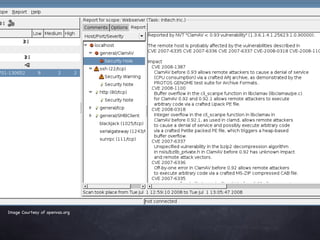
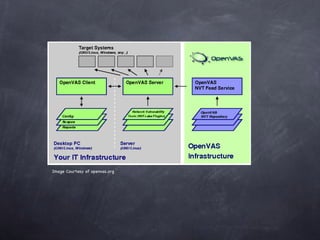
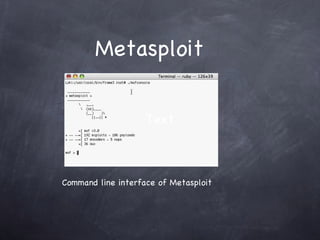
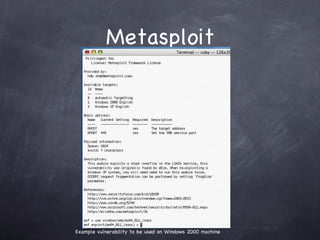
The document provides an overview of free and open source network security tools including Kismet for wireless monitoring, OpenVAS for vulnerability scanning, Metasploit for exploitation, and Nmap for port scanning and service detection. It discusses how these tools can be used both offensively to detect issues and defensively to harden networks, and highlights advantages like cost but also challenges like potential instability. The presentation focuses on demonstrating these tools and educating administrators about network security risks and defenses.