This document describes a distributed malware analysis system using Cuckoo Sandbox. It discusses:
1) Cuckoo Sandbox is an open source automated malware analysis system that runs binary files in virtual machines to record behaviors like API calls, files created, registry access, and network traffic.
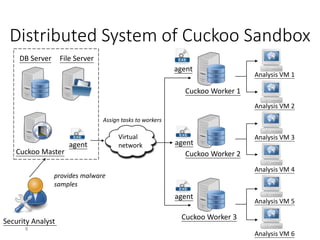
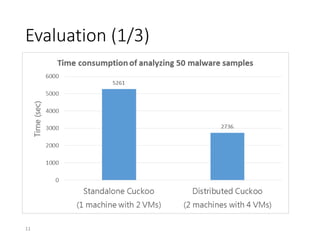
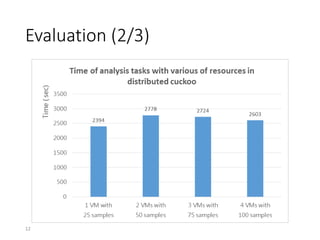
2) The motivation for a distributed system is that the computing power of a single machine is limited, causing performance bottlenecks for analyzing large numbers of samples.
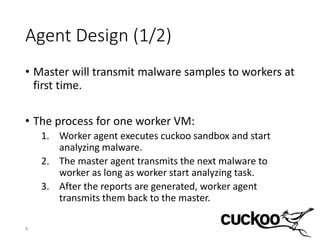
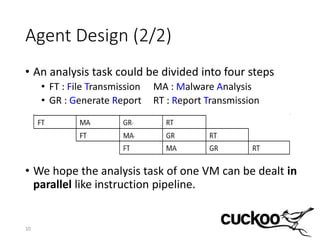
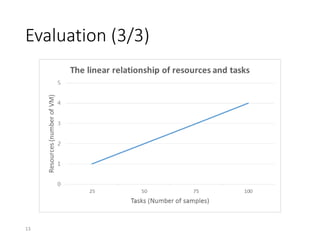
3) The distributed Cuckoo system uses a master-worker architecture to assign analysis tasks to multiple worker nodes in parallel, reducing total analysis time and allowing the system to scale to more samples as hardware resources increase.