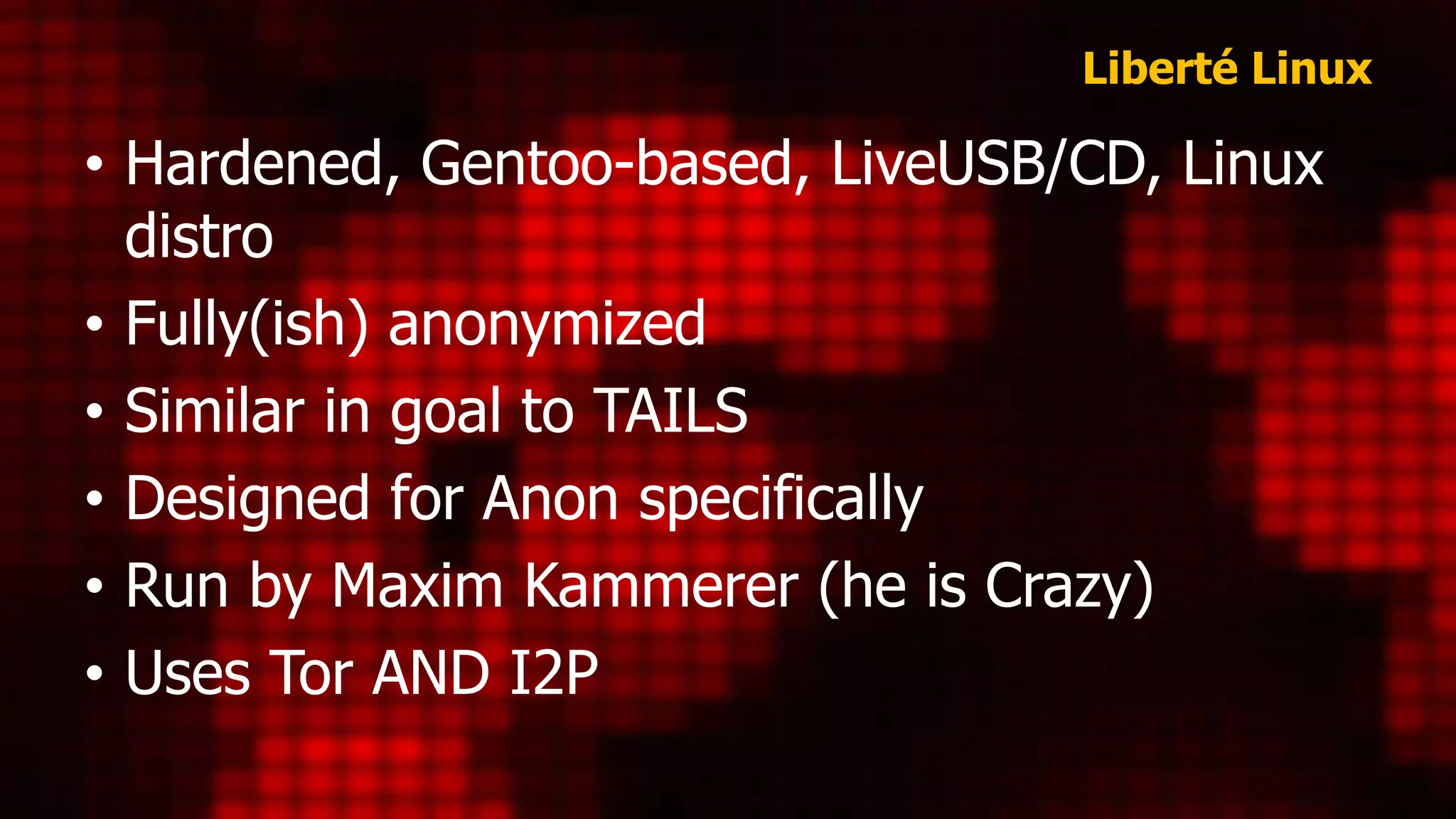
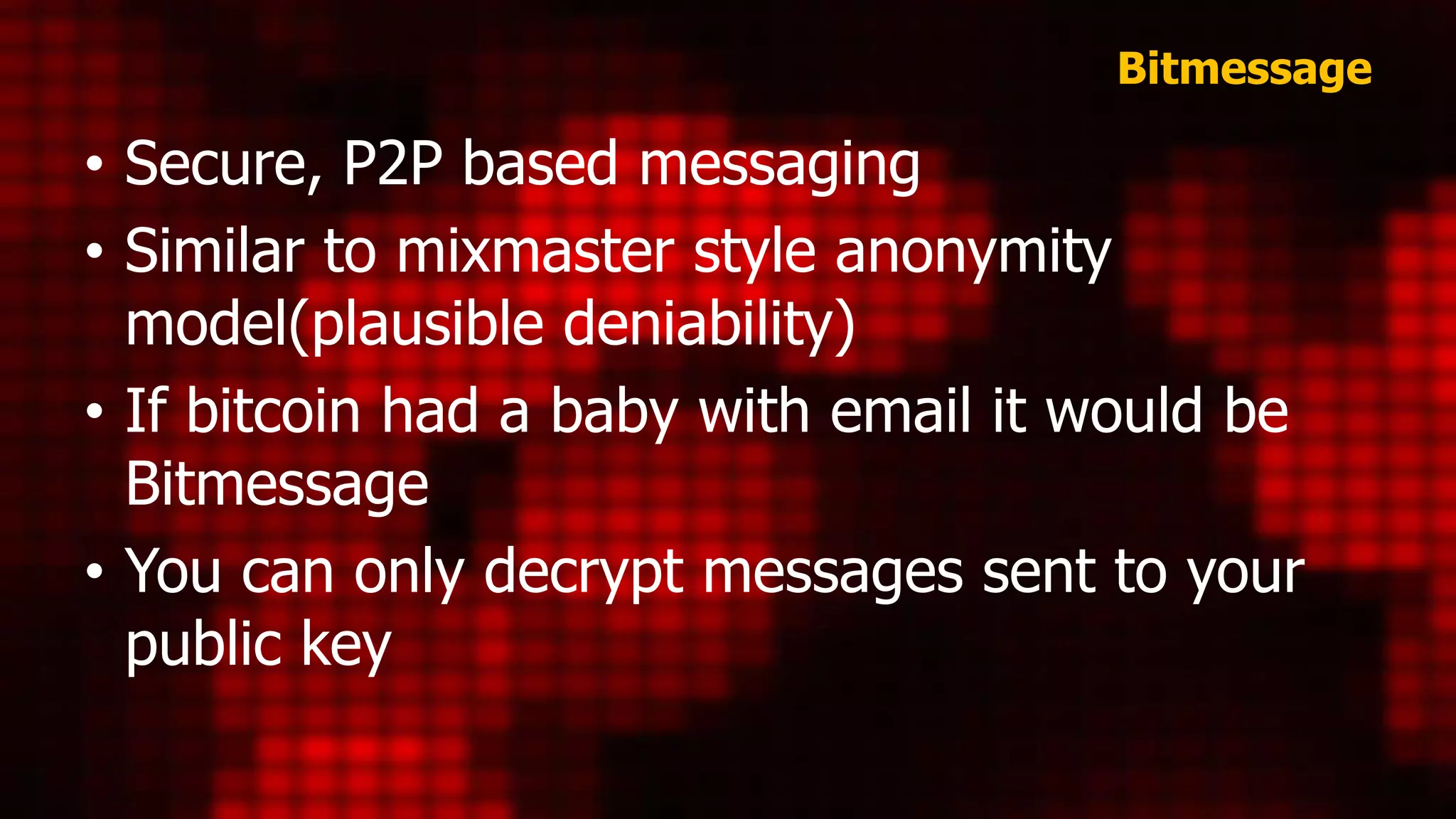
Liberte and Tails are both Linux distributions focused on anonymity, with Liberte being Gentoo-based and emphasizing security features like anti-forensic capabilities and custom HTTP headers, while Tails, based on Debian, offers regular updates and broader user support. Cables aims to provide a decentralized messaging platform but lacks popularity and effective user adoption compared to Bitmessage, which is favored among deep web users for its p2p approach. Overall, while Liberte is innovative, Tails is more user-friendly and widely supported, and Bitmessage is the most utilized despite the complexity of its security features.










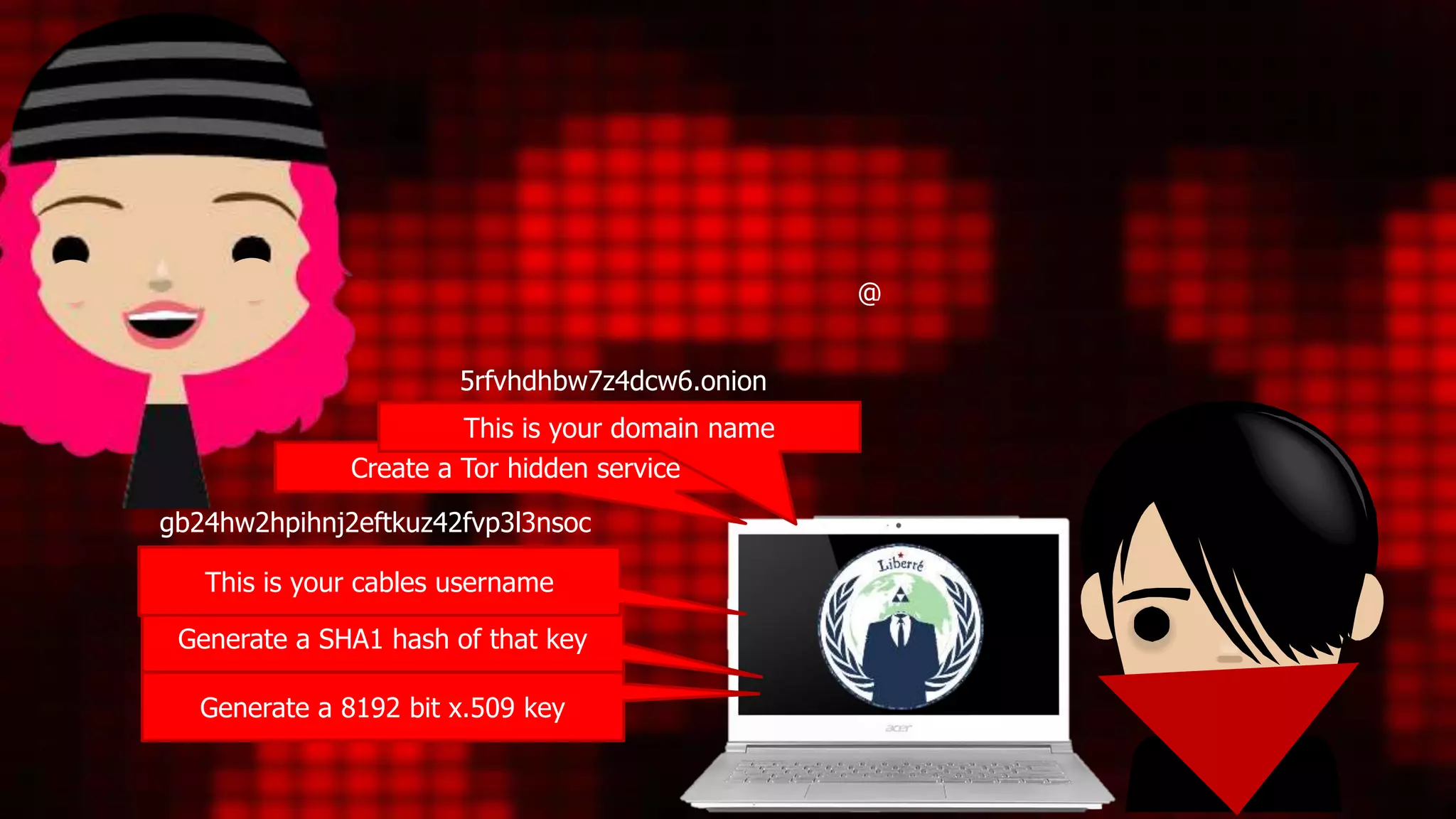









![Crypto
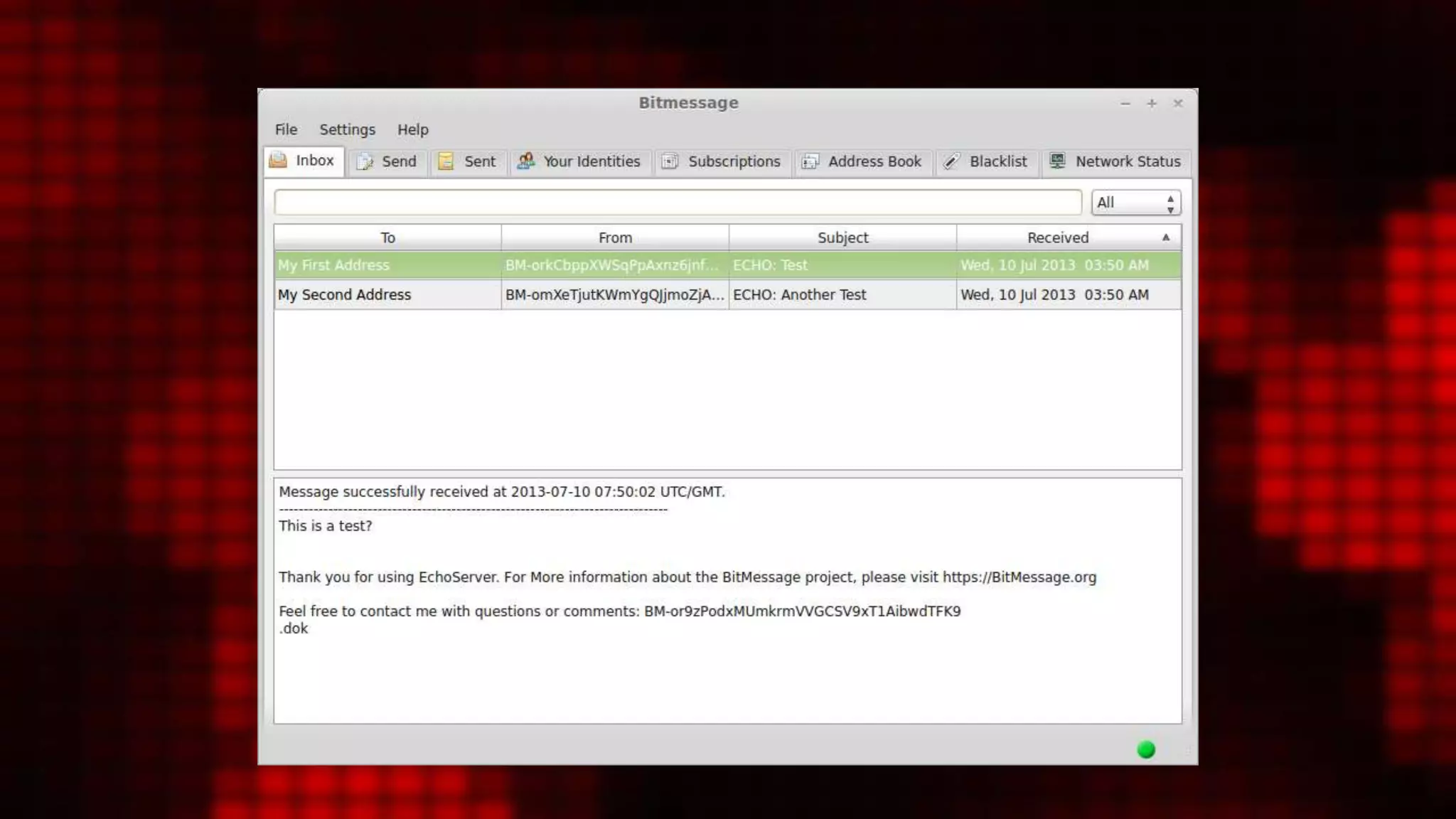
• payload = time + streamnumber + encrypted
• target = 2^64 / ((length of the payload in bytes +
payloadLengthExtraBytes + 8) *
averageProofOfWorkNonceTrialsPerByte)
• initialHash = sha512(payload)
• while trialValue > target:
nonce = nonce + 1
resultHash = sha512(sha512( nonce + initialHash))
trialValue = int(resulthash[:8])
• Output: trialValue](https://image.slidesharecdn.com/reinventinganonemail-momversion-150603153338-lva1-app6892/75/Reinventing-anon-email-36-2048.jpg)