This document summarizes how SSH can be used to compromise security in several ways:
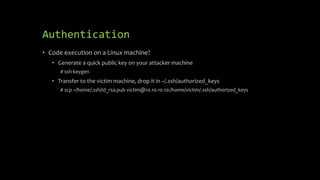
1. Authentication can be bypassed by generating a public key on an attacker's machine and transferring it to a victim's machine to allow code execution without a password.
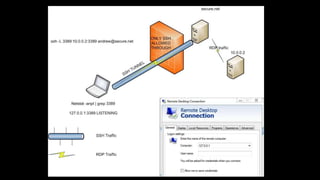
2. SSH allows file transfer and traffic tunneling which can be used to transfer tools, exfiltrate data, and bypass firewalls by tunneling any protocol over an SSH connection.
3. Dynamic tunneling with tools like SOCKS and Proxychains allows running scans, exploits, and other tools through an SSH connection without needing privileged access on the target.