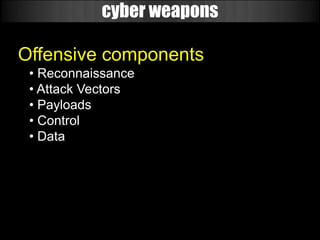
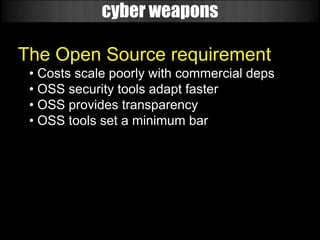
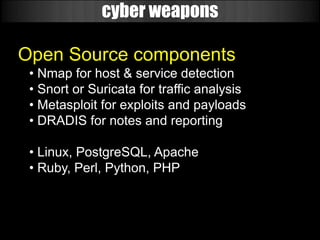
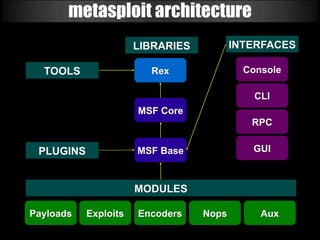
The document discusses the evolution of cyber weapons and offensive security tools from 1999 to today. It describes how such tools have progressed from being in their infancy to becoming highly sophisticated. A key point is that many military and government contractors now openly use open source tools like Metasploit due to their capabilities, cost effectiveness, and the ability to easily adapt them. The document highlights the features and power of the Metasploit framework, including its modular design, wide range of exploits and payloads, automation capabilities, and use by many organizations for tasks like vulnerability research and penetration testing at scale.











![metasploit
888 888 Y8P888
888 888 888
88888b.d88b. .d88b. 888888 8888b. .d8888b 88888b. 888 .d88b. 888888888
888 "888 "88bd8P Y8b888 "88b88K 888 "88b888d88""88b888888
888 888 88888888888888 .d888888"Y8888b.888 888888888 888888888
888 888 888Y8b. Y88b. 888 888 X88888 d88P888Y88..88P888Y88b.
888 888 888 "Y8888 "Y888"Y888888 88888P'88888P" 888 "Y88P" 888 "Y888
888
888
888
=[ metasploit v3.4.2-dev [core:3.4 api:1.0]
+ -- --=[ 578 exploits - 296 auxiliary
+ -- --=[ 212 payloads - 27 encoders - 8 nops
=[ svn r9949 updated today (2010.08.03)
msf >](https://image.slidesharecdn.com/cyberweaponry-100804085753-phpapp01/85/Open-Source-Cyber-Weaponry-19-320.jpg)