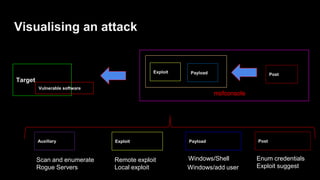
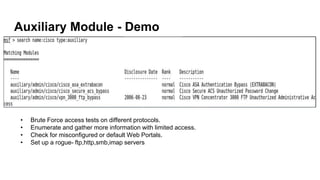
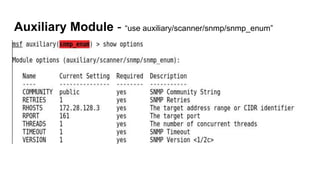
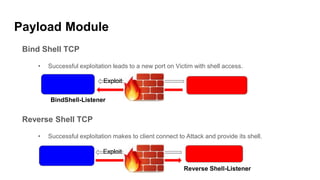
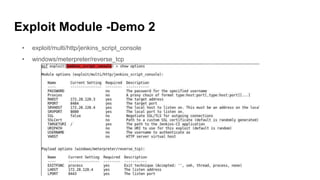
This document provides an overview of Metasploit for beginners. It discusses why Metasploit is useful, how to set up a demo environment, and how to use auxiliary and exploit modules. It then demonstrates auxiliary modules for scanning and information gathering. It also demonstrates two exploit modules against ElasticSearch and Jenkins, using reverse shell payloads. The document provides a cheat sheet for navigating msfconsole and describes common commands used prior to demonstrations.




![Metasploit Framework
Current stable version is v4.13.X
• Written in ruby, https://github.com/rapid7/metasploit-framework.git,
• [ 1610 exploits, 914 auxiliary, 279 post ,471 payloads , 39 encoders , 9 nops ]
Ready in kali - used in this demo.
Available as windows installer. (Never really tried!..)](https://image.slidesharecdn.com/metasploitforbeginnersatnull-170121140307/85/Metasploit-For-Beginners-5-320.jpg)