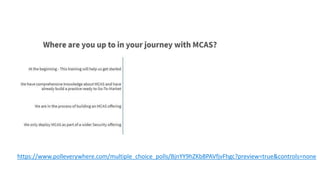
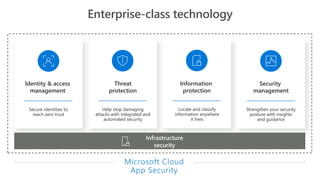
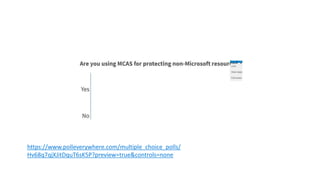
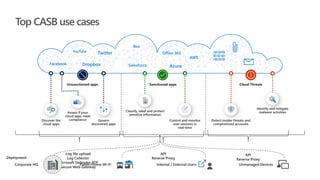
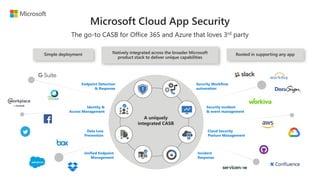
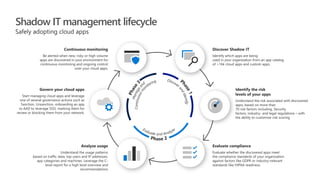
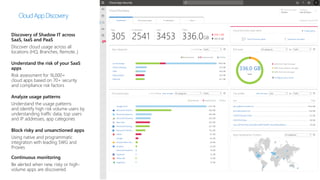
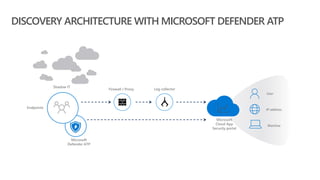
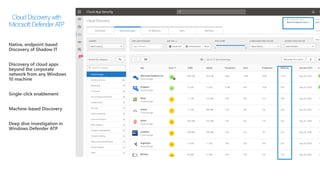
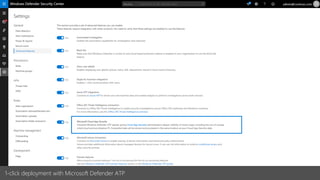
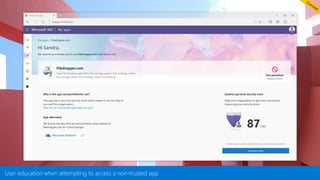
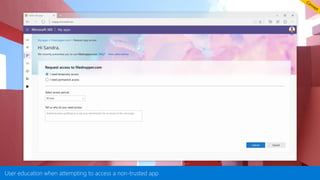
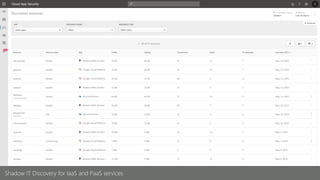
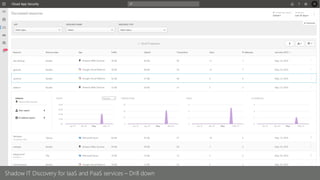
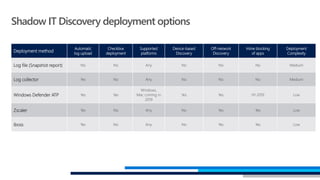
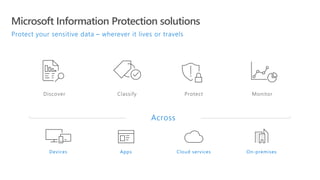
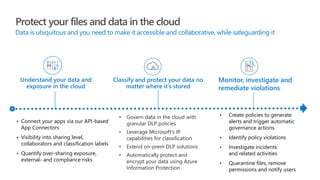
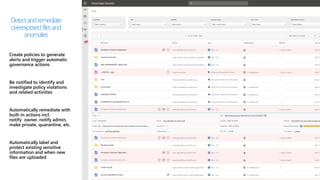
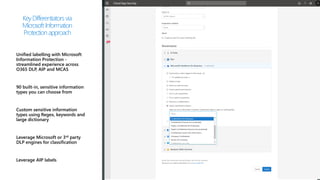
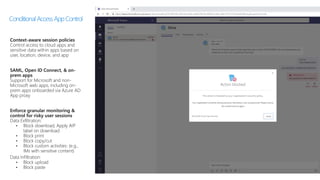
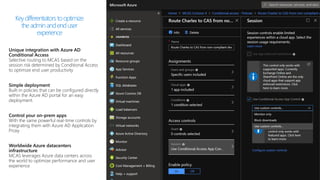
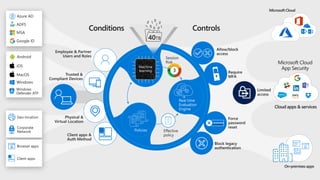
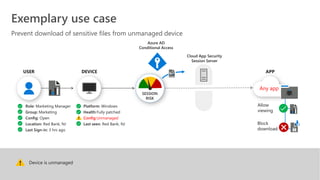
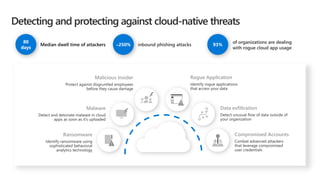
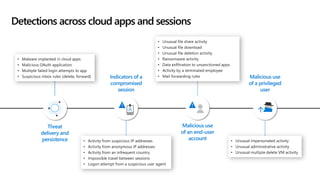
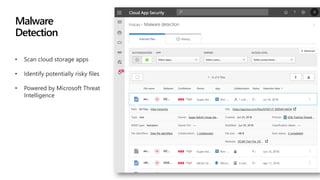
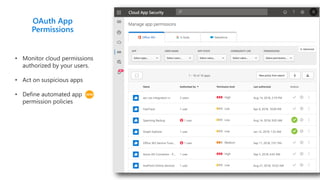
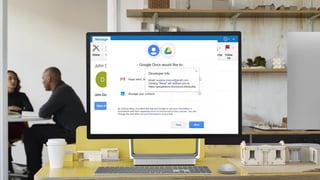
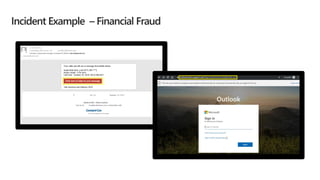
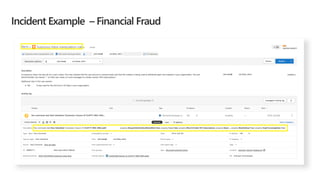
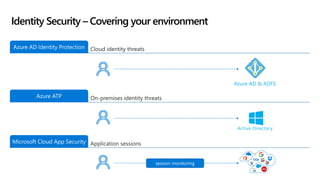
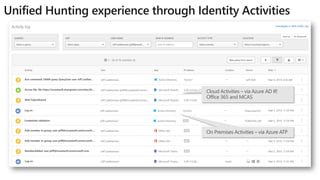
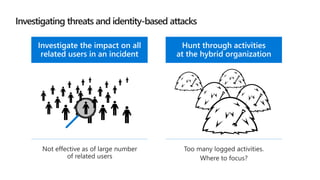
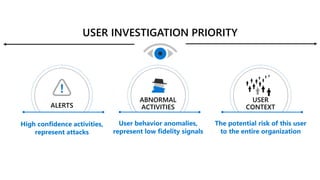
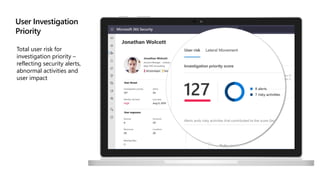
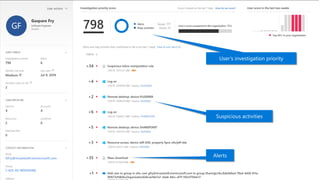
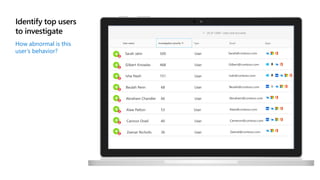
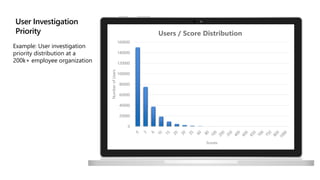
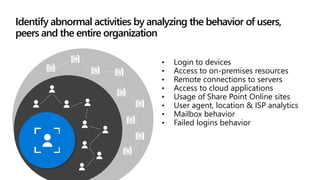
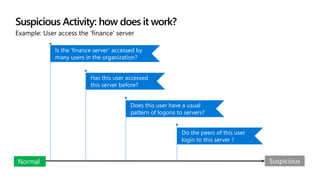
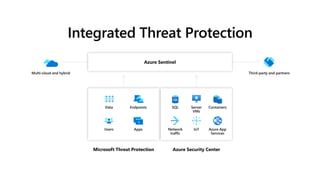
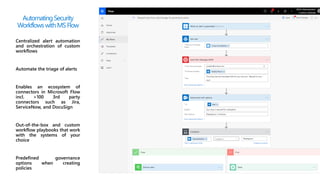
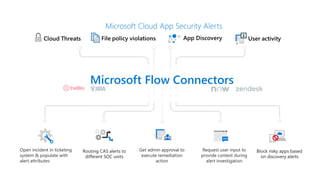
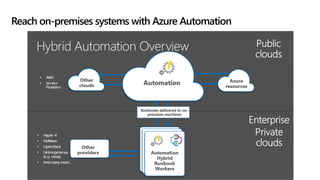
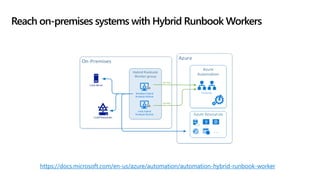
This document provides an overview of Microsoft Cloud App Security. It discusses how the platform provides enterprise-class security for identities and access management, threat protection, information protection, and infrastructure security across cloud apps and services. Key capabilities include discovering shadow IT, assessing app risks, blocking unsanctioned apps, detecting threats, classifying and protecting data, and integrating with other Microsoft security solutions. The document also presents demos of the discovery, protection, and threat detection capabilities and discusses how Cloud App Security can integrate with other security tools and automate security workflows. It concludes with next steps around signing up for a trial and exploring use cases.