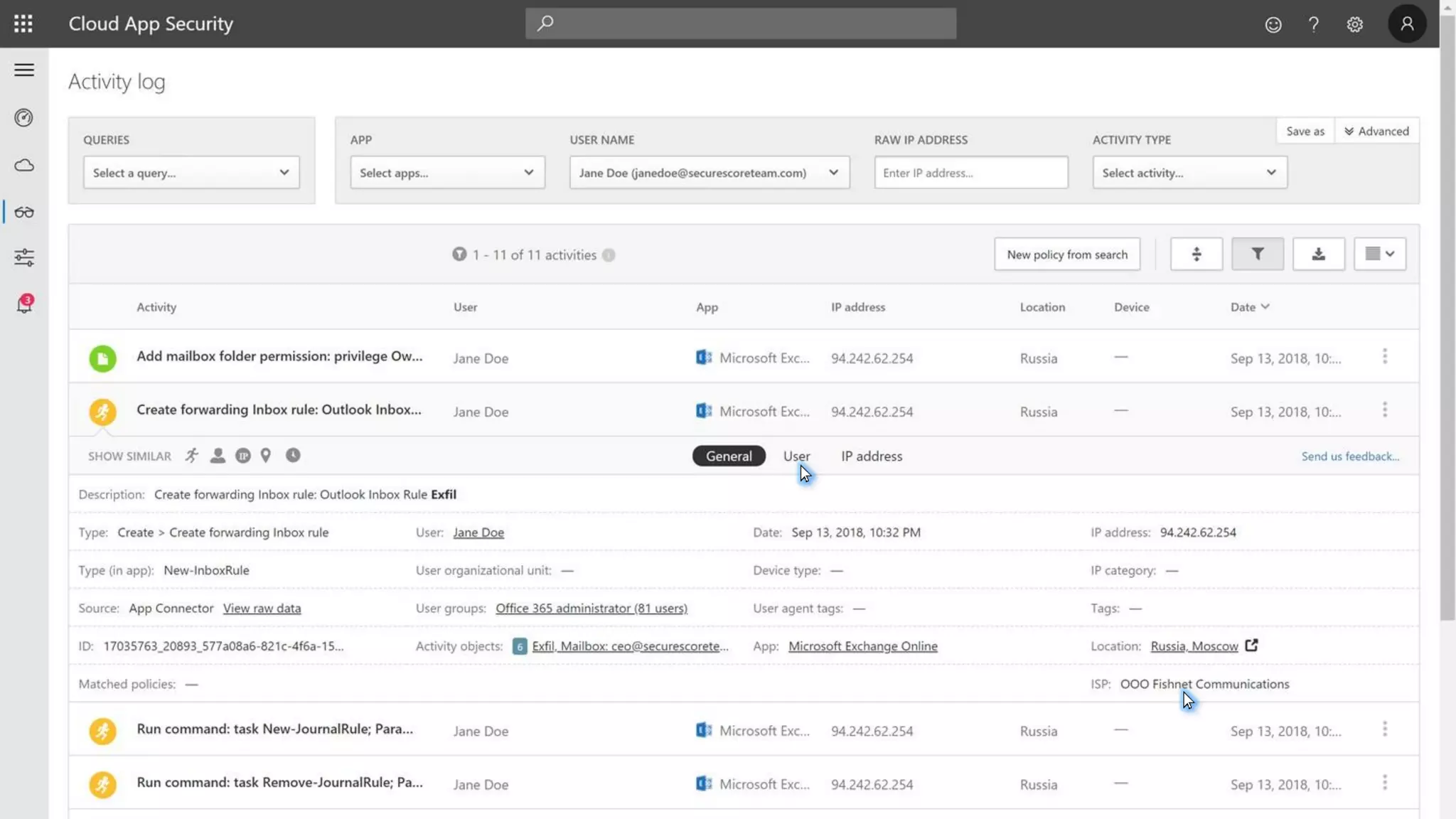
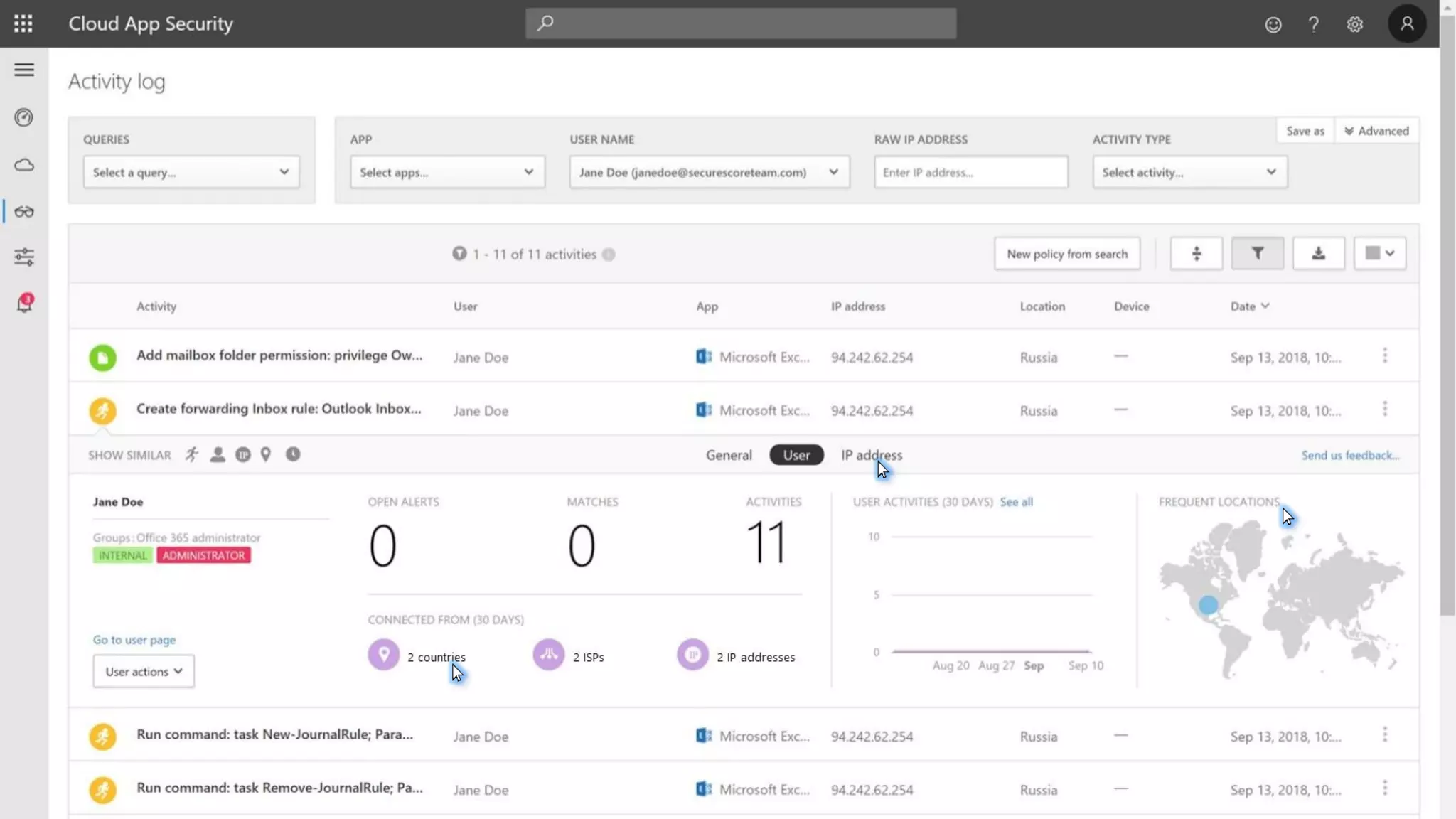
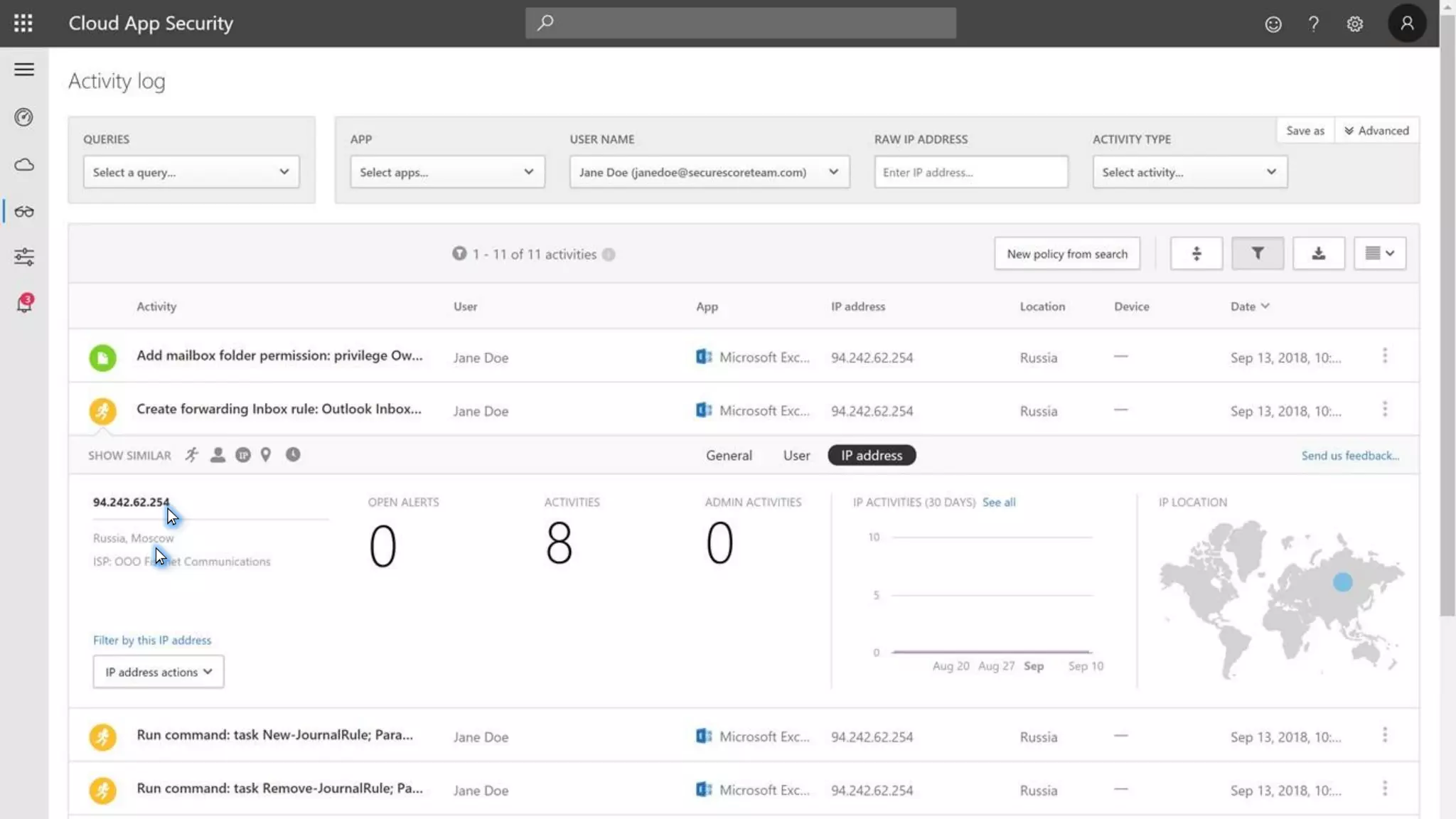
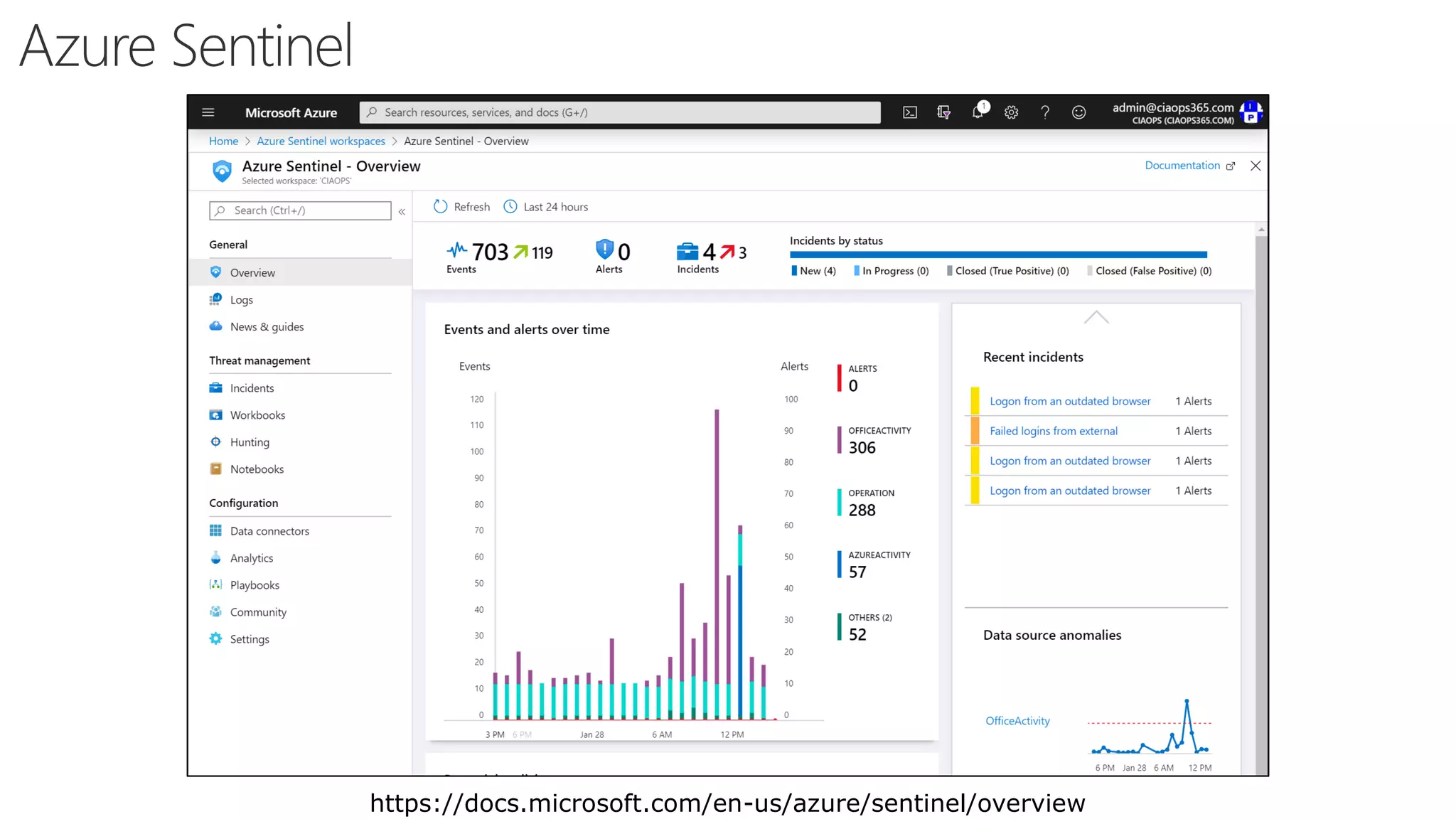
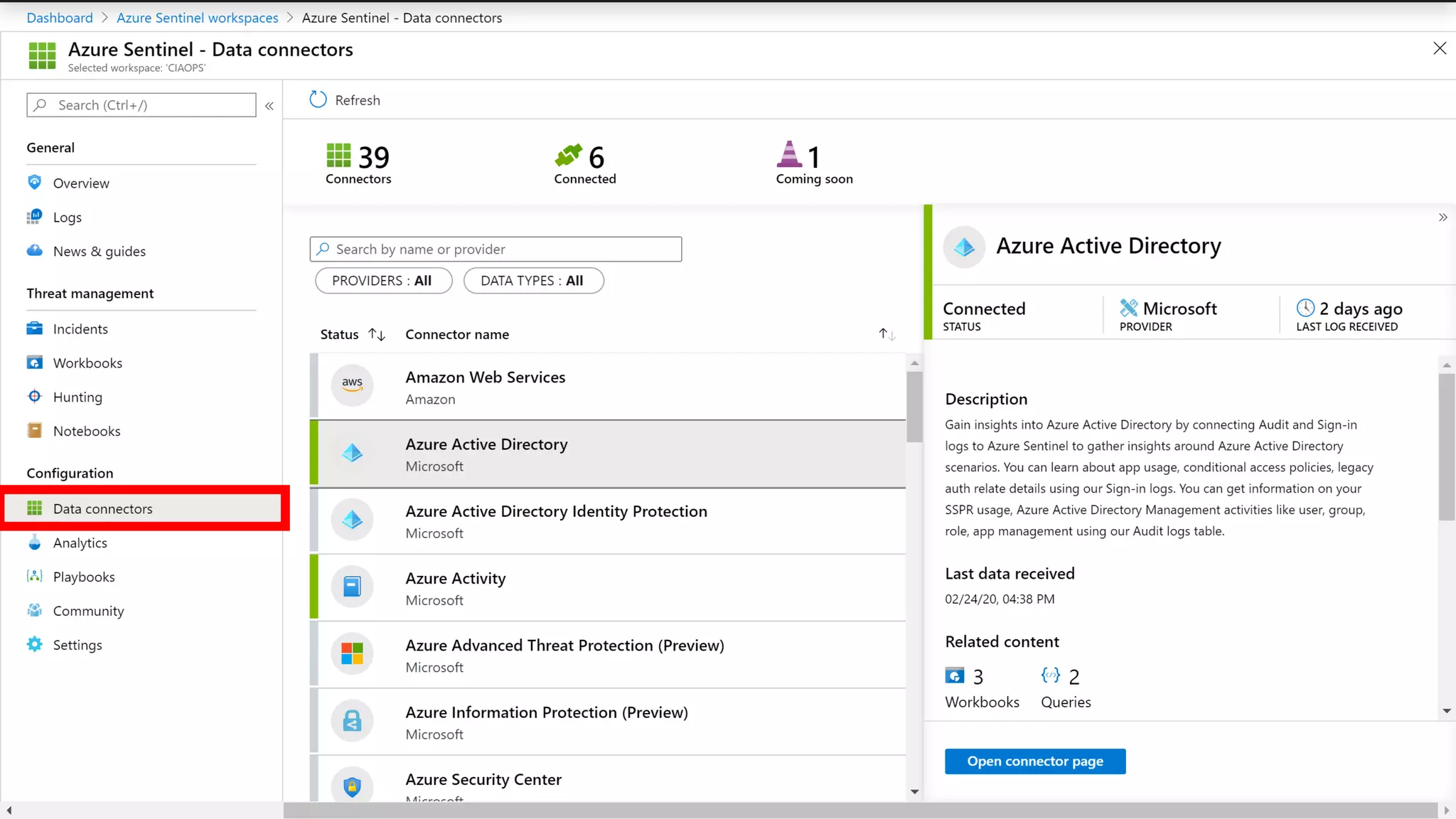
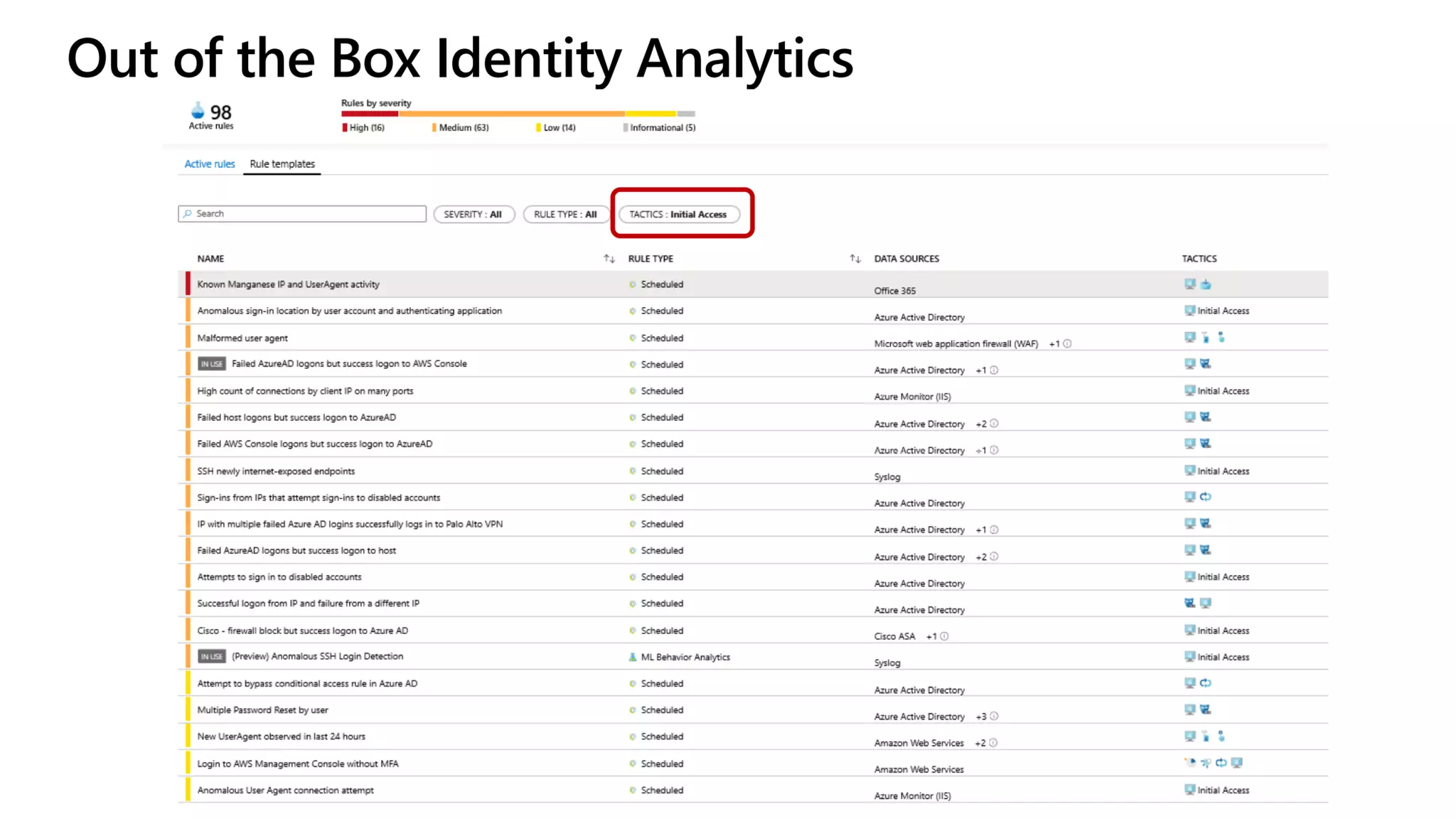
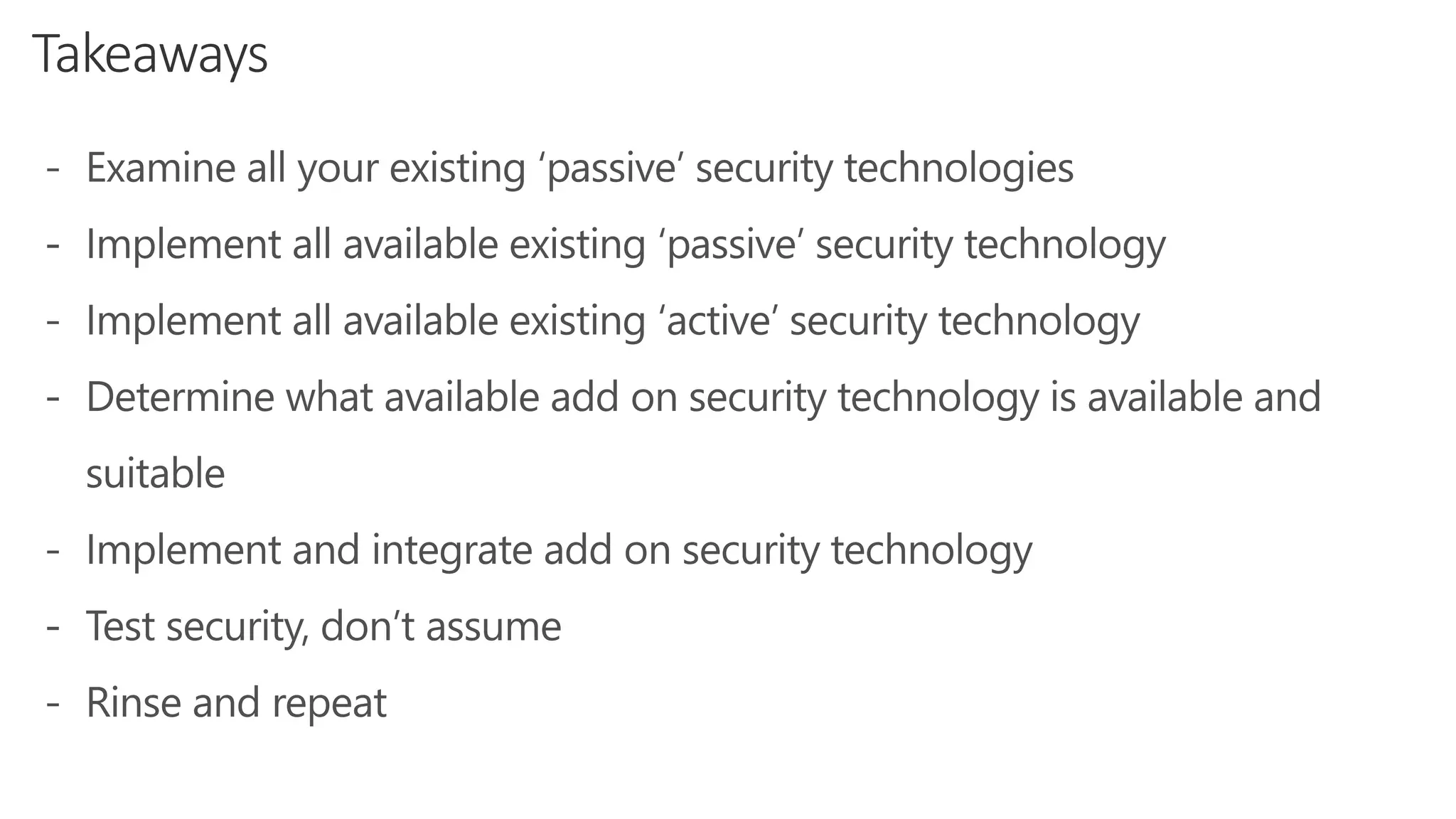
The document discusses Microsoft 365 security strategies, emphasizing comprehensive protection against identity attacks and data breaches across various platforms, including Azure and Office 365. It highlights the importance of using advanced analytics for threat detection and response, as well as the increasing prevalence of cyber threats such as phishing and ransomware. Additionally, it includes links to resources for implementing Microsoft Cloud App Security and monitoring anomalies in user and file behavior.